macOS XCSSET Malware Variant: Firefox Clipper and Persistence Threat in 2025

Hoplon InfoSec
26 Sep, 2025
macOS XCSSET Malware Variant
I remember a morning when I drank coffee, and a friend, who was an app developer, saw a strange string in a build log and felt the little chill that every engineer dreads. This article is about that chill: a threat that is coming back and quietly hunts developer machines and browser data. This story is about a macOS threat that has gotten stronger and why anyone who makes or uses Mac apps should be worried.
What is XCSSET, and why should developers care?
XCSSET started out as a strange and targeted macOS threat that infected Xcode projects to get to developers. To put it simply, the infection model means that the code you write can have a hidden passenger.
The macOS XCSSET malware variant is more than just a pain; it’s a supply chain risk because infected projects can spread harmful code to other developers and to end users who download the compiled apps.
Researchers found that the latest version of the macOS XCSSET malware targets more than just Safari, steals crypto transfers by hijacking the clipboard, and adds stealthy persistence.
The authors probably wanted fewer noisy traces on disk and more stamina on the host by adding run-only compiled AppleScripts and obfuscation techniques. Security teams that are keeping an eye on the family have written down these changes, which show that theft is becoming quieter and more focused.
How This Variant Affects Firefox
It’s concerning that targeting is now explicitly expanding to Firefox, a browser that is popular with developers and people who care about their privacy. The macOS XCSSET malware variant now looks for cookies and artifacts from Firefox, which means it can target more people and more types of accounts.
This change makes a simple point: attackers go after people who are valuable, and Firefox users are one of those groups.
What clipboard hijacking and clipper behavior are
The clipper module is simple but works well at its core. The macOS XCSSET malware variant can keep an eye on the contents of the clipboard and change cryptocurrency addresses that are copied to addresses that the attacker controls when they are pasted.
Victims paste in what they think is their address, but the bytes have changed without anyone knowing. This is how quiet theft works: it doesn’t need to break into a system; all it needs is a trusted user to do something and a small, well-timed change
Persistence: LaunchDaemon, Scripts, and Quiet Reboot Survival
What makes an event a campaign is persistence. The newest version of the macOS XCSSET malware adds LaunchDaemon entries and other things that make it come back after a reboot and hide in legitimate flows.
Researchers saw that compiled scripts can run without any obvious triggers and that entries can pretend to be normal services. That combination makes it harder to take things out and gives people more time to steal them.
Infection Vector: What Makes Xcode Projects Dangerous
The main way to get infected is still to hack Xcode projects, which spreads the infection to forks, clones, and shared templates. The macOS XCSSET malware variant uses the build process itself to deliver its payload. This means that a naive build from a tainted repo can start the attack. This is a clear example of supply chain risk: the trusted developer workflow becomes the way to get things done.
Stealth tactics, AppleScripts, and obfuscation
More and more, the people behind this threat are using obfuscation and real tools to do their dirty work. The macOS XCSSET malware variant encodes payloads, uses base64 wrappers, and makes use of AppleScript bundles that don’t leave many obvious file footprints. Using built-in tools makes it harder to find signatures, so the defender’s job becomes finding unusual behavior and behavior changes.
Malware goes where the money is. The macOS XCSSET malware variant goes after digital wallets, saved passwords, Notes app data, and browser cookies or autofill data. With these artifacts, an attacker can rebuild sessions, send phishing emails to get multi-factor windows, or just move money to addresses they control.
A short story shows the risk: a developer sends a test link and a request for payment to a partner. They copy and paste a wallet address into the chat, not knowing that the clipboard has been switched. The transfer is done, the money is gone, and the developer is left to figure out how trust turned into theft. The macOS XCSSET malware variant makes small trust failures very expensive.
Detection: Signs of Behavior Defenders Should Look For
To find this family, you need to be able to see how the build pipeline and endpoints work. Keep an eye out for LaunchDaemon registrations that you didn’t expect, compiled scripts that you don’t know about that run when you log in, or processes that access developer folders and then go to external network endpoints.
Behavioral detections that link changes to files in project trees with outgoing connections are very helpful. Share signs of compromise with vendor tools to make it easier for the community to find them.
