Simonmed data breach: No CVE Found, Data Exposed

Hoplon InfoSec
14 Oct, 2025
Imagine going to a typical medical imaging appointment, like an MRI or CT scan, and then finding out months later that hackers may have acquired access to your personal and health information.
In early 2025, SimonMed had a big breach; this is what happened. The attack's size, approach, and consequences should be a warning to healthcare, patients, and cybersecurity.
In this essay, I'll tell you everything we know so far about the breach: how it happened, what data was affected, who was behind it, how SimonMed responded, what risks patients face now, and what healthcare organizations need to learn. Let's get started.
This leak wasn't little. More than 1.2 million patients had their personal information taken. The leak indicates that even large medical service companies can be attacked. Cybercriminals love to steal health care data, which includes medical histories, health records, insurance information, and personal information.
You can utilize that mix to commit fraud, blackmail, or more precise targeting. The delay between the breach and the public revelation was significantly longer, which makes me very worried about openness, obligation to patients, and regulatory monitoring. The SimonMed data breach isn't simply another news story; it's a lesson in what went wrong and how the healthcare industry can repair it.
What is SimonMed, and why did someone want to attack it?
SimonMed Imaging is one of the major companies in the U.S. that does medical imaging for people who don't need to stay in the hospital. It has dozens of sites in various states. They do MRIs, CT scans, X-rays, ultrasounds, and other tests that help doctors see what's wrong. Imaging facilities are a very valuable target since they store a lot of patient information, like photos, reports, and comments from doctors.
Now, hackers are going after healthcare and medical imaging companies instead of banks and other businesses' data. The data is incredibly sensitive and hard to update or reissue. For example, you can change your credit card but not your MRI scan. The SimonMed data leak shows that no business that has sensitive data is safe anymore.
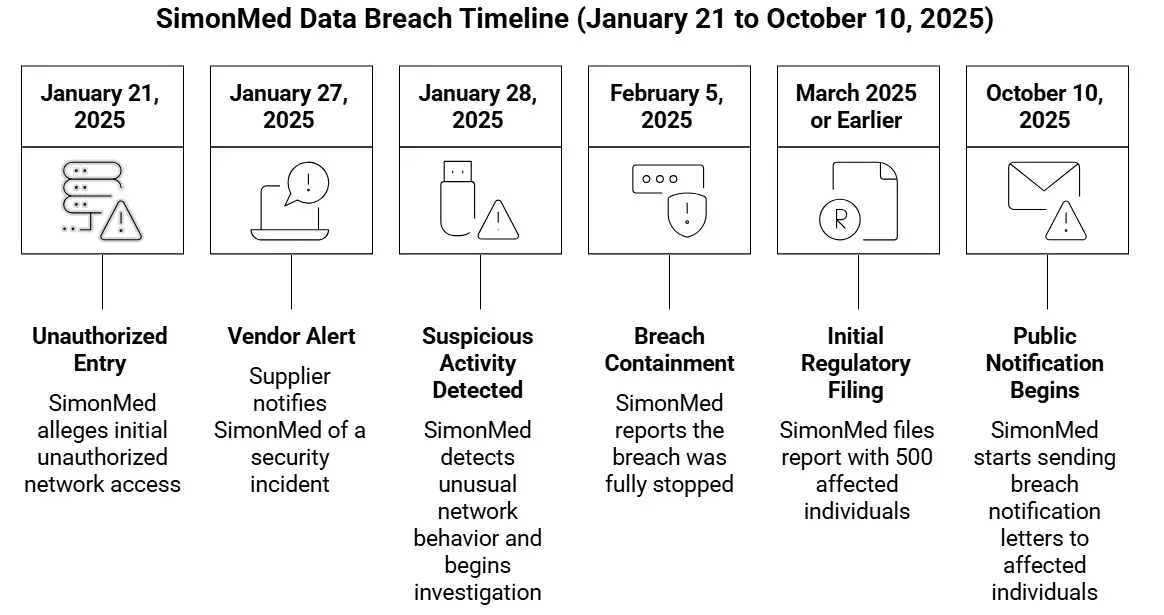
What Happened During the Breach Based on a number of stories, this is what I think happened and when. Entry and Exposure (January 21 to February 5, 2025)
• SimonMed alleges that people who weren't supposed to get in did so on January 21, 2025.
