Windows SMB Vulnerability: CISA Warns of Active Exploits

Hoplon InfoSec
21 Oct, 2025
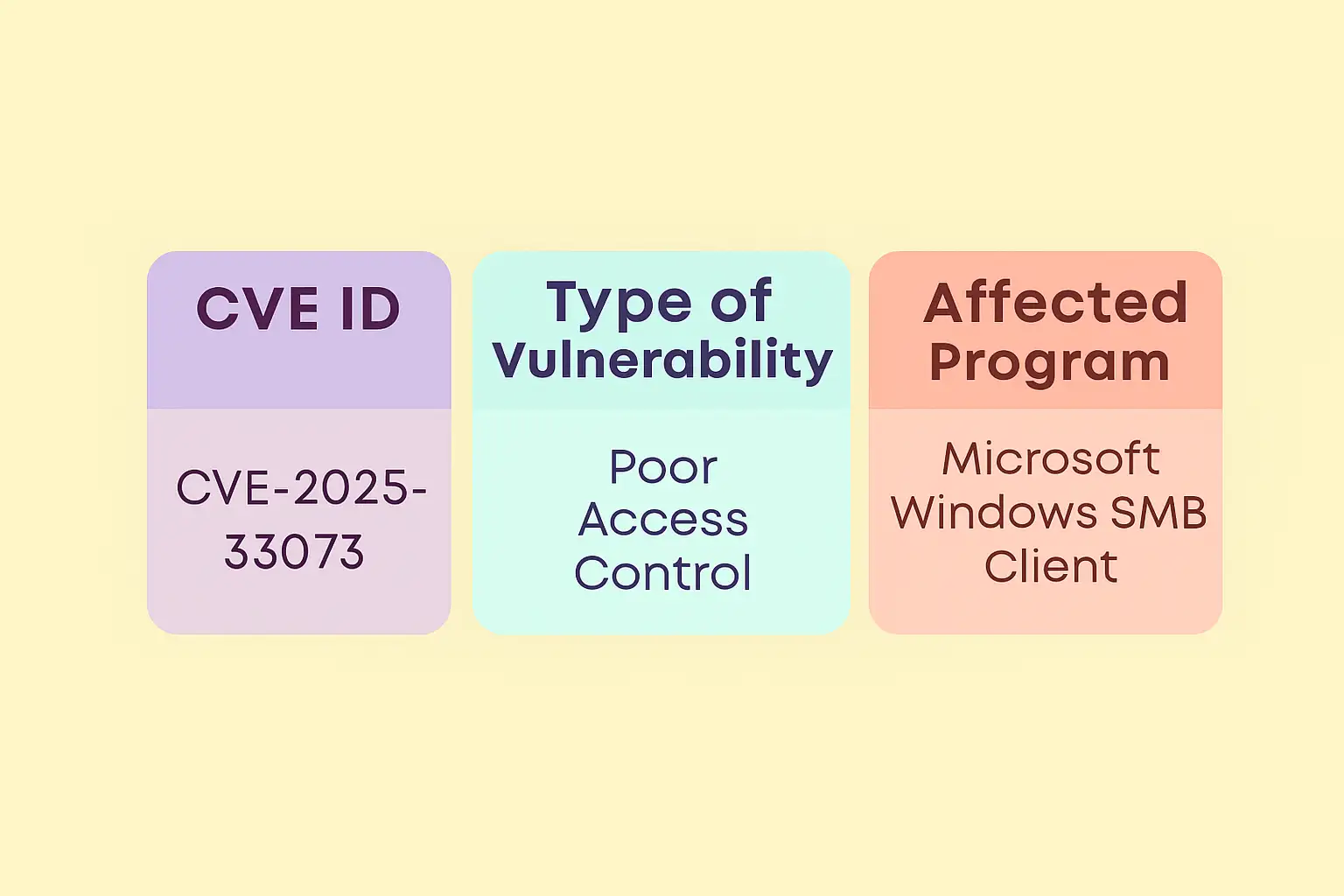
CISA has warned about a serious Windows SMB security hole (CVE-2025-33073) that hackers are already using. Attackers can get higher privileges by tricking systems into connecting to fake SMB servers because of a flaw in the Microsoft Windows SMB Client. Once used, it can let you move sideways, steal data, or install malware. CISA says that all businesses should patch right away, keep an eye on SMB traffic, and follow Microsoft's security advice to stay safe.
What happened in one line?
A major problem with Microsoft's Server Message Block implementation was found and given its own CVE number. Attackers can get higher privileges on affected hosts because of the vulnerability. This means that once they get in, they could take full control of the system. The national agency's warning shows that exploitation is happening, which makes the risk go from theoretical to real.
