Network Penetration Testing: 7 Proven Secrets for 2025

Hoplon InfoSec
11 Nov, 2025
You throw a party at your house, but instead of locking the doors and hoping nothing goes wrong, you ask someone to try to break in to see where your weak points are. Network penetration testing is basically an organized, fake attempt to break into your digital "house" so you can fix the holes before a real attacker gets in.
I've written about cybersecurity for a long time, and I've seen a lot of companies treat pen testing like a box to check. That way of thinking can cost them a lot of money. Let's go over what network penetration testing really is, why it's important, how to do it (and how not to do it), and what to do with the results.
What is network penetration testing, and why do you need it?
The main idea behind network penetration testing is that security experts (also known as ethical hackers) try to exploit weaknesses in a network's infrastructure, just like a hacker would, so you can stay one step ahead of them. The point isn't to break things for fun; it's to find the weak spots before someone who wants to hurt you does.
Why is this so important? Because networks are big, changing, and often have blind spots these days. One mistake, like a misconfigured firewall, a forgotten wireless access point, or a remote VPN that isn't being watched, can lead to data loss or ransom. A recent review of the literature said that network penetration testing is a "mandatory element," especially when you're working with sensitive data, following the rules, or a big infrastructure.
You also need to act like a real attacker after you scan. For instance, a vulnerability scan might find known problems, but a network penetration test goes further by showing you the effects of a breach, not just the existence of a flaw.
-20251110151823.webp)
Common ways and methods for testing network penetration
The way that businesses choose to do network penetration testing can have a big effect. Here are some common ways to do it:
Testing in a black box
In this case, the tester doesn't know much about the target network, just like an attacker who comes in with no information. This method is helpful for testing how well your external assets hold up when someone tries to get into them from the outside.
Testing in a white box
The tester can see everything here: network diagrams, credentials, and architecture. The point is to go deep into the network and find weaknesses that might not be obvious from the outside. This method is very thorough, but it also takes up more resources.
Testing in a gray box
A little bit of both: the tester knows some things but not everything. It acts like an attacker who has gotten a foot in the door, maybe through social engineering or stolen credentials. This method often finds the right balance between being realistic and useful.
You should choose the right method for your network penetration testing plan based on your risk profile, resources, and goals. Each method has its own pros and cons.
What happens during a network penetration testing engagement is a typical process.
When you set up a network penetration testing engagement, this is what you'll probably see: each step is important, and skipping one can make the exercise less useful.
1. Planning and gathering information
At the very beginning, you set the scope, goals, and rules of engagement. You choose which assets are in scope, such as servers that are open to the outside world, the internal LAN, wireless, VPN, and IoT devices. Then the tester collects data, such as open ports, network maps, and user directory structures.
2. Scanning and assessing vulnerabilities
The tester uses both tools and their own hands to find possible security holes, unpatched services, insecure settings, and exposed credentials. This isn't the end, though; it's more like a list of possible entry points.
3. Taking advantage of someone and getting more power
This is the more offensive part. The tester tries to take advantage of known weaknesses, gain more access, move laterally, and act like an attacker would to get deeper into the network. It's not just "can I get in," but "how far can I go?"
4. Reporting and post-exploitation
Once the tester gets in, they will look at what assets can be accessed, what data is at risk, and how long someone could stay hidden. Then they give you a report that includes their findings, evidence, a risk rating, and suggestions for how to fix the problem. A good network penetration testing report doesn't just say "you're vulnerable"; it also says "here's how to fix it."
5. Fixing and retesting
It's a good idea to retest after you make changes based on the results, such as applying patches, tightening configurations, and changing processes. This will make sure that the fixes work and that no new problems have come up. Instead of treating security as a one-time thing, continuous monitoring and periodic network penetration testing help keep it safe.
-20251110151820.webp)
Important things to think about and mistakes to avoid
I've seen companies use network penetration testing as a way to check things off a list. That way of thinking makes the value less. So here are some things to remember and learn from:
If you only test external servers and don't test wireless or remote endpoints, you're missing a big part of the picture. A rogue access point, for instance, could let someone from outside your LAN in, which is something that often goes unnoticed.
• Thinking of it as a one-time thing: It's dangerous to do a network penetration test once a year and then forget about it. Threats change, and new devices join networks. It's much better to do penetration testing all the time or more often.
• Ignoring the process: It's almost pointless to skip the reporting or remediation phases. The real value is in finishing the loop.
• Tool dependence: Tools are helpful, but it's also important to do manual testing and think like an attacker. A lot of vulnerabilities are logical or related to configuration, and automated scanning alone won't find them.
• Insider threats: A lot of companies test their defenses against outside attacks, but don't think about the risks from inside. You can find out about different types of exposure by doing a network penetration test that simulates an insider (gray box or white box).