• The breach lasted for roughly two weeks, until February 5, 2025, when it was totally stopped.
• Reports say that the people who weren't supposed to be there got in through a vendor security incident or a third-party access chain. One of SimonMed's suppliers alerted them about a security incident on January 27, 2025.
• SimonMed noticed peculiar behavior on its network the day after the incident, on January 28, 2025, and started a forensic investigation.
• The study later found that the breach included stealing files over that time period, like health data and personal information. Notification and Disclosure to the Public
• The breach happened in January and February, but SimonMed didn't start delivering letters to the people who were affected until October 10, 2025.
• The official notification to regulators, like state attorneys general or breach portals, said that 1,275,669 people (approximately 1.28 million) were affected.
• SimonMed had said in a regulatory filing earlier in March or earlier that there were just 500 people on the list. This was customary till the complete investigation was over.
What it is and what it does: What Information Was Stolen?
The assailants were able to get their hands on some dangerous information. Based on what people have said and done in court:
• Personal identifiers include names, addresses, birth dates, driver's license numbers, and sometimes social security numbers.
• Health information: records of diagnosis and treatments, information about medical conditions, drugs, provider names, and health insurance.
• Medical record numbers and patient identifiers: these connect the clinical data to individual patients.
• Proof data or leaked samples: The Medusa gang claims they took 212 GB of data and released sample files such as ID scans, spreadsheets, and medical documents. SimonMed has indicated that, as of their previous updates, there is no confirmation that the data that was obtained has been utilized to commit fraud or steal someone's identity.
That doesn't mean there isn't a risk, though. Once data is out, it can stay there, be sold or exchanged silently to other people, or just sit there.
Who Was Behind the Medusa Ransomware Attack?
The Medusa ransomware organization is a name that keeps showing up in the press. Many accounts indicate that Medusa was responsible for the intrusion at SimonMed.
What We Know
• Medusa alleged she was at fault and sought $1 million in ransom.
• The organization put up sample files on its extortion site to illustrate that they could get to them.
• They are quite good at using three different types of extortion. They might not just encrypt data, but they might also threaten to make it public and put pressure on victims in various ways.
It's strange that SimonMed isn't on Medusa's active leak site right now. Some people believe that the ransom was paid or that the arrangement was made without anyone knowing. What Makes This Attack Different Usually, ransomware groups lock up computers and then demand money.
In this case, there is proof that the attackers wanted to steal data and extort money more than they wanted to take over the system. This corresponds with an increasing trend of breaches in healthcare, where data is the prime target.
Also, the timing and delay in revealing the information made things worse. The attackers may have had months to go over the material and send it out again before they had to be open because of public pressure. That extended timeframe is one of the worst things you can do while managing a breach
SimonMed's answer:
stages, critique, and holes After they found out about the breach, SimonMed did a lot of things. But some people have complimented them, and some people have questioned how they handled it. What was done
• Change all passwords and make sure that vendors can't access internal systems directly.
• Set up or upgraded multifactor authentication (MFA).
• Used endpoint detection and response (EDR) tools to watch for odd behavior.
• Only allowed traffic to and from sources on a whitelist.
• Brought in privacy, forensics, and legal specialists and told the police.
• Helped people who were affected by credit monitoring and identity theft protection, usually through a third party like Experian. Criticism and holes
• Delay in disclosure: It's not good that patients have to wait eight to nine months to find out. Many people think that being honest about problems early on could assist.
• Initial under-reporting: Putting in a placeholder number of 500 affected people when the real number was substantially greater damages trust.
• Not clear what caused the problem: SimonMed hasn't specified publicly whether software or vulnerability was to blame.
• No proof of misuse: They argue there is no proof of fraud, but not having proof is not the same as not having proof. There is a chance to misuse it.
• Liability exposure: There have already been a number of class action lawsuits filed against the corporation, claiming that it was careless in protecting data.
In short, SimonMed performed what they had to do, but their early blunders and bad communication made people less likely to trust them.
Risks and Effects on Patients
If your information was stolen in the SimonMed breach, here's what you might be facing and what you should watch out for. Theft of Identity and Fraud People who have names, birthdates, addresses, driver's license numbers, and maybe even Social Security numbers can try to commit fraud by getting credit, loans, or opening accounts in someone else's name.
