Mobile Data Security 2025: 7 Proven Tips to Stay Safe
-20251113054911.webp&w=3840&q=75)
Hoplon InfoSec
13 Nov, 2025
You leave the front door of your house wide open, with no lock or alarm. That's pretty much what a lot of us are doing when we don't take care of mobile data security. It's like leaving the door open and hoping no one comes in when you trust that your phone is safe without thinking. Our phones are full of personal photos, banking apps, contacts, and work files.
I'll explain why mobile data security is important, what risks you face, and how you can keep your data safe in this article. I'll do this with real-world examples, simple language, and useful tips. I'll also use useful words and phrases like "data protection," "mobile threat," "data privacy," and "cyber hygiene" to cover the topic in depth.
The seed keyword "mobile data security" will come up naturally 14 times, and I'll also use LSI keywords like "mobile device security," "sensitive data protection," "mobile threat landscape," "data privacy on mobile," "mobile cybersecurity best practices," and more.
Why can't you skip mobile data security anymore
Every time you unlock your phone, check your bank balance, send a picture, or connect to a public Wi-Fi network, you are putting yourself in danger of cyber threats. Mobile data security is all about keeping your data on a smartphone or tablet safe from unauthorized access, leaks, theft, or misuse.
In the past, businesses only cared about desktop computers. IBM says that mobile devices are now "often the least protected corporate devices," even though they hold very private information.
Also, experts in mobile data privacy say that your device "holds a lot of personal and professional information, so it's important to keep it safe from unauthorized access."
When you spend time improving mobile data security, you lower the chances that someone will be able to see your contacts, bank information, private chats, or location history. And if you don't take care of it, the risk isn't "maybe," it's "when."
-20251113054911.webp)
What you need to know about the mobile threat landscape
Let's look at some of the most common threats to mobile data security so you can see how real they are.
1. Public Wi-Fi and networks that aren't secure
Your café smartphone session sounds innocent until you remember that public Wi-Fi networks are not always safe. That means that if you send login information, private information, or even just browse the web over such a network, attackers could get it. IBM says that mobile devices "often connect to public networks... making them easy targets for attackers."
2. Malware, phishing, and social engineering
Viruses and malware can get into mobile devices, and they are becoming more and more common. Brightsec says that malware, spyware, phishing, social engineering, and unsecured Wi-Fi networks are all threats to mobile security.
Imagine getting a text from someone who says they're your bank and clicking on a link in it. Your credentials are gone, or your device is hacked before you know it.
3. Losing or having your device stolen
You lose your smartphone or drop it. If you don't protect it properly, anyone who finds it may be able to get into your accounts as well as the device. Stealing physical devices is still a very real threat to mobile data security.
4. Bad habits when it comes to updates and weak protections for devices
Security patches are often included in updates for mobile operating systems. But if you don't update your device or skip security settings, you leave it open. IBM says again that mobile devices don't get updates as often as desktops do.
5. Worries about data privacy and regulatory risks
It's not only the device; it's also what you keep and send. TrustArc says that data privacy means properly handling, storing, accessing, keeping, and changing sensitive data. So if your mobile data is stolen, you may not only lose personal information, but you may also be breaking the law.
-20251113054909.webp)
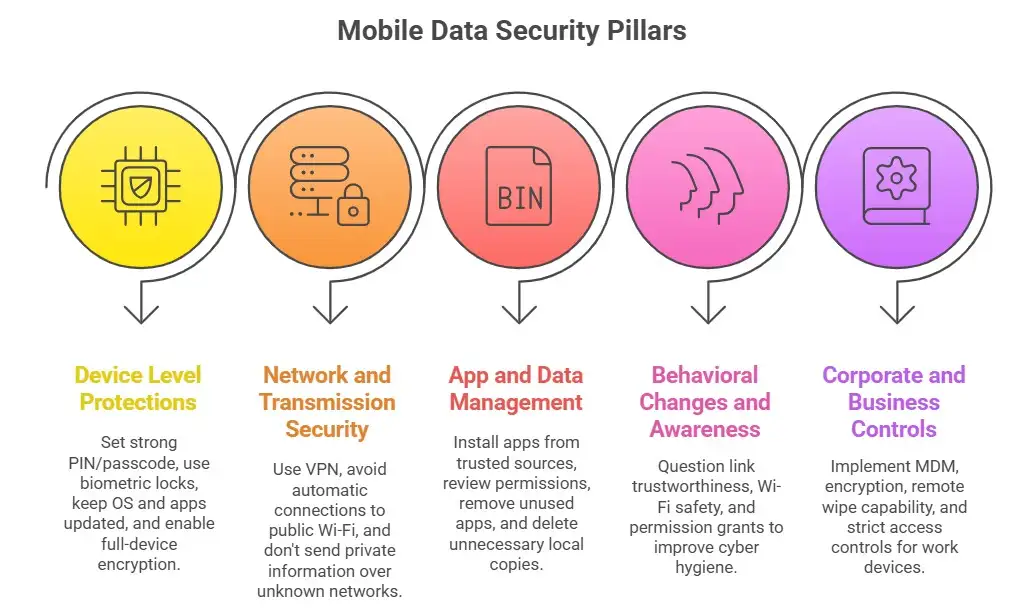
Key parts of mobile data security
So now you know what the threats are. Let's get to work and talk about how to protect your mobile world with strong steps. All of these help keep mobile data safe.
