Phishing Attack Using Signal App: German Agencies Warn

Hoplon InfoSec
09 Feb, 2026
Is a Phishing Attack Using the Signal App Really Happening, and Why Does It Matter Today?
Yes.German security agencies are investigating a phishing attack using the Signal app. This attack targeted politicians, military members, journalists, and policy advisors.People don't think Signal is broken or hacked. The problem is that hackers are quietly taking over accounts by using people's trust, linking devices, and everyday habits.
In early 2026, German officials warned that bad actors are using fake messages. They want to trick important targets into connecting a device they control to their Signal account. When this happens, they can copy private conversations without anyone knowing.knowing. This is not only a problem for people who work with private information. It is a threat to national security.
A lot of people trust Signal as a safe way to send messages, so this warning is important now. When people feel safe, they tend to let their guard down. Attackers know this better than anyone else.
What Exactly Is a Phishing Attack Using the Signal App?
At its core, a phishing attack using the Signal app is not about exploiting software flaws. It is about exploiting people.
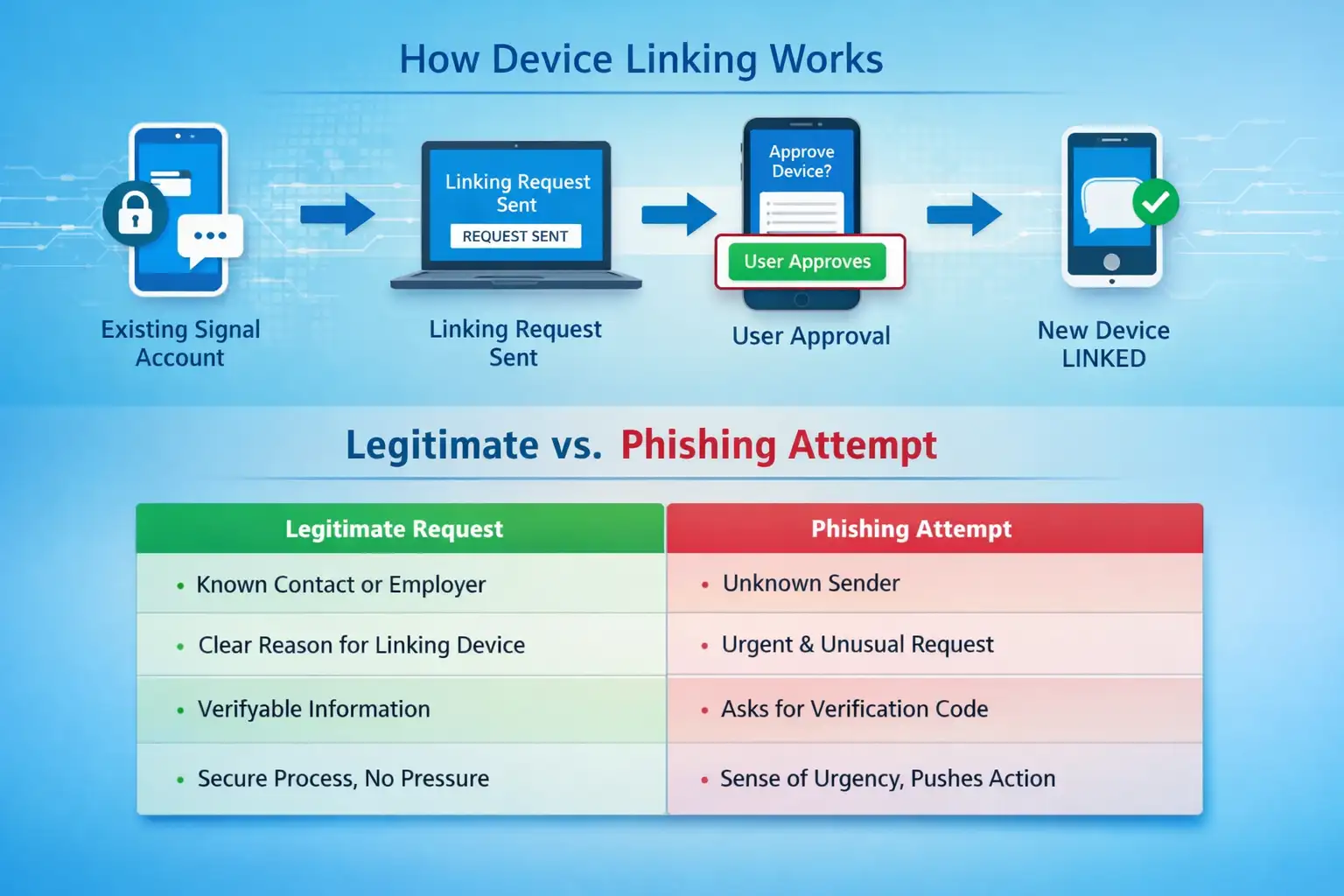
Attackers send messages that appear urgent, official, or familiar. A lot of the time, these messages look like they come from trusted people, internal teams, or security alerts. It's clear what the goal is. Ask the victim to agree to a device linking request or give you a one-time code.
