From Fear to Justice: How the LockerGoga, MegaCortex and Nefilim Admin Was Finally Caught

Hoplon InfoSec
11 Sep, 2025
LockerGoga MegaCortex Nefilim arrest
The news hit like a sudden change in the weather in an already stormy digital world: headlines screamed about the arrest of the LockerGoga MegaCortex Nefilim, and business owners, hospital workers, and factory workers all felt an old fear come back. This story isn’t just about one name in a court document. It’s about a series of attacks that kept changing and investigators finally finding links that seemed impossible to find.
You don’t have to be a security expert to care. When power plants, hospitals, or factories can’t get to their files, the cost isn’t just a number on a balance sheet. It means that operations break down, IT teams have to work extra hours, and sometimes important services are interrupted for customers or patients. The human and economic touch is what makes the LockerGoga MegaCortex Nefilim arrest important to everyone.
A brief overview of the arrest
In short, prosecutors say that one person was in charge of several ransomware strains that hit hundreds of targets. The indictment that prosecutors made public names the accused administrator and links him to organized extortion campaigns that happen all over the world. These aren’t the break-ins that happen once in a while. This is a criminal business that worked together for a long time.
The news used language that law enforcement is used to, like “indictments,” “extradition,” “international cooperation,” and “rewards for information.” For defenders, it was both a relief and a warning. It’s normal to celebrate the success of trackers, but the criminals’ methods change quickly, and the arrest is just one chapter in a long, ongoing fight.
What LockerGoga, MegaCortex, and Nefilim Are
All of these names are for groups of ransomware that became well-known for being able to lock networks and ask for money. LockerGoga became well-known after attacks on big companies. MegaCortex showed up as a version made for big business settings. Nefilim was a rent-a-toolkit that affiliates could use, and it was often provided through an online control panel.
The three of them together show different phases and business models in the world of ransomware: direct destructive attacks, targeted enterprise strikes, and a service model that made the core developers’ work reach more people. That variety let the supposed operator change course when one strain stopped working or when defenders found ways to decrypt older versions.
Well-Known Incidents and Victims
Some of the attacks that were linked to these families affected well-known people and big businesses. One well-known LockerGoga campaign brought a global aluminum company to its knees, forcing it to do things by hand and make public statements about how it was getting better. People have blamed MegaCortex for complicated attacks on business backup systems that made it harder for victims to recover.
The indictment and news stories show that there are hundreds of victims in the US and many more in other countries. The scale is big. Hundreds of businesses, from factories to hospitals, were affected by the chaos and the need to respond quickly to the crisis. The legal filings seem less abstract and more important because of these human stories.
The campaign’s timeline
The supposed activity has been going on for a long time. The first campaigns that used LockerGoga and MegaCortex were mostly in 2019 and 2020. After that, the actor changed and was linked to Nefilim until 2021. Attackers changed their tools as defenders learned how to stop older versions.
That pattern is common in cybercrime. When defenders release decryption tools or police break up an affiliate network, the developers either change the code, give it a new name, or switch to a service model. The timeline for these three families shows that they adapted and kept going, not just one big event.
How the Investigation Went
Modern cyber investigations often use a mix of different types of information, such as network telemetry, open-source clues, cryptocurrency traces, and cooperation between agencies. In this case, prosecutors say that law enforcement used a mix of methods, such as following the money used to pay the ransom, looking at the binaries used to spread the ransomware, and following the infrastructure used to deliver malware.
It doesn’t happen overnight that those leads come together. They are the result of analysts putting together logs, sharing information from the private sector, and sometimes doing old-fashioned work like interviews and working with hosting providers. A public indictment means that investigators think they have enough evidence to take the case to court.
