AI-Powered Linux Malware Koske Exposed: What You Must Know to Stay Safe

Hoplon InfoSec
28 Jul, 2025
Koske, an AI-driven Linux malware, is a new and growing threat recognized by cybersecurity experts globally. What makes it distinctive is its use of artificial intelligence to conceal itself openly while launching highly covert attacks on Linux servers. In this article, I will explain what makes Koske unique, how it works, and what steps you can take to protect your Linux environments.
What is AI-powered Linux malware Koske?
AI-powered Linux malware Koske is a sophisticated form of malicious software that targets Linux systems. Unlike traditional malware, it employs advanced methods that incorporate artificial intelligence to evade detection. Koske embeds harmful code within seemingly innocent image files, such as panda pictures, which are cleverly designed to also act as executable programs. This double nature makes it very difficult to catch. In addition, Koske installs a rootkit to remain hidden and runs cryptocurrency mining software to steal resources from infected machines.
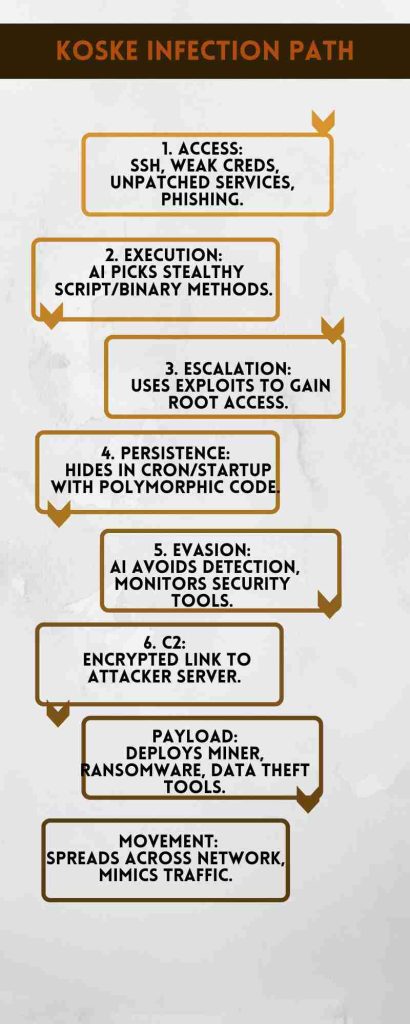
AI-Powered Linux Malware Koske was first discovered in early 2025 when security researchers noticed unusual cryptocurrency mining activities linked to Linux servers. The malware spreads mainly through cloud environments, often exploiting misconfigured services such as JupyterLab. Attackers use specially crafted image files to deliver the payloads. Over time, Koske has grown more advanced, adopting proxy switching and machine learning strategies to avoid detection and maintain persistent access.
Why AI-Powered Linux Malware Koske Matters for Your Security
Koske is a serious threat for anyone managing Linux servers because it can quietly infiltrate and take control of systems. Once inside, it uses the server’s computing power without permission, often for activities like cryptocurrency mining or launching further attacks. The malware operates stealthily, which makes early detection difficult and allows it to run undisturbed for long periods.
What sets Koske apart is its use of artificial intelligence. This allows it to adapt to changing environments and security defenses, shifting its behavior to avoid detection. As a result, traditional security tools may not be enough to catch or stop it. Infected systems are at risk of slow performance, data breaches, and deeper system compromise if attackers use the access to escalate privileges or move laterally across a network.
Financial Impact of Koske Infections
Once Koske infects a Linux server, it commandeers system resources to perform cryptocurrency mining. This activity heavily utilizes CPU and memory, resulting in greater power usage. As a result, organizations often face noticeably higher electricity bills and accelerated wear and tear on their hardware components. In cloud environments, this surge in resource usage can cause unexpected spikes in service costs, putting additional financial strain on businesses.
Beyond these direct operational expenses, the broader impact on an organization’s reputation can be severe. If Koske’s presence leads to a data breach or exposes sensitive information, companies may face legal and regulatory consequences, including fines or sanctions. Moreover, addressing an infection requires costly investigations, thorough system cleanups, and sometimes full system rebuilds to ensure that the threat is completely removed and systems are secure again, adding to the overall financial burden.
Attack Strategies and Evolution of AI-Powered Linux Malware Koske

Koske starts by targeting vulnerable or misconfigured Linux environments. One favored entry point is JupyterLab setups that lack proper security. The malware is delivered via polyglot image files that look harmless but contain executable code. Once inside, it installs a rootkit that hides its presence from regular monitoring tools. Its cryptocurrency miner runs entirely in memory, avoiding detection by scanning file systems.
One remarkable aspect of Koske is its use of artificial intelligence to manage communication with its control servers. It can detect when traffic is being monitored or blocked and switch proxy servers or mining pools automatically. This flexibility allows it to keep operating longer and makes it harder to remove.
AI-Powered Linux Malware Koske mainly affects Linux servers in cloud or enterprise environments where security configurations are not tight. Targets include research organizations, technology companies, and service providers that use JupyterLab and similar tools. Since its discovery in early 2025, reports of infections have gradually increased, though no major public data breaches have yet been linked directly to Koske.
