Protect Your Business from Ransomware Attacks Today

Hoplon InfoSec
07 Jun, 2025
What is Ransomware?
Definition
Ransomwares are a form of malicious software that prevents users from accessing their systems or files by encrypting them or locking the interface. A ransom is then demanded, typically in cryptocurrency, in exchange for restoring access. It’s a modern-day form of digital extortion that has rapidly evolved into a global cybersecurity crisis, affecting individuals, corporations, hospitals, universities, and government bodies alike.
Purpose and Motivation
The core motivation behind ransomwares are financial gain. Attackers exploit the critical importance of digital data, knowing that organizations will pay large sums to recover operational access and avoid legal or reputational consequences. In some variants, attackers also threaten to leak sensitive data publicly, increasing the pressure to pay.
Common Infection Methods
Ransomware often spreads through phishing emails, malicious attachments, fake software updates, infected websites, or exposed remote desktop services. Some advanced strains exploit software vulnerabilities to infiltrate networks without any user interaction. Once inside, ransomwares can rapidly spread laterally across systems and domains.
Rise of Organized Crime
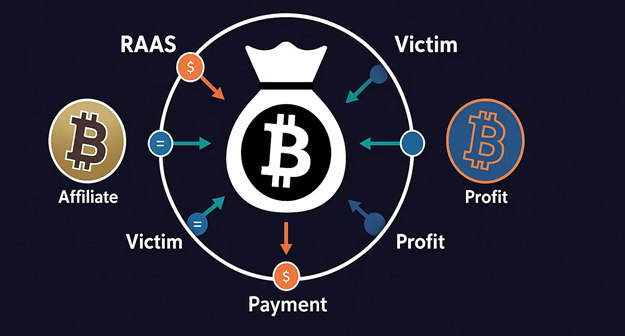
Today’s ransomware landscape is dominated by sophisticated cybercrime groups. These attackers operate like businesses, offering ransomware kits to affiliates in exchange for a share of the profits. Known as Ransomware-as-a-Service (RaaS), this model has industrialized attacks and lowered the technical barrier to entry, making ransomware more accessible and widespread.
Ransomware is no longer a singular threat, but a growing cyber ecosystem fueled by weak security practices, vulnerable infrastructure, and the anonymity of cryptocurrency. Understanding what it is and how it’s evolving is the first step toward building a proactive defense strategy.
Types of Ransomwares
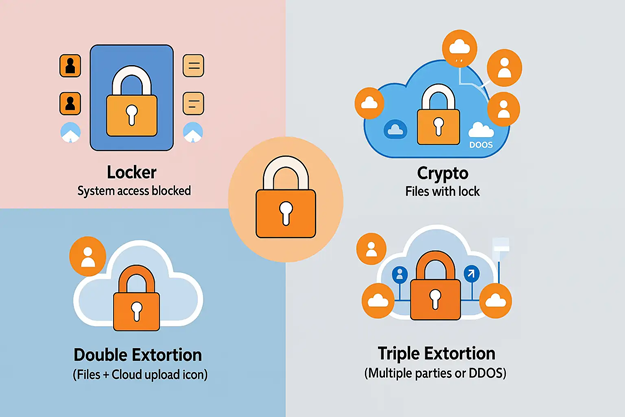
Locker Ransomware
This type of ransomware denies users access to their devices by locking the entire interface. Unlike other variants, it doesn’t encrypt files. Victims are prevented from using their keyboard, mouse, or desktop while being presented with a full-screen ransom message. Though less sophisticated, it can cause major disruption, especially if deployed on public-facing systems.
Crypto Ransomware
Crypto ransomware is the most common and dangerous type. It targets data rather than access, encrypting important files like documents, databases, and media, demanding a ransom for the decryption key. Victims often can’t restore data without backups or paying the ransom. Some variants even target cloud-based storage or backup systems.
Double Extortion Ransomware
Double extortion is an evolution of crypto ransomware. Here, the attacker not only encrypts data but also exfiltrates sensitive information. Victims are threatened with public leaks, regulatory action, or reputational damage if they refuse to pay. This makes the attack more damaging, even for those with good backups.
Triple Extortion Ransomware
In this latest variant, attackers apply pressure not only to the victim but also to third parties, such as customers, partners, or suppliers, by leaking their data or launching DDoS attacks. This tactic spreads liability and escalates urgency, forcing faster payouts.
Ransomware types are no longer just technical classifications; they represent different business strategies used by cybercriminals to maximize financial gain and psychological pressure.
Comparison of Ransomware Types
| Type | Mechanism | User Impact | Additional Threats |
| Locker Ransomware | Locks access to user interface | Device becomes unusable | No encryption of files |
| Crypto Ransomware | Encrypts files | Data becomes unreadable | Backup files may also be targeted |
| Double Extortion | Encrypts + steals data | Loss of access + threat of leaks | Regulatory/legal damage |
| Triple Extortion | Adds pressure on third parties | Multi-organization impact | DDoS or third-party compromise |
This table highlights how ransomware has evolved from basic file-locking to multi-tiered, highly pressurized extortion schemes. Each level brings increasing consequences and complexity to incident response.
What Are the Benefits? (From the Attacker’s Perspective)
High Return on Investment
Ransomware is incredibly profitable. Attackers can demand ransoms ranging from a few hundred to millions of dollars, often in cryptocurrency, which allows anonymous transactions. Even a small success rate results in massive profits due to low operational costs and global reach.
Scalable Operations
Through the RaaS model, developers create ransomware and lease it to affiliates who perform attacks. This makes ransomware scalable like a business franchise, developers write code, and “partners” spread infections. Everyone involved earns a cut, making it a lucrative criminal enterprise.
Low Risk of Prosecution
Most attackers operate from countries with weak or non-existent cybercrime enforcement. These jurisdictions don’t cooperate with international law enforcement, making it nearly impossible to identify or extradite criminals.
Control and Leverage
Encryption gives attackers direct control over critical files and services. Adding the threat of public data leaks via double extortion amplifies psychological pressure. Victims feel trapped and desperate, which often results in ransom payment.
Ransomware’s benefits for criminals, anonymity, scale, profit, and leverage are exactly why it remains one of the most dangerous and prevalent forms of cyberattack today.
Why Is Ransomware Important?