Imagine someone exploiting your health information to get a credit card in your name. It's not a scientific story. Scams in health care and insurance Criminals could use your identity or other information to create bogus claims with your health insurance or bill you for things you didn't do.
They might also try to deceive you with false "insurance reviews" or schemes that involve medical care. Scams that try to gain your money and phishing Now that attackers know you went to SimonMed and have health problems or testing, they can run very convincing, targeted phishing or social engineering attacks.
For example, "We're looking into your MRI from January." Click here to see your results. What it does to the mind and emotions It's really disturbing to consider that your private health history could potentially be public.
The feeling of being vulnerable, exposed, and deceived by a trusted provider are all harms that can't be seen but lead to anxiety, second-guessing, and distrust in medical systems. Longer Time of Exposure Data can linger on black-market servers for months or years, even if no one is using it right now.
Over time, hackers may come up with new ways to use your data or mix it with previous data breaches.
What This Breach Can Teach Us: Lessons and Insights
The SimonMed breach offers lessons for patients, healthcare professionals, regulators, and IT experts that go beyond the case itself. Here are a few of mine: There is a significant danger in the supply chain. Reports claim that this breach began with something that happened with a vendor that wasn't part of the company.
The lesson is that the part of your security that is most vulnerable may not be behind your firewall. Healthcare providers should not think of vendor security as a side issue but as a main security issue. It can be fatal to wait too long to find something. Long dwell time, or the time attackers stay hidden, makes damage worse. Faster detection, zero trust, and persistent monitoring are all necessary defenses.
Trust grows when you are open. Not disclosing enough or reporting late makes credibility worse. A prompt and honest revelation could generate attention, but it also demonstrates that you care about the individuals who are affected and are responsible. It's important to keep data to a minimum. Healthcare practitioners typically hold data longer than they need to or gather more than they need to.
The impact might not be as terrible if the SimonMed data breach had fewer fields or retained the data for a shorter time. Patients Need to Do Something As a patient, you can question your provider about how they keep your records safe, demand improved data practices, use strong passwords for patient portals, and check your credit and medical statements straight away.
What Healthcare Providers Should Do Right Now
If I were giving advice to hospitals, imaging centers, or medical organizations after SimonMed, I would suggest the following items in this order:
1. Not just the key medical apps, but all systems should be fully forensically audited.
2. Use a zero-trust design so that no one inside the company can automatically get in.
3. Make contracts with vendors and other parties stronger so that they have to include strong security measures, regular audits, and shared liability.
4. AI and behavioral technologies that always watch for risks and swiftly locate them as they move.
5. There should be regular, transparent communication with patients, regulators, and the media during an occurrence.
6. Splitting up data so that not all of a patient's information is kept in one "crown jewels" database.
7. Do tabletop breach exercises to find out how ready you are and what the worst-case situation would be.
8. Spend money on training your workers to cut down on phishing, social engineering, and blunders caused by your own workers.
If a lot more physicians did these things, it might be harder for groups like Medusa to assault the healthcare industry.
What You Should Remember
The breach of SimonMed's data is a wake-up call. It indicates that even major, well-funded medical companies are still vulnerable to fraudsters. Health information, identities, and other data about more than 1.2 million patients were made public. You can't "reissue" this data. Patients are in danger. People are keeping an eye on service suppliers. People don't trust each other like they used to. But there is still a chance.
We can learn from what we do wrong. We can make it less likely that the next hack will happen by tightening security, making the rules clearer, and making patients more aware. If I were one of the people in that pool, I would sign up for identity monitoring, freeze my credit where I could, check my medical bills carefully, and ask my doctors how they keep my information safe.
I think the good news is that these breaches are getting people mad and putting pressure on the government to reform how healthcare security works from being reactive to being proactive. The SimonMed data breach is likely to be one of the most important things that has ever happened in cyber health.
After breaches like SimonMed’s, stolen data can quietly spread on hidden sites. Hoplon Infosec’s Deep and Dark Web Monitoring spots those leaks early, tracking underground sources and alerting clients fast helping limit damage and keep sensitive information safe.
Follow us on X (Twitter) and LinkedIn for more cybersecurity news and updates. Stay connected on YouTube, Facebook, and Instagram as well.
Share this :