Once the attacker gets the go-ahead, they can get in without needing passwords or viruses. This method is often described as a Signal phishing attack or a Messenger account takeover, and it is alarmingly effective against busy professionals.
What makes this different from older phishing scams is the subtlety. There is no fake login page. No obvious red flags. Just a normal-looking Signal prompt that seems harmless in the moment.

Why German Agencies Are Taking This Threat Seriously
German cybersecurity agencies rarely issue public warnings unless the risk is real and ongoing. In this case, the targets tell the story.
Politicians, defense personnel, and investigative journalists hold conversations that can influence policy, expose corruption, or affect military planning. Even partial access to these discussions can provide intelligence value to hostile groups.
Authorities believe these campaigns show signs consistent with state-sponsored hackers, although official attribution has not been publicly confirmed. That uncertainty is important to acknowledge. Investigations are ongoing, and not every detail has been disclosed.
What is confirmed is the technique. This is classic social engineering combined with device linking abuse. No vulnerabilities. No exploits. Just carefully planned deception.
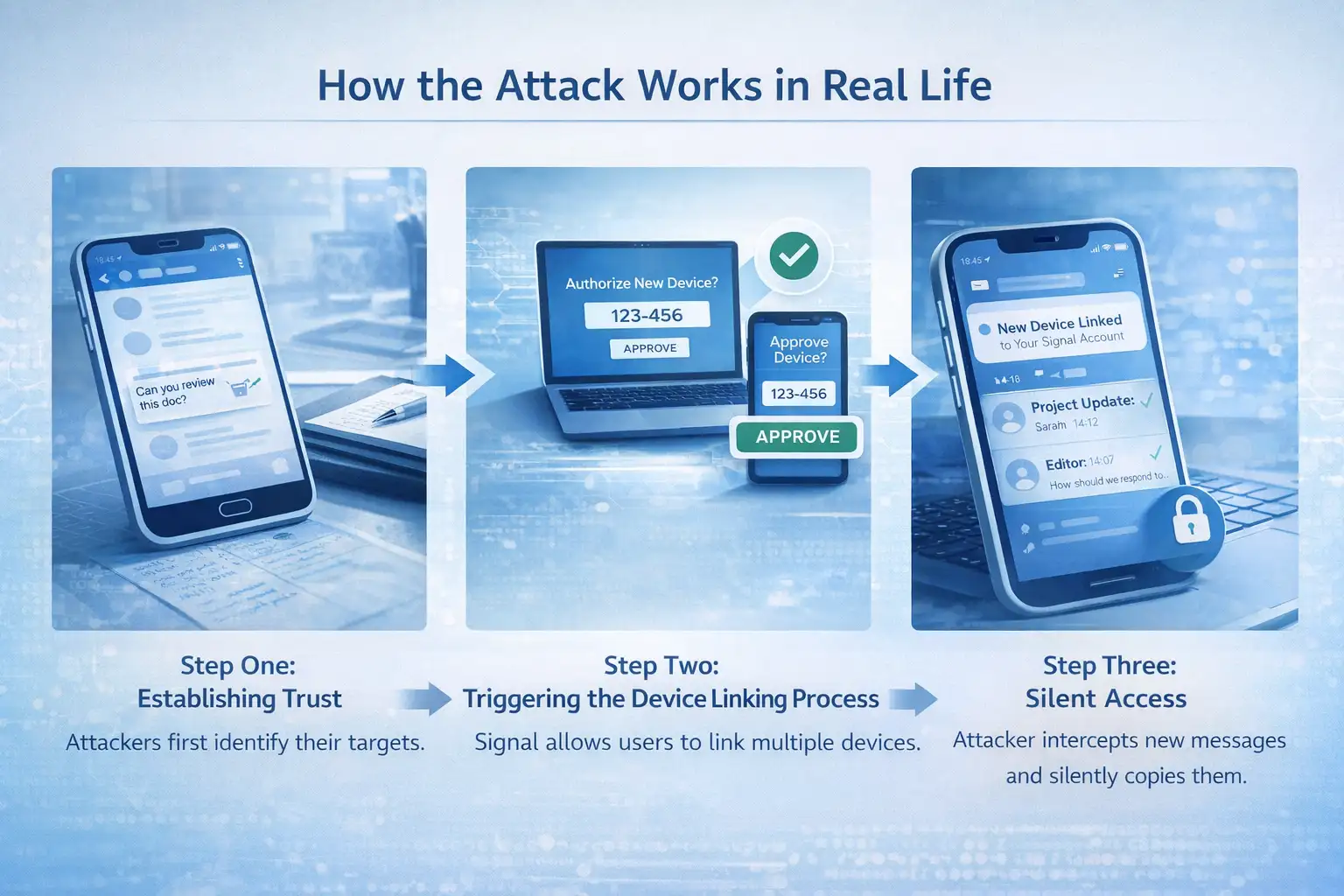
How the Attack Works in Real Life
Step One: Establishing Trust
Attackers first identify their targets. Public figures often have contact details, social circles, or assistants that can be studied. Sometimes previous breaches provide background information.
The attacker then sends a message that feels familiar. It may reference a meeting, a document, or an ongoing issue. In some cases, the message appears to come from a known contact whose account was compromised earlier.
The tone is calm but urgent. That balance matters.
Step Two: Triggering the Device Linking Process
Signal allows users to link multiple devices. This is a legitimate feature designed for convenience. Attackers take advantage of this by asking victims to approve a new device. They often call it a work phone, a replacement device, or a temporary secure terminal. The victim gets a notification.It looks real because it is real. Signal is doing exactly what it was designed to do.
One tap. One approval. That is all it takes.
Step Three: Silent Access
