CVE-2025-37899 ksmbd Use-After-Free Exploit Technique Exposes Critical Linux Kernel Flaw

Hoplon InfoSec
09 Sep, 2025
CVE-2025-37899 ksmbd use-after-free exploit technique
A single short network message can be the first domino in a cascade that topples an entire system. That is the grim idea behind a freshly publicized kernel bug, and it makes standard assumptions about safety feel suddenly thin. The flaw is not a flashy remote backdoor with a clever name. It is a timing and lifecycle mix-up inside the kernel that, when prodded the right way, lets code reuse freed memory in dangerous ways. The discovery has been written up in multiple places and carries the identifier CVE-2025-37899 ksmbd use-after-free exploit technique.
When you read technical write-ups, they can feel abstract. This time the story is concrete. A server handling file sharing calls a function to free a user object while another running thread still expects that object to be valid. That tiny mismatch is what the CVE-2025-378997899 ksmbd use-after-free exploit technique takes advantage of. The bug sits in a subsystem many people do not watch closely, but it is reachable in common deployments, and so it deserves immediate attention.
What is a use-after-free, and why does it matter?
Use after free is one of those classic programming mistakes that keeps reappearing in new guises. At a basic level a memory region is freed and then later referenced as if it were still valid. The code is trusting memory that no longer belongs to it. That trust can be broken by an attacker who forces the program to reallocate that memory for something useful to them.
In the kernel space the stakes are higher. A user mode program corrupting memory in the kernel can lead to privilege escalation or code execution with system-level rights. In this case, the CVE-2025-37899 ksmbd use-after-free exploit technique targets a kernel server process that handles network file sharing, so the path from a remote request to kernel memory corruption can be surprisingly short.
Why KSMBD is an attractive target for attackers
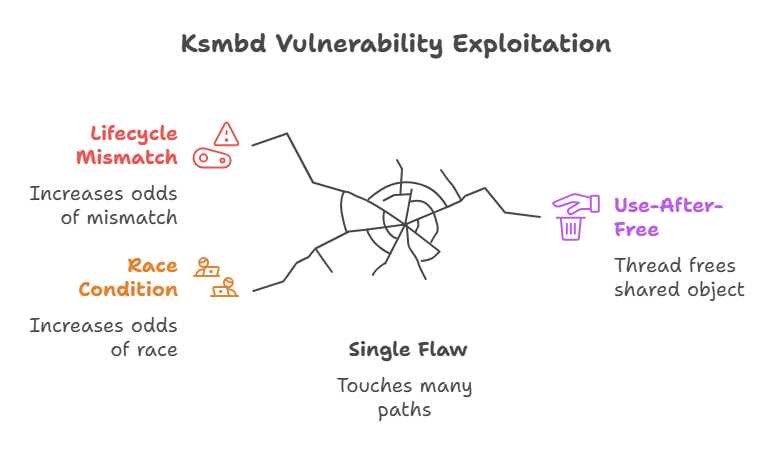
ksmbd implements the SMB protocol inside the Linux kernel, and that is a lot of functionality in one place. File sharing, session state, multi-connection bindings, and more all live inside that code. That concentration of features means a single flaw can touch many paths and states, which increases the odds of a race condition or lifecycle mismatch.
Attackers like components that accept network input and keep state. ksmbd does both. The specific issue behind the CVE-2025-378997899 ksmbd use-after-free exploit technique arises in session logoff handling, where one thread may free a shared object while another thread still uses it. That kind of concurrency hazard is exactly the sort of foothold an exploit developer wants.
The root cause behind the bug in plain language
Imagine two clerks sharing a guest book. One clerk removes a visitor entry thinking it is safe, while the other looks for that same visitor to do follow-up work. If the second clerk finds a new visitor in the same slot, confusion arises. In program terms the memory slot was freed, then reallocated, and now contains attacker-controlled data.
CVE-2025-37899 ksmbd use-after-free exploit technique leverages this pattern inside the kernel. The handler for a logoff request frees the session user object without ensuring that no other connection is about to access it. With carefully timed requests, an attacker can cause reuse of that freed memory under attacker control. The core programming mistake is small; the consequences can be large.
