SmarterMail Fixes Critical Unauthenticated RCE Vulnerability (CVSS 9.3)
-20260130173602.webp&w=3840&q=75)
Hoplon InfoSec
31 Jan, 2026
Is CVE-2026-24423 exploited in the wild right now?
As of January 30, 2026, there is no publicly verified confirmation that CVE-2026-24423 is actively exploited in the wild, although a related SmarterMail vulnerability (CVE-2026-23760) has documented in the wild.
How to check if you are affected
I’m going to keep this practical. No magic scanners. Just what most admins can do today.
1) Confirm your build number
Your first question is not “do we have a firewall?” It’s “what build are we on?”
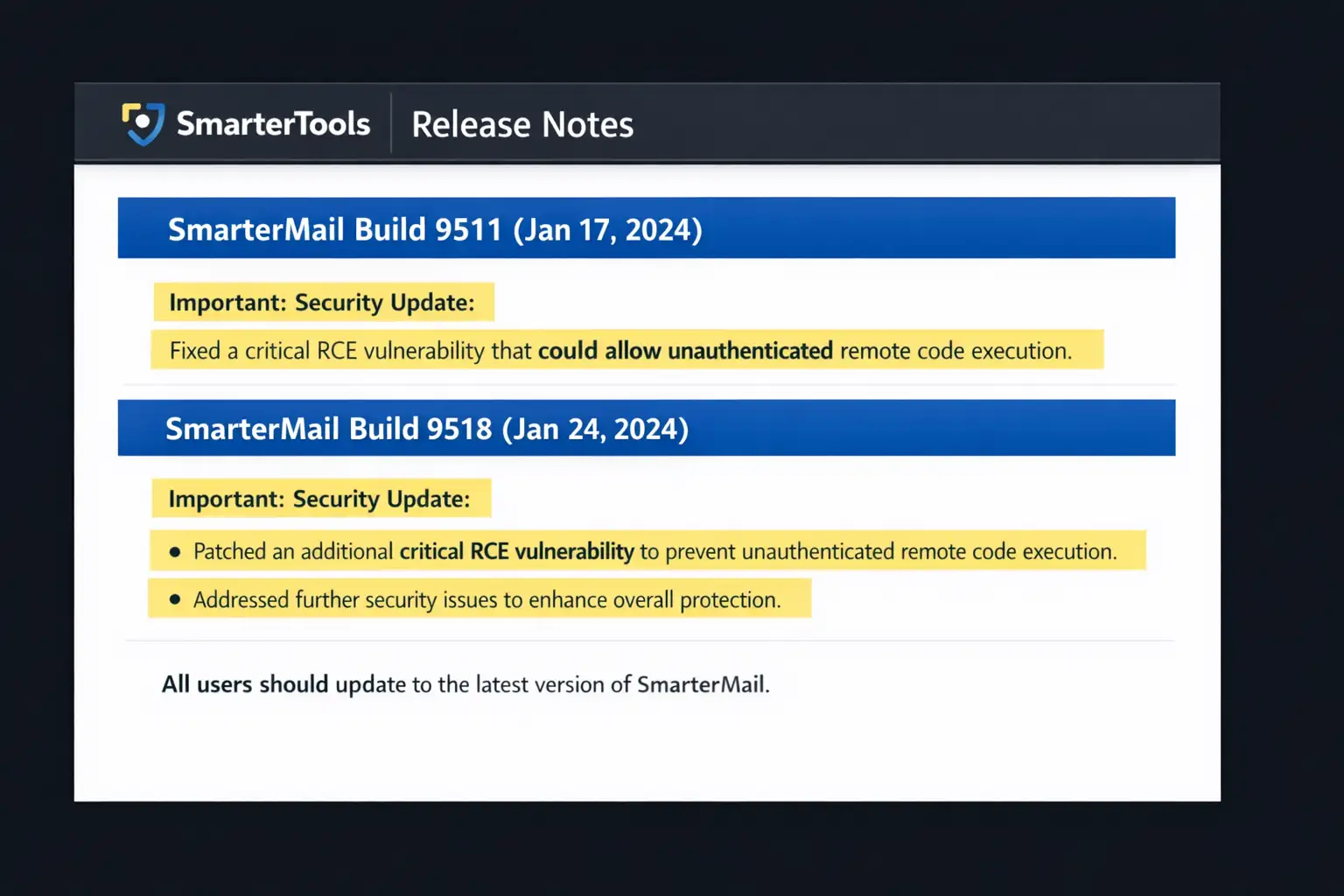
SmarterTools’ release notes show Build 9511 as containing critical security fixes, and later builds include additional fixes.
