Deadly macOS Homebrew Fake Websites Putting Users at Risk
Hoplon InfoSec
14 Oct, 2025
You could be working on a side project or adding a library to your Mac. You type "Homebrew install macOS" into your search engine, click on a page that appears like it would work, copy a command, and then paste it into Terminal. Your system gets stealthily hacked a few minutes later. That's the danger of using bogus macOS Homebrew websites.
The fact that this attack is so covert is what makes it so startling. It doesn't need a major hole in the operating system. It leverages something you do all the time without even thinking about it: copy and paste. And it makes that into a weapon. Code is just as deadly as trust.
Why should you use Homebrew? Why now?
Many macOS users like homebrew. Many developers depend on it because it is free and simple to use. Attackers think it's worth a lot to utilize it because so many people trust it.
Some recent attempts have used Google Ads to bring consumers to links that seem like the real Homebrew page but actually take them to a phony installer site. In one of these operations, the perpetrators even made brew look like it did. The spacing and fonts are practically perfect as well.
These bogus sites trick people into clicking a "Copy" button instead of selecting the text themselves. This allows them toHomebrew. put secret commands on the clipboard. The most crucial step is that extra one. It helps the attacker disguise dangerous files in what looks like an innocuous program to install anything.
Kandji's Threat Intelligence team discovered that names like homebrewoneline[.]org resolved to an IP address mimicking brew.sh. These sites employed scripts to prevent normal copying and injected hidden malicious commands into the clipboard.
What Happened During the Attack
1. Malvertising and Domain Deception
The first piece of bait is an ad on Google. When someone types "install Homebrew" into a search engine, they will see an ad that seems authentic with the words "brew.sh." The connection will, however, take them to a false site with a tiny alteration, such as "brewe.sh."
Some security reports suggest that the rogue site utilized a cURL command to silently download malware, including the AmosStealer infostealer for macOS in one case.