Step by step: how the exploit is triggered
The exploit starts from the network. An attacker opens connections, performs operations that bind connections to a session, and then triggers a logoff that frees shared structures. The key is to create a window where a different thread goes looking for that same object after it has been freed. If that freed memory is reallocated for attacker data, the attacker gains a read or write primitive in kernel space.
From that primitive, the exploit developer can escalate. They may cause kernel crashes to probe behavior or craft fake objects to move the attack forward. The CVE-2025-37899 ksmbd use-after-free exploit technique is essentially a choreography of connections and timing. It is not trivial, but it is reproducible in the right conditions.
How modern techniques amplify simple heap bugs
A plain use-after-free can be noisy and unreliable. Modern research has shown ways to make these conditions far more reliable. Timing side channels, allocator behavior, and careful memory grooming let attackers control what gets allocated into freed slots. That turns a flaky crash into a deterministic exploit path.
That amplification is why administrators should not dismiss “minor” heap bugs. CVE-2025-37899 ksmbd use-after-free exploit technique might look like a limited flaw on paper, but with allocator manipulation and cross-thread timing strategies, it becomes much more powerful. Researchers have demonstrated several such methods that take limited primitives and upgrade them into arbitrary memory read or write capabilities.
The role of SLUBStick and related allocator attacks.
SLUBStick is a concrete example of how allocator timing and cache behavior can be weaponized. It uses timing leakage in the kernel allocator to reliably arrange memory reuse. That reliability converts a one in a hundred success into a near one hundred percent success for commonly used caches.
This is relevant because the CVE-2025-378997899 ksmbd use-after-free exploit technique sits in the same category of vulnerabilities that SLUBStick can exploit. If an attacker pairs the session logoff race with an allocator timing trick, they can increase the exploit success rate dramatically. The wider lesson is simple. Exploitation is often a two-step dance. The bug gives the steps, and a technique like SLUBStick supplies the rhythm.
Who found it and how the discovery unfolded.
A security researcher documented the discovery and analysis in a public write-up. The researcher traced the race path inside the session handling code and reproduced the conditions that allow a user object to be freed while still referenced elsewhere. That careful, patient work is typical of kernel vulnerability research, and it paid off here.
The research thread is also a reminder of how much detail goes into such findings. The write-up walks through code paths, reproducer cases, and the precise conditions needed to trigger the issue. That level of disclosure is useful to defenders because it lets them test and validate mitigations in their environments.
What systems and kernel versions are affected??
Public vulnerability trackers list kernel versions that include the faulty ksmbd code paths. Vendors and distributors have been updating advisories as fixes land. At the moment, the CVE-2025-37899 ksmbd use-after-free exploit technique is noted as fixed in recent kernel releases, but older kernels remain vulnerable until they receive backported patches.
If you run kernels shipping ksmbd and you cannot immediately upgrade, vendors like Red Hat and other distribution maintainers have published advisories and patches. You should check your distribution security channels and apply any kernel updates or backports your vendor supplies.
Patching and mitigation status you should know.
The official vulnerability entry for CVE-2025-37899 records the fix in the ksmbd logoff handler and points administrators toward patched kernel versions. Upstream kernel maintainers committed a code patch that prevents freeing the object while it could still be referenced. Distributions are now packaging and releasing those kernels or backported fixes.
Practical mitigation in the short term includes disabling ksmbd if you do not need in-kernel SMB support or restricting access to SMB ports at the network perimeter. Many teams will choose to schedule a kernel update during a maintenance window to apply the definitive fix. Those updates remain the central defensive action against the CVE-2025-378997899 ksmbd use-after-free exploit technique.
Detection signals and forensic clues to hunt for
Know what to look for. Kernel oops messages, unusual log messages from the ksmbd service, and repeated crashes tied to SMB session events are all red flags. In many cases an exploit attempt will cause instability before it succeeds, so watching for unexplained kernel panics or repeated session resets can give you an early warning.