If you are below 9511, you are in the direct affected range for CVE-2026-24423 as described by NVD and VulnCheck.
2) Identify exposure
Ask a simple question: Is your SmarterMail admin interface reachable from the internet, directly or through a reverse proxy?
Email servers often need inbound connections, but admin interfaces do not always need to be globally reachable. If you can restrict management access to VPN or a safe IP range, do it.
3) Patch forward, not sideways
Upgrade at least to Build 9511, and seriously consider moving to Build 9518 to pick up the NTLM relay-related fix too.
-20260130173602.webp)
What to do after patching
Patching closes the door, but it doesn’t tell you whether someone walked in earlier.
Here are the “boring but effective” checks:
Review the admin account activity
If you can, look for unexpected admin logins, password resets, or newly created admin-level users. CVE-2026-23760 specifically centers on password reset behavior.Look for suspicious changes in configuration.
Attackers who gain control often change settings that keep access alive: scheduled actions, system events, new domains, or unusual automation patterns. Security reporting around SmarterMail exploitation has mentionedthe use of built-in functionality after compromise.Check the host, not just the app.
When a vulnerability enables code execution, the host becomes the real target. Review Windows event logs, process execution history (if you have it), and any endpoint detection alerts around the server.
If you don’t have endpoint visibility on the mail server, this incident is a good reason to add it.
A simple “risk heatmap”
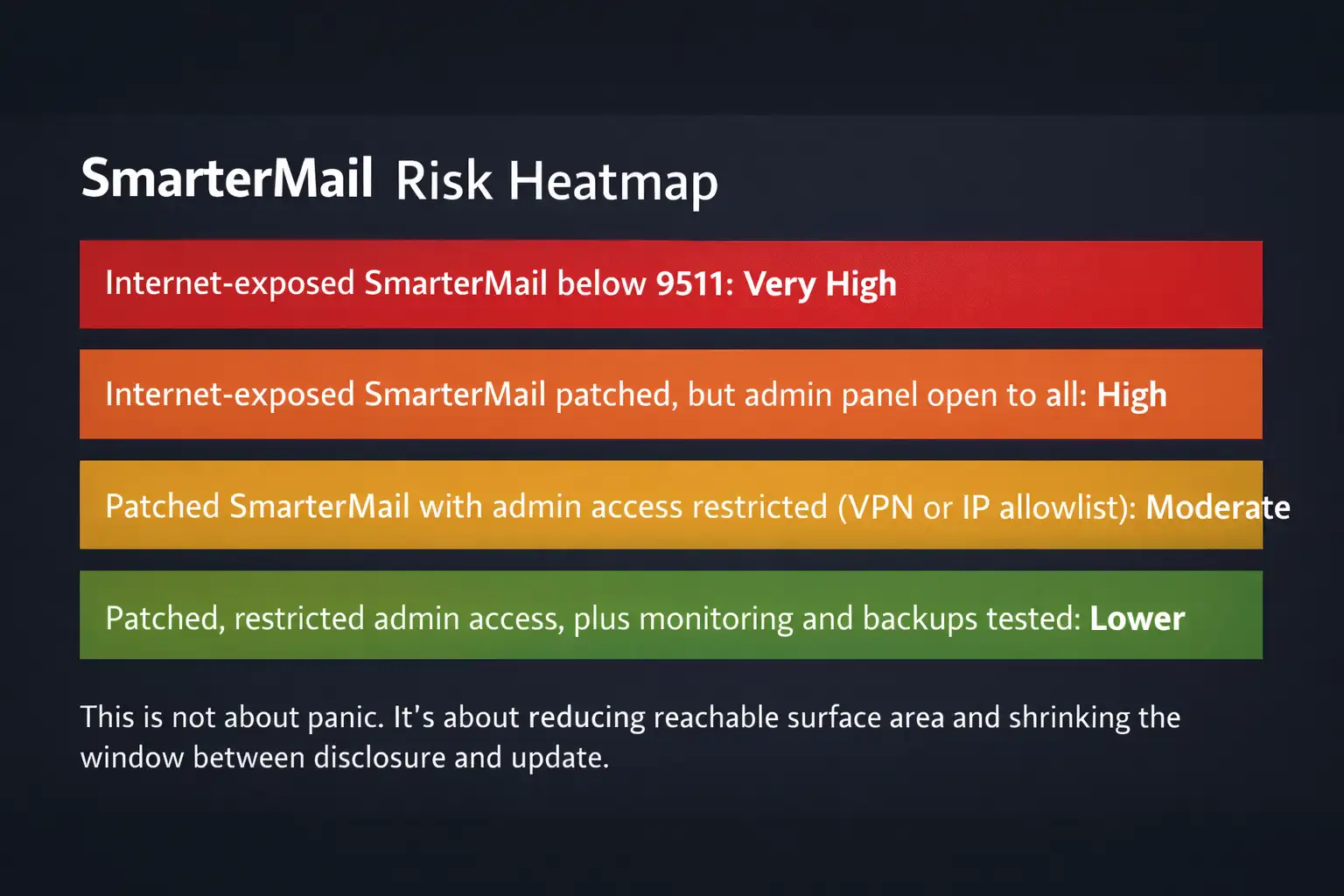
This is not about panic. It’s about reducing reachable surface area and shrinking the window between disclosure and update.
Why attackers like email servers
When attackers compromise a mail server, they don’t just “break email.” They can often:
Read sensitive communications
Reset passwords for other systems using email flows
Send believable phishing from a trusted domain
Use the host as a stepping stone into internal systems
That’s why a SmarterMail critical RCE vulnerability is not an isolated IT problem. It’s a business risk.
And yes, I’ve seen teams underestimate this because “it’s just email.” The,n payroll wire fraud happens. Then everyone suddenly cares.
FAQs
1) Is the SmarterMail critical RCE vulnerability the same as the auth bypass issue?
No. The RCE disclosure here refers to CVE-2026-24423 and the ConnectToHub API behavior. The auth bypass issue is CVE-2026-23760 in the password reset API, which can lead to admin takeover and then code execution through admin capabilities.
