Libraesva Vulnerability Alert 2025: Protect Email Security

Hoplon InfoSec
24 Sep, 2025
Libraesva vulnerability
There is a small, ugly crack that you need to worry about if your company uses an email gateway to stop phishing and malware. A problem that was just made public in a popular email appliance can let one carefully crafted email do more than just annoy users. Some hackers are already using that hole in the gateway to run commands inside it. This short piece talks about what happened, why it matters, and what you can do about it right now.
This isn’t just a theory. The flaw is called CVE-2025-59689, and it is a command injection bug in the Libraesva Email Security Gateway. The vendor put out an advisory and a list of fixes and patched versions for vendors and trackers.
Why this story is important right now
Email gateways are in front of business mailboxes. They get rid of spam, unpack attachments, and clean up active content. If a gateway is weak, that protective layer doesn’t just filter traffic; it also lets people into the network. Imagine a locked front door that suddenly lets someone change the lock from a mailbox slot.
People have seen this specific Libraesva vulnerability in real attacks. Reports show that skilled, well-resourced actors can use exploitation scenarios. That means this is more important than a normal Patch Tuesday.
The flaw in simple terms
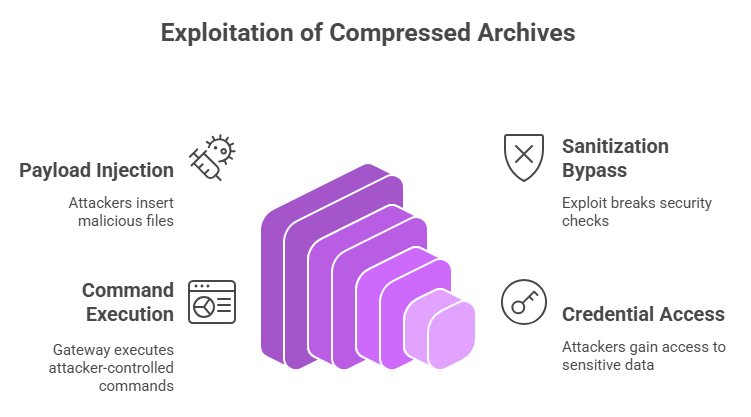
The main issue is cleaning up the input. When the product checks compressed attachments, it tries to get rid of any active code that is inside of files. You can fool that step. An attacker makes an archive that causes the gateway to misread the file names or contents, which causes it to run shell commands as a user with no privileges.
In short, one bad compressed file can make the gateway run commands. That’s what “command injection” means, and it’s exactly what the Libraesva advisory and the national vulnerability databases say is a problem.
How attackers use compressed files to get into systems
Attackers like compressed archives because they can hide a lot of files and change how they are set up. In this case, the exploit puts payload files in the archive in a way that breaks the sanitization logic. The gateway then does things like shell calls or other command-level interactions, and the attacker’s data makes those calls include content that the attacker controls.
Once an attacker runs a command on the appliance, even if they are not the root user, they can often list credentials, read cached email, and move to other services that the gateway connects to. If a company treats its email gateway like a trusted network neighbor, the effects are very bad.
Proof of state-sponsored abuse
Several security outlets and vendor notices say that the flaw has been used in targeted campaigns and that the people behind them seem to be state-backed or very skilled groups. People say that attack patterns, infrastructure reuse, and the fact that targets are chosen carefully are more likely to be signs than random spam runs.
That doesn’t mean that every case we’ve seen so far is a big breach. It does mean that defenders should expect a higher level of skill and act quickly, since state-sponsored actors tend to be patient and sneaky.
Who is in the most danger?
Many small and medium-sized businesses and large businesses use the device. If an organization has a Libraesva Email Security Gateway that is open to the public and is using software that is known to be vulnerable, it could be in danger. Managed service providers (MSPs) and hosting companies that host many instances are especially at risk because a single successful exploit can affect many customers.
When you think about exposure, don’t just think about the gateway itself. Also think about the people and services that support it, such as admin consoles, backup systems, integrated mail systems like Microsoft 365 or Google Workspace, and logging endpoints.
Timeline: finding, telling, and fixing
The vendor put out a notice about a command injection flaw and gave out fixed builds for a number of supported versions. The problem has been given the CVE-2025-59689 number in national vulnerability databases, and several security sites reported that it was being actively exploited soon after the advisory.
