Penetration Testing vs. Vulnerability Scanning: What Is the Real Difference in 2025?
Hoplon InfoSec
01 Dec, 2025
If you manage security for any organization, this comparison comes up a lot: penetration testing vs. vulnerability scanning. Many people still mix them up, even though they play completely different roles in a security program.
So the question for today, January 2025, is simple: Can one replace the other, or do you actually need both to stay secure?
Based on verified industry data and widely accepted security frameworks, the short answer is that both are required, but for different reasons. One finds weaknesses; the other proves whether attackers can actually break in.
Below is a clear, people-first guide that walks through the differences, use cases, cost factors, and real examples naturally and practically.
Understanding the Core Difference
At the heart of this discussion is one important truth. A vulnerability scan detects potential issues, while a penetration test proves impact through a real attack simulation. This is the simplest way to understand the topic of penetration testing vs. vulnerability scanning.
What Vulnerability Scanning Actually Does
A vulnerability scan uses automated tools to look for known issues. It follows a database of weaknesses and matches them with your systems. This helps security teams understand their exposure and start the vulnerability management lifecycle. The goal is coverage. It checks as many systems as possible.
This is why companies run continuous vulnerability scanning every week or every month. It is cheaper, faster, and great for routine visibility. When people ask whether the purpose of vulnerability scanning is enough for real security, the answer is usually no, because scans identify problems but do not validate them.
The biggest limitation is false positives. Every security engineer has seen long scan reports with issues that look scary but are not actually exploitable. Teams often feel overwhelmed by these results. That is why many ask how to handle vulnerability scanner false positives and how to triage. The realistic solution is to mix scanning with validation steps, often through a penetration test.
What Penetration Testing Does
Now we enter the world of human-led testing. A penetration test looks and feels very different from a scan. It is an ethical hacking engagement where testers mimic real attackers. They use manual techniques, exploit validation, and use creative problem-solving. This approach gives a deeper security posture assessment because it does not rely only on signatures or automated checks.
People often compare penetration testing vs vulnerability assessment as if both are automated. In truth, a vulnerability assessment still focuses on listing issues, while a penetration test focuses on proving impact. When you read about pentest vs. vulnerability scan conversations on forums, you will notice testers always highlight that manual exploitation cannot be replaced by any tool.
A penetration test also goes beyond basic weaknesses. It explores chaining issues, misconfigurations, identity abuse, logic flaws, and areas that scanners simply cannot understand. Whether it is a web app or an internal network, penetration testing benefits include clarity, prioritization, and realistic attack stories that leadership can understand.
When to Use Them, and How They Complement Each Other
Here are practical situations where each type of testing fits best.
• Use vulnerability scanning first when you need wide coverage.
• Use penetration testing when you want to understand real risk.
• Use both if you want a mature security program.
A scanner may tell you a server has a high-severity weakness. A penetration test shows whether that weakness can be used to move deeper into your systems. Many security teams now choose PTaaS vs. pen testing, especially if they want a subscription model with easier reporting. Others still prefer one-time pen tests. The right choice depends on how dynamic your systems are.
Organizations also ask how often you should perform penetration testing vs scanning. Scans make sense monthly or weekly. Penetration tests are usually run once or twice per year unless compliance states otherwise. Some companies do a test after major product launches or major infrastructure changes. Others run smaller, targeted tests throughout the year for web apps.
Cost matters too. Many buyers look up penetration testing vs. vulnerability scanning cost in 2025. Scans remain cheaper because they rely on automation. Penetration tests cost more because they require skill, time, and human expertise. When someone asks if I need a penetration test if I run vulnerability scans monthly, the answer is simple. Scanning monthly gives visibility, but it will never tell you how attackers actually behave.
Practical Explanation with Clear Breakdown
Think of it like a medical checkup. A vulnerability scan is similar to using a home health monitor. It measures indicators and gives you a quick overview. A penetration test is like seeing a specialist who performs deeper examinations. One covers broad areas; the other focuses on what can truly harm you.
When considering penetration testing for web apps vs. network vulnerability scanning, the gap becomes very visible. A scanner may detect outdated software or missing headers. A penetration test checks how that missing piece can be used to break authentication, chain injections, and steal data. That is why many organizations treat them as separate tools in a broader security strategy.
