Lite XL Text Editor Vulnerability 2025: Hidden Risk Exposed
-20251113051404.webp&w=3840&q=75)
Hoplon InfoSec
13 Nov, 2025
If you use the lightweight code editor Lite XL (often described as a “lite text editor” or “lite xl editor”), you might think you’re safe simply because it’s minimal, fast, and streamlined. But a newly disclosed vulnerability in this code editor turns that assumption upside-down.
The flaw allows attackers to execute arbitrary code on systems where Lite XL is installed, even if you open what looks like a harmless project directory. In this article, I’ll walk you through how this happens, tie it into how modern text editors and code editors operate, and explain what you should do (and what to avoid) to stay secure.
The Background: What is Lite, XL, and why do people use it
The software “lite xl text editor” is a modern fork of the earlier “lite” project, often called simply “lite xl” or “lite-xl editor.” It is designed to be a very lightweight, fast, and hackable text editor (or code editor) that runs on Windows, Linux, and macOS.
Compared to some of the heavier full-IDE environments or “examples of text editors” such as Visual Studio Code or Sublime Text, Lite XL is intended to keep things simple: you get a “lite text editor” environment, minimal dependencies, and speed. As the site puts it: “Fast, Lightweight and Powerful Text-Editing Experience.”
In lists of text editors, you’ll find Lite XL alongside other tools, but its appeal is that it focuses on being the Lite XL code editor,” not a full IDE, but rather a nimble environment for writing and editing code or text.
Because many developers favour a minimal environment, or want cross-platform portability, tools like Lite XL (and other “lite text editor” options) populate the market of “list of text editors” beyond the mainstream.
Given this context, it’s no wonder many people use it for quick edits, a small code base, or as a general-purpose “editor”.
-20251113051405.webp)
The Vulnerability: What’s wrong with the Lite XL text editor
Earlier this month, security researchers discovered serious flaws in the Lite XL editor that allow arbitrary code execution.
What the vulnerabilities are
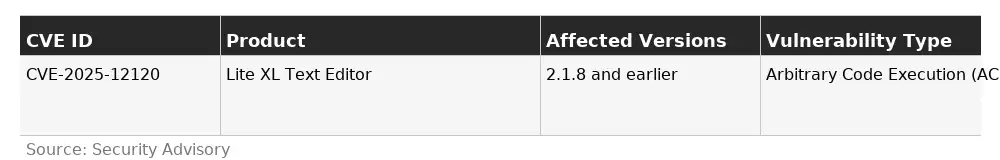
There are two distinct but related vulnerabilities in Lite XL (versions 2.1.8 and prior):
· CVE-2025-12120: When a user opens a project directory in the Lite XL editor, a file named .lite_project.lua It is automatically executed without asking for user confirmation. Because that file can contain arbitrary Lua code, an attacker could craft a malicious project directory, have you open it, and trigger arbitrary code execution with the privileges of the Lite XL process
· CVE-2025-12121: Lite XL contains a legacy function system.exec that builds and executes shell commands without proper sanitization. This appears in various parts of the code (such as project launching, drag-and-drop file handling, and the tree view plugin). An attacker who can influence inputs system.exec might execute arbitrary shell commands on the host.
Why this matters
For those using the Lite text editor or the Lite XL editor, especially in environments where you open many external projects or pull code from repositories, this is a serious risk. You might think you’re simply “opening a project” in your editor. But if the editor automatically runs code on opening, then simply trusting a repository or project folder without inspection could lead to compromise.
In other words, just because you assume the “list of text editors” you use is safe doesn’t mean the “Lite XL code editor” you chose is exempt from security issues.
Because the vulnerability is arbitrary code execution (ACE), effectively letting an attacker run whatever code they like in your context, the potential for data theft, malware installation, or worse is high.
And because Lite Xl is hackable, scriptable (via Lua), and used by people who often open unknown or third-party code, the attack surface is real.
-20251113051406.webp)
How the attack could work in real life
Let me paint a scenario. You download a git repository from someone on GitHub (or via some shared link). You decide to open it in your favourite “lite text editor” or “lite XL editor”.
Inside that project directory, there's a file named .lite_project.lua. Normally,y you might think it’s a harmless config, maybe sets up compile commands, plugin settings, etc. But thanks to the vulnerability CVE-2025-12120, the editor opens that file and executes it immediately, without askingDodo you trust this file?”. The attacker inserted malicious Lua code there, perhaps retrieving sensitive data, spawning a shell, altering files, etc.
Meanwhile, the second vulnerability makes it worse: even if that file doesn’t contain the payload, if the project allows drag-and-drop or “open in system” via plugin treeview, if an attacker influences the path or data, they might exploit system.exec to send shell commands like rm -rf /, or install backdoors, etc.
Because this happens in a “lite” or “lightweight” environment that you picked for ease, you may not have applied the same security mindset you’d use for a full IDE. That’s exactly what the attacker is counting on.
S: Using the Lite XL code editor means you must be aware that even minimal editors can still open major security holes.
What you should do right now
If you use Lite XL (or “lite xl editor”/“lite text editor”), here are practical steps.
1. Update immediately to the latest patched version (i.e., remove or avoid versions ≤ 2.1.8) because those are affected by both CVE-2025-12120 and CVE-2025-12121.
2. Avoid opening untrusted project directories with Lite XL until you are confident the .lite_project.lua file (or similar config) is safe. Think of opening a project as being nearly equivalent to running code.
3. Inspect.lite_projectt.lua files manually (or restrict their execution) if you must open external projects. If you’re in a corporate environment, consider applying a policy restricting such files.
4. Run the editor with the least privileges possible. If you normally run with elevated rights, consider downgrading. Because arbitrary code execution then has more impact.
