Mobile Security Management: Ultimate 2025 Guide to Protect Data

Hoplon InfoSec
23 Nov, 2025
A Complete Expert Guide to Mobile Security Management for Modern Businesses
Managing mobile security has quietly become one of the most important things for businesses to do today. More and more workers use mobile devices to do their jobs every year, and attackers get smarter every year.
What used to be an optional layer of security is now the first line of defense that decides whether a business stays safe or makes the news. This is a lesson that many companies have to learn the hard way, usually after a breach that could have been avoided.
This guide talks about the real problems, the strategies that really work, and the useful tips we've learned over the years by helping businesses keep their mobile environments safe.
Today, phones and tablets can store everything from private messages to important work documents.

One device can access financial dashboards, customer data, and internal systems. When employees take these devices with them everywhere, security becomes more difficult, dangerous, and unpredictable. That's why managing mobile security is more important than ever.
How to Understand Mobile Security Management in the Real World
Mobile security management is all about keeping mobile devices, data, apps, and communication safe across an organization. It talks about how the device is set up, how the data is handled, and what the company does when something goes wrong. It also has rules, tools, and ways to keep an eye on things that help keep unauthorized people from getting to sensitive information.
This topic might sound technical, but it's really about people. Most of the time, employees don't mean to put data at risk. They still take their phones with them to airports, cafes, hotel rooms, public Wi-Fi areas, and sometimes even risky apps. Without a well-organized security system, even a small mistake can turn into a big problem.
Security teams can track, lock, wipe, or set up devices with mobile device management, mobile application management, and endpoint security tools. Not only can big businesses use these tools. Small businesses now depend on mobile work and can't afford to lose any data.
Why every business needs to take care of mobile security
Ignoring mobile security management puts a business at great risk. Attackers often look for the easiest way in, and many times that way in is through an employee's phone. Mobile devices are always moving between different networks and situations, which is not the case with office computers. This inconsistency makes a lot of things weak.
Companies that care about mobile security can lower the number of data breaches, unauthorized access, and malware infections. They also avoid downtime and keep their clients’ and partners' trust. Another important reason to invest in the right security controls is that rules are getting stricter all over the world.
One surprising trend is that hackers are now going after mobile banking sessions, messaging apps, and work-related collaboration tools. The goal is to get login information and use it to get deeper into the company's systems. This risk has only grown as more people work from home, so it's important to have strong mobile security management to stay safe.

How to Manage Mobile Security In Steps
1. Setting up and signing up for the device
First, companies add devices to a security platform. This lets the business set up settings, manage permissions, and make sure updates happen on time. When a device is enrolled, it joins a safe space that doesn't violate employee privacy.
2. Control of Access
Businesses choose who can see what. Strong authentication keeps attackers from getting into systems with stolen passwords. If a phone is lost, multi-factor authentication and role-based permissions help protect it.
3. Keeping an eye on security
The system is always on the lookout for suspicious activity. This includes apps that aren't allowed, dangerous networks, or signs of malware. When something seems strange, the team gets a warning.
4. Managing Apps
You can only use apps that have been approved. This stops workers from putting in dangerous tools that could let hackers in through a backdoor. Encryption and containerization are other ways that businesses can protect work apps.
5. Responding to Incidents
The team can lock or wipe a device from afar if it goes missing or shows signs of being hacked. This makes sure that data never gets into the wrong hands. A lot of companies depend on this feature to quickly get back lost devices.
In Real Life, an example of bad mobile security management
A retail company learned the hard way when one of its employees connected to a public WiFi network that was not safe. The attacker got login information and used it to get to internal sales data. It took weeks to find out what happened because the company didn't have mobile security management in place.
By that time, private information about customers had gotten out.
A good system could have stopped the unsafe connection, found the strange behavior, and stopped the breach. More often than most people think, this kind of thing happens.
Common Risks When Mobile Security Isn't Managed Properly
When businesses don't protect their mobile devices, security holes grow quickly. These are:
Theft of devices that can give criminals direct access to company data if there is no protection.
Phishing attacks that look like regular emails.
Apps that look like productivity tools but are actually harmful.
Networks that aren't secure and let attackers watch traffic.
Old operating systems that don't have the latest security updates.
Even small mistakes can lead to big problems. That's why businesses put money into structured protections and regular reviews.