Why SMB matters and why you should care
SMB is not a weird piece of software. It is the network's plumbing for sharing files, printing, and many other Windows services. Because SMB is so common, a flaw in it can let you move from one computer to another, hide bad behavior in normal traffic, or get into systems that are very important.
If your computers can talk to each other over SMB and one of them isn't patched, an attacker can use that conversation to get into privileged accounts and cause a lot of trouble.
In the last few years, problems with SMB have not just been ideas. As has happened before, attackers use a protocol flaw a lot when they find one that works. That history makes a new warning about SMB very important for businesses that still use old systems or that let bigger networks use their file services.
A simple explanation of the technical core
In the SMB client part, this is mostly an issue with access control. An attacker who is already on a network or can trick a host into connecting to a bad SMB endpoint can get the system to do things that give them more power.
When you get SYSTEM or admin rights, you go from being a normal user to being an administrator. After that, the hacker can create backdoors that last a long time, steal passwords, or encrypt files.
This hole doesn't let you run code from far away without doing anything. It is still dangerous because it can turn small footholds into full system breaches.
Who is affected, and how far does the effect go?
Public vulnerability records and vendor advisories say that a lot of Windows versions can be affected, even some desktop and server releases that are still supported. That means that the danger is present in every field and everywhere. Small businesses, schools, and factories that still use old systems are especially at risk because they don't always patch their systems in time.
In real life, the systems that matter most are the ones that can handle network traffic that starts SMB connections.
The national agency added this issue to a list of known vulnerabilities that are being used. This means that businesses with systems that are connected to the internet or not separated should take action right away. This catalog helps a lot of businesses figure out what needs to be fixed first and when.
How attackers are using the flaw in the real world
Several security news sites have said that threat actors are already using this flaw in targeted attacks. I know the pattern. Phishing, a weak internet service, or an open management interface can all let an attacker in. After that, they use the SMB flaw to get more access and move sideways. In some cases, that second stage lets ransomware be used or private information be stolen.
Attackers like this staged approach because it gives them more power, which makes a small compromise more valuable. When defenders are in a hurry, they might not see small side-to-side movements that happen before a clear act of destruction. That's why it's so important to find it early.
Every business needs to take useful steps right away.
If you are in charge of systems, start here.
First, look for all the Windows hosts in your environment and check to see if they are on the list of patch vendors.
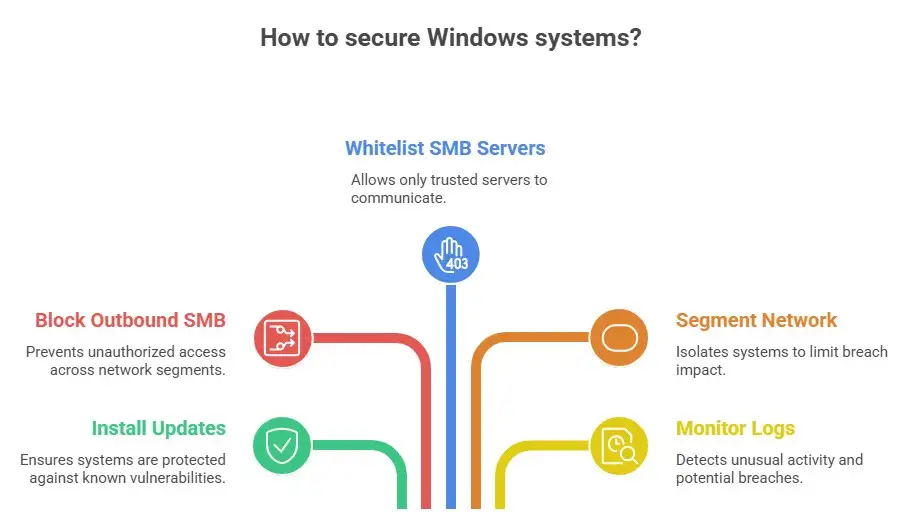
Second, make sure you install updates from the vendor first.
Third, don't let SMB cross network segments where it doesn't need to.
Fourth, keep an eye on SMB activity that seems strange and look for signs that someone is trying to gain more access.
Finally, check that your backups are current and have been tested in case you need to recover from a breach.
The best thing to do is to install updates as soon as you can. If you can't install updates right away, you can lower the risk by doing things like blocking outbound SMB to unknown hosts, whitelisting trusted SMB servers, and segmenting your network. You should also check the logs for remote desktop and file sharing to see if there are any strange login attempts or connections that don't follow the usual patterns.