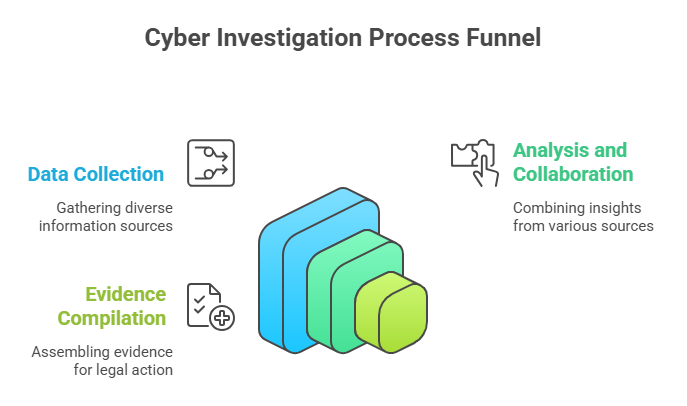
Information about the arrest and indictment
The federal court unsealed an indictment that names a Ukrainian national who is accused of running several ransomware operations. It also lists criminal charges related to extortion and intentionally damaging protected computers. Prosecutors say the defendant gave ransomware to affiliates and helped plan attacks that cost millions of dollars.
The filing goes into detail about the time frames, number of victims, and ways the attackers got in. It also serves as a reminder that modern cyber prosecutions depend a lot on people working together across borders. An indictment is a formal charge, but the paper trail and the public release of evidence are meant to let victims and possible informants know that the police are actively looking for leads
Reward, fugitive status, and international alerts
The person named in the indictment is not in U.S. custody right now, so the Justice Department and the State Department put out reward notices to get people to come forward with information. The government made a public offer of millions of dollars for information that leads to an arrest and conviction. When the suspect is found overseas, that financial incentive is often used with diplomatic pressure to get them to come back.
Rewards are a simple but useful tool. They send a message that the case is very important and that they can get witnesses who don’t want to come forward to do so. International alerts and red flags sent to banks and crypto exchanges can also make it harder for criminals to cash out money they got illegally.
How the Ransomware Worked on a Technical Level
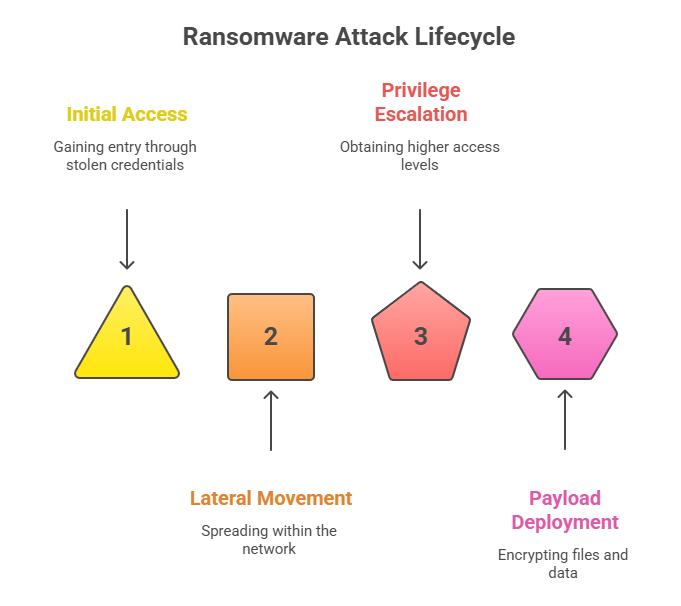
Prosecutors and researchers talk about a technical process that starts with getting initial access, which is often done by using stolen credentials or exposing services. This is followed by lateral movement, privilege escalation, and finally the deployment of an encrypting payload. The ransomware was often changed for each victim so that the keys to decrypt it were different for each case.
Customization made sense in a cruel way. By customizing encryption for each victim, the criminals made a single leaked key less valuable and gave people another reason to pay. Attackers sometimes used file encryption along with threats to publish private information, which put even more pressure on victims who were worried about the damage to their reputation and the law.
The Ransomware-as-a-Service Model and Economics
Nefilim and other similar strains worked with an affiliate economy. Developers gave affiliates the tools and a control panel, and affiliates did the work of breaking into networks and negotiating ransoms. The developers then took a cut of the ransom payments, which was usually between 15 and 30 percent. This model made it possible to specialize and grow.
From a criminal business point of view, it worked well. While affiliates took care of intrusion and negotiation, a developer could focus on coding resilient payloads. That division of labor made it harder for police to find one person responsible, because roles were split up and profits were sent through middlemen and mixing services.