Once linked, the attacker can read messages as they arrive. In many cases, the victim does not notice anything unusual. Messages still send. Contacts still reply.
This is how a Messenger account takeover can last for weeks without detection.
A Simple Example That Makes This Feel Real
Imagine a parliamentary aide receives a Signal message late at night. The message says a senior official lost their phone and needs urgent access to ongoing discussions. A device linking request follows moments later.
The aide is tired. The message seems reasonable. The name checks out.
They approve the request.
By morning, sensitive conversations are no longer private.
This is not speculation. This is exactly the kind of scenario German agencies are warning about.
What Makes Signal Phishing Attacks So Effective?
The biggest strength of Signal is also its weakness in this context. Trust.
People use Signal because they believe it protects them. That belief is largely correct at a technical level. End-to-end encryption remains intact.
But encryption does not protect against human error. Social engineering thrives in environments where users feel safe.
Another factor is interface familiarity. Device linking prompts are not rare. Many users have seen them before. Attackers rely on that familiarity to avoid suspicion.
Who Is Most at Risk Right Now?
While the current warnings focus on German officials and journalists, the technique itself is not limited to them.
Anyone who uses Signal for work, activism, or sensitive planning could be a target. This includes lawyers, businesspeople, researchers, and people who work for NGOs.
The difference is in what drives them. State-sponsored hackers often spend more time and effort to target important people with personalized attacks.
That doesn't mean that regular users are safe. It just means that the stakes are different.
Effects on More Than Just One Account
A phishing attack using the Signal app has effects that go beyond just one hacked account.
Conversations that get out can show networks of contacts. One takeover can lead to another. People's trust goes down quickly when they find out that private chats aren't as private as they thought.
For institutions, the harm can be serious. It can damage their reputation. It may also lead to changes in their policies. Additionally, there is a risk of sensitive information being exposed for a long time.
This is why German agencies are urging caution rather than panic. Awareness changes behavior. Behavior reduces risk.