Widespread Impact
Ransomware attacks have global reach. They affect organizations of all sizes, from small clinics to large oil pipelines. Disruptions can shut down entire operations, delay public services, and even put lives at risk, especially in sectors like healthcare or transportation.
Financial Consequences
The cost of a ransomware attack goes far beyond ransom payments. Victims face downtime, recovery expenses, reputational damage, legal fees, and potential fines. The global cost of ransomware is expected to reach over $265 billion annually by 2031.
Regulatory and Compliance Risks
Leaked or exfiltrated data exposes companies to GDPR, HIPAA, or other compliance violations. In double or triple extortion attacks, this exposure escalates, leading to lawsuits and public backlash.
Cybersecurity Policy Transformation
Ransomware has changed how organizations approach cybersecurity. Companies are now investing more in incident response plans, zero-trust architectures, user awareness training, and continuous monitoring. Insurance providers are also increasing scrutiny on ransomware defenses before offering coverage.
The scale, frequency, and destructiveness of ransomware attacks make them a critical issue in both cybersecurity and operational resilience planning.
Key Features of Ransomware
Infection and Delivery
The lifecycle of a ransomware attack begins with infection. This typically occurs through phishing emails containing malicious links or attachments, drive-by downloads from compromised websites, or by exploiting unpatched vulnerabilities. Some attacks are initiated through exposed services like Remote Desktop Protocol (RDP), where weak or reused passwords are brute forced. These methods allow attackers to enter a system with minimal resistance or user awareness.
Execution and Persistence
Once inside the target system, the ransomware silently executes. It may elevate privileges, bypass endpoint protection, and install itself in hidden or protected directories. Persistence mechanisms such as scheduled tasks, registry edits, and disguised services ensure that the ransomware survives system reboots or manual removal attempts. This allows it to maintain a strong foothold in the environment.
Encryption Process
The ransomware scans the system and connects network drives for valuable files, including documents, images, spreadsheets, databases, and configuration files. Using strong encryption algorithms like AES or RSA, it encrypts these files and may rename or reformat them. Without the attacker’s private key, the encrypted data is rendered useless to the victim.
Ransom Demand and Communication
After encryption, the ransomware drops a ransom note, often in every affected directory or as a full-screen message. The note includes payment instructions, usually in cryptocurrency, a deadline and often threats to increase the ransom or delete files if demands are not met. Some variants provide a communication channel like a chat portal or email address to negotiate or confirm payment.
Spread and Lateral Movement
Sophisticated ransomware doesn’t stop at a single machine. It attempts to spread across the network by scanning for shared folders, mapping drives, or using harvested credentials to infect other endpoints and servers. This can lead to complete network compromise within hours.
Command and Control (C2)
Many modern ransomware strains communicate with remote command-and-control servers. These C2 systems manage encryption keys, track infection metrics, and allow attackers to send updates or commands. This central control enhances the attacker’s ability to adapt during an active breach.
Payment and Decryption Outcomes
Paying the ransom doesn’t guarantee results. Some victims receive working decryption tools; others receive partial recovery or nothing at all. In many cases, paying the ransom can increase the likelihood of future attacks, as the organization is marked as a profitable and cooperative target.
Forward Outlook

Ransomware remains one of the most dangerous cyber threats today. It can disrupt critical operations, leaking sensitive data, and causing immense financial and reputational harm. Its evolution from simple file encryption to complex extortion tactics, such as data theft and pressure on third parties, reflects how sophisticated and damaging these attacks have become.
Cybercriminals continue to exploit vulnerabilities and human error while benefiting from anonymity and weak enforcement in certain regions. At the same time, organizations are increasingly adopting stronger defenses, including zero trust architectures, endpoint protection, and regular backups.
While ransomware may never be completely eradicated, its impact can be significantly reduced through proactive planning, employee awareness, and resilient cybersecurity strategies. The key is to treat cybersecurity not as a reaction but as a foundational part of digital business continuity.
Share this :