Protect Your Spreadsheets: Google Sheets Client-Side Encryption Now Fully Available

Hoplon InfoSec
17 Sep, 2025
Google Sheets client-side encryption
Imagine a shared spreadsheet that holds your company payroll template, a partner contact list, or regulated health records. Now imagine those cells encrypted in a way that even the cloud provider cannot read them. That is the promise behind Google Sheets client-side encryption, and the recent general availability makes that promise real for many organizations.
This is not just a new checkbox on a security settings screen. It is a change that nudges where control sits in cloud collaboration. For teams worried about compliance, insider risk, or cross-border rules, this turns an abstract feature into a practical option.
What Google means by full availability
When Google declares a feature generally available, it means the beta is over and the feature can be used with production-level support. In this case, the full availability announcement confirms that Sheets now supports import, export, decryption, and closer interoperability features that were previously limited.
Put plainly, full availability means IT can plan projects that depend on this capability without expecting sudden changes in behavior. It also signals enterprise readiness: admins can include client-side encryption in their security baseline.
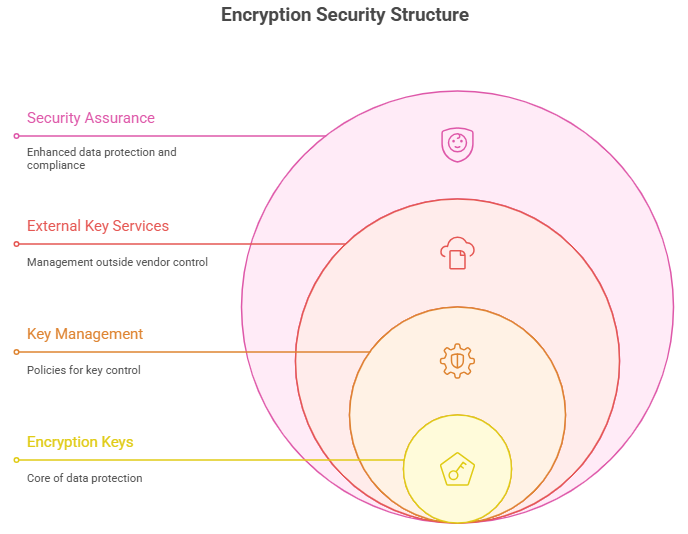
A simple explanation of how client-side encryption works in Sheets
Client-side encryption moves the encryption operation from a remote server to the user’s device, typically the browser. Data is encrypted before it leaves the user’s machine, and only encrypted bytes are stored in the cloud. That prevents the cloud provider from having a usable plaintext copy of the content.
From a practical view, this is about control. If you hold the keys or manage the key service, you decide who can decrypt. That is where the phrase “customer-managed encryption keys” becomes important, and it is what many regulated organizations want.
Keys, key services, and why they matter to IT teams
Encryption only works with keys, and who holds and controls those keys is the core security decision. Google Sheets client-side encryption ties into external key services that let organizations manage keys outside of Google’s domain. This design reduces the attack surface and helps with legal, regulatory, and contractual obligations.
Key management brings operational overhead. It introduces policies for key rotation, access control, monitoring, and recovery. That overhead is the trade for higher assurance: you get stronger separation of duties and less vendor access to plaintext.
Who can use this now, and which editions are supported?
Not every Workspace plan gets every advanced feature, and client-side encryption is no exception. Google lists specific supported editions where admins can enable these protections for users. That matters when you budget or negotiate licenses.
Before you build a rollout plan, check which edition you have. If you are in a regulated environment, verify that your edition and the chosen key service meet your compliance needs. This is a concrete gating factor for adoption.
How admins prepare and enable the feature step by step
Start with a simple audit. Identify the sheets that store sensitive data. Classify them by sensitivity and regulatory obligations. Next, choose a key service and plan your key management policies. That paves the way for a pilot.
A recommended pilot focuses on a single team: finance, legal, or a data protection owner. Test how sharing, versioning, and backups behave. Expect some processes to change. Educate users about how encryption affects search, previews, or external collaboration.
Office and Excel interoperability made practical
One surprise benefit in the rollout is improved interoperability with Office formats. Google has extended functionality so that client-side encrypted spreadsheets can be imported, exported, and converted more smoothly, including conversions to and from Excel. That helps mixed environments where teams use both platforms.
Practically, this reduces friction for partners who insist on Excel. You do not have to force every collaborator into Google Sheets only. That matters for mergers, third-party audits, and cross-vendor workflows.