What Signal Has Said So Far
As of now, there is no public indication that Signal’s core encryption or infrastructure has been compromised. This distinction matters.
Signal has previously warned users about phishing and device linking risks. The app includes security notifications and device management features for a reason.
The problem is not a broken system. It is a system that assumes informed users.
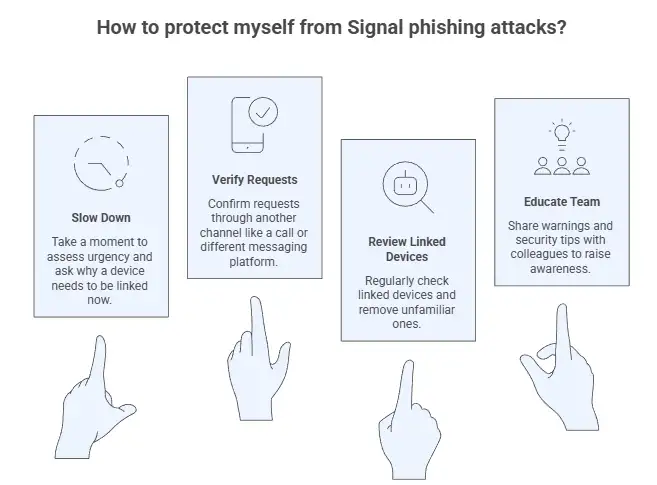
How to Protect Yourself From Signal Phishing Attacks
Slow Down Before Approving Anything
Most successful attacks rely on urgency. Take a moment. Ask why a device needs to be linked right now.
If something feels rushed, it probably is.
Verify Requests Through Another Channel
If a colleague asks you to approve a device, verify it through a call or a different messaging platform. This simple step defeats most Signal phishing attacks.
Regularly Review Linked Devices
Signal allows users to see which devices are linked to their account. Make it a habit to check.
If you see something unfamiliar, remove it immediately and alert your contacts.
Educate Your Team
Security is not an individual effort. Share these warnings with colleagues. Especially those who handle sensitive conversations.
Awareness is the strongest defense against social engineering.
Technical Reality Check
It is important to be clear. There is no evidence, as of now, of a mass exploitation or automated campaign affecting millions of users.
German agencies have not confirmed the scale, duration, or specific threat actors involved. Much of the investigation remains confidential.
This appears to be a targeted operation, not a widespread outbreak.
Why This Trend Is Likely to Continue
Messaging platforms are now central to professional and political communication. That makes them attractive targets.
As encryption improves, attackers will continue shifting toward human-focused techniques. Device linking abuse is just one example.
Future campaigns may blend phishing with voice calls, deepfake audio, or compromised assistants.
The tools will evolve. The psychology will stay the same.
What Users Should Do Next
If you use Signal for sensitive communication, review your security settings today. Not tomorrow.
Encourage verification culture. Normalize double-checking requests. Remove the stigma around asking questions.
Security improves when caution becomes routine.
Frequently Asked Questions
Can Signal itself be hacked through this method?
No. This method does not break Signal encryption. It relies on user approval through legitimate features.
How common is a Signal phishing attack?
There is no confirmed data on frequency. Current warnings suggest targeted, not widespread, activity.
Are journalists outside Germany at risk?
Yes. The technique is not country specific. Motivation depends on the attacker.
Does two-factor authentication stop this?
It helps, but it does not fully prevent device linking abuse if users approve requests.
What sign should you look for the most?
Unplanned urgency and requests to link devices or share codes.
Hoplon Insight Box: Practical Recommendations
• Treat every device linking request as sensitive
• Verify through a second channel
• Review linked devices weekly
• Educate high-risk users regularly.
• Assume trust can be exploited
Final Takeaway
A phishing attack using the Signal app does not mean Signal is unsafe. It means no tool can replace human judgment.
Encryption protects data in transit. Awareness protects decisions.
In a world where messaging apps shape real-world outcomes, slowing down and asking one extra question can make all the difference.
Most Signal phishing attacks work because the threat starts and ends on the phone. Strong mobile security helps find risky behavior. It stops people from linking their devices without permission. It also ensures that users use their devices safely. This way, no one can take over their messenger account. It focuses on where the attack happens, not after the damage is done.
Share this :