Internal Penetration Testing: 7 Proven Tips for 2025

Hoplon InfoSec
24 Nov, 2025
The first time I watched a company face a serious security scare, it didn’t come from a criminal syndicate overseas or a Hollywood-style hacker smashing through firewalls. It came from a forgotten workstation sitting quietly in a conference room, logged in, ignored, and wide open. That moment changed how I viewed cybersecurity forever, because it showed that the biggest risks often exist inside the network, not outside it.
Most businesses assume danger approaches from the perimeter. They imagine attackers hammering at firewalls, probing external systems, and launching remote exploits. But the truth? The real surprises appear behind trusted walls. Internal penetration testing exposes those hidden weaknesses long before an attacker does.
What Internal Penetration Testing Really Is
Believe it or not, internal penetration testing is far less mysterious than people assume. At its core, it simulates what happens if someone gains access inside your network. That someone could be:
Disgruntled employees
People with access and a motive.
Stolen or leaked credentials
Passwords reused, cracked, or phished.
Physical access and tailgating
Someone simply walks in behind an employee.
Internal penetration testing answers one simple but critical question:
If an attacker is already inside, how far can they go?
Most leadership teams are shocked by the answer.
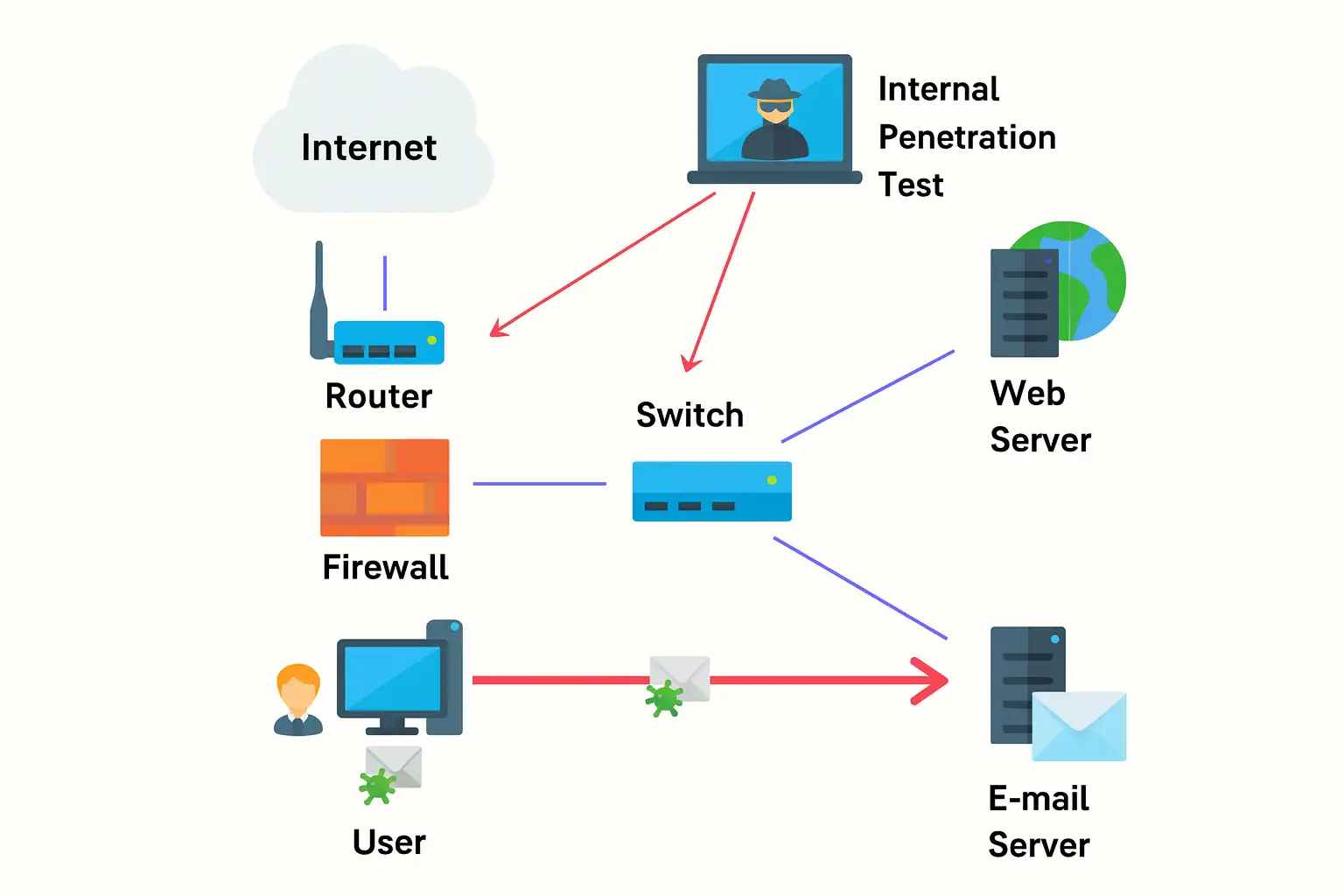
How Internal Penetration Testing Differs From External Testing
External testing feels like protecting a castle, high walls, guarded gates, watchtowers scanning the horizon. Internal penetration testing feels very different.
It’s like discovering someone already standing in the hallway.
Suddenly, the challenge becomes:
preventing movement,
detecting behavior,
protecting crown-jewel systems, understanding lateral pathways.
Instead of attack resistance, it measures attack survivability.
The Shocking Weaknesses Found Inside Networks
One IT manager I worked with believed his network segmentation was airtight… until an internal test showed that a low-privileged user could reach payroll records in under fifteen minutes.
Other common discoveries include:
open shared folders full of sensitive data, administrative tools available to ordinary accounts,
legacy systems still trusting old permissions.
Nobody expects these issues until they’re exposed.
The Slow Accumulation of Internal Misconfigurations
Here’s the uncomfortable truth:
Most internal weaknesses aren’t created intentionally.
They come from:
rushed deployments,
convenience over security,
undocumented changes,
temporary access that became permanent.
Internal penetration testing shines a light on risks that quietly snowball over the ears.
Human Error and Internal Security Failures
Phishing ties directly into internal compromise more than most leaders realize. One clicked link gives an attacker the same starting point as an internal penetration test.
I’ve watched:
entire networks unravel because one employee reused a password,
malware spread through mapped drives,
domain access escalated from a single infected laptop.
The smallest human habit can unlock the largest breach.