2. Control of Commands and Visual Cloning
When you get to the false site, everything looks regular. Instead of the regular input box, there is a "Copy" button. This is where you would normally highlight and copy text. When you click it, JavaScript adds commands to the clipboard that you can't see.
A notify.php script on the page also keeps track of your clicks and transmits information about them back to the attacker. There are also Russian comments on the site that give advice about where to insert the payloads.
3. Getting the payload to work and getting it out
When the command copied from the fake site is executed in Terminal, it runs the genuine Homebrew installer along with a hidden malicious payload, and it also downloads and runs a secret payload at the same time. The researchers then saw base64-encoded code being downloaded, decrypted, and run.
Odyssey Stealer was one of the payloads that was being watched. It gathers cookies, browser logins, files, system information, and other data. The same infrastructure had sent the Cuckoo Stealer in other campaigns using the same tactics.
Oliver Simonnet wrote a detailed report about reverse engineering in which he talked about how a campaign he termed "Trouble Brewing" worked to decode, decrypt, and inject.
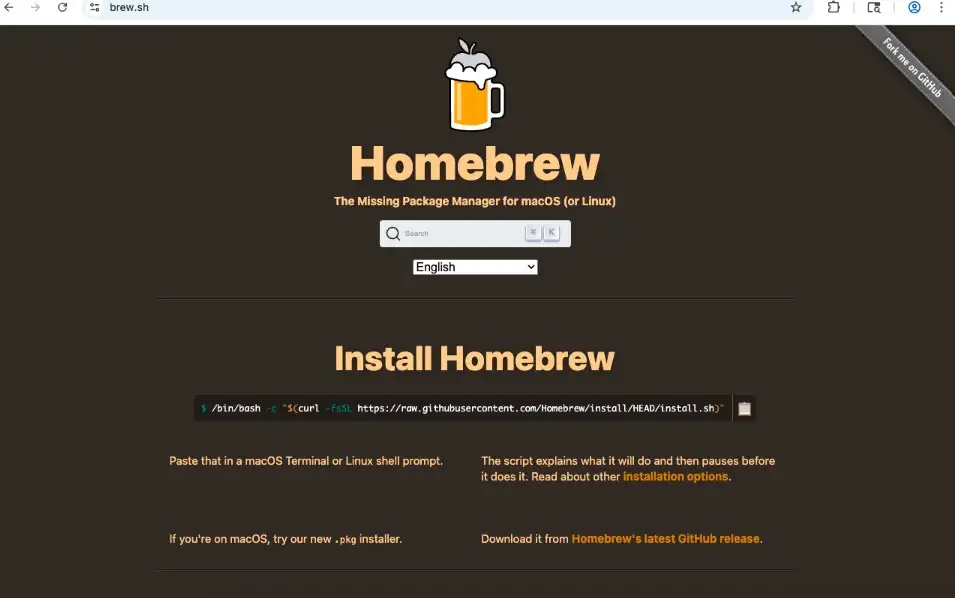
Screenshot of the real Homebrew install page.(source: the-sequence)
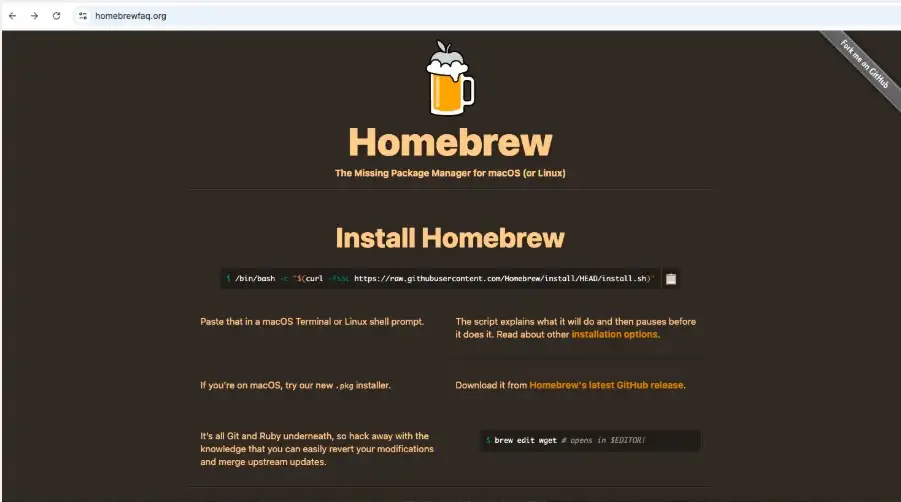
Screenshot of a spoofed Homebrew install page(source: the-sequence)
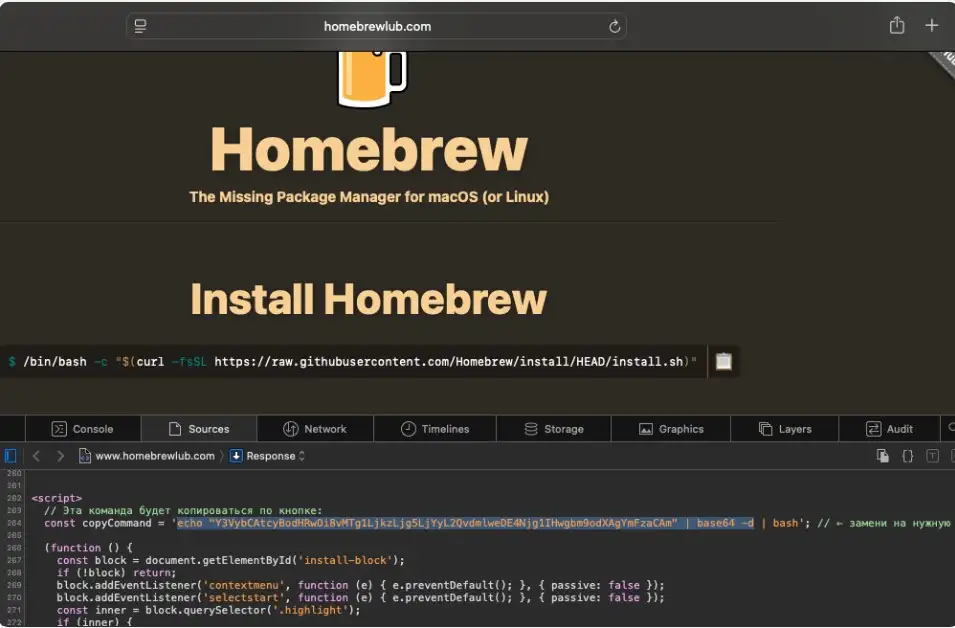
screenshot showing the malicious command injected into the page(source: the-sequence)
Why This Trick Works
It looks more like social engineering than hacking. The attacker is counting on several mistakes: • Trusting "official" styling and domain names
• Not carefully examining commands
• Using a one-click approach without thinking
• Thinking that a site that seems so wonderful must be safe
This is like how bigger cyber attacks work: they use things that individuals do without thinking. In that manner, it's like credential phishing or the leaks that happen in huge breaches. And now, phony websites for macOS Homebrew are a new way to achieve it.