In real life, that order meant that defenders only had a short amount of time to react between the first reports of exploitation and the release of fixes. The good news is that specific patch builds were released. The bad news is that a lot of companies are still behind on applying updates.
A technical deep dive for readers who want to know more
Here is the practical anatomy if you like the mechanics. The gateway gets an email attachment that has been zipped up. It extracts files and runs sanitization routines that are supposed to get rid of active content while it is processing.
The step that cleans things up calls on utilities that work with compressed formats and file metadata. A specially made archive with altered filenames or metadata makes the sanitization routine create a command line that has tokens that the attacker can control. The shell interprets those tokens and runs any command it wants.
This kind of flaw is bad because the attack looks like normal archive processing, and the exploit surface is something that happens a lot. The best way to fix it is to get vendor updates, which make careful changes to how inputs are checked and how subprocesses are called.
Versions that are affected and fixes that are available
The vendor advisory and tracking databases say that versions 4.5 and up to some 5.x builds were affected. Libraesva put out patches and small fixes for a number of supported branches. Administrators should read the vendor’s advice and use the patched builds that are appropriate for their version of the software.
If you can’t apply the patch right away, it’s best to isolate the appliance and use temporary fixes until you can. The vendor tells you which builds were fixed and the exact version numbers to look for.
How to tell if you were the target
There are a few useful signs to look for. You should look for strange process calls on the gateway, outbound connections you don’t recognize, new user accounts or cron jobs, or changes to configuration files that happen all of a sudden. Log entries that show failed or suspicious attempts to unpack archives are a warning sign.
You can also see lateral movement by looking at endpoint and network telemetry from the gateway to back-end services. If you have configuration snapshots or file integrity monitoring, look at the most recent changes and see how they compare. Take a cautious approach: if anything seems off around the time you got strange emails, look into it.
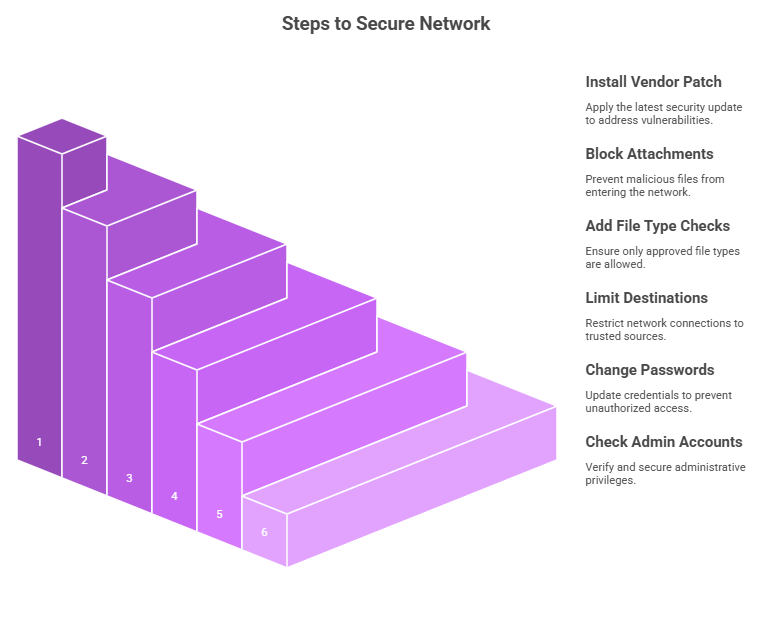
Steps admins can take right away to fix the problem
First, as soon as you can, install the vendor patch for your version. If you can’t patch right away, think about these temporary steps:At the gateway, block or quarantine all compressed attachments, add strict file type checks, and only let the gateway connect to approved destinations on the network.
You should also change the passwords for any service accounts that the gateway can access and check the admin accounts. Even though the exploit runs as a non-privileged user, it may still be able to see credentials that are stored or cached nearby.
A playbook for SOCs on how to respond to an incident
If you find that a gateway has been hacked, treat it like an umbrella incident. Isolate the appliance from the network to contain it, and then collect memory images, configuration backups, and logs to keep forensic evidence. Email systems often connect to a lot of different services, so make sure you know how all of them work together before making big changes.