Example from the real world (story)
I remember talking to a medium-sized business that had been focusing on web application security for years but had not paid enough attention to its internal LAN and wireless network. They hired a network penetration testing team, which found several unregistered wireless access points in the offices during their reconnaissance.
Employees had set them up "for convenience." The testers used one of those access points to connect, used a poorly-segmented network to get higher privileges, and got to sensitive financial data in just a few hours. The business knew that their big investment in testing firewalls and web apps didn't mean much if there was a "back door" inside. That story shows how network penetration testing can find attack vectors that weren't planned for.
Benefits of consistent network penetration testing
When done correctly, network penetration testing gives you real benefits:
• You find security holes before criminals do. That gives you a chance to fix things before they go wrong.
• You make your network security stronger by using better segmentation, stricter controls, and clearer processes.
• You have a better chance of meeting your compliance obligations (for example, in industries that are regulated).
• You can relax and let everyone know that you are taking cybersecurity seriously.
• You create a culture of constant improvement and security awareness over time, which makes your organization less of an easy target.
Useful tips for getting the most out of your network penetration testing
Here are some useful tips for planning your next network penetration test (or thinking you should):
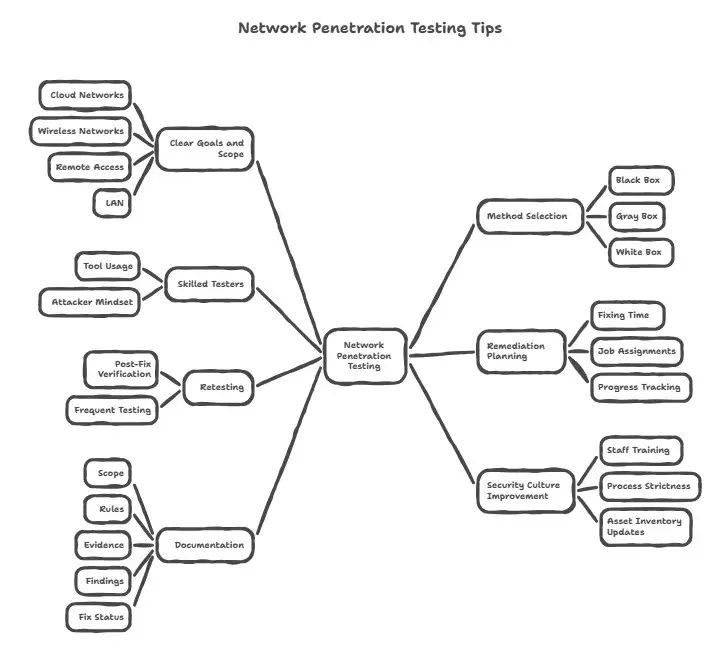
• Make sure your goals and scope are clear. Know if you're testing networks that are connected to the cloud, wireless, remote access, or LAN.
• Based on your risk profile and resources, pick the right method (black box, gray box, or white box).
• Make sure that the person or team you are testing with has the right skills, including how to use the tools and how to think like an attacker.
• Make plans for how to fix things ahead of time. Don't think of the test as just a way to make reports. Set a time to fix things, give people jobs, and keep track of progress.
• Do the test again. Check again after the fixes are in. You might also want to test more often or all the time to keep up with new threats.
• Use what you learned to make your security culture better by training your staff, making processes stricter, and updating your asset inventories.
• Write down everything: scope, rules, evidence, findings, and the status of the fix. Clear documentation is helpful for audits and talks at the board level.
Frequently Asked Questions
Q: How often should you test your network for holes?
A: There isn't a rule that works for everyone, but you should do a full network penetration test at least once a year. You should test sooner if there are big changes, like new systems, big updates, or acquisitions. It also helps to do vulnerability assessments or scans more often with it.
Q: What's the difference between testing for network vulnerabilities and doing a vulnerability assessment?
A: That's a good question. A vulnerability assessment looks for known problems in your systems. You can think of it as a list of problems. Network penetration testing goes even further by using vulnerabilities to see what happens when someone acts on them.
Q: Is network penetration testing only for big companies?
A: Not at all. Big companies with big networks have clear needs, but smaller companies with important data or systems that are connected also benefit. In fact, they might be easier to hit. So yes, anyone who has a network and data that needs to be protected should think about it.
Think of network penetration testing as a journey, not just a one-time thing.
If I could only give you one piece of advice, it would be to think of network penetration testing as putting a mirror in front of your network's worst nightmare and saying, "Show me what you would do so I can be ready when you do it."
When you think that way, you don't just take a test; you get stronger. You go from being reactive to being proactive. You make it so that you don't hope nothing happens; you know you're ready if it does.
Explore our main services:
· Deep and Dark Web Monitoring
· ISO Certification and AI Management System
· Web Application Security Testing
For more services, go to our homepage.
Share this :