Ransomware Protection Services: Why Attacks Are Rising Again in 2026

Hoplon InfoSec
26 Jan, 2026
I’ve heard variations of the same story from IT folks for years, and it usually starts small.
It starts with a weird login alert that someone dismisses because it is Friday and the helpdesk is buried. Or a patch that gets postponed because “nothing ever happens.” Or a vendor portal that needs one more exception to keep a workflow running.
Then Monday hits. Files open slowly. A few shared folders look scrambled. Someone jokes about “another Microsoft update.”
And then the note appears.
That is why the best ransomware strategy is boring on purpose. It is backups. It is identity control. It is patching. It involves logging activities that are actually reviewed by someone. It is rehearsing a response plan, like you would rehearse a fire drill. Government guidance emphasizes exactly these kinds of practical controls and checklists because they work across industries and budgets.
How ransomware attacks usually begin
1) Exploited vulnerabilities, the “left the window open” problem
Sophos reports that exploited vulnerabilities were the most common technical root cause cited by victims in their 2025 survey.
This is not always a fancy zero-day. Often, an internet-facing system harbors a known flaw. Managed file transfer tools, VPN appliances, and perimeter devices show up again and again in incident write-ups because they are reachable from the outside and often under-patched.
The Cl0p group exploits the widely documented MOVEit Transfer vulnerability CVE-2023-34362 for mass data theft and extortion. Even in situations where encryption is not the primary event, the threat of extortion remains real.
2) Compromised credentials, the “someone guessed the key” problem
Passwords get reused. MFA gets skipped for one “special” admin. A former contractor’s account is never fully closed out. It happens in the real world because people are busy.
Sophos lists compromised credentials as a major perceived attack vector, and phishing and malicious emails remain common paths of entry.
3) Phishing and social engineering, the “human moment” problem
Phishing is not just bad spelling and suspicious links anymore. It is invoices, HR forms, fake vendor threads, and believable prompts that match your workflow.
Even when the initial email is blocked, attackers often pivot to credential stuffing, MFA fatigue prompts, or remote access tooling once they have a foothold. Optiv describes familiar initial access patterns like phishing, exploiting vulnerabilities, and leveraging exposed services.
-20260126063648.webp)
Why “ransomware is rising again” feels true in 2026
One reason this topic keeps returning is that ransomware changes shape.
