Penetration Testing Methods Explained: Real-World Security Testing
Hoplon InfoSec
25 Jan, 2026
Are penetration testing methods still useful in 2026, or are they just another way to check off a compliance box?
Yes, they are more important than ever. As of January 2026, companies are dealing with faster attacks, more complicated clouds, and exploits that target people that automated scanners can't find. That is why penetration testing methods are still very important for real security validation. NIST and OWASP are the most trusted global sources for penetration testing practices, and this explanation is based on their publicly available advice.
Why penetration testing methods are still useful today
Most security problems don't start with something big. They start quietly. An admin panel that was forgotten. A weak API access. An employee clicks on something they shouldn't. I've seen businesses spend a lot of money on security tools, but they still get hacked because no one tested how well those tools work together.
That's where penetration testing comes in. They don't just talk about attacks; they actually do them. Instead of asking, "Are we following the rules?" they ask, "Can someone really break in?"
Penetration testing looks at how weaknesses connect to each other, while vulnerability scans do not. A small mistake in the settings might not seem like a big deal on its own, but when it's combined with another flaw, it becomes a full breach path. This is the gap that a lot of automated tools don't see.
What penetration testing really means
People often call penetration testing "ethical hacking," but that can be confusing. It has nothing to do with tricks or chaos. It's about testing that is done with permission, a clear scope, and clear goals.
Testers try to get into systems the same way real attackers would by using tried-and-true penetration testing methods. The difference is what you want to do. The goal is not to hurt, but to learn.
It's like hiring someone to check every door and window in your house, even the ones you forgot about. That experience can't be replaced by a checklist.

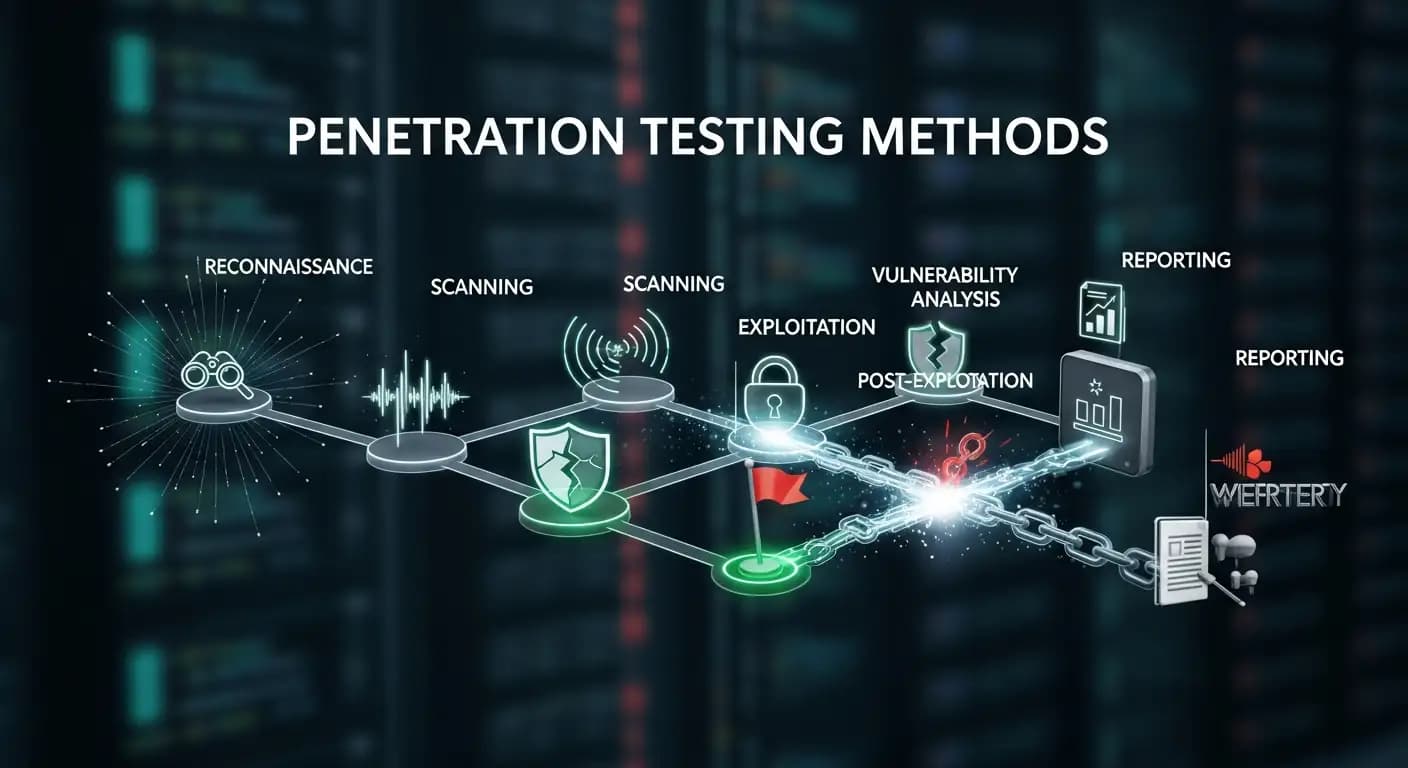
The main types of penetration testing methods
Penetration testing has changed over the years into several clear methods. There is a reason for each one. There isn't one way that works for all organizations.
Testing in a black box
Black box testing starts with very little information. The tester only knows what an outside attacker would know. This method is the most similar to real-life attacks.
In a black box setup, penetration testing can help answer one big question: what can someone from the outside really get to?
The bad thing is time. Coverage may be limited because testers start blind. Still, it is very useful for systems that are connected to the internet.
Testing in a white box
The opposite of black box testing is white box testing. The tester can see architecture diagrams, credentials, and sometimes even the source code.
This approach is all about depth. It finds mistakes in logic, bad design choices, and trust assumptions that black box testing might not find. From what I've seen, white box testing often finds problems that developers didn't know could be used.
For the best results, many modern security teams combine this with secure code review.
Testing in a gray box
Gray box testing is in the middle. The tester can only access certain things, like a standard user account.
This is one of the best ways to test the security of modern SaaS platforms. It shows risks of insider threats, hacked accounts, and privilege escalation.
Testing network penetration in real-world settings
Network testing is still one of the most common types of testing. It talks about how systems talk to each other and trust each other.
Testers look at firewalls, services that are open to the public, internal segmentation, and authentication flows. They look for old protocols, weak passwords, and ways to move sideways.
Many people think that internal networks are safe. In reality, once attackers get in, they can move around as they please. Network-focused penetration testing methods are made to show that risk.
Testing for security holes in web applications
Most businesses interact with users through web apps, and attackers know this.
Web testing looks for problems like broken access control, insecure APIs, authentication flaws, and injection vulnerabilities. The OWASP Top 10 is still a good place to start, but real testing goes beyond lists.
Good testers look at how features work together. For instance, a file upload function might be safe on its own, but it could be dangerous if it is used with a cloud bucket that is set up incorrectly.
In this case, manual testing always does better than automation.
API penetration testing is now required
APIs are now what make mobile apps, SaaS platforms, and integrations work. Still, a lot of companies only test them after the fact.
APIs are now seen as first-class attack surfaces by modern penetration testing methods. Testers check authentication tokens, rate limits, object-level authorization, and business logic.
API authorization flaws have led to a number of high-profile breaches in the past few years. These hacks weren't very hard. They were wrong assumptions.
Testing for cloud and container penetration
In cloud environments, everyone is responsible for something. Providers protect the infrastructure, but customers are in charge of setting it up.
Cloud testing looks at things like identity and access management, storage permissions, management interfaces that are open to the public, and services that are set up wincorrectly
Testing containers adds another layer. Images, registries, orchestration platforms, and managing secrets all fall under the scope.
Without cloud context, traditional penetration testing methods can leave gaps. Skilled testers change their methods to fit the needs of cloud-native systems.
Using social engineering as a way to test for security holes
Code isn't used in every attack. A lot of people use psychology.
Testing for social engineering looks at how workers react to phishing, pretexting, or harmful attachments. You need to be careful and honest when you do these tests.
When done correctly, they give you information that no technical scan can. They show where people need more training, where policies aren't clear, and where people are doing things that could be dangerous.
This is often the most uncomfortable type of test, but it also has the biggest effect.