Compliance wins and data sovereignty benefits
For organizations subject to laws like HIPAA, GDPR, or sector-specific rules, controlling encryption keys helps build defensible compliance postures. Client-side encryption supports auditability and gives legal teams a stronger story about who had access to plaintext.
Beyond rules, there is data sovereignty. If your company must keep control of keys under local law, the ability to host keys with a local provider or within a cloud HSM gives real operational comfort. This shift supports customers operating across stricter jurisdictions.
Real-world scenarios where this changes the game
Think of a hospital sharing lab results with a research partner. With client-side encryption, the hospital can encrypt spreadsheets before sharing, then revoke or manage decryption rights via key policies. The cloud still stores the file, but the hospital retains decryption control.
Or consider a defense contractor that must prevent cloud provider access to certain project sheets. The contractor can use a customer-controlled key service and limit decryption to devices inside a secure perimeter. These are not hypothetical; they are practical moves companies can make now.
Practical limitations and trade-offs to watch for
Nothing is free, and client-side encryption introduces trade-offs. Features like full-text search, real-time content scanning, or built-in preview functionality may be limited or behave differently when data is encrypted at the client. Plan for operational impacts.
You will also encounter higher complexity for backups, eDiscovery, or automated workflows that rely on reading file contents. Those tools need decryption access or new integration patterns, and that usually means coordination between security, legal, and engineering teams.
Performance and end-user experience: realistic expectations
Encrypting and decrypting in the browser adds CPU and network considerations. On modern devices the delay is often small, but on older hardware or large spreadsheets users may notice lag. Test with representative workloads.
User training helps. If people understand why small delays occur, they tolerate them better. Provide quick reference guidance and an escalation path for files that seem slow.
Migration, backup, and data portability considerations
Moving existing spreadsheets into a client-encrypted posture requires planning. If you add encryption to existing Sheets, you must ensure backups and exports include decryption pathways. Rekeying data, or rotating keys, also has a process.
For long-term access, you should document the key lifecycle, who holds key recovery rights, and how to perform emergency access. These are not optional details for regulated data.
The growing ecosystem: key providers and tooling options
A healthy ecosystem exists around key providers and hardware security modules. Google supports integrations with external key services, and the market offers commercial providers and Cloud HSM options for different risk profiles. That gives a choice to teams that want local control or high-assurance key protection.
Choice brings variety in SLAs, features, and integration effort. Evaluate providers for auditability, attestation, and compliance certifications. The right partner can simplify adoption and lower operational load for your security team.
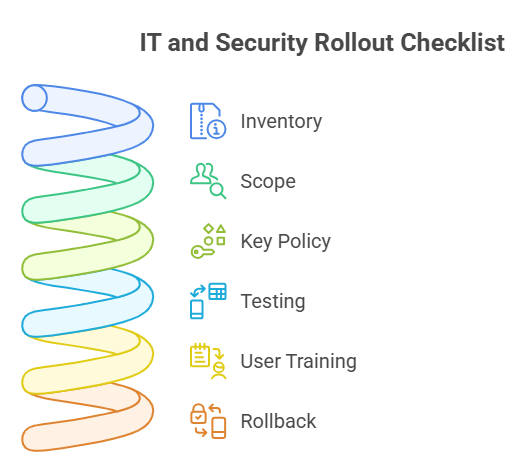
A practical checklist for IT and security teams
[Quick adoption checklist]
• Inventory: list sheets with sensitive data.
• Scope: pick pilot groups and use cases.
• Key policy: choose key service and rotation rules.
• Testing: validate sharing, export, Vault, and Takeout behavior.
• User training: prepare short guides for end users.
• Rollback: Have a contingency plan for decryption access.
This checklist keeps your rollout ordered. It helps bridge the gap between security goals and daily operations.
final takeaways and an action plan
This is a practical moment. The arrival of Google Sheets client-side encryption in full availability gives teams a real option to control encryption keys, reduce vendor access to plaintext, and tighten compliance posture. It will not replace every security control, but it is a strong addition to a layered strategy.
Actionable next steps: run an inventory, pick a pilot, choose a key provider, and test thoroughly. Balance the gains in control against the operational complexity. For many organizations the trade is worth it, because the outcome is clearer data ownership and stronger technical separation between the cloud provider and your most sensitive information.
Encryption on the client side makes data more secure, but it works best when it is used with more testing. Hoplon Infosec’s Web Application Security Testing finds hidden risks in apps and cloud tools, giving your business extra protection and peace of mind.
Follow us on X (Twitter) and LinkedIn for more cybersecurity news and updates. Stay connected on YouTube, Facebook, and Instagram as well. At Hoplon Infosec, we’re committed to securing your digital world.
Share this :