Sometimes it is a loud encryption. Sometimes it is quiet data theft plus a threat to leak. Sometimes it is a supplier compromise that spreads pain downstream.
Optiv’s Q1 2025 analysis reported a jump in victims listed on leak sites, along with shifts in which groups dominated leak activity, and noted the rise of double extortion and ransomware-as-a-service dynamics.
Sophos also points out that exploited vulnerabilities and email-based vectors remain consistent, which is frustrating because it means the basics still matter.
Attack entry points. cited by
Source: Sophos State of Ransomware 2025 (survey of 3,400 orgs hit).
Exploited vulnerabilities |█████████████████████| 32%
Compromised credentials |████████████████ | 23%
Malicious email |█████████████ | 19%
Phishing |████████████ | 18%
“Heatmap” of common risk areas
“Darker” means “more commonly involved in real incidents,” based on recurring themes in CISA guidance and industry reporting.

The cost question people avoid saying out loud
Let’s be honest. The reason for the keyword ransomware protection services cost trends is that budgets are real.
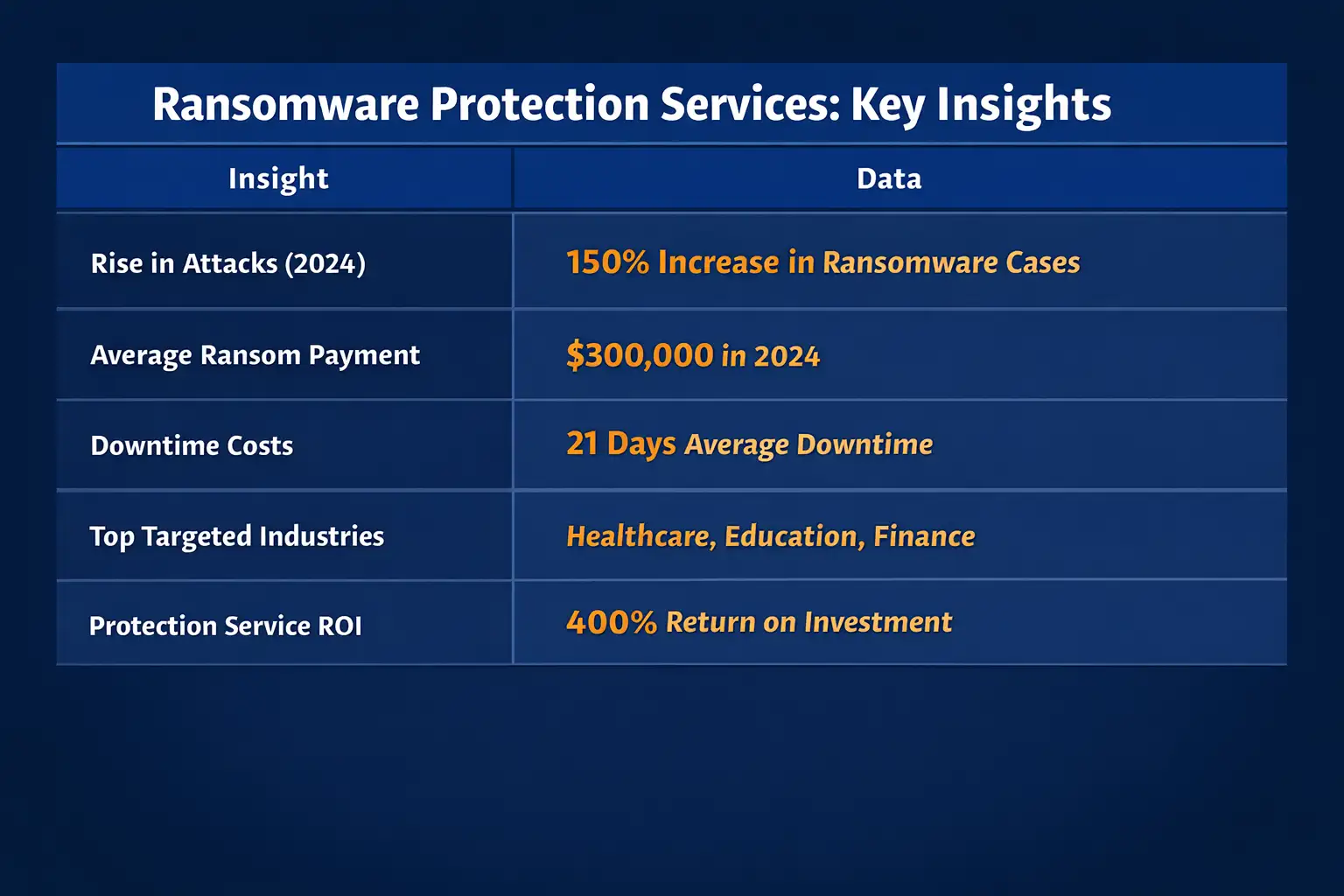
Sophos reported an average (mean) recovery cost excluding ransom payments of $1.53 million in their 2025 findings and noted improved recovery speed for many victims, with over half recovered within a week in their survey.
That does not mean your business will see that exact number. It depends on size, industry, downtime tolerance, insurance, backups, and whether data was stolen. But it gives a grounded way to talk about ROI: if your downtime costs $50,000 a day and your recovery takes two weeks, you do not need a spreadsheet genius to see why prevention spending can be rational.
This is one of the strongest reasons to evaluate ransomware protection services as a business continuity purchase, not a “security toy.”
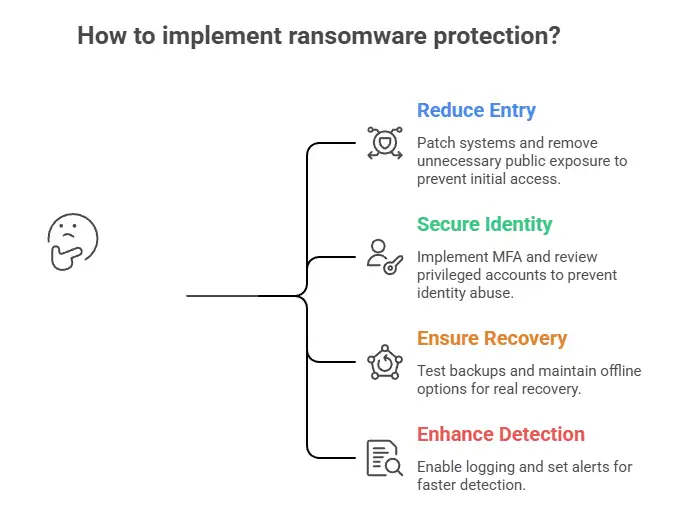
A practical checklist: what to do this week, not “someday.”
Here is a simplified version that maps cleanly to what good ransomware protection services should help you execute:
Step 1: Reduce easy entry
Patch the systems attackers love: internet-facing appliances, VPNs, file transfer tools, and remote access paths.
Remove unnecessary public exposure. If it does not need to be internet-facing, do not make it internet-facing.
Step 2: Make identity harder to abuse
Require MFA for admins and remote access.
Review privileged accounts and remove “just in case” access.
Watch for impossible travel, repeated auth failures, and new admin creation.
Step 3: Make recovery real, not imaginary.
Backups must be tested, not just “present.”
Keep offline or immutable backup options.
Practice restoring a critical system, end-to-end, with a stopwatch.
Step 4: Make detection faster
Turn on logging; you can actually use it.
