Iframe Payment Skimmer: How Hidden Loopholes Fuel Checkout Attacks

Hoplon InfoSec
24 Sep, 2025
iframe payment skimmer
You wake up to a lot of chargebacks and one terrible line in the security log: strange POST requests from a domain you don’t know. The site looks good. Customers checked out like they always do. But the names, card numbers, and CVVs are all gone. The browser skimmed those details while the customer typed them. This kind of failure starts with something small and trusted, like an iframe or script that everyone thought was safe.
You might want to think of payment iframes as a black box that you can ignore. A lot of teams do just that. That choice keeps work light and quick for weeks, but then it doesn’t. The risk isn’t very big. It is smart, quiet, and hidden in code from other people.
What is a payment skimmer in an iframe?
An iframe payment skimmer is a type of malware that steals payment information from fields that are inside iframes or are displayed by code on a checkout page. Attackers can add JavaScript that listens for form input, copies it, and then quietly sends the data to their own servers. People often call this kind of attack “web skimming” or “Magecart campaigns.”
It’s helpful to think of the checkout page as a small stage. The frame around your payment fields may look safe, but if a hidden actor has a microphone or a patch to the stage wiring, they can still hear you from the wings. For merchants, that microphone often comes from a third-party script, a CDN asset that has been hacked, or an integration that has been set up wrong.
How attackers use iframes and overlays as weapons
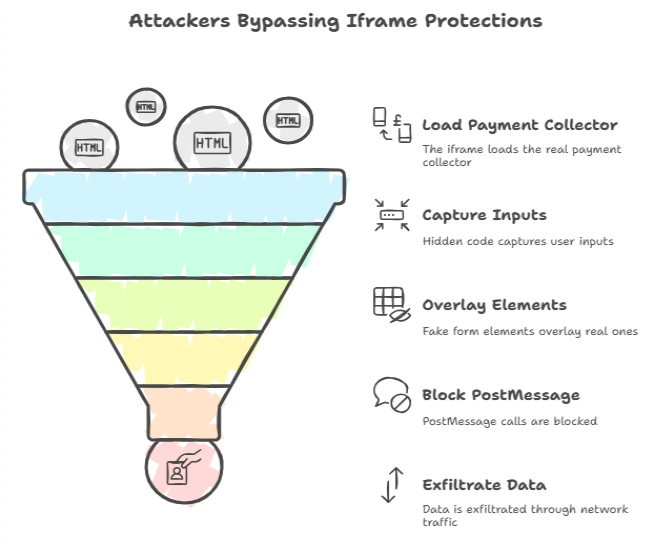
Attackers use a number of clever tricks to get around the protections that people think iframes offer. One way to do this is to make an iframe that the attacker controls and that loads the real payment collector along with hidden code that reads inputs. Another way is to put fake form elements on top of real ones or block postMessage calls so that the payment information goes to a place that the site owner can’t access.
These methods let attackers get around same-origin protections and look like trusted content for a short time.
Those tricks don’t stay the same. Attackers also hide exfiltration in normal network traffic, delay activation until a certain page state, and obfuscate code. From a defender’s point of view, the technique looks like normal browser behavior until someone looks closely at the DOM or watches how scripts work while they are running.
Actual events that changed how teams think about the safety of the checkout process
Many teams have had to rethink checkout safety because of high-profile campaigns and targeted incidents. Recent reports have framed the threat not just as opportunistic fraud but also as a structural flaw in how payment pages use third-party code and services. The stories made it clear that even if the payment provider is trustworthy, the integrations around it can be risky.
You don’t have to be a huge brand to be targeted. Attackers like big things. If one hacked library gets into a lot of stores, they can skim thousands of cards at once. That’s why the industry has stopped worrying about single-site compromises and started worrying about how they affect the whole supply chain.
Why classic iframe protections don’t work in real life
People use iframes to separate sensitive inputs on a page, and they depend on headers like X-Frame-Options or simple CSP rules. In many real-world situations, those headers are there but not enough. The reason is that the rest of the page often loads scripts from other sites that can change the DOM, add overlays, or switch sources without the page owner knowing.
The practical outcome is that solely static controls, despite their utility, do not constitute a comprehensive solution. Monitoring the behavior of scripts and the integrity of the resources you load must be part of defense.
The supply chain problem: scripts that were once trusted become hostile
A lot of modern checkouts have analytics, personalization, ad tags, chat widgets, and payment helpers all mixed up. Each of those is an outside call and a possible entry point. Attackers don’t always get into your server. They go after the supply chain, like the CDN, the marketing tag manager, or a vendor that sends code to a lot of clients. Once they get control of one of those things, they can access dozens or even hundreds of payment pages.
That means keeping track of and controlling third-party scripts is not a choice. It is a basic security job. It also means that getting rid of just one bad script can stop an attack faster than looking for code in your app
PCI rules and the new reality for payment pages when it comes to compliance
Standards organizations saw the change and made controls to match it. New rules stress that scripts running on payment pages must be managed, approved, and watched over, and that change detection must be in place to quickly find any unauthorized changes. In short, compliance now wants proof that the client side is being actively controlled, not just an afterthought.
For a lot of teams, meeting these requirements means getting new tools and learning new ways to do things. It also changes the way you talk to payment service providers about who is responsible for what.
What to look for in real time to find tampering
The quickest way to find a skimmer is to look at the page from the browser’s point of view. Be on the lookout for unexpected changes to the DOM around payment fields, network calls to domains you don’t know after input events, or hidden inline scripts that show up during checkout. These strange things are often the first clear sign that something is wrong.
A monitoring agent that only looks at network calls won’t see script behavior that only happens inside the DOM. To get the clearest signal set, use network and integrity checks along with DOM monitoring.