Future Outlook on AI-Powered Linux Malware Koske
As artificial intelligence technologies improve, malware like Koske will likely become more common and more challenging to detect. Attackers will continue to build smarter malware that can adjust tactics quickly. Security teams need to prepare for threats that use unexpected hiding spots and automated behaviors to bypass defenses.
Detecting Koske is difficult due to its unique methods. The malware’s polyglot images can bypass traditional file filters. Its rootkit hides from normal system scans, and the mining process runs entirely in memory. Many security teams are not equipped with tools that can detect these stealth techniques. Additionally, cloud environments add complexity with numerous services and access points, increasing the risk of misconfigurations.
Prevention
Keep all Linux systems and cloud services updated with the latest security patches.
Regularly applying security updates is crucial because these patches fix known vulnerabilities that malware like AI-Powered Linux Malware Koske often exploits. Staying up-to-date reduces the chances of attackers finding weak points in your systems.
Harden JupyterLab and related services by enforcing strong authentication and restricting access.
Since Koske frequently targets poorly secured JupyterLab environments, implementing strong password policies, multi-factor authentication, and limiting user access only to trusted personnel can significantly reduce the risk of unauthorized entry.
Monitor uploads for suspicious files, especially images that could contain hidden code.
Because Koske hides malicious code inside seemingly harmless image files, it’s important to use tools or filters that scan uploaded files for hidden scripts or unusual behavior. This helps catch threats before they reach your servers.
Limit exposure of administrative and management interfaces on the internet.
Reducing the number of publicly accessible admin portals and using firewalls or VPNs to restrict access ensures that only authorized users can reach sensitive control panels, minimizing opportunities for attackers to exploit these entry points.
Detection
To detect the presence of AI-Powered Linux Malware Koske, use behavioral monitoring tools that can identify unusual memory usage and suspicious process activity. These anomalies often signal that the malware is running in the background, attempting to evade traditional detection methods.
Additionally, analyze network traffic for abnormal connections, such as those leading to proxy servers or cryptocurrency mining pools. Regularly reviewing system logs can also help spot unauthorized commands or unexpected configuration changes, which are early indicators of a potential compromise.
Containment
Isolate infected systems as soon as an infection is suspected to prevent spread.
Immediately disconnecting compromised devices from the network helps stop the malware or attacker from spreading to other systems. This isolation limits the attack’s scope and protects critical infrastructure from further damage.
Use specialized tools to remove rootkits and memory-resident malware.
Rootkits and memory-resident malware are designed to evade detection and persist on infected machines. Using advanced anti-malware and forensic tools specifically built to detect and eradicate these threats ensures thorough cleaning of the system.
Audit scheduled tasks, cron jobs, and services for unauthorized entries.
Attackers often create or modify scheduled tasks and services to maintain persistence. Regularly auditing these system components helps identify and remove any unauthorized or suspicious activities that may reinfect or continue the attack.
Reset network settings, including proxies and DNS configurations.
Malware or attackers may alter network configurations to redirect traffic through malicious servers or to evade detection. Resetting these settings to their trusted defaults helps restore secure communication and prevents data leaks or further compromise.
Several cybersecurity groups have released detection signatures and guides for Koske. Trusted blogs and open-source malware analysis platforms are good sources of updated information and indicators of compromise. Staying connected with the security community helps keep defenses current.
How Hoplon Infosec Helps Protect
Hoplon Infosec supports organizations by providing expert assessments and incident response for threats like the AI-powered Linux malware Koske. We specialize in identifying advanced threats and securing cloud and Linux environments. Our services include patch management, security audits, and ongoing monitoring to ensure systems remain safe.
Frequently Asked Questions
Is AI-Powered Linux Malware Koske limited to Linux?
Yes, Koske targets Linux systems specifically, focusing on servers and cloud environments.
Does Koske need user interaction to infect?
No, it primarily exploits security gaps such as weak configurations or exposed services.
Will traditional antivirus catch AI-Powered Linux Malware Koske?
No, due to its use of image files and memory-only malware, traditional antivirus solutions often miss Koske.
What should I do if I suspect infection?
Isolate the affected systems immediately and conduct a thorough investigation and cleanup.
Final Thoughts
The AI-powered Linux malware Koske is a growing threat that combines artificial intelligence with clever hiding techniques to attack Linux servers silently. By hiding inside panda images and using rootkits and memory-resident miners, it stays under the radar. If you manage Linux or cloud environments, this malware should be on your radar. Applying timely patches, tightening access controls, and monitoring systems closely are your best defenses. If you need help, experts like Hoplon Infosec can guide you through detection and recovery. Staying proactive is the best way to keep your systems safe from this evolving threat.
Explore our main services:
ISO Certification and AI Management System
Web Application Security Testing
For more services, go to our homepage.
Follow us on X (Twitter) and LinkedIn for more cybersecurity news and updates. Stay connected on YouTube, Facebook, and Instagram as well. At Hoplon Infosec, we’re committed to securing your digital world.
Share this :