Quantum Computing Threats, Benefits in Cybersecurity: Understanding the Risks and Opportunities

Hoplon InfoSec
25 Jun, 2025
Quantum computing is rapidly transitioning from a theoretical marvel to a practical force capable of transforming multiple industries. Fueled by advances in quantum physics, engineering, and computer science, quantum computers harness a radically different set of principles compared to classical machines. While their power promises revolutionary benefits in science, optimization, and communication, it also introduces significant cybersecurity concerns. The arrival of large-scale quantum computing could compromise the cryptographic foundations that protect digital communications, financial transactions, healthcare data, and government secrets.
This article explores quantum computing threats in depth by analyzing what they are, their potential benefits, why they are critically important, the key features that enable both power and peril, and the fundamental mechanics of how quantum computing works.
What are the Quantum Computing threats in Cybersecurity?

An Emerging Cybersecurity Challenge
Quantum computing threats refer to the emerging risks to data confidentiality, digital infrastructure, and global security that arise from the unique capabilities of quantum computers. Unlike classical computers, which perform computations sequentially using binary bits (0 or 1), quantum computers use quantum bits (qubits) that exploit superposition and entanglement. These properties allow them to perform many calculations in parallel, making them capable of solving specific problems exponentially faster than traditional machines.
Breaking Modern Encryption
One of the most critical areas where quantum computing poses a threat is cryptography. Most of the encryption standards in use today, such as RSA, Diffie-Hellman, and Elliptic Curve Cryptography (ECC), are based on mathematical problems that are extremely difficult for classical computers to solve. These include factoring large integers and computing discrete logarithms. A powerful quantum computer could run Shor’s algorithm, which dramatically accelerates the factoring of large numbers, thereby rendering RSA and ECC ineffective.
This issue is not just a future concern. Data encrypted today can be intercepted and stored by malicious actors who anticipate the eventual availability of quantum decryption tools. This tactic, known as “Harvest Now, Decrypt Later,” presents a time-bomb scenario: once quantum capability is achieved, previously secure data could be rapidly decrypted.
Expanding the Threat Landscape
In addition to breaking cryptography, quantum computing could give rise to more advanced quantum malware, stealthy surveillance, and AI-driven quantum cyberattacks. Scientists could harness the same power to circumvent network defenses, jeopardize critical infrastructure, and undermine trust in digital systems.
What Are the Benefits of Quantum Computing?
Scientific Discovery and Materials Engineering
One of the most compelling promises of quantum computing lies in its ability to simulate quantum systems, something classical computers struggle with. For example, modeling the behavior of molecules or materials at the atomic level can lead to discoveries in drug development, battery chemistry, and climate modeling. Pharmaceutical companies are already investing in quantum research to shorten drug discovery timelines and reduce the cost of bringing new therapies to market.
Transforming Optimization and Logistics
Quantum algorithms can optimize complex systems far more efficiently than their classical counterparts. This has vast implications for industries such as logistics, finance, energy, and transportation. For instance, companies like Volkswagen and FedEx are exploring quantum computing to optimize delivery routes, warehouse layouts, and fleet operations in real time.
Boosting Artificial Intelligence Capabilities
AI and quantum computing can reinforce each other. Quantum-enhanced machine learning could drastically reduce the time required to train deep learning models and detect anomalies. In cybersecurity, this could mean faster identification of threats and better automated responses. In healthcare, it could improve diagnostics by recognizing patterns in massive datasets with greater accuracy.
Secure Communication Through Quantum Mechanics
Although quantum computers threaten existing encryption, they also support more secure communication protocols such as Quantum Key Distribution (QKD). QKD relies on the rules of quantum entanglement and measurement to make sure that if someone tries to intercept a message, it will be noticed right away, offering a way to create communication systems that are almost impossible to break.
Important about Quantum Computing in Cryptocurrency?
Quantum computing is not just a scientific breakthrough; it is a strategic asset. Countries including the United States, China, Germany, and Canada are pouring billions of dollars into national quantum initiatives. The first nation to achieve large-scale, fault-tolerant quantum computing will have a competitive advantage in cybersecurity, intelligence gathering, financial forecasting, and even military planning.
Potential to Cripple Digital Infrastructure
Most of our internet infrastructure relies on public-key cryptography. Falling encryption systems could compromise everything from online banking to secure emails, medical records, cloud platforms, and blockchain networks. Such a situation is not a minor inconvenience; it is a catastrophic scenario that could result in massive data breaches, financial loss, identity theft, and geopolitical instability.
Slow Cryptographic Migration
Transitioning to post-quantum cryptography (PQC) is not easy. It involves updating every software platform, hardware device, and communication protocol that uses legacy encryption. Government agencies like the U.S. National Institute of Standards and Technology (NIST) are working to standardize quantum-resistant algorithms, but adoption across industries is lagging. The longer organizations delay preparation, the more vulnerable their data becomes to future quantum attacks.
Implications for Future Technologies
Technologies such as blockchain, IoT, autonomous vehicles, and smart grids are built on encrypted communication. If those encryption methods become obsolete, these future-defining technologies could become points of failure instead of progress.
Key Features of Quantum Computing That Enable Its Threat Potential