How to tell if you were hit
It can be hard to find exploitation, but there are some things you can look for. Look for SYSTEM-level processes that are being used in strange ways, new services that are installed without an administrator's permission, scheduled tasks that seem strange, authentication events that are out of the ordinary, and network traffic to SMB endpoints that you don't know about. A lot of endpoint detection tools and EDR solutions can find attempts to move laterally and set rules for how to give people more access.
You should check out connections to SMB servers that aren't part of your network right away if your logs show them. Companies that are good at logging and threat hunting should also look for unusual process chains and changes to credential stores.
A short list of things that sysadmins need to do right now
1. Write down the Windows hosts and their patch status.
2. Install official patches from the vendor right away.
3. Block SMB ports at the edges and in between trust zones.
4. Check to see that the Group Policy settings that control how SMB works are safe.
5. Review and make better the controls that keep local admins and privileges separate.
6. Watch out for SMB clients who are acting strangely and getting more access rights.
These steps are simple to follow and work. Network controls and monitoring lower the risk of lateral movement and give defenders time to react, even if you can't patch right away.
Why this is important for small businesses
People pay a lot of attention to big businesses, but it's easier to attack small ones. A small server that hasn't been updated or a worker's computer that uses SMB to access shared folders could be the weak link that lets attackers get to important business systems.
Because small teams don't always have extra IT staff or set patch windows, it's best to patch hosts that share files and connect to the internet first and then add compensating network controls.
If your team doesn't have a lot of resources, focus on the most important assets and those that work with systems that hold customer, financial, or identity data. You don't have to be perfect.
You need to move faster than the people who are attacking you.
Imagine your office has a lot of rooms but only one lock. SMB is like the doors in a hallway that let people pass file folders. The lock on the hallway door is broken, so someone who has already gotten into reception can walk through all the doors and get to the safe.
That is an example of privilege escalation. You can lock the doors, change the locks, or make sure the intruder never gets to the front desk. When it comes to cybersecurity, those options are like patching, stopping initial access, and isolating SMB traffic.
This example shows teams why it's important to both keep people out and control what they can do once they're inside.
Changes to the building and actions that will last longer
Along with quick fixes, you should also think about changing the architecture so that it doesn't rely as much on legacy SMB. Use modern identity and access management to limit the number of local admins who can access sensitive file services.
Also, split networks so that a compromised workstation can't reach servers. Regularly testing backups and incident response playbooks can help you respond to an incident more quickly.
Also, plan for updates to happen during the whole life cycle. Older operating systems that don't get updates anymore are great targets. Make sure to include patch management in your buying plans and plan for regular refresh cycles.
How businesses communicate and make choices
When leaders find a big security hole, they want two things. First, clear steps on how to do things. Second, a short update on the status that shows what has been done and what is planned. Make a message template for stakeholders that shows who is in charge, what systems are affected, and what is being done to fix the problem. That openness makes people less afraid and speeds up their recovery.
Communications at the board level don't need to be too technical. In business terms, risk is things like possible downtime, data exposure, or regulatory impact. List the exact steps being taken to deal with these risks.
Add tools for finding things and signals for defense.
If you have a product for endpoint detection and response, set it up to flag process chains that change the SYSTEM level, install new services, or change authentication stores.
You should watch for SMB traffic to external IPs, odd SMB negotiation sequences, and a lot of internal SMB file access that is higher than normal on the network. Simple heuristic rules can quickly point out activity that seems suspicious.
If you don't have special tools, you can make things easier to see by using detailed Windows event logging, keeping all your logs in one place, and checking for unusual behavior by hand every once in a while.
What we learned and how people play a role
These alerts always show how people are working to keep their computers safe. A patched server can still be affected by a reused password or a firewall that isn't set up right. Attackers use a mix of bad settings, social engineering, and technical problems.
That's why it's just as important for workers to be aware, have the least amount of access, and keep their hands clean as it is to install patches.
Take this time to remind yourself to put money into the basics. A quick training on phishing, stronger password policies, and stricter administrative rights can help when small mistakes turn into big ones.
Lastly, what you should remember and do tomorrow
This SMB Windows security hole is real and not just a thought experiment. Right now, there is a problem that needs to be fixed. First, check your inventory. If you can't patch right away, use network mitigations. Then, look through logs for signs of exploitation. This week, managers need to get a quick update on risks and check that backups work.
Following a list will help you feel less unsure and give your business a better chance of success. The technical record will be changed to fix the problem. You need to figure out where you are weak and make sure that small mistakes don't cost you a lot of money.
Hoplon Infosec’s Endpoint Security protects your systems from SMB exploits, detecting and stopping attacks before they impact your organization.
Share this :