Russian Hackers Ramp Up Cyber Espionage, Warn Microsoft and Dutch Agencies

Hoplon InfoSec
28 May, 2025
Are you aware about the Russian Hackers? A sweeping investigation released in May 2025 by Microsoft and Dutch intelligence agencies (AIVD and MIVD) has revealed a surge in Russian state-backed cyber-espionage activities across Europe, North America, and NATO-aligned states. These multifaceted offensive weaves together decades-old tradecraft with modern cloud abuse, stolen credentials, and increasingly professionalized tactics.
At the heart of these revelations are two interconnected storylines: the quiet, persistent data theft campaigns of Void Blizzard (also tracked as Laundry Bear) and the raucous, propaganda-fueled return of Killnet, now rebranded as a hybrid hacktivist-mercenary collective.
The Rise of Void Blizzard (Laundry Bear): From Stolen Credentials to Geopolitical Espionage
Void Blizzard/Laundry Bear represents a new chapter in Russian cyber warfare—an actor that fuses low-sophistication entry points with advanced cloud-native exploitation.
A Clear Strategic Mission:
Dutch intelligence assessments conclude that Laundry Bear’s operations are laser-focused on:
- Intelligence gathering for the Russian military effort in Ukraine, particularly Western weapons procurement and shipment data.
- Exfiltration of strategic communications across diplomatic and defense sectors.
- Undermining trust in Western institutions by compromising sensitive governmental and industrial data.
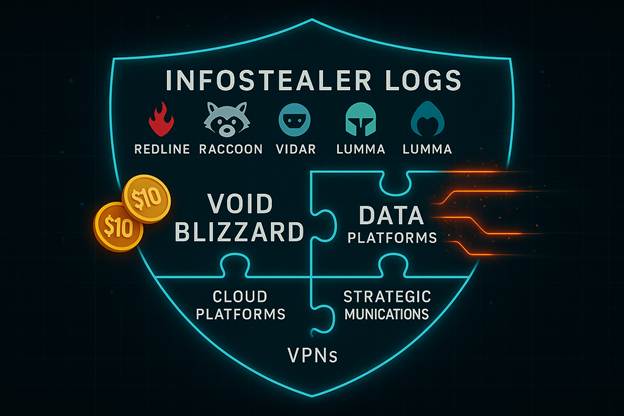
Entry Points: Infostealer Markets Fuel Initial Access
Void Blizzard does not rely on custom-developed implants or zero-day exploits. Instead, they leverage the massive underground market of infostealer logs. These logs often sold for as little as $10are sourced from low-level malware families (like RedLine, Raccoon Stealer, Vidar, and Lumma) and contain:
- Stolen credentials for corporate email, cloud platforms, and VPNs.
- Browser-saved passwords, cookies, and session tokens.
- Auto-fill data and OS-level clipboard information.
This approach illustrates a blurring of boundaries between state-backed espionage and financially driven cybercrime ecosystems. Russian APTs increasingly depend on this commoditized cybercrime infrastructure to launch state-directed campaigns.
Beyond the Perimeter: Exploiting Cloud APIs and Session Hijacking
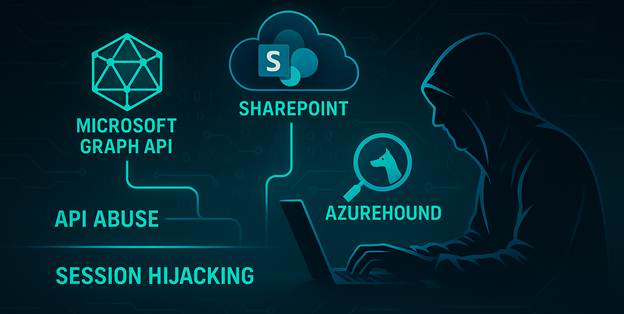
Once initial access is secured often through password spraying or credential stuffing; Void Blizzard uses legitimate tools and APIs to conduct deep reconnaissance and data theft:
- Microsoft Graph and Exchange Online APIs: Used for silent enumeration of mailboxes and downloading of all accessible data; bypassing typical endpoint detection.
- SharePoint Online and OneDrive: Attacks pivot to corporate file shares and collaborative workspaces, exploiting inherited permissions and misconfigured sharing.
- AzureHound (an open-source variant of BloodHound): Mapping entire Entra ID (Azure AD) environments to identify privileged accounts, delegated permissions, and nested group memberships.
This living-off-the-land approach minimizes the need for malicious binaries or implants; a key to stealthy, long-term espionage.
Adversary-in-the-Middle (AitM) Sophistication: Evilginx Campaigns
Void Blizzard has evolved beyond simple credential phishing to deploy AitM phishing using the Evilginx framework (publicly available since 2017). Evilginx acts as a transparent proxy between the victim and legitimate login portals, enabling:
- Harvesting of user credentials (username and password).
- Stealing MFA tokens and session cookies—bypassing even robust MFA protections.
- Continuous access to compromised accounts, including after password resets (until tokens expire or are revoked).
Recent campaigns included highly targeted spear-phishing lures themed as invitations to European defense summits sent with malicious QR codes that redirected to typo-squatted domains.