The No More Ransom Project and efforts to decrypt
Sometimes, when defenders and law enforcement worked together, they were able to beat the criminals to the punch. In a previous international effort related to these ransomware families, a volunteer group that helps victims get back encrypted files made decryption keys for some LockerGoga and MegaCortex infections available to the public. That intervention kept a lot of organizations from having to pay.
Projects like that, led by the community, show that working together really does work. They also reveal an uncomfortable truth: making backups and reporting intrusions quickly can mean the difference between a quick recovery and a long, expensive business interruption.
What This Means for Business Defenses
The arrest and charges are a warning and a lesson. Ransomware is not just an IT problem for businesses. It is a business risk that affects HR, operations, communications, and the law. Not just a sysadmin checklist, but also board-level talks should include investing in segmentation, immutable backups, and tabletop exercises.
A second lesson is how important it is to report things quickly. When victims tell the police and share technical indicators early, those tips can help solve bigger crimes. Defenders need to learn how to make the time between an intrusion and deployment shorter.
Legal, Policy, and International Consequences
These cases set a precedent for future cases. They show that working together across borders can lead to charges and public rewards. They also add to the debate about whether to treat ransomware payments differently, make it harder to get into cryptocurrency, or spend money on building up global cyber capacity.
At the same time, prosecutions aren’t a quick fix. Extradition is still politically difficult because laws are different in each country. Still, showing that operators can be found, charged, and pursued makes it more expensive for cybercriminals to do business.
Things Businesses Should Do Right Now
To begin, act as if you are a target and see if your company has the basics: air-gapped or otherwise isolated backups that have been tested, multifactor authentication for privileged accounts, and network segmentation between critical systems and general user environments. Practice your incident response plan on a regular basis. It should include legal advice and communication.
In addition to the technical checklist, get to know outside incident response companies and local law enforcement contacts. It’s easier to call a number you already know than to frantically look for help when you’re under attack. When the clock starts ticking, all of those human and contractual preparations pay off big time.
Questions that people ask a lot
1. What does the arrest of LockerGoga, MegaCortex, and Nefilim mean?
This arrest shows that even skilled ransomware criminals can be found and charged. These types of ransomware hurt hundreds of businesses around the world and cost them millions of dollars. The authorities sent a message by charging the administrator that international cooperation and persistence can break up even the most organized cybercrime networks.
2. What were the steps that LockerGoga, MegaCortex, and Nefilim ransomware took?
These strains used strong encryption to lock files and networks and then asked for money in exchange for the keys to unlock them. They often broke into networks, turned off backups, and threatened to leak stolen data in order to get at big companies. Nefilim, for example, used an affiliate model where developers made tools and affiliates did the attacks, splitting the money they made from the ransom.
3. How can businesses keep themselves safe from ransomware like LockerGoga or Nefilim?
Layered security is the best way to protect yourself. Companies should keep backups that can’t be changed offline, use multifactor authentication, quickly patch systems, and separate networks. Regular drills for responding to incidents and reporting suspicious activity right away can help limit damage. Working with law enforcement and security vendors also makes you more resistant to new types of ransomware.
Main Points
The arrest of LockerGoga, MegaCortex, and Nefilim is a hard-won victory in an unfair fight. It shows that careful investigation, cooperation between the public and private sectors, and pressure from other countries can expose complicated criminal activities. But it also shows that the enemy changes quickly and will keep doing so.
The lesson for businesses is both simple and hard to hear. Now is the time to build resilience, practice your response, and see ransomware as a strategic risk. The news about the law will come and go, but making systems and people stronger is what keeps today’s news from becoming tomorrow’s crisis.
The LockerGoga MegaCortex Nefilim arrest is a reminder that ransomware remains a real risk. Hoplon Infosec’s Endpoint Security solutions help organizations detect and stop such threats before they spread, keeping business operations safe and resilient.
Follow us on X (Twitter) and LinkedIn for more cybersecurity news and updates. Stay connected on YouTube, Facebook, and Instagram as well. At Hoplon Infosec, we’re committed to securing your digital world.
Share this :