GitHub Notifications Phishing Attack and How Hackers Are Tricking Developers in 2025

Hoplon InfoSec
23 Sep, 2025
GitHub notifications phishing attack
I checked my email late one night and saw a message that looked like it came from a government agency. It said it came from GitHub. The subject line told me that someone was trying to log in in a way that looked suspicious. I panicked right away. I hovered over the link and almost clicked without thinking too much. Something made me stop, maybe instinct or luck. When I examined it more carefully, I realized it was not genuine. That moment made me remember how easy it is to fall for scams that are hidden in trusted platforms.
This is exactly how the phishing attack that uses GitHub notifications works. Hackers are using GitHub’s own notification system to attack developers. These alerts look real, so they get past filters and go straight to inboxes. People trust them because they come from GitHub’s infrastructure, which makes it harder to find the trap. In the next sections, I’ll show you what these attacks look like, how they spread, and how to keep from being the next victim. It’s not a story about paranoia. It’s about being one step ahead when the attacker is right at the door.
What GitHub notifications are and why they are important
You already know how important notifications are if you’ve worked on a project hosted on GitHub. They let you know when someone brings up your name in an issue, comments on your pull request, or when there is a new security alert. They are what makes working together possible. Without them, developers would always miss updates.
Because they are so important, they are also great weapons for criminals. Think about getting an important email with the GitHub logo, the right address, and the right style. It seems safe. But there could be a poisoned link or a malicious app request inside. Because speed is important to developers, they often skim and click without thinking twice. The GitHub notifications phishing attack takes advantage of this dependence.
How hackers use notifications as weapons
Hackers don’t have to get into GitHub itself. Instead, they misuse the features that are already there. They make up problems or tag developers in repositories. GitHub’s system automatically sends emails to everyone who is tagged after that. The email looks real at first glance because it comes from GitHub’s own servers. But there is usually a bad link inside. Sometimes it takes you to a phishing site that looks like GitHub’s login page.
At other times, it asks you to give permission to an OAuth app that looks like a security tool. The attacker can get in once you click and agree. Some criminals even use the device code method to get you to give them access tokens in some campaigns. It’s a smart twist. They don’t try to fool your spam filter; instead, they let GitHub send the bait for them. That’s what makes this type of phishing so dangerous and effective.
Fake “security alerts” are filling up developers’ inboxes
A few weeks ago, thousands of developers got emails warning them about strange login activity. The subject lines said that someone from outside the country was trying to get into their accounts. The attackers even used the same format that GitHub uses for real alerts to make the warning seem real.
The link inside told users to change their security settings. In reality, it sent them to a fake OAuth app. Once they got permission, the attacker could see private repositories, delete code, and change workflows. This campaign spread quickly, affecting almost 12,000 repositories in just a few days. It showed how easy it is for a GitHub notifications phishing attack to grow.
The Job Offer Scam That Caught Developers
Hackers started using job offers as bait, which was another twist. Think about getting a message from GitHub that says you can make six figures. A lot of developers clicked on it, thinking it was a chance they couldn’t pass up. The link didn’t take them to a careers page; instead, it took them to a fake hiring portal.
The victim was asked to log in with GitHub or give permission for an app to continue the application. They didn’t know something was wrong until it was too late. This scam spread quickly because it used excitement instead of fear. A different approach, but the same outcome: account takeover.
Why OAuth Apps Are a Risky Way
Most people think that OAuth apps are safe. They see the request, click “accept,” and then go on. The problem is that a lot of these apps ask for a lot of permissions. Some want to read and write to all repositories, access workflows, or handle data for the organization. It’s like giving a stranger a copy of your house keys to let them use the app. Malicious OAuth apps are the last step in the GitHub notifications phishing attack.
After you install them, they don’t even need your password. They can work quietly in the background, stealing code, putting in malware, or deleting whole projects. One victim said that their repo was deleted overnight after they accidentally trusted an app that was linked to a fake alert.
Phishing with Device Code In Plain English
Device code phishing sounds complicated, but it’s really not. Hackers use GitHub’s system to make a verification code. Then they send you that code and ask you to enter it on a real GitHub site. When you agree, you unknowingly link your account to their app.