5. Monitor plugins and extensions you install, since Lite XL is hackable and scriptable, malicious or compromised plugins may also exploit these paths.
6. Consider alternative editors temporarily if you cannot patch immediately. In your “list of text editors”, you might choose one that has audited behaviour and fewer “execute-on-open” risks. But note: every editor has potential risks, so staying updated matters most.
7. Educate your team or developer peers: Many folks assume “lightweight editor = less risk,” but this shows you still need standard security hygiene.
-20251113051407.webp)
Why this issue happened (and what it teaches us)
In the world of examples of text editors and lists of text editors, we often focus on features (speed, plugin ecosystem, language support) and forget about security. The Lite XL editor was designed with hackability and simplicity (via Lua scripts) in mind. That made it easy for users to extend it, but this same flexibility becomes a vector for attack.
The automatic execution of .lite_project.lua It is convenient (you open a project, and it sets itself up), but from a security standpoint, it is risky. There was no prompt or “are you sure” step. Combine that with legacy functions system.exec that don’t sanitise inputs, and you have a perfect storm.
This teaches a broader lesson: even in so-called “lite” tools, you can get “heavy” risks if the design allows execution of code without user consent. The “lightweight” nature doesn’t equal “risk-free”.
Also note: in modern times, with many projects coming from GitHub or shared drives, many “unknown” project folders end up being opened locally. Editors that treat a folder as a “project” and run scripts inside it by default are inherently risk-prone unless designed carefully. This helps us understand why the lite text editor in this case was vulnerable.
How does this compare to other “text editors”
If you look at a “list of text editors”, you’ll find many options: large IDEs, full-blown code editors, and lightweight editors like Lite XL. For instance: Visual Studio Code, Sublime Text, Notepad++, or minimal editors like nano, vim, or Lite XL. Each has trade-offs.
In the case of the Lite XL code editor, its strength is being lightweight and hackable. Its weakness turned out to be that hackability plus convenience introduced risk. By contrast, some heavier editors might not automatically execute project files or might sandbox more.
It’s a real-world case that using a “lite text editor” does not mean you can ignore security. Also, users switching to “lightweight” editors for speed still need to watch for security-relevant features such as plugins, scripts, or automatic project-loading behaviours.
Take-Away: what to remember
· The Lite XL text editor vulnerability shows that even lightweight, easy-to-use editors can be exploited if they automatically execute project code or use unsanitised shell functions.
· If you use the lite-xl editor, update it immediately and treat project folders as potential risks rather than innocent containers.
· In your personal or team workflow, ensure that tools listed in your “examples of text editors” or “list of text editors” are audited not only for features but for security posture.
· Always apply the principle of least privilege and privilege separation when running code editors, even those you trust.
· Finally, think of your editor as part of your security surface. The lightweight editor you picked for convenience can still be the entry point for compromise.
Frequently Asked Questions (FAQ)
Q 1: Does this vulnerability affect all versions of Lite XL?
Yes, the disclosed issues (CVE-2025-12120 and CVE-2025-12121) affect Lite XL versions 2.1.8 and earlier. If you’re using a version beyond that which includes the fixes (trust guard for project modules, removal of legacy exec), you are in better shape.
Q 2: I open project folders in various editors. Amm I safe if I switch from Lite XL?
Switching helps, but you still need to verify how your chosen editor handles project-config files and whether it can automatically run code. Many code editors have plugin systems or allow scripting and thus carry risk. The key is to understand how they treat external project directories and config scripts.
Q 3: What if I already opened a malicious project with Lite XL?
If you opened it before patching, the attacker may already have run code with the privileges of your editor process. You should assume the system might be compromised: run full security scans, change passwords, check for unusual processes or persistence mechanisms, and update to patched software immediately.
Q 4: How does this compare to “remote code execution” or “arbitrary code execution”?
This is a clear instance of arbitrary code execution, meaning the attacker can run code of their choice in your context. If the editor opens a project from a remote source (GitHub, shared drive) and then executes code without a prompt, it may also become remote code execution if the attacker controls the project source. See definitions of arbitrary code execution for context.
My personal reflection
I’ve used lightweight editors for years, often favouring speed and minimalism. Ironically, one of those (the lite text editor environment) became a vector for serious risk. It reminds me that the trade-off for “light” is often “less built-in safety” and more reliance on the user to make correct choices.
In my work, I’ll now treat any “project open” operation in an editor as a potential risk zone: “OK, what is this .lite_project.lua doing? Is this plugin safe? Did I get this from a trusted source?” Those questions may feel heavy for an editor that’s supposed to be “lightweight”, but the vulnerability proves they matter.
If you’re a professional or hobby developer using Lite XL or any other editor in your “list of text editors”, updating software and watching how you open external code bases will go a long way toward staying safe.
Final word
The vulnerability in the Lite XL text editor is a vivid example that even minimal, blazingly fast editors are not immune to major security issues. It underscores that in the realm of code editors, “lightweight” is no excuse for laxness. If you use Lite XL (or plan to), update now, treat unknown projects as potential threats, and apply best-practice hygiene. Remember: a simple “open” action in a text editor might actually be a run action in disguise.
Stay safe, keep your tools updated, and treat your editor as more than just a productivity engine; treat it as security-sensitive software, too.
Author: Hoplon Infosec
Bio: Security enthusiast with over 10 years in mobile cybersecurity. Connect with me on LinkedIn.
Address: 1415 W 22nd St Tower Floor, Oak Brook, IL 60523, United States
Phone: +1 773-904-313 , Contact: [email protected]
About/Privacy: At Hoplon Infosec, we provide expert insights into cybersecurity. Our editorial policy: all articles are written by in-house specialists or thoroughly reviewed by them to ensure accuracy, credibility, and up-to-date information.
Share this :