How optional plugins can help hackers steal data and launch DoS attacks with SmokeLoader malware

Hoplon InfoSec
16 Sep, 2025
SmokeLoader Malware Plugins Explained
A lot of people think of cybercrime as a single virus that destroys computers. The truth is more complicated and much more dangerous. We don’t always see a big attack; sometimes we see quiet entry points that go unnoticed. SmokeLoader malware is a great example of this because it has been around for years and is small, flexible, and easy to hide.
Imagine a thief who doesn’t just break in once; they leave a key under the mat so they can come back anytime with different tools. This loader works just like that. It doesn’t always carry the same load. It steals passwords, sends denial-of-service floods, and sometimes it just gets things ready for bigger threats.
This article explains what makes SmokeLoader so hard to get rid of, how its plugins change roles, and how defenders can avoid being caught off guard. At the end, you’ll understand why security experts still think this old loader is a serious threat.
What is the malware called SmokeLoader?
At first glance, SmokeLoader malware doesn’t seem very impressive. It doesn’t get a lot of news coverage like ransomware does, and it’s small and easy to use. But this is what makes it dangerous: it sneaks in, stays in memory, and waits for orders. The loader doesn’t directly cause chaos; instead, it brings the tools that will.
Cybersecurity experts call it a “Swiss Army knife” for hackers. The base loader has the parts that let it talk to command-and-control servers. Once it’s connected, it can download plugins like keyloggers and denial-of-service modules. In a lot of cases, victims don’t know they were infected until they see stolen credentials for sale on secret forums.
Because it can change, it has a big effect. This loader can be used by anyone who buys or rents it on the dark web, unlike a targeted malware family that only steals banking data. Because of that open-ended use, security companies always tell businesses to take any detection seriously.
A short history and how things have changed
For more than ten years, SmokeLoader has been around. At first, it only had a few basic features: it could get a payload, run it, and stay persistent. Its makers improved it over time. They added layers of encryption, made it easier to manage plugins, and made it better at getting past antivirus software.
It’s like an old car that keeps getting new parts to make it better. It may look like something you’ve seen before, but it’s been set up for modern roads. The loader that security analysts are looking at today is not the same one that was seen years ago. Every time it changes, it adds new tricks that make defenders work harder.
This change is important because it shows that criminals can get away with it. The developers built trust in underground markets by keeping the brand alive and slowly updating it. Buyers know it works, and sellers keep making money. The loader is still doing well in 2025 because of that cycle.
How infections start: delivery methods
Most SmokeLoader attacks start with something simple, like an email that tries to trick you into giving them your personal information. Attackers send fake invoices, job offers, or delivery notices that trick someone into opening an attachment. The bad file that starts it all is in that document or archive.
Attackers sometimes take advantage of software that hasn’t been updated. For example, old Microsoft Office vulnerabilities are still popular because many businesses don’t update their software. If you click on a file that looks harmless, it could run hidden code that downloads the loader in the background without your knowledge.
After you install it, the loader gets in touch with its control server. After that, it asks for plugins or payloads. Basic cyber hygiene, like patching, training people to be aware, and scanning emails, is still very important because the first step depends on human error or old systems. But history shows that even big companies can be fooled by these simple tricks.
The modular architecture: an explanation of optional plugins
The modular design of this loader is what makes it so great. Not all of the features are included in the base program. Instead, it works like a framework that can be added to. Attackers decide which optional plugins to send based on the goals of their campaign.
For instance, if the goal is to steal money, a plugin that steals browser credentials might be used. If the goal is to cause chaos, a denial-of-service plugin could be sent instead. The loader is like a chameleon because it can change modules. It changes to fit the operator’s needs.
This makes it hard for defenders to find them. You can’t just look for one payload. In one case, the same loader could act like a banking trojan, and in another, it could act like a botnet node. Because of this unpredictability, security teams have to watch behavior instead of just relying on signatures.
Plugins and targets for stealing data
Stealing data is one of the most common things that people use SmokeLoader for. Plugins made for this job can steal login information, scrape browser cookies, or look for private files. Even small businesses are tempting because hackers can quickly sell usernames and passwords.
Think about a clinic in your area that isn’t very safe. A loader infection there could steal staff logins, which could then be used to get into patient records. The criminals might not even care about the clinic. They just put the stolen data in a box and sell it to other groups.
Because of this crime supply chain, the loader doesn’t often work alone. It is the opening act that makes a steady stream of stolen data that feeds bigger fraud markets. That’s why even small infections need a lot of care.
DoS and plugins for disruption
Many plugins don’t make any noise, but some do and can be harmful. DoS modules are made to send a lot of traffic to networks, making infected computers part of a botnet without their knowledge. These attacks can take down websites, overload business systems, and hurt reputations.
It’s interesting that the same loader that stole credentials yesterday could launch a denial-of-service attack tomorrow. This unpredictability makes it even more dangerous. Security teams can’t just assume that the infection will only cause silent theft.
This is especially bad for small businesses. A sudden flood of traffic on the network could stop business, which would drive customers away. Sometimes, companies don’t even know that the attack came from their own broken systems.
