Google Careers Recruiter Scam: How to Spot and Avoid Gmail Phishing

Hoplon InfoSec
01 Oct, 2025
"Interview invitation from Google Careers" showed up in the subject line on a Tuesday morning. It was short, courteous, and weirdly exhilarating. Most people looking for work know the feeling of hope when they get a message from a recruiter.
The person who sent the message even talked about a job that fit my skills. It felt like an opportunity was knocking for a second. But the link within wasn't what it seemed like.
This is the main part of the Google Careers recruiter scam. It takes advantage of people's desire to succeed, their confidence in major companies, and their natural need to click quickly when something appears good.
A lot of folks don't stop to think about why a recruiter would require my Gmail login information only to chat to me. That moment is what makes the difference between safety and giving in.
What this fraud truly is
The Google Careers recruiter scam is a type of phishing in which thieves pretend to be real Google recruiters. They send bogus emails or LinkedIn messages that sound like actual outreach. There is generally a link inside that takes you to a bogus Google login page. The victim enters in their Gmail login information, thinking they are confirming their identification for a real interview.
What makes this work so well is that it combines familiarity with urgency. People looking for work often apply to more than one location and expect to hear back. It looks like an email that talks about Google Careers is real. The trap is easy to fall for, but once someone steals your Gmail login information, the results can be terrible.
How the attackers got things ready
Cybercriminals don't send bad communications very often nowadays. They steal LinkedIn profiles, replicate job descriptions, and change the wording so it sounds natural.
One frequent method is to email a link that seems like an invitation to an interview. Another is to send a PDF called "Job Description.pdf" that needs a login to see.
The phony login page looks almost exactly like the real Google sign-in page. Even people who know a lot about security can be deceived. It's easy to miss the small things, like the URL being a little odd, when you're excited about a possible employment. That flood of feelings is exactly what attackers want.
A chain reaction that starts with one hacked inbox
One of my friends works in IT for a medium-sized business. Last year, one candidate who had applied for an opening fell prey to this identical trick. The person typed in their Gmail login information on a phony page and didn't think twice about it. In less than 48 hours, everyone on their contacts list was getting phishing emails.
Some of those messages went to the company's hiring manager, who almost clicked the same bad link. One thoughtless click turned into a week-long battle to limit the problem. It was a mess with password resets, system scans, and frantic phone calls.
The Google Careers recruiter fraud usually doesn't simply involve one individual. It starts a chain reaction that pulls other people into the problem.
The indicators of danger are clear to see.
How do you tell if a recruiting message is phony before it's too late?
First, look at the domain of the sender. Real emails from Google won't come from free services like Gmail or sites that look like Gmail, like "google-careers.com."
Second, pay attention to the tone. Real recruiters don't pressure you to act right away or warn that the offer will be gone in a few hours.
The request itself is another hint. It's a big red flag if someone invites you to check in to your Gmail through their link. A real recruiter will send you to official channels, not a strange site that steals your login information.
Looking more closely at messages that seem strange
It helps to build little habits. Hover your cursor over the link before clicking. Does it go to "careers.google.com" or something that seems wrong? Be careful if the path is buried by a URL shortener. You can also find out where an email came from by looking at its headers.
It's like inspecting the seal on a medicine package. Most of the time it's alright, but a quick look can keep you from taking anything bad. That little bit of doubt can keep you from being caught off guard by the Google Careers recruiter scam.
When customization makes it tougher to question
A lot of victims claim the bogus message seemed like it was designed just for them. Scammers will talk about your talents, the companies you've worked for, or a project that's on your profile. This personalization makes you less cautious because it seems like someone really looked into you.
It's scary, yet it shows how attackers change their tactics. They are no longer casting a wide net. Instead, they're looking at you and making up a story that you'll want to believe. The end effect is a scam that seems real enough to get past the natural doubts most of us have when we're online.
How to make sure a recruiter is who they say they are
If you ever get a message that says it's from Google Careers, stop what you're doing. Check out the recruiter's LinkedIn page. Do their connections and background on their profile make sense? That's strange if not.
The safest and easiest way to find the job ad is to go directly to the official Google Careers page. The message is phony if it doesn't exist there. Instead of replying to the email that looks suspicious, you can also get in touch with Google's official HR department through their contact forms. A real recruiter won't mind you taking this extra step.
Why your Gmail login is worth a lot
Your Gmail login information gives you access to a lot more than simply your inbox. Think about it: Gmail is often the email address that your bank, shopping accounts, or work tools use to send you recovery emails. A crook can reset dozens of services with just one password.
That's why the Google Careers scam is so profitable. It's not just about one person's job search; it's about snatching the digital keys to their whole online life. Once Gmail is hacked, everything from cloud storage to banking information is open to anyone.