Even compliance frameworks point toward this dual approach. PCI DSS, for example, requires both scanning and penetration testing. Companies researching compliance penetration testing PCI DSS soon realize that they need regular scans plus annual pentests. Both complement each other and help close real risk gaps.
A Realistic Scenario
Imagine a mid-sized business with a cloud platform. They run continuous vulnerability scanning on all servers. One month, the scanner reports a critical issue on an API endpoint. The team is worried, but they later discover it was a false positive. This wastes time.
Now consider the same environment during a penetration test. A tester notices a low-severity weakness that the scanner ignored. The tester chains it with a minor permission issue and eventually reaches customer data. In this case, the scan missed the real threat, while the test revealed the true attack path.
This example shows why security teams often compare vulnerability assessment vs. penetration testing differences. They do not compete. They complement each other and deliver different types of value.
Key Insights
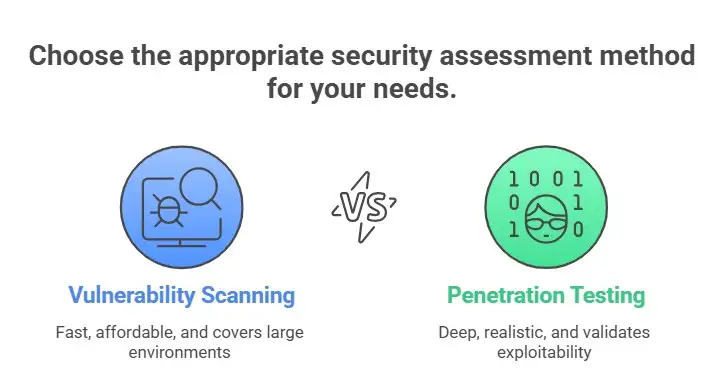
Key Benefits of Vulnerability Scanning
• Fast and affordable
• Covers large environments
• Helps maintain consistent monitoring
• Useful for early detection in the vulnerability management lifecycle
Limitations of Vulnerability Scanning
• High number of false positives
• Cannot validate exploitation
• Limited understanding of system logic
• Cannot simulate real attacker behavior
Key Benefits of Penetration Testing
• Deep, realistic attack simulation
• Validates exploitability
• Uncovers issues scanners cannot detect
• Helps leadership understand real-world impact
Limitations of Penetration Testing
• More expensive
• Takes longer
• Requires skilled ethical hacking professionals
• Not ideal for daily monitoring
FAQs
What is the difference between vulnerability scanning and penetration testing?
Scanning finds possible issues automatically. Penetration testing proves whether those issues can be used by attackers.
Which is cheaper: vulnerability scanning or penetration testing?
Scanning is cheaper because it is automated. Penetration testing requires human expertise.
How often should vulnerability scanning be performed?
Most organizations run scans weekly or monthly to maintain visibility.
Can penetration testing replace vulnerability scanning?
No. Penetration testing cannot provide continuous coverage. Both are needed for a complete security program.
Final thoughts
When you compare penetration testing vs vulnerability scanning, the real difference becomes clear. One lists possible weaknesses. The other measures real risk through expert analysis. No security program in 2025 can rely on only one of them. If you want true protection, combine both for a strong and balanced defense.
If you need help selecting the right testing approach for your business, feel free to ask. I can guide you through scope, pricing, and strategic planning.
Explore our main services:
· Deep and Dark Web Monitoring
· ISO Certification and AI Management System
· Web Application Security Testing
For more services, go to our homepage.
Author: Hoplon Infosec
Bio: Security enthusiast with over 10 years in mobile cybersecurity. Connect with me on LinkedIn.
Address: 1415 W 22nd St Tower Floor, Oak Brook, IL 60523, United States
Phone: +1 773-904-313 , Contact: [email protected]
About/Privacy: At Hoplon Infosec, we provide expert insights into cybersecurity. Our editorial policy: all articles are written by in-house specialists or thoroughly reviewed by them to ensure accuracy, credibility, and up-to-date information.
Share this :