From the attacker’s point of view, the best thing about this trick is that it gets around regular security. The attacker can still get valid tokens from the code you just entered, even if you use two-factor authentication. It feels like a normal login for the victim. It’s an open door for the hacker.
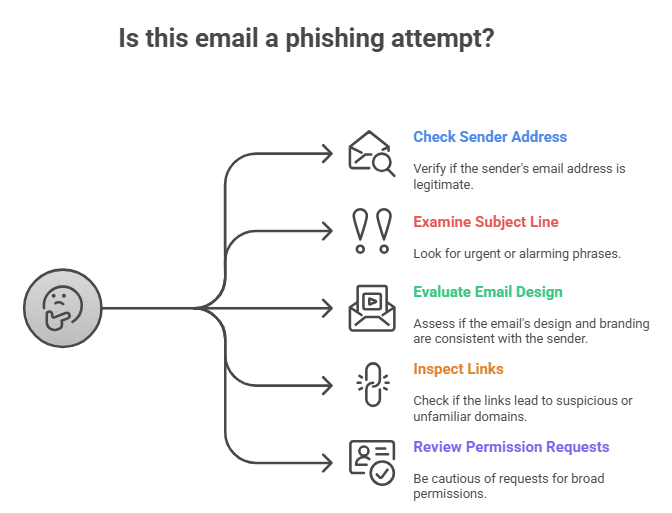
How a Phishing Notification Looks
There are some clear signs that an email is an attack. The sender’s email address is often [email protected], which is real. The subject line often has words like “Security Alert,” “Action Required,” or “Important Login Notice” that make it sound urgent. The email looks professional on the inside, with GitHub’s branding and layout. The links are the real trick.
They could either send you to a domain that looks like theirs or send you through several sites. Some attackers even host the fake site on GitHub Pages so it feels legit. Often the authorization screen will request broad permissions, sometimes full access to your repositories and workflows. If you ever see that, pause and do not approve the request. If you can spot these signs, you can avoid making a mistake.
The Human Side: Why People Still Fall for It
Developers are not careless. They are often under a lot of stress. It’s normal to want to fix something quickly when an alert says there might be a problem with your account. Social engineers use stress and urgency to get what they want. I remember talking to a friend who works at a startup.
While he was fixing a problem with a production system at 2 a.m., he clicked on a notification that looked suspicious. He didn’t read carefully because he was in that state of mind. His browser blocked the domain, but luck saved him. This kind of story shows why the GitHub notifications phishing attack works, even on people who are very good at what they do.
GitHub’s Response and Community Work
GitHub has been working hard to stop these scams. They delete harmful apps, suspend accounts that abuse notifications, and let users know about new campaigns. They also tell developers to check the permissions of OAuth apps and let them know if they see anything strange.
But the problem doesn’t go away because attackers keep changing their strategies. Every time GitHub blocks an app, a new one with a different name appears. It’s very important for people to report problems and be aware of them. When developers share stories and examples, it helps other people see the traps more quickly.
How to Keep Yourself Safe as a Developer
So, what do you do to stay safe? A few habits can make a big difference. Before you click, always check the domain. If you’re not sure, open GitHub by hand and sign in directly instead of clicking on an email link. Check the permissions of your OAuth app very carefully.
Don’t give permission if something seems off. Also, make sure your security layers are strong. If you can, use a hardware security key. Even when attackers get creative, it makes things harder for them. And last but not least, slow down. An urgent message is meant to make you hurry. If you take a breath, you’ll often see the red flags.
Defenses at the Organization Level
The risk is higher for businesses that use GitHub because one hacked account can affect whole teams. Companies should limit which apps can be approved, check repositories on a regular basis, and teach developers about phishing by having them try it out. It is also helpful to keep security logs.
They show strange behavior, like trying to get permission over and over again. Looking at these logs gives you a heads-up. Keep in mind that policies are needed for large-scale prevention, not just being careful yourself.