From a forensic angle, capturing network traces that show unusual session setup and immediate logoff sequences can indicate someone probing for the exact race. If you have endpoint or kernel tracing tools in place, capture the sequence of calls around session logoff and check for unexpected frees or use of freed pointers. Hunting with concrete indicators improves odds of catching an attempted CVE-2025-37899 ksmbd use-after-free exploit technique in the wild.
How adversaries might weaponize this in real attacks
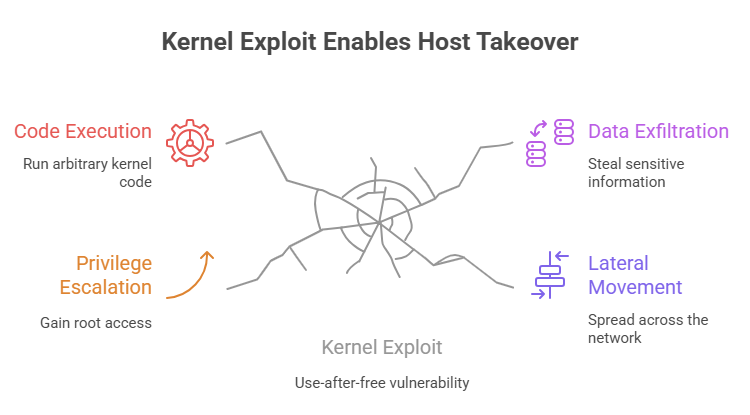
An attacker who converts this bug into a reliable primitive can escalate privileges or run arbitrary kernel code. That opens a path to persistence, data exfiltration, or lateral movement from a compromised host. For example, a miscreant who gains low-tier access to a server through a web application could use the kernel exploit to take full control and implant backdoors that survive reboots.
Beyond single host compromise, attackers could combine the exploit with network scanning to move horizontally across a cluster that uses kernel SMB features. The CVE-2025-378997899 ksmbd use-after-free exploit technique is therefore not just a single server problem; it is a component in a larger attack lifecycle for skilled operators.
Practical hardening steps for system administrators
First, patch. Apply the vendor kernels that contain the fix. If you cannot immediately patch, limit network exposure for SMB services and use host-based firewall rules to prevent untrusted access. Consider disabling in-kernel SMB support in favor of user space SMB servers if that fits your environment.
Second, add monitoring around SMB session lifecycles. Track session setup and teardown patterns and alert on anomalies. Third, keep memory protection features enabled on your kernels and apply allocator hardening patches where available. These steps together reduce the window of opportunity for the CVE-2025-378997899 ksmbd use-after-free exploit technique and similar vulnerabilities.
Responsible disclosure and the timeline of fixes
The process that led to this public advisory followed standard disclosure practice. The researcher reported the issue, maintainers produced a fix, and public entries were created describing the problem and the remediation. That chain allowed distributions to prepare patches before wide public attention made exploitation more likely.
Timelines matter because they give defenders time to test patches. If you saw the first public mentions and have not patched, act quickly. The official records show the fix and point to the kernel commits you can review. That transparency is helpful for teams who want to understand exactly what changed.
Final takeaway and what to do right now
This is a technical vulnerability with big implications. The CVE-2025-378997899 ksmbd use-after-free exploit technique is a reminder that small code mistakes in complex, stateful subsystems can escalate into significant risks. The research around allocator amplification means do not discount a bug because it looks minor on paper.
Actionable next steps are simple. Check for vendor advisories, schedule kernel updates, and if needed, restrict SMB access to trusted networks only. Add monitoring around session creation and logoff activity, and review any historical kernel oopses tied to SMB. Treat this as a priority, not an academic curiosity. Patch and verify, and then breathe a little easier.
CVE-2025-37899 ksmbd use-after-free exploit technique underlines why strong defenses are critical. Hoplon Infosec’s Endpoint Security service helps block such kernel-level attacks, keeping systems resilient and secure.
Follow us on X (Twitter) and LinkedIn for more cybersecurity news and updates. Stay connected on YouTube, Facebook, and Instagram as well.
Share this :