Alert on mass file changes, unusual encryption behavior, and suspicious tool execution.
If you do not have 24/7 coverage, consider managed monitoring.
This is where ransomware protection services can be the difference between “we had logs somewhere” and “we contained it within 30 minutes.”
What a “good” ransomware response looks like in the first hour
CISA’s response checklists and Microsoft’s incident-focused guidance emphasize sequencing and containment.
Here is a realistic first-hour flow you can adapt:
1. Confirm it is real. Do not assume. Check a second machine, check file shares, and check alerts.
2. Isolate affected devices fast. Disconnect from the network, disable compromised accounts, and stop lateral spread.
3. Preserve evidence. Take notes, save logs, and snapshot systems if possible.
4. Communicate internally with one source of truth. Chaos is the enemy.
5. Decide whether law enforcement or regulators need to be involved. This depends on jurisdiction and sector.
6. Start recovery planning while containment is ongoing. These efforts can run in parallel.
Organizations without a plan often lose time arguing about who is in charge. That is why ransomware protection services often include a retainer or readiness package: you are buying time and clarity before the crisis.
Key technical details that are safe to mention publicly
To keep this factual and not speculative, here are examples that are widely documented and relevant:
CVE-2023-34362 (MOVEit Transfer) was exploited in a major extortion campaign attributed to the Cl0p group, prompting joint advisories and extensive coverage.
Ransomware operations often rely on common initial access patterns such as phishing, exploiting vulnerabilities, exposed services, and “initial access brokers,” as described in threat intelligence reporting.
Guidancee continues to emphasize practical prevention and response checklists, including preparation, mitigation, and recovery steps.
If you have a specific incident you are writing about, only include a threat actor name or malware family when it is publicly confirmed by reputable sources. Otherwise, keep it generic and focus on tactics.
How to choose ransomware protection services without getting burned
Here’s my blunt take. If a provider cannot explain what happens on a bad day, they probably have not lived through one.
When evaluating ransomware protection services, ask for evidence of these capabilities:
1) Clear scope
Do they cover identity hardening, patch prioritization, detection, and recovery, or just “monitoring”?
If the service ends at “we send alerts,” that is not protection. That is a fancy notification.
2) Real response support
Do they offer an incident response retainer or a guaranteed path to expert help? Who actually picks up the phone?
A strong partner is specific about time-to-engage, escalation paths, and what you need ready on your side.
3) Recovery competence
Can they help verify adversary eviction, not just restore backups? Microsoft’s guidance on human-operated ransomware stresses complete eviction, because partial cleanup leads to repeat compromise.
4) Proof of practice
Do they run tabletop exercises? Do they review backups? Do they test restores?
A service that never practices recovery is like a fire department that only owns hoses.
FAQs
How do you protect against ransomware?
Start with patching internet-facing systems, strong identity controls like MFA, tested backups, and monitoring that can spot abnormal behavior quickly. CISA’s #StopRansomware guidance breaks this into practical prevention and response steps.
Should you pay the ransom?
There is no universal answer, and guidance varies by situation and legal context. Many organizations recover without paying, and payment can encourage further crime. Sophos reports that many victims do pay, but recovery paths also include backups and other methods.
What is the best defense against ransomware?
A layered approach. Patching and identity controls reduce entry, backups reduce impact, and monitoring reduces dwell time. Microsoft’s guidance emphasizes urgent configuration steps and structured hardening.
How long does ransomware recovery take?
It depends on how widespread the compromise is and how ready you are. Sophos reportsthat many victims recovered within a week in their 2025 survey, but that is not guaranteed for every organization.
Hoplon Insight Box, January 2026
1. Treat patching like a revenue-protection activity, not a maintenance chore. Focus on the systems that face the internet first.
2. Run a backup restore test that includes one “business-critical” system. Time it. If it takes two days, write that down and plan around it.
3. Lock down admin accounts and remote access. MFA is not optional anymore.
4. If you cannot monitor 24/7, look at ransomware protection services that include response help, not just dashboards.
5. Write a one-page “first hour” plan and print it. A real incident is not the time to hunt through SharePoint.
Chainalysis found that ransomware attackers pulled in over $1 billion in 2023 in extorted cryptocurrency payments, highlighting how financially motivated and persistent this ecosystem remains.
That single data point explains a lot. When the business model works, attackers keep iterating. It also explains why defenders need repeatable fundamentals, not one-off heroics.
Final takeaway
If you only remember one thing, make it this: ransomware is less like a lightning strike and more like a house fire risk. Most of the time, the causes are boring and preventable, and the damage is worse when the response is improvised.
Build a baseline of patching discipline, identity control, tested backups, and monitored detection. If your team cannot sustain that alone, ransomware protection services can be a practical bridge between “we hope we’re fine” and “we can actually handle this.”
Some organizations also work with independent cybersecurity firms, for example, Hoplon InfoSec, for incident response and forensic support when dealing with complex ransomware cases.
Share this :