If you get caught, here are some steps to take to get better
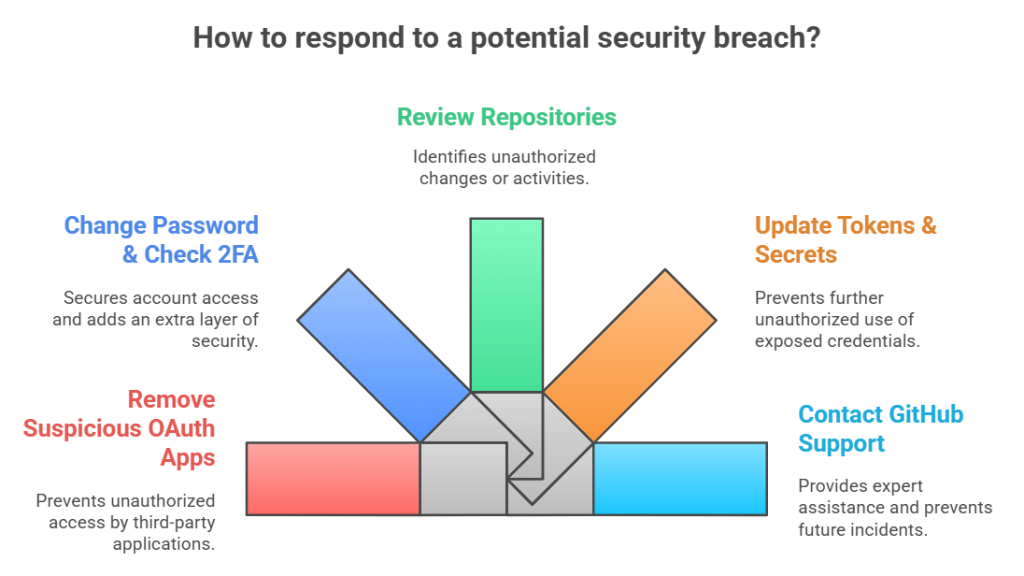
If you think you’ve been a victim, act quickly. First, use GitHub’s settings to remove any OAuth apps that seem suspicious. Change your password and see if two-factor authentication is still on. Start by reviewing your repositories carefully.
Keep an eye out for activity that seems out of character. You might notice commits showing up that you never made, branches missing without explanation, or workflows that have been altered in ways you did not plan. If you notice anything unusual, report it to your team or organization immediately, particularly when the repositories hold sensitive information.
Then update or replace any tokens or secrets that might have been exposed. Replacing exposed tokens and secrets cuts down the chance someone can keep using your account. Do that first. Then contact GitHub support and give them a clear summary of what happened. Their team can dig into logs, point out what changed, and walk you through steps to lock things down so the same problem is less likely to repeat.
Now think about what might come next. Attackers are creative and will try new angles. Instead of only sending fake alerts, they may begin hiding hooks inside discussion comments, pull request messages, or even sponsor invitations. These sections appear routine, so it is easy for people to skim past them and miss the warning signs.
On top of that, AI tools let scammers tailor messages to your work history. That makes phishing notices sound like they were written for you, which makes them harder to spot. The best defenses are simple: slow down before you click, check domains and permissions carefully, and report anything that feels off so others can learn from it.
It’s clear that attacks change, but so does awareness. There is more to the GitHub notifications phishing attack than just this one event. It might look different tomorrow, but the basic idea will still be the same: taking advantage of trust and urgency.
Final Thoughts
The last thing to remember is to trust but check. Trust is at the heart of this problem. We trust the platforms we use every day. Notifications from GitHub were made to help us, not hurt us. But when attackers take advantage of that trust, the results can be very bad. Fear is not the answer. It is paying close attention. Trust your gut, check out requests that seem strange, and talk to other people about your experiences.
When one developer finds a scam, it helps other developers avoid falling for it. The best way to protect yourself is to stay alert. When you see a GitHub notification in your inbox, stop for a second. Think about whether this is real or if someone is trying to trick you. That moment of caution could save you months of work that you have saved in your repositories.
Follow us on X (Twitter) and LinkedIn for more cybersecurity news and updates. Stay connected on YouTube, Facebook, and Instagram as well. At Hoplon Infosec, we’re committed to securing your digital world.
Share this :