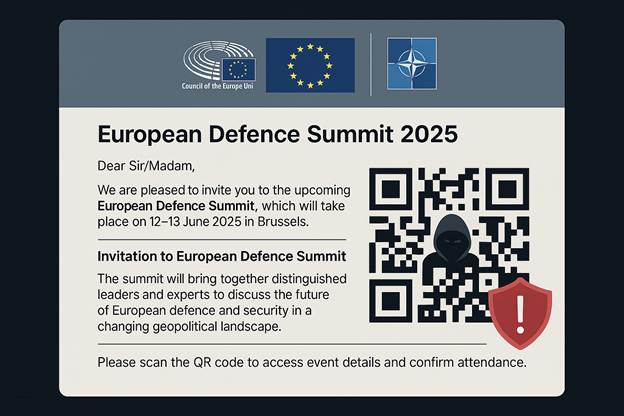
Laundry Bear’s Focused Espionage Operations: A Timeline of Precision
The Dutch Police breach (September 2024) offers a telling example of Void Blizzard’s precision:
- Attackers gained access through a stolen session cookie—likely purchased from infostealer markets.
- They pivoted directly to the Global Address List (GAL), harvesting contact information for all police personnel—critical for future social engineering attacks or targeting of law enforcement operations.
Similarly, Laundry Bear’s campaigns against Ukrainian aviation and transport agencies mirror Russia’s historical focus on airpower intelligence, dating back to Cold War-era targeting of NATO’s air and missile defense networks.
Geopolitical Implications: APT Convergence and Russian State Strategy
Void Blizzard’s activities overlap significantly with targets of APT28 (Fancy Bear) and APT29 (Cozy Bear), suggesting a coordinated intelligence mandate:
- APT28: Historically tied to the Russian military intelligence service (GRU), focused on battlefield and strategic defense intelligence.
- APT29: Linked to the Russian Foreign Intelligence Service (SVR), known for targeting diplomatic and policy-making networks.
The coincidence of targets—including defense ministries, arms suppliers, and military-industrial infrastructure—reflects Russia’s broader doctrine of integrated hybrid warfare: using cyber operations as force multipliers for traditional military and diplomatic objectives.
Killnet’s Reinvention: From Loud DDoS to Cyber Mercenary Activity
In contrast to the stealthy approach of Void Blizzard, Killnet has historically operated as a noisy, pro-Kremlin hacktivist collective focusing on defacement, DDoS, and propaganda.

Collapse and Acquisition
- In late 2023, Killnet’s founder, KillMilk, was publicly exposed in Russian media, revealing ties to drug trafficking and personal luxury, eroding the group’s ideological credibility.
- Control shifted to the Deanon Club, an anti-drug vigilante group, reportedly purchasing Killnet’s infrastructure for between $10,000 and $50,000.
- The group’s operational capabilities temporarily faltered as core members splintered or rebranded (e.g., KillNet 2.0, Just Evil).
Pivot to Profit
Under new leadership, Killnet has:
- Shifted from patriotic hacktivism to hack-for-hire services and ransomware-style extortion schemes.
- Targeted Ukrainian defense networks (though unverified) and claimed involvement in drone-tracking system compromises coinciding with Russian Victory Day propaganda efforts.
- Blended self-promotion on Russian media with deeper integration into cybercrime marketplaces, positioning themselves as “cyber mercenaries” rather than purely ideological actors.
Ongoing Fragmentation and Brand Reuse
Analysts like Rik Ferguson of Forescout argue that Killnet’s behavior mirrors broader trends in both state-linked and independent cyber groups:
“Rebranding, splintering, and reactivating older identities whenever needed—it’s a hallmark of the Russian underground, allowing them to maintain plausible deniability and adapt to new demands.”
A Dual-Track Threat: Stealth vs. Noise
The juxtaposition of Void Blizzard’s surgical data exfiltration and Killnet’s propaganda-laden operations illustrates Russia’s layered approach to cyber warfare:
- State-directed cyber espionage for battlefield intelligence and political leverage.
- Commercial and disruptive operations by hacktivist-mercenary hybrids like Killnet, sowing confusion and amplifying disinformation.
Defensive and Policy Implications
The combined impact of these campaigns underscores the need for:
- Continuous cloud security posture management (CSPM) to monitor for suspicious API usage and misconfigured permissions.
- Hardened MFA deployment; eliminating legacy protocols and phasing out password-only systems entirely.
- Threat intelligence sharing alliances; to identify and respond to these shared Russian threat vectors quickly.
- Strategic policy realignment: recognizing that Russian cyber-espionage efforts are not purely military; they target social, economic, and diplomatic sectors as part of a broader influence campaign.
Conclusion: A Reshaped Russian Hackers Landscape
The revelations around Void Blizzard and Killnet underscore that Russian cyber operations are not monolithic but rather a complex web of state-backed intelligence units, cloud-centric espionage campaigns, and mercenary-like operators exploiting commercial crime tools.
For Western governments and corporations, these findings highlight an urgent truth: the frontlines of modern geopolitical conflict increasingly run through cloud platforms, stolen cookies, and stolen credentials—and defending them requires not only technical hardening but also global collaboration, shared intelligence, and vigilance against the ever-evolving Russian cyber offensive
Share this :