What makes penetration testing different from vulnerability scanning?
People don't realize how important this difference is.
Vulnerability scanning finds problems that are already known. Penetration testing checks to see if something can be exploited. A scanner might find 100 problems. A penetration test shows which five are the most important.
Security teams can set realistic priorities by using penetration testing methods. That saves time, money, and worry.
Both methods are helpful, but they have different uses.
Things that businesses often do wrong when they do penetration testing
A common mistake is to only test once a year. Threats change more quickly than that.
Another problem is only paying attention to compliance. Putting a report away doesn't make things safer.
Penetration testing methods are used as feedback loops in effective programs. Findings help make changes to the architecture, train developers, and improve monitoring.
Testing without follow-up is pointless.
What happens after a penetration test is very important
The test itself is only part of the story. The real value comes from fixing things and learning.
Strong teams look over their findings together. Developers have questions. In business terms, security means risk. Fixes are kept track of and checked.
This is where trust grows. Penetration testing is no longer a fight; it's a team effort.
People also want to know about ways to do penetration testing
How often should you run penetration tests?
According to advice from NIST and OWASP, testing should happen at least once a year and after big changes. You might need to test high-risk systems more often.
Are penetration tests done automatically?
Automation can help with testing, but people still need to do some of the work. People's ability to think is what finds chained exploits and logic flaws.
Is it legal to do penetration testing?
Yes, as long as you have written permission and a clear scope of work. Testing without permission is against the law.
Do small businesses gain from penetration testing?
Yes. You can change the scope to fit your budget while still getting value.
If you are planning a test, what to do next
Define your goals first. Do you want coverage for realism, depth, or compliance?
Pick penetration testing methods that fit your risk profile, not just what you need for an audit. Get technical and business stakeholders involved early on.
Plan how to fix things before testing starts, and that's the most important thing. That's how results become real protection.
A useful suggestion from Hoplon Security of Information
When companies use penetration testing as a way to make things better all the time instead of just once, they get the most out of it. Testing networks, websites, APIs, and clouds together gives you a clear picture of how modern attacks work. Clear scoping, honest reporting, and help with fixing problems are more important than flashy exploits.

Final thought
Dashboards do not prove security. Resistance proves it.
When used carefully, penetration testing methods show how systems act when they are really stressed. They trade guesses for proof. They make things clear when you're not sure.
That's wh
A reliable source:
NIST SP 800-115: A Technical Guide to Testing Information Security
Share this :