What the malware does: Real Threats
Payloads like AmosStealer and Odyssey Stealer are very strong.
They can:
• Get cookies, sessions, and saved passwords from your browser
• Read entries in the Keychain
• Get files from your home folder
• Get information about your system, installed programs, and logs
• On macOS, steal passwords for crypto wallets, browser extensions, and more.
These consequences go beyond just thoughts. A developer environment that isn't safe could let access tokens, repository keys, and internal systems leak out. That's how enormous problems happen.
One article regarding security noted that the people who made the false Homebrew sites had used the same tools earlier to propagate Cuckoo Stealer. This shows that this isn't just a test; it's a long-term plan.
SecurityWeek states that a malvertising campaign drove them to brew.sh, where it suggested it would install brew but actually installed AmosStealer.
How to Stay Safe
Always look over the commands.
Don't just run a one-liner you found on a link. Check the official brew.sh or GitHub docs to make sure the command is right. Don't copy and paste anything that seems strange.
Pay close attention to the domain. Only utilize brew.sh or other trusted sources. Be careful of domains that don't change much, like homebrewoneline[.]org. Kandji noted that a lot of these kinds of domains were not good.
Stay away from ad tricks.
Don't even notice bogus Google Ads by using an ad blocker. A lot of these campaigns rely on persuading people to click on paid links.
Protect your endpoints.
Modern security tools can stop script injection, watch for odd fetches, and stop behavior that sounds suspect. CrowdStrike's Falcon, for instance, has prevented malware campaigns that were similar by utilizing the same one-line installer logic.
Teach your group.
Tell everyone on your development team about these fake installer attacks. One click can put the whole system in danger.
Be careful with IoCs.
Recent studies warn that security teams should watch out for domains that are known to be bad, payload servers, and evidence that a system has been hacked. Kandji wrote down a list of fake instructions and domains.
Problems and trends for the future
• Blacklists are less useful because attackers can quickly generate new clone domains. The payloads can alter. For example, injected scripts containing comments in Russian have been shown to have a modular structure.
• Right now, Google Ads validation isn't very good. These attacks got via ad clearance processes by acting like legitimate domains.
• Other command-line programs or package managers, in addition to Homebrew, could potentially be the target.
• As macOS becomes a bigger target, the assumption that "macOS = safe" will lose its power.
What I think and what you should remember
I have always considered that the most hazardous flaws are the ones that people cope with every day. This fake Homebrew trick shows that. Your daily routines, like copying, pasting, and trusting, are what make you weak, even though code and infrastructure are crucial.
This threat is like a digital Trojan horse in a way. You were happy to see it because you thought it was safe. Be careful, examine things twice, and remember that convenience can be a trap.
Important Advice
• Check the commands again.
Before running the copied install command, always check it against the one on the official Homebrew page.
• Check out the domain.
You can only trust brew.sh. There are bogus ones that can hurt you, such as brew.sh and homebrewoneline.org.
• Stop the advertising.
Google Ads has a lot of bogus connections to Homebrew. Blocking them stops the attack before it can do too much damage.
• Keep your system safe.
Use trusted endpoint technologies that can immediately discover threats that emanate via scripts or the clipboard.
• Teach your group.
Tell developers about bogus installation sites and how to stay away from them.
• Be careful of dodgy domains.
To stay one step ahead of emerging bogus websites, read security reports from reliable sources.
These little factors make it very hard for macOS Homebrew phony websites and other attempts that try to get consumers to lose faith to work.
Hoplon Infosec’s Endpoint Security can protect macOS users from threats like Homebrew spoofed websites. By detecting suspicious scripts, clipboard injections, and unusual activity in real time, they help prevent attacks before damage occurs.
Follow us on X (Twitter) and LinkedIn for more cybersecurity news and updates. Stay connected on YouTube, Facebook, and Instagram as well. At Hoplon Infosec, we’re committed to securing your digital world.
Share this :