The hidden effects that go beyond losing access
It could seem like a hassle at first to lose an email account. But the harm goes deeper. Attackers typically pretend to be victims and send phishing emails to coworkers, clients, and relatives. People don't trust you when they think you tried to swindle them.
The risk is higher for companies. If an employee falls for the fraud, they could put the company's systems at risk, reveal private information, or provide thieves a way into the corporate network. The devastation goes far beyond one inbox.
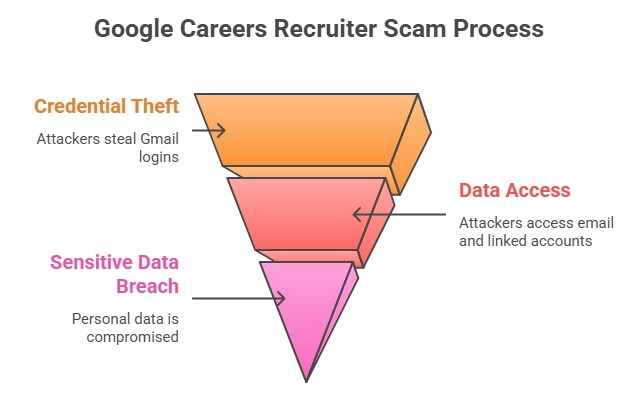
What to do if you previously clicked
If you think you've fallen for it, do something right now. Change your Gmail password from a device that hasn't been used before. Use two-factor authentication, and if you can, use an authenticator app or a hardware key. Look at the activity tab for your account to see if there were logins from places that don't usually log in.
Next, check which apps can get into your Google account. Take back anything you don't know. Change the password on all of your accounts if you used the same one somewhere else (this is a typical mistake). Let people who are close to you know that your email may have been hacked so they may be careful with any communications that seem strange.
Things you do every day to stay safe
You don't need to buy pricey gear to stop the Google Careers recruiter fraud. Every account should have its own password, so use a password manager. Turn on two-factor authentication for all of your accounts, not just Gmail. Also, never sign in to a job email through a link. Always go straight to the company's official site.
Little things build up. Checking your email from a recruiter should become as second nature as locking your door.
Extra layers for high-risk consumers
You are a prime target if you work in IT, finance, or leadership. Basic steps may not be enough for you. YubiKey and other hardware security keys offer the best protection because they physically stop phishing attempts.
Companies should keep an eye out for strange sign-in attempts and have a plan for how to respond quickly. If someone steals your account, a rapid lockout and reset process will limit the harm. Don't think of these scams as small problems; think of them as severe security threats.
What job sites and companies should do better
This is not just the candidate's issue. LinkedIn and Glassdoor should make it easier for recruiters to check people out and report impersonation. Employers can make it clear how they will contact candidates, which will help cut down on confusion.
A simple statement from Google Careers noting, "We will never ask you to log in through third-party links," would go a long way. Clear communication and quicker takedowns might make it harder for scammers to get away with their crimes.
Reporting and asking for aid
If you see or fall for the Google Careers recruiter scam, don't stay quiet. Use Google's phishing report tool to tell them about it. Let your country's cybercrime unit know—many have online forms for this kind of thing. Send the information to groups that fight phishing and keep an eye on bad websites.
When you report anything, you not only protect yourself, but you also keep other people from falling into the same trap. Every takedown makes it difficult for crooks to use the same techniques again.
Lesson: Before you click, stop.
People trust opportunity, which is the main reason this hoax works. The best approach to fight back is to take it easy. Before you click, ask yourself, "Does this message follow the steps I expect?" Is there an official source I can check? That little break could save you weeks of healing time.
The Google Careers recruiter scam is a good example of how current phishing mixes with real life. Job seekers, employers, and platforms all have a part to play in stopping it. And by being careful, you may make it tougher for them to get to you.
Source of Trust and Research Note
To learn how to hire safely, go to the official Google Careers page or the Google Safety Center.
A recent analysis from Proofpoint said that pretending to be a big brand in a phishing email is still one of the most prevalent ways for hackers to get into accounts around the world.
Suggestions from Hoplon
· Always check the identity of recruiters on the official pages of the companies they work for.
· Don't ever log in using links in messages from recruiters you didn't ask for.
· For Gmail and other important accounts, use hardware security keys.
· Teach your staff how to spot phishing tendencies in job emails.
· Tell providers and authorities right away if you get a questionable outreach.
Mobile Security: Blocks phishing links and malicious apps on phones before they steal Gmail logins.
Endpoint Security: Protects devices from takeover after stolen credentials are used.
Deep and Dark Web Monitoring: Alerts you if stolen Gmail details appear for sale online.
Web Application Security Testing: Secures job portals so attackers cannot host fake Google-like pages.
Penetration Testing: Simulates phishing attacks to expose weak points and train staff.
Follow us on X (Twitter) and LinkedIn for more cybersecurity news and updates. Stay connected on YouTube, Facebook, and Instagram as well.
Share this :