Pillar A: Protections at the device level
Start with the basics: set a strong PIN or passcode, use biometric locks (fingerprint or face) when you can, and make sure your phone's operating system and apps are always up to date. If your phone can do full-device encryption, use it so that data can't be read if someone gets to it physically.
Pillar B: Security of the network and transmission
When you connect to Wi-Fi, especially outside of your home or a trusted office, be aware that the network could be dangerous. If you can, use a Virtual Private Network (VPN), don't let your device automatically connect to public Wi-Fi networks, and don't send very private information over networks you don't know. Encryption and secure protocols like HTTPS and TLS are very important.
Pillar C: Keeping apps and data clean
Look at the apps you install. Are they from sources you can trust? Do they ask for more permissions than they need? Get rid of apps you don't use anymore. Make sure your data is safe and then delete any local copies that you don't need. If an app loops in the cloud, you should be able to control what data is shared and stored.
Pillar D: Changing behavior and raising awareness
This is the personal side of mobile data security. A lot of hacks work because someone clicked on a link, accepted a bad install, or used a weak password. Teach yourself to stop and ask, "Do I really trust this link?" Is this Wi-Fi safe? "Did I just give too many permissions?" These breaks help you improve your cyber hygiene.
Pillar E: Corporate and business controls (if they apply)
If you use a mobile device for work or business, you should expect extra layers of security, such as mobile device management (MDM), encryption at rest and in transit, the ability to wipe a device remotely, and strict access controls. As part of a mobile security strategy, Brightsec suggests things like MDM and secure coding practices.
A real-life story: What happens when mobile data security doesn't work
This is a story. One time, a friend of mine charged his phone at an airport lounge that had a shared charging station. The charging port was hacked (a type of "juice jacking"), and he didn't know it, but some of his data was also compromised.
Later, he saw strange attempts to log in to his email. A portable power bank or USB data blocker could have stopped that from happening.
This small mistake shows how small mistakes in mobile data security can lead to bigger problems. We put a lot of our identity, contacts, emails, apps, and accounts on the device. If one link in the chain breaks, we're at risk.
Common myths about mobile data security and why they are wrong
Myth 1: "My phone is safe because I don't keep anything important on it."
Truth: Even if you don't think your phone has "important" data, it probably does. It probably has contacts, personal photos, passwords, and location history. Hackers often use harmless information to get into more sensitive areas.
Myth 2: "It's okay to use public Wi-Fi if I go to sites I trust."
Even trusted sites can be hacked on a compromised network. DNS spoofing, fake hotspots, and man-in-the-middle attacks are all very dangerous. IBM says that mobile devices are often at risk when they are connected to public networks.
Myth 3: "Nothing can happen because my device is locked with a PIN."
If biometric or pattern unlock is weak, or if the attacker gets physical access and the device is old, they may be able to get around protections. It's important to keep your software up to date and use strong lock methods.
Putting it all together: Your checklist for keeping your mobile data safe
Here's a short list you can use to check the mobile data security of your own smartphone or tablet:
• The operating system and apps are up to date. • Device encryption is turned on (if it's available).
• Strong passcode and biometrics are used; • Auto-connect to public Wi-Fi is turned off; • VPN is turned on for public/untrusted networks; • Installed apps are trusted and necessary; • Permissions are checked for each app; • Data is backed up and old data is deleted; • Users are aware of phishing, suspicious links, and unknown install prompts; • Remote wipe and device tracking are turned on (if possible);
Crossing these off one by one slowly builds a wall around your data, making it safe and easy to use your phone.
Questions and answers about mobile data security
Q1.What is mobile data security, really?
Mobile data security is the protection of data that is stored on or sent by mobile devices like smartphones and tablets. It includes protecting devices, networks, apps, and how people use them.
Q2: What makes mobile devices more dangerous than desktops?
This is because mobile devices are always connecting to different networks, use a lot of apps, store personal and sensitive information, and users are more relaxed. IBM says that mobile devices "provide platforms from which to launch social engineering attacks."
Q3: Is the data on a stolen phone still safe?
Yes, you lower the risk if you set up passcodes, encryption, and remote wiping. But a thief could easily get to the data without those protections.
Q4: How often should I change the way I protect my phone?
All the time. Updates when they are available, but also every few months, you should review your apps, networks, backup plan, and permissions.
Last thought
Your phone is more than just a gadget; it's a place where you keep your identity, memories, money, and work. When you focus on mobile data security, you're not only avoiding problems, you're also protecting yourself.
You don't have to feel like the steps are too much. Begin with a strong password and regular updates. After that, add network security and app hygiene on top. These habits become second nature over time.
Author: Hoplon Infosec
Bio: Security enthusiast with over 10 years in mobile cybersecurity. Connect with me on LinkedIn.
Address: 1415 W 22nd St Tower Floor, Oak Brook, IL 60523, United States
Phone: +1 773-904-313 , Contact: [email protected]
About/Privacy: At Hoplon Infosec, we provide expert insights into cybersecurity. Our editorial policy: all articles are written by in-house specialists or thoroughly reviewed by them to ensure accuracy, credibility, and up-to-date information.
Share this :