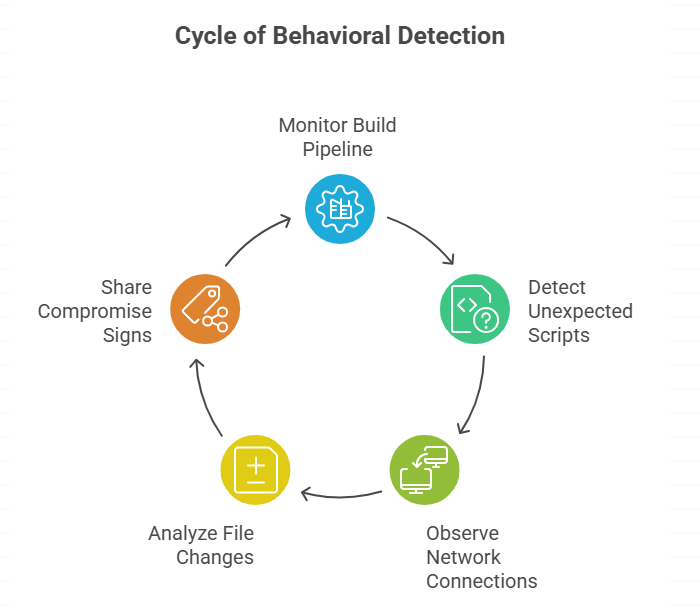
Developers and Mac users should take these short-term steps:
Check your repositories for scripts you don’t know about, look at commit histories for files that were added without permission, and don’t run build scripts that haven’t been checked.
Lock clipboard utilities, turn on system updates, and use trusted endpoint solutions that flag strange service registrations for Mac users. When you think someone might have gotten your keys or wallet address, revoke them and give them back to the person who had them.
In the long run, treat your build environment like a crown jewel. Use signed commits and releases, make code reviews required, and run automated scans that look for script injections or strange binary artifacts. Separate build machines, use temporary credentials for CI, and follow the “trust but verify” rule for any third-party code you add to a project.
What people with wallets and browsers can do right now
If you deal with crypto, make it harder for silent replacements to happen by using hardware wallets to sign, double-checking the checksums of addresses, and allowing transaction confirmations that show the destination before approval. To keep things from getting mixed up, keep your personal and development profiles separate.
The security community is responding with alerts, telemetry updates, and detection signatures, but not every problem can be fixed with a patch. The macOS XCSSET malware variant takes advantage of trust and script-based behaviors more than flaws in the operating system itself, so changes to people and processes are just as important as technical fixes. Vendors are still improving their detections and giving advice to the groups that are affected.
A Useful List for Developers and Teams
I wish someone had put this useful checklist on my friend’s desk. Don’t treat it like a religious text; treat it like a living list.
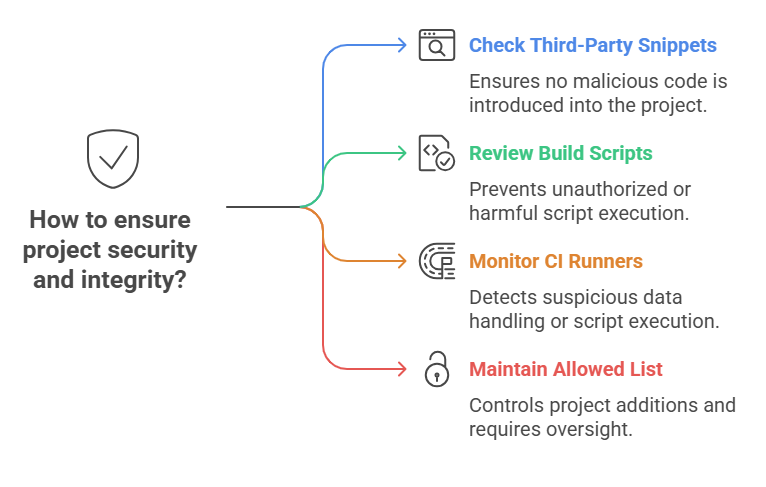
First, check every third-party snippet before adding it to a project.
Second, make sure that any build script is at least looked over before it runs, and don’t run any binaries that you don’t know about on your own computer.
Third, set up monitoring on CI runners at the process level so that any step that reads or writes data that looks like clipboard data or runs shell scripts is logged and checked. Fourth, keep a list of things that are allowed to be added to a project and require a second set of eyes on any service-like addition.
Why Supply Chain Threats Seem Different
Supply chain attacks rely on trust because they wear developer clothes and use channels that you and your team already use. The macOS XCSSET malware variant uses the same kind of psychology.
The enemy doesn’t want to attack just one workstation; they want to poison a source of truth that many people use: code. This is why you need to be extra careful with open-source projects, shared templates, and example apps. To think like a defender, you have to picture how something you trust could hurt you.
