Q1 2025 Vulnerability Landscape: A Surge in Exploited CVEs

Hoplon InfoSec
24 Apr, 2025
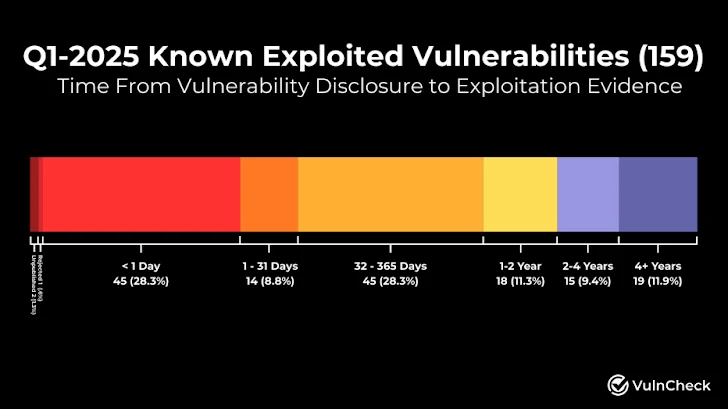
Did you know that in Q1 2025, security researchers flagged 159 distinct CVE identifiers (Common Vulnerabilities and Exposures) as having been actively exploited in the wild? This is an increase from the 151 exploited flaws recorded in Q4 2024. This continuing upward trajectory underscores the accelerating pace at which attackers weaponize newly disclosed software weaknesses.
VulnCheck, a leading vulnerability intelligence firm, notes that 28.3 percent of these flaws were used in live attacks within one day of their public disclosure. That equates to 45 vulnerabilities going from public record to real-world exploitation in just 24 hours. Another 14 were compromised within a month, and an additional 45 saw attacks within the year following disclosure.
The One-Day Threat Window with Q1 2025 Vulnerability
Why the First 24 Hours Matter
When a CVE goes public, vendors often race to issue patches—but attackers race even faster to reverse-engineer fixes and develop exploit code. The fact that nearly a third of all Q1 2025 CVEs were exploited within a single day highlights a critical “golden window” in which organizations remain highly vulnerable.
- Patch deployment delays: Even when a patch is available immediately, many enterprises require testing and change-control processes that can delay deployment by days or weeks.
- Exploit automation frameworks: Toolkits such as Metasploit and publicly shared proof-of-concept code dramatically lower the bar for attackers to craft reliable exploits.
- Target prioritization: Exploit developers tend to focus on high-impact flaws—those affecting widely deployed products or granting elevated privileges, amplifying risk.
Therefore, organizations must streamline their vulnerability management workflows, prioritizing rapid testing and deployment of critical fixes within hours rather than days.
Breakdown of Exploited Software Categories
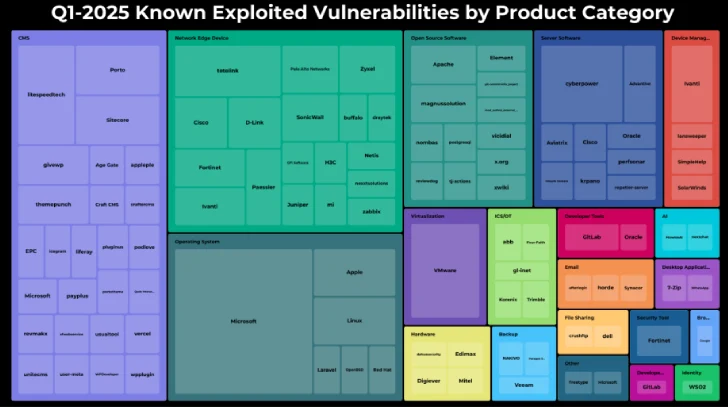
VulnCheck’s analysis groups the 159 exploited CVEs by the type of software they affect. The most heavily targeted categories in Q1 2025 were:
| Software Category | Number of Exploited CVEs |
|---|---|
| Content Management Systems | 35 |
| Network Edge Devices | 29 |
| Operating Systems | 24 |
| Open-Source Software | 14 |
| Server Software | 14 |
Content Management Systems (CMS) in the Crosshairs
With 35 CVEs exploited, CMS platforms topped the list. Popular web-publishing systems frequently run third-party plugins and themes, creating a sprawling attack surface. Once compromised, these platforms can serve malware to site visitors, harvest credentials, or pivot deeper into corporate networks.
Network Edge Devices Under Siege
Attackers targeted 29 CVEs in routers, firewalls, VPN concentrators, and other edge appliances. Vulnerabilities in these devices often allow remote code execution or authentication bypass, opening the door for network-level compromise, data interception, and lateral movement.