2) What versions are affected by CVE-2026-24423?
Public advisories describe SmarterMail versions before Build 9511 as affected.
3) How to patch SmarterMail CVE-2026-24423 safely?
The safest route is straightforward: upgrade to Build 9511 or later, then validate services, then confirm the build number post-upgrade. If you can, schedule a short maintenance window and take a backup first. The vendor release notes are the best official checkpoint for builds and fixes.
4) What should I do if I suspect compromise?
Patch first, then investigate. Review admin activity, configuration changes, and host-level logs. If you see suspicious behavior, isolate the server and follow your incident response process. Public reporting has already highlighted active exploitation around a related SmarterMail flaw, which raises the urgency of validation.
Hoplon Insight Box
If you only do three things today:
Upgrade SmarterMail to Build 9518 if possible (it covers Build 9511 fixes plus the later NTLM relay fix).
Restrict admin access to a VPN or IP allowlist. If the admin UI is not meant for the whole internet, don’t leave it there.
Verify, don’t assume. Confirm build number, review admin actions, and check the host for unusual command execution paths.
If you have time for two more improvements this week:
Add monitoring that alerts on new admin users, password reset spikes, and unusual outbound connections from the mail server.
Revisit patch cadence. When a product gets multiple critical CVEs close together, your update process needs to be measured in days, not months.
A calm takeaway you can actually use.
Here’s the thing about the SmarterMail critical RCE vulnerability story: it’s not just one bug. It’s a reminder that internet-facing business software gets probed constantly, and the gap between “patch released” and “attacks begin” can be painfully short.
If you run SmarterMail, the best time to updateiss January 15, 2026. The second-best time is today. Upgrade, restrict access, and then do the quiet verification work that prevents surprises later.
Trusted sources: SmarterTools SmarterMail release notes. “
This appears to be unverified or misleading information, and no official sources confirm its authenticity.”A SecurityWeek report quoted watchTowr’s CEO describing “active, widespread exploitation” of the auth-bypass issue soon after patching. That quote relates to CVE-2026-23760, not necessarily CVE-2026-24423, but it explains why defenders should move fast.
Share this :