A Note on Sharing and Reporting in the Community
If you see files that look suspicious in a repository or signs that someone is messing with the clipboard on a machine, think of it as information that helps everyone. Share anonymized indicators with vendors, post details to trusted forums, and get in touch with threat intelligence teams so that everyone can benefit from better signatures and heuristics.
The sooner these signals are shared, the better vendor detections work. Often, collective action is what keeps small campaigns from turning into big outbreaks.
Finding a balance between being careful and being easy to use
One last thing: security measures have to be easy to use. Developers will find ways around your protections if they slow down development to a crawl. Make templates that are safe by default, give developers easy-to-use tools for cryptographic signing, and set up automated checks in CI pipelines so that developers get warnings as soon as possible. The goal is to encourage safe behavior without making every build a nightmare.
When I have to do something sensitive, I keep two small mental lists.
First, don’t trust the clipboard, especially when it has to do with money.
Second, if you get a sample project from the internet, you should go through it quickly line by line at least once before you start building it. These habits are easy to follow and can stop a lot of attacks that depend on people trusting them. The macOS XCSSET malware variant thrives on routine and trust,
so these small habits can make it more expensive for attackers. Because this strain uses that route to spread, you should treat every example app as if it could be infected.
The Cost to People and the Importance of Empathy
It might be easy to just make a list of protections and IOCs, but at the heart of these stories are real people who lose money, time, and sometimes their reputations. I’ve talked to developers who were embarrassed after a supply chain problem, and that stigma can make people not want to report problems. Building a culture of empathy helps.
When teams respond without blaming anyone and focus on recovery, victims are more likely to share information that will stop the next incident. Encourage open postmortems and put learning ahead of blaming others.
Habit to Practice: Slow Down When You Pay
A small habit can help: stop what you’re doing when money moves. When you copy and paste an address or confirm a transaction, look for small differences. Take an extra beat to confirm with the person you’re sending it to, and think of that pause as part of your safety protocol. Those few seconds have kept me and many others from making mistakes that could have been avoided.
Lessons learned and cautious hope
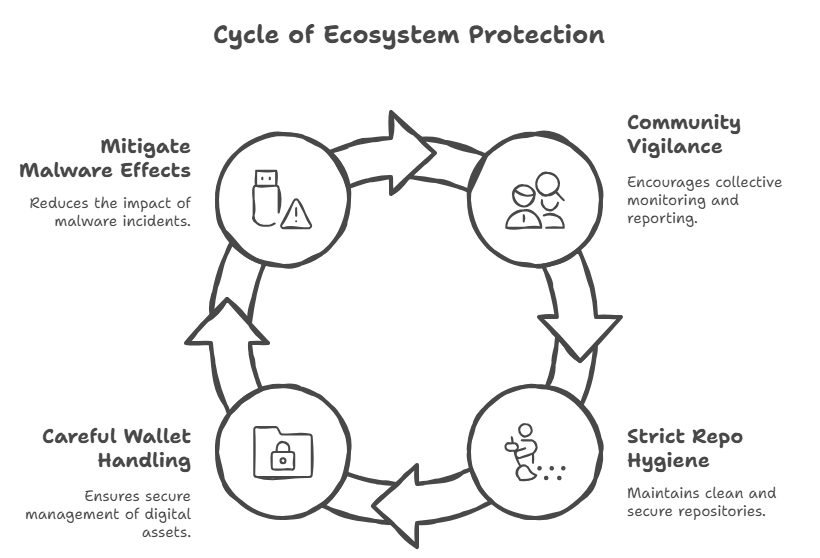
This new activity is a reminder that the ecosystem around development tools is something we need to protect. The macOS XCSSET malware variant can change, but it is not unbreakable. Community-driven vigilance, strict repo hygiene, and careful handling of wallets can lessen its effects and turn that scary morning into just one event instead of a pattern.
Final Thoughts
Handle sample projects as if they were untrusted input. Lock down the places where you build. Check the addresses of your wallets before you send them. And most importantly, tell the community what you learn so that the next suspicious log line is a story about how to avoid it instead of a story about how to feel bad about it.
Microsoft Threat Intelligence says that the newest version of the macOS XCSSET malware has advanced obfuscation, clipboard hijacking, and persistence mechanisms. It targets Firefox and steals crypto transactions.
Hoplon Infosec can help organizations defend against threats like the macOS XCSSET malware variant through advanced Endpoint Security solutions
Follow us on X (Twitter) and LinkedIn for more cybersecurity news and updates. Stay connected on YouTube, Facebook, and Instagram as well. At Hoplon Infosec, we’re committed to securing your digital world.
Share this :