Superposition: Parallel Problem Solving
Superposition allows each qubit to represent both 0 and 1 simultaneously. This enables a quantum system to evaluate many inputs at once. For instance, a 20-qubit quantum computer can represent over one million combinations simultaneously. This exponential scalability is what allows quantum computers to outperform classical machines for certain types of problems.
Entanglement: Interconnected Calculations
Entangled qubits are linked such that the state of one immediately influences the state of the other, even across vast distances. This allows quantum computers to carry out complex operations in coordinated ways that are impossible with independent classical bits.
Quantum Interference: Filtering the Correct Solution
Quantum algorithms use interference to amplify correct answers and suppress incorrect ones. This process allows quantum computers to narrow down results efficiently after exploring many options in parallel, a capability especially useful in search and optimization.
Quantum Algorithms: Breaking the Unbreakable
The most famous example is Shor’s algorithm, which can factor large integers exponentially faster than any classical method. This renders RSA and ECC, which rely on the hardness of such problems, vulnerable. Meanwhile, Grover’s algorithm offers a quadratic speedup for brute-force attacks on symmetric encryption like AES, reducing its effective security level.
Hardware Complexity and Error Sensitivity
Quantum computers are delicate machines. Qubits are extremely sensitive to heat, noise, and electromagnetic interference. Maintaining a stable quantum system requires cryogenic cooling, precise calibration, and constant error correction. As such, current quantum devices are still experimental and limited in power.
Comparison Table: Classical vs. Quantum Computers
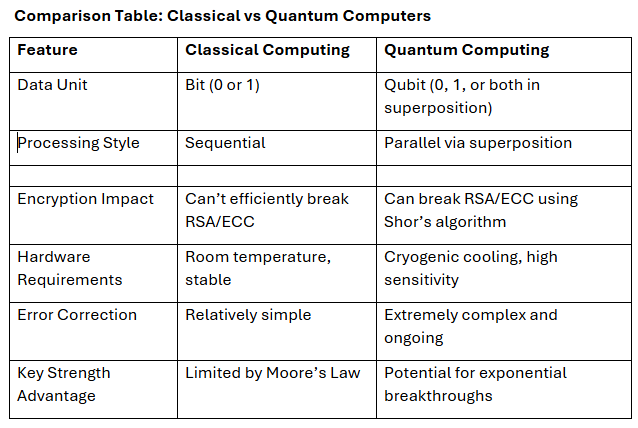
Classical Computing
How Does Quantum Computing Work?
Qubits and Their Quantum Nature
A qubit is the basic unit of quantum information. It can exist in multiple states at once thanks to superposition. When qubits are entangled, their states are linked in a way that enables a level of coordinated computation far beyond classical limits. These phenomena allow quantum computers to explore vast solution spaces rapidly.
Quantum Logic and Computation
Instead of using classical logic gates like AND, OR, and NOT, quantum computers use quantum gates such as Hadamard, Pauli-X, and CNOT. These gates manipulate the state of qubits through rotation and interference, forming the building blocks of quantum circuits.
Measurement and Probabilistic Outcomes
Quantum computations yield probabilistic results. When a qubit is measured, it collapses into a definitive state, either 0 or 1. Because of this, quantum algorithms are often executed multiple times to build confidence in the output. The probability of correct outcomes increases with each run and clever use of interference.
Building a Working Quantum Computer
There are several approaches to building quantum computers. The most common include
- Superconducting Qubits (used by IBM and Google)
- Trapped Ions (used by IonQ)
- Photonic Systems (being explored by Xanadu)
Each has trade-offs in terms of error rates, speed, and scalability. All approaches require quantum error correction, a critical component that helps protect fragile quantum information from degradation.
Current Limitations and the Road Ahead
Despite incredible progress, today’s quantum computers are still Noisy Intermediate-Scale Quantum (NISQ) devices. They are powerful for experimentation but not yet practical for widespread application or cryptographic threats. However, progress is accelerating, and experts estimate that powerful quantum systems could emerge within the next 10–15 years, or even sooner.
Conclusion: Preparing for the Quantum Future
Quantum computing will fundamentally reshape the way we process, secure, and interact with information. Its power to solve problems considered intractable by classical computers makes it one of the most exciting scientific advancements of our time. But this power comes with real risks, particularly to digital security and encryption.
Organizations, governments, and individuals must prepare now. This means investing in post-quantum cryptography, monitoring the evolution of quantum hardware, and beginning the complex process of migrating vulnerable systems. If you want to learn more click here.
The question is no longer whether quantum computing will arrive but whether we’ll be ready when it does.
Resources:
Palo Atto
Tech Trget
Share this :