Maximize Protection with Reliable Endpoint Security Solutions

Hoplon InfoSec
10 Jun, 2025
Endpoint security refers to the comprehensive protection of devices (endpoints) such as laptops, desktops, mobile phones, and servers against cyber threats. As organizations become increasingly digitized and employees work from diverse locations, each endpoint becomes a potential entry point for attackers. Endpoint security solutions safeguard these devices to ensure the security of corporate data and maintain network integrity.
Key aspects of endpoint security include:
- Continuous monitoring: Devices are constantly analyzed for suspicious activity or anomalies.
- Threat prevention: Tools like antivirus and anti-malware protect endpoints from known and emerging threats.
- Policy enforcement: Security policies are enforced to control device behavior and data access.
- Remote management: Centralized consoles allow security teams to manage and update all endpoints, regardless of location.
Endpoint security is not a single product but a suite of tools and practices working together. By combining real-time protection, threat intelligence, and policy enforcement, endpoint security creates a secure perimeter around every device. This prevents cybercriminals from exploiting vulnerabilities or compromising sensitive information.
Given the growing complexity of IT environments, ranging from in-office devices to cloud-connected resources, endpoint security has become an essential part of modern cybersecurity strategies. It acts as the first line of defense against malware, ransomware, data breaches, and insider threats, significantly reducing the risk of incidents that can cause reputational and financial damage.
What are the Benefits of Endpoint Security?
Endpoint security delivers significant benefits to organizations of all sizes, making it a cornerstone of a robust cybersecurity strategy. By providing comprehensive protection for endpoints, it enhances the resilience of an organization’s digital infrastructure and ensures data integrity.
Key benefits include:
- Proactive threat detection and prevention:
Endpoint security uses advanced detection techniques to identify and neutralize malware, ransomware, phishing, and zero-day attacks before they can cause harm. - Data protection and privacy:
Data encryption and secure storage keep sensitive data safe, even if an endpoint is lost or stolen. - Regulatory compliance:
Helps organizations meet requirements under regulations like GDPR, HIPAA, and PCI DSS. - Reduced incident response time:
Automated threat detection and response capabilities allow faster containment and mitigation of threats. - Remote work support:
Endpoint security ensures secure connections and device compliance, supporting remote and hybrid work environments. - Improved productivity:
With secure, functioning endpoints, employees can work without disruptions caused by security incidents.
Ultimately, endpoint security provides peace of mind by reducing the risk of financial loss, reputational damage, and regulatory penalties. By investing in a comprehensive endpoint security solution, organizations can stay ahead of cyber threats and maintain operational continuity.
Why is Endpoint Security Important?
In today’s interconnected world, endpoint security has become essential for businesses and organizations to thrive. With cyber threats becoming increasingly sophisticated, every device represents a potential attack vector that can be exploited to access sensitive data or disrupt operations.
Reasons why endpoint security is critically important:
- Endpoints are the frontline:
Devices such as laptops and smartphones are often the first target for attackers trying to gain access to a network. - Growing remote work environment:
As remote work expands, endpoints operate outside traditional security perimeters, making them more vulnerable. - Data security concerns:
Compromised endpoints can lead to data breaches, exposing sensitive business information or customer data. - Insider threats:
Endpoint security helps identify and mitigate threats posed by insiders who may misuse or mishandle data. - Compliance and legal risks:
Failure to secure endpoints can result in significant fines and reputational damage for violating privacy and security regulations.
Without robust endpoint security measures, organizations expose themselves to financial, legal, and reputational risks. Investing in endpoint security is not just a technical decision; it’s a strategic necessity that safeguards long-term business success.
Key Features of Endpoint Security

Effective endpoint security solutions integrate a wide range of features designed to provide holistic protection for every device in an organization’s network. These features work together to detect, prevent, and respond to evolving cyber threats.
Essential features include:
- Antivirus and anti-malware:
Scans and removes malicious software, including ransomware and spyware. - Firewall protection:
Controls incoming and outgoing network traffic to block unauthorized access. - Data encryption:
Protects sensitive data stored on endpoints by encrypting files and drives. - Application control:
Prevents unauthorized or risky applications from running on endpoints. - Device control:
Manages and restricts the use of external devices like USB drives, reducing the risk of data leakage. - Behavioral analysis:
Detects unusual or suspicious behavior that may indicate a compromise. - Patch management:
Ensures endpoints are updated with the latest security patches and software updates. - Remote wipe and lock:
Provides the ability to erase data or lock devices if they are lost or stolen.
These features, when combined, create a powerful and proactive security framework. They help organizations stay ahead of sophisticated cyber threats while ensuring compliance and protecting critical data assets.
How Does Endpoint Security Work?
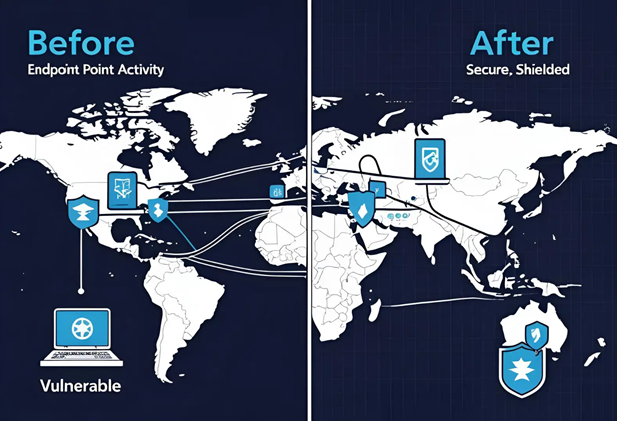
Endpoint security works through a combination of software agents installed on devices and a centralized management system that oversees security policies and updates. This integrated approach allows organizations to maintain comprehensive visibility and control over their endpoint environments.
Here’s how it works:
- Agent installation:
Each endpoint device has a lightweight agent that continuously monitors activity, enforces policies, and scans for threats. - Real-time threat detection:
The agent uses advanced algorithms to detect and block known and unknown threats in real-time. - Centralized management:
Security teams use a console to manage all endpoints, deploy updates, and respond to incidents from a single interface. - Automated response:
When a threat is detected, the agent can isolate the affected endpoint, remove malware, or initiate data encryption. - Reporting and analytics:
Provides detailed logs and insights into endpoint health, threat activity, and compliance status. - Integration with broader security stack:
Endpoint security solutions often integrate with other security tools (SIEM, EDR, threat intelligence) to provide a unified defense.
This layered approach ensures that each endpoint is actively protected while contributing to the overall security posture of the organization. By combining real-time detection, proactive defenses, and automated response, endpoint security stops attacks before they can spread or cause significant damage.What is Endpoint Security?
Share this :