Making payment frames stronger with rules and checks for integrity
You can use Content Security Policy to limit which domains can run scripts and Subresource Integrity hashes on third-party libraries to stop the browser from accepting changed files. Those tools make it harder for attackers, but they aren’t perfect; they need to be kept up to date, and they don’t always work when a trusted vendor is hacked.
Use iframe sandbox attributes whenever you can, limit postMessage endpoints, and use strict cookie flags and SameSite attributes in addition to those. When used together, these tools make it harder for attackers to get into the system and limit what foreign code can do during checkout.
Payment service providers and merchants should use safer integration patterns.
One common practice is to have a PSP handle all of the payment collection and give you a locked frame that you can’t change. Another way is to use tokenization so that the raw card data never gets to your server.
Both strategies work, but they need to be kept in check. For example, make sure that the embedded frame’s source never changes and keep other page scripts separate from the payment flow.
If you can’t avoid third-party scripts on the same page, use strict selectors or micro frontends to keep those scripts separate from the payment DOM. The goal is to make the checkout area as calm and easy as possible.
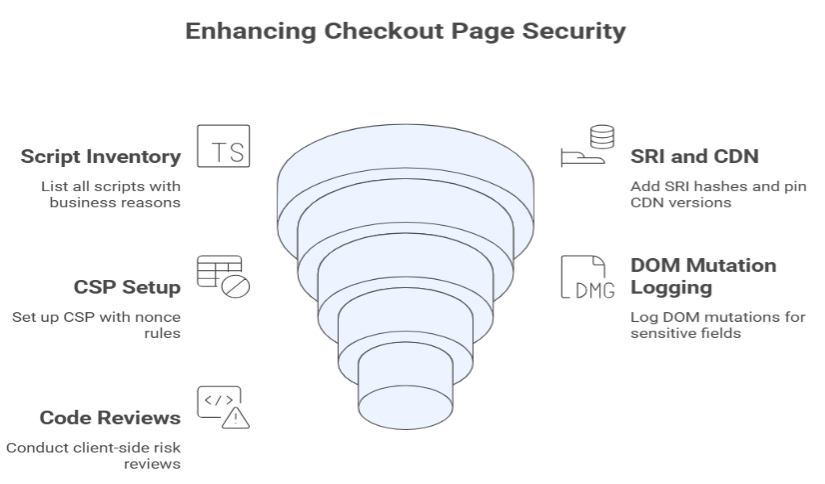
A checklist for developers: the code and settings that are important
Keep a list of all the scripts that run on checkout pages. Each one needs to have a business reason. Add SRI hashes and pin CDN versions. Set up CSP with nonce rules and limit where forms can POST. For sensitive fields, set up logging for DOM mutations. These things aren’t very exciting, but they can mean the difference between an accident and a close call.
Also, add code reviews that look at risks on the client side. A lot of teams do great server audits but forget that the browser is a runtime full of secrets.
A playbook for monitoring, alerting, and responding to live attacks
If you find something, make sure you can quickly contain it by taking the page down, changing the keys or tokens, cutting off the compromised vendor’s access, and letting your payment provider know. Make a checklist for how to respond to an incident that includes how to talk to customers and card networks, and take a forensic snapshot of the checkout state for later analysis.
Automation is helpful. Automated page snapshots, network flow captures, and short-lived feature flags that you can turn off all help lower the mean time to containment.
Quick fixes that stop the most common skimmers from working
In the short term, turn off any third-party tags that aren’t needed on checkout pages. Use strict CSP and subresource integrity. Add checks that run at runtime and send alerts when the DOM around payment fields changes. If you use tag managers, only let certain people make changes and make sure they get approval first.
Those fixes sound small because they don’t take long. But small fixes are what stop a lot of opportunistic campaigns before attackers try something harder.
When to call your PSP, vendor, or incident response team for help
Call the PSP right away if you see data being stolen or POSTs from the browser that you don’t know about. Payment processors can help you figure out if a frame or collector has been changed. If the attack vectors involve third-party vendors, tell their security contacts and treat the event as a breach in the supply chain.
Escalation does not mean weakness. When containment needs actions you can’t do by yourself, this is the right play.
How to act if you are hit: customer trust and disclosure
Be clear and quick. Tell customers who have been affected to keep an eye on their statements and work with banks to stop fraud. Write a short, honest statement that explains what the problem was and what you did about it. Customers are more likely to forgive you if you talk to them than if you don’t.
Add coordinating with the law and public relations to the checklist after the event. Good communication with customers can help protect your reputation and make it easier to deal with regulations.
Threats that are coming and how to keep your defenses up to date
Expect attackers to keep getting better at hiding their tracks, using CSS tricks to hide data collection, and automating the search for vulnerabilities in the supply chain. Your defenses need to change as well. Think about using behavioral detection, script behavior fingerprints, and regular audits of vendor code. Most of the time, security that feels automatic comes from doing the same thing over and over again.
Keeping up with things is not a one-time thing. It’s a cycle: take stock, harden, watch, review, and do it again.
A useful guide for stopping iframe payment skimmers
This week, do three useful things. First, take out any third-party scripts that aren’t necessary from your checkout. Second, add Subresource Integrity and make your Content Security Policy stricter. Third, put a runtime DOM monitor on the payment fields and connect it to an alert channel. These moves are quick and stop most attacks before they get too big.
You should think of payment pages as part of your security perimeter. You trade in lucky escapes for planned resilience when you do this. That is the key to real iframe payment skimmer prevention: small, steady steps that make it costly and uncommon to take advantage of.
Follow us on X (Twitter) and LinkedIn for more cybersecurity news and updates. Stay connected on YouTube, Facebook, and Instagram as well.
Share this :