Operating Systems and Beyond
Twenty-four OS flaws saw exploitation, including both client and server editions of primary desktop and server operating systems. Meanwhile, a combined 28 CVEs in open-source libraries and server applications rounded out the most exploited categories, illustrating that no layer of the stack is safe.
Top Vendor Products Affected
Among exploited products, the leading vendors and vulnerable applications in Q1 2025 were:
- Microsoft Windows – 15 CVEs exploited
- Broadcom VMware – 6 CVEs exploited
- CyberPowerPanel – 5 CVEs exploited
- LiteSpeed Technologies – 4 CVEs exploited
- TOTOLINK Routers – 4 CVEs exploited
High-profile Microsoft Windows flaws remain perennial favorites for attackers due to the ubiquity of the platform. Virtualization software from Broadcom (VMware) also attracted sustained interest, as successful exploits can subvert entire data-center infrastructures.
CISA’s KEV Catalog and Public Exploitation Evidence
Weekly Disclosure Rates and KEV Growth
Over Q1 2025, VulnCheck observed an average of 11.4 Known Exploited Vulnerabilities (KEVs) disclosed per week, amounting to approximately 53 per month. The U.S. Cybersecurity and Infrastructure Security Agency (CISA) added 80 new entries to its KEV catalog during the quarter; of these, only 12 had no prior public evidence of active exploitation.
This suggests that the majority of KEVs tracked by CISA were already weaponized before formal cataloging, reinforcing the need for organizations to monitor exploit trends independently rather than relying solely on government lists.
Deferred and Pending Analysis Status
- 25.8 percent of Q1 2025 exploited CVEs are still awaiting or undergoing detailed analysis by the NIST National Vulnerability Database (NVD).
- 3.1 percent have been assigned a new “Deferred” status, indicating that scoring and impact assessment remain on hold.
These lagging classifications can hinder accurate risk prioritization, as lacking a CVSS score complicates comparing and triaging newly disclosed flaws.
Exploitation in Data Breaches: Industry Reports
Verizon DBIR 2025 Findings
According to the Verizon Data Breach Investigations Report (DBIR) 2025, exploitation of vulnerabilities as the initial access vector in data breaches grew by 34 percent year-over-year, representing 20 percent of all documented intrusions. Attackers increasingly favor direct exploitation over traditional phishing or social-engineering techniques when high-value targets are patched slowly.
Mendiant’s Perspective on Initial Infection Vectors
Data from Google-owned Mandiant confirms that exploits remained the most frequently observed initial infection vector for the fifth consecutive year. Although stolen credentials have overtaken phishing as the second-most common vector, vulnerability exploitation still accounts for a substantial share of incidents.
- In Q1 2025, 33 percent of intrusions with a known initial vector began with exploit activity.
- This marks a slight drop from 38 percent in 2023 but aligns closely with the 32 percent observed in 2022.
Evolving Defender Capabilities
Median Dwell Time Trends
Despite attackers’ growing sophistication, incident response and detection capabilities have improved. The global median dwell time—the number of days an attacker remains undetected on a compromised system—stood at 11 days in Q1 2025, up just one day from 2023. While any unauthorized presence is cause for concern, maintaining a two-week detection window represents progress compared to historical averages that once stretched into months.
Recommendations for Security Teams
- Accelerate Patch Management
- Implement automated patch-testing pipelines for critical CVEs.
- Leverage virtual patching or compensating controls (WAF rules, IPS signatures) during test cycles.
- Enhance Threat Intelligence Integration
- Subscribe to real-time exploit feeds and KEV updates.
- Map threat data to your asset inventory to prioritize high-risk systems.
- Strengthen Perimeter and Endpoint Defenses
- Deploy behavior-based detection capable of spotting exploit attempt patterns (e.g., anomalous memory operations).
- Monitor network edge devices for unusual configuration changes or firmware tampering.
- Reduce Dwell Time
- Increase the frequency of internal threat hunts focusing on indicators of exploitation (IOEs).
- Correlate SIEM alerts with threat intel on newly disclosed CVEs to catch fast-moving attacks.
Conclusion
Q1 2025’s record of 159 exploited CVEs, 35 more than the same quarter in 2024, drives home a stark reality: software vulnerabilities continue to be the easiest and most effective entry point for attackers. The fact that nearly a third of flaws are weaponized within 24 hours demands that organizations rethink traditional patch-management cycles.
By combining accelerated vulnerability remediation with robust detection, threat-intelligence integration, and targeted hardening of high-risk systems (CMS platforms, network edge devices, and widely deployed OSes), security teams can begin to close the gap between disclosure and compromise. As attackers refine their automation and exploitation toolkits, defenders must respond with equal agility, ensuring that the window of vulnerability never remains open long enough to invite a breach.
Share this :