Internal Penetration Testing as a Business Fire Drill
I often compare internal penetration testing to a fire drill:
You hope you never need it,
But if the day comes, it saves everything.
It exposes:
response delays,
communication confusion,
monitoring tool failures.
Many organizations discover during testing that alerts never triggered. That realization alone justifies the effort.
Compliance Drivers for Internal Testing
Frameworks and regulations now expect internal controls to be validated, not assumed. Internal penetration testing directly supports compliance programs like:
ISO 27001
SOC 2
HIPAA
PCI DSS
Auditors want proof. Customers want assurance. Boards want liability reduction.
Here are two examples that always stay with me:
Manufacturing network crossover
A testing team unintentionally accessed machine control interfaces because production equipment was connected to corporate WiFi without segmentation. The risk was physical and dangerous.
Printers leaking sensitive data
A healthcare office discovered that printers cached patient records. Nobody monitored them because they seemed harmless.
Internal penetration testing uncovers entry points nobody even thinks to question.
How Internal Penetration Testing Promotes Security Maturity
Internal penetration testing teaches an important lesson:
Security is not a checkbox; it’s a living environment.
Networks evolve. Users change. Systems drift. Internal testing keeps organizations aware rather than complacent.
This is why businesses search for:
proactive risk assessment strategies,
continuous improvement approaches,
internal network hardening methods.
Modern Factors Increasing Internal Exposure
Several trends have amplified internal risk:
Remote work
Home networks are the new internal pathways.
Cloud integrations
Services connect in ways teams don’t always track.
Shadow IT and device sprawl
More devices = more trust relationships = more risk.
Attackers know this, and they exploit it.

Why Businesses Need Internal Penetration Testing Now
Perimeter defenses aren’t enough anymore. Attackers bypass them every day using credential harvesting, supply-chain infiltration, and social engineering.
Internal penetration testing provides the reality check organizations desperately need:
What can an attacker touch?
How fast can they move?
How long until someone notices?
Knowledge creates resilience.
Final Thoughts-You Can’t Fix What You Can’t See
After years of watching internal penetration testing transform environments, I believe it is one of the most valuable security measures any business can take. Not because it finds flaws, but because it reveals truth. Awareness leads to stronger policies, smarter controls, and safer operations.
The simple takeaway:
Internal penetration testing lets you finally see what’s happening inside your own network, before someone else does.
FAQs
1. Does internal penetration testing require specialized tools?
Yes, but professional testers combine tools with manual techniques, which is where real insight comes from.
2. Can internal testing help prevent insider threats?
Absolutely, by limiting privileges and detecting abnormal internal movements.
3. Is internal penetration testing safe for production systems?
When properly scoped and managed, it is designed to avoid operational disruption.
4. Who inside a company should know a test is happening?
Often, only key stakeholders, to preserve realistic conditions.
5. Does internal testing help justify cybersecurity budgets?
Yes, leadership responds far faster to demonstrated risk than to theoretical vulnerability.
Explore our main services:
· Deep and Dark Web Monitoring
· ISO Certification and AI Management System
· Web Application Security Testing
For more services, go to our homepage.
Author: Hoplon Infosec
Bio: Security enthusiast with over 10 years in mobile cybersecurity. Connect with me on LinkedIn.
Address: 1415 W 22nd St Tower Floor, Oak Brook, IL 60523, United States
Phone: +1 773-904-313 , Contact: [email protected]
About/Privacy: At Hoplon Infosec, we provide expert insights into cybersecurity. Our editorial policy: all articles are written by in-house specialists or thoroughly reviewed by them to ensure accuracy, credibility, and up-to-date information.
Share this :