After containment, use known-clean backups or rebuilt appliances to get rid of the problem and get things back to normal. Check by playing back test messages and making sure that the expected logs and alerts are there. Finally, hold a lessons-learned session to update playbooks and patching procedures.
Long-term protection for email gateways
Patching isn’t enough. Design the system so that the gateway can’t access any internal services that it doesn’t need to. Give the gateway only the network access it needs and use strong segmentation. Instead of using shell interpretation, use safer APIs to make subprocess calls within the product safe from injection.
Only let trusted partners manage your third-party accounts, and make sure that admins use multi-factor authentication to get in. Check and test those controls on a regular basis, such as with tabletop exercises or red-team engagements.
What companies should teach their end users
Users should be wary of compressed files from unknown senders because the first vector is an email attachment. Teach your employees to check with the sender through a different channel before opening attachments that seem suspicious. Make reporting easy: a single click to flag an email for investigation is more effective than a talk about security.
Users should also learn how to quickly report strange behavior in apps. Analysts often find early-stage campaigns with the help of small hints from non-technical staff.
Wider effects on trust and the supply chain
This event is another reminder that the safety of one vendor can put the whole system at risk. When a lot of businesses rely on the same gateway, a weakness can become a supply chain risk. When looking at vendors, procurement teams should think about secure development lifecycle practices and open disclosure processes.
These trends are also being watched by regulators and insurance companies.
Expect more attention to vendor risk management and maybe even contract clauses that deal with how to handle incidents.
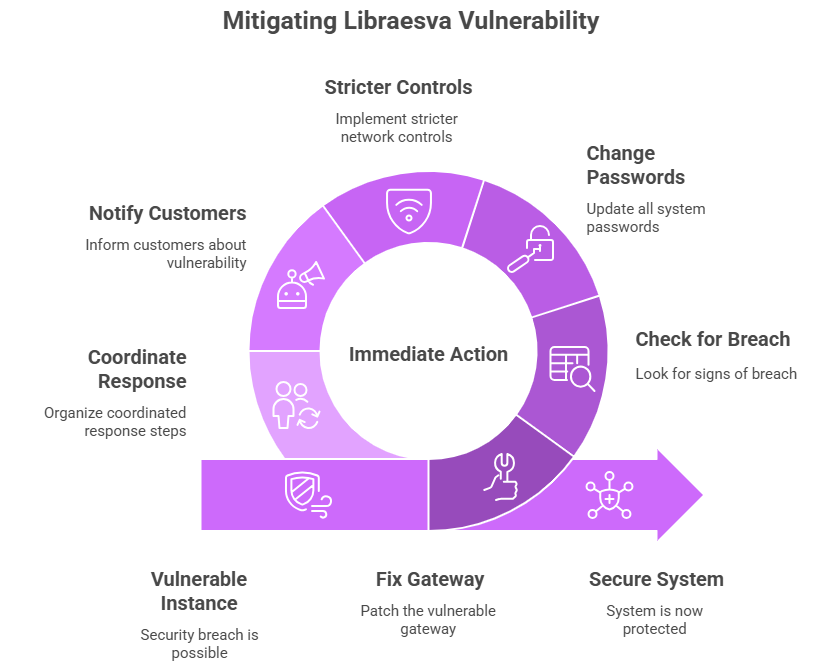
A useful checklist and a final thought
If you run an affected instance, do something right away. Fix the gateway, look for signs of a breach, change passwords, and make network controls stricter. For MSPs and hosts, making sure that customers are notified and that response steps are coordinated should be the top priority.
In short, think of the Libraesva vulnerability as a real threat that you can do something about. It shows that a small parsing bug can make a big hole in security when it is in a trusted, important appliance. A mix of timely patching, good network hygiene, and the habit of questioning unexpected emails is the best defense.
Hoplon Infosec’s Penetration Testing Services uncover vulnerabilities like those in Libraesva ESG before attackers exploit them, helping organizations strengthen defenses against advanced threats.
Follow us on X (Twitter) and LinkedIn for more cybersecurity news and updates. Stay connected on YouTube, Facebook, and Instagram as well. At Hoplon Infosec, we’re committed to securing your digital world.
Share this :