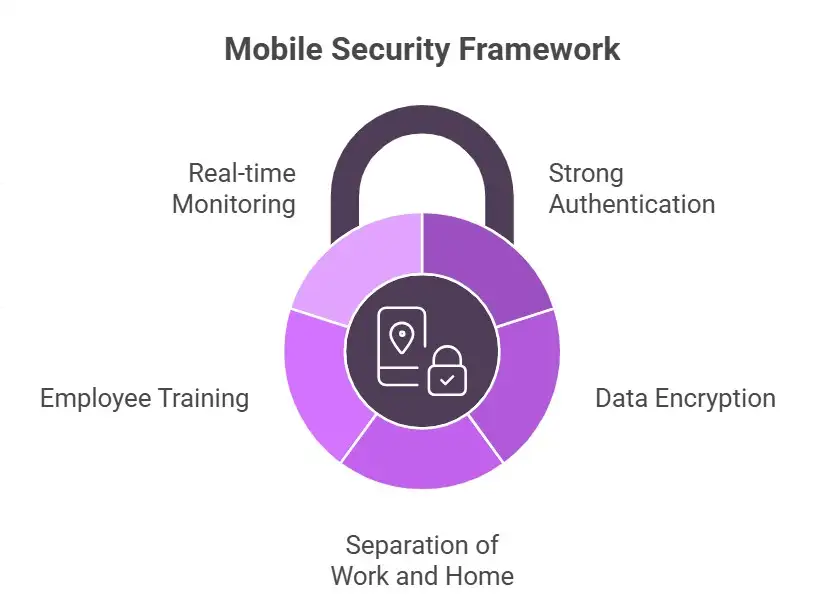
Tips from experts to improve mobile security management
1. Use strong authentication on all of your devices.
Passwords aren't enough on their own. Use biometric controls and checks with more than one factor.
2. Always encrypt private information
Encryption makes stolen data useless, even if hackers get into the device.
3. Keep work and home separate
Containers keep business data safe while giving employees the freedom to do what they want.
4. Teach your employees regularly
Training is just as important as the tools you use. People are usually the first line of defense.
5. Use tools that let you watch things in real time.
Security teams can act quickly thanks to instant alerts. In response to an incident, speed is important.
Tools That Help with Strong Mobile Security Management
A lot of businesses use special platforms to keep their mobile devices safe. Mobile device management systems, unified endpoint platforms, and threat detection tools are some of the most common solutions. These tools help you automate tasks, make sure policies are followed, and learn more about how devices work.
The right choice often depends on how big the company is, what kinds of devices it uses, and what rules it has to follow. Some businesses like to use cloud-based tools, while others use systems that are already in place. What matters most is making sure the rules are followed and that everyone can see them.
End
Companies that treat mobile devices like important business tools get better security results. Mobile security management is a planned way to keep data safe, help employees, and lower risk. It builds trust, makes sure people follow the rules, and gets businesses ready for the unpredictable nature of modern work.
Businesses are more confident and don't have to deal with problems that aren't necessary when they have strong controls in place. The first step is to know the risks and pick a system that lets you see everything and have full control.
Questions and Answers
1. What is the management of mobile security?
It is the planned way to protect apps, devices, and data in a business. It includes setting up, keeping an eye on, verifying, and responding to incidents.
2. What is the need for mobile security management in businesses?
It lowers the risk of data breaches, stops unauthorized access, helps with compliance, and protects company systems from attacks that happen on mobile devices.
3. Can small businesses use tools to protect their phones?
Yes. A lot of mobile security platforms have features and prices that work well for small and medium-sized businesses.
4. How does mobile security keep lost devices safe?
Companies can lock or wipe lost devices from a distance, which stops people who shouldn't have access to private information from getting it.
Explore our main services:
· Deep and Dark Web Monitoring
· ISO Certification and AI Management System
· Web Application Security Testing
For more services, go to our homepage.
Author: Hoplon Infosec
Bio: Security enthusiast with over 10 years in mobile cybersecurity. Connect with me on LinkedIn.
Address: 1415 W 22nd St Tower Floor, Oak Brook, IL 60523, United States
Phone: +1 773-904-313 , Contact: [email protected]
About/Privacy: At Hoplon Infosec, we provide expert insights into cybersecurity. Our editorial policy: all articles are written by in-house specialists or thoroughly reviewed by them to ensure accuracy, credibility, and up-to-date information.
Share this :