Events in the real world
SmokeLoader has been used in campaigns all over the world in the last few years. Analysts found that one wave of infections came from phishing campaigns in Taiwan that sent out plugins that stole credentials. Another case linked the loader to ransomware groups, which shows how it can be used as a stepping stone for bigger attacks.
These examples show how it helps things happen. The loader is not often the main story. The quiet trigger, on the other hand, opens the door for something worse. This same loader has been linked to ransomware, banking trojans, and botnets.
The lesson for defenders is clear. If you catch the loader early, you might be able to stop a breach that makes the news. If you don’t pay attention, the problems can get worse quickly.
Signs of a breach
Defenders often look for signs that a computer has been infected with SmokeLoader. These include strange outbound connections to domains that aren’t known, encoded network traffic, or sudden spikes in attempts to inject processes. The loader doesn’t always leave obvious files behind because it often hides in memory.
Another helpful sign is strange behavior between parent and child processes. For example, a Microsoft Word document that starts a hidden command line process is suspicious. Analysts also flag situations where processes that seem harmless start making encrypted web requests.
The problem is that none of these signs are unique by themselves. The story is in the combination. That’s why security monitoring uses layers of signals instead of just one alarm.
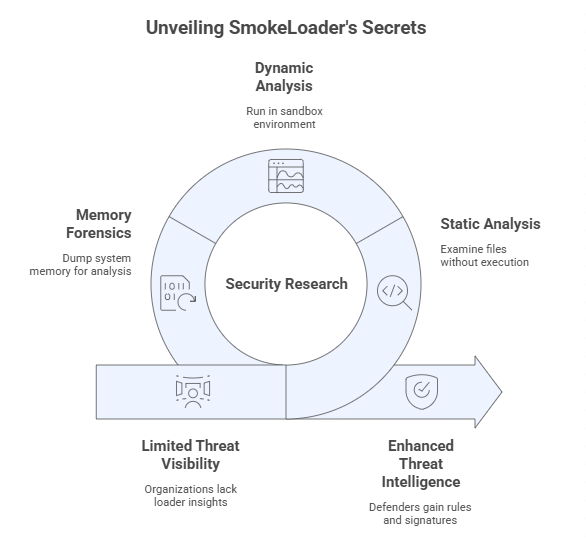
Methods used by researchers
Security researchers spend a lot of time looking at loader samples. Static analysis, which looks at the file without running it, is usually the first step in the process. Then they do dynamic analysis by running it in a sandbox and watching how it works.
Forensics of memory is also important. Analysts need to dump system memory to see what was running because SmokeLoader often tries to avoid dropping files on disk. They use these traces to figure out how commands work and how plugins act.
The results are then put into threat intelligence reports, which give defenders rules and signatures they can use. Without this community effort, organizations would be in the dark about the loader.
Finding threats and hunting them down
Finding SmokeLoader malware is not usually as easy as finding one file. Instead, defenders look for strange things, like executables running from user folders, rundll32 making web connections, or spikes in DNS queries.
Threat hunters often make their own queries in SIEM tools to keep an eye on process trees that look suspicious. For example, they might look for office files that open scripting engines without warning. Those queries catch loader patterns early, before plugins are fully installed.
It is very important to keep detection packs up to date. Because plugins and infrastructure change, the rules from yesterday might not apply to today’s campaign. Defenders stay one step ahead by constantly tuning.
Prevention and making things stronger
It always sounds boring to prevent things, but it works. Patching, limiting macro execution, and requiring multifactor authentication can all greatly lower risk. Another way to protect yourself is to use email filtering to block attachments that look suspicious.
Application allow-listing works well for businesses. By limiting which executables can run, you stop a lot of loader infections before they even start. Segmentation also helps by stopping infections from spreading too far.
People who use computers at home aren’t safe either. Regularly updating your software, using strong passwords, and being careful with email attachments all help. Cybercriminals love when people don’t pay attention, and even small actions can stop them.
Responding to incidents
When an organization thinks SmokeLoader is there, speed is key. To stop more plugin downloads or data theft, the first step is to isolate the machine. Next, take memory and logs to look at them. This proof helps figure out which plugins were running.
Rotate credentials, especially privileged ones, after containment. Since stolen logins are often the first thing hackers go after, it’s safer to assume that they are. Look for related indicators all over the network, since loaders don’t usually stop at just one machine.
Finally, look back at how the breach started. Was it a phishing attack? Was there a flaw that hadn’t been fixed? Closing that gap makes sure that the same road isn’t used twice.
Why it keeps going
One reason SmokeLoader won’t die is because of money. Criminals can rent it, buy add-ons, and start campaigns without having to build everything from scratch. That ease of use drives demand. The loader will keep going around as long as it makes money.
Adaptability is another thing to think about. Every time security companies make detection better, the people who made the loader change something, like the encryption or the format of the plugin. This back-and-forth keeps it important.
For defenders, that persistence is tiring. But understanding the economics of the loader helps change how you see things. Cutting off demand, sharing information, and making defenses stronger all work together to limit its reach.
Final thoughts and lessons learned
Even though SmokeLoader malware doesn’t sound very interesting, it’s one of the most reliable tools for cybercriminals. It gives you plugins that steal information, start denial-of-service floods, and make it easier for ransomware to get in. Every infection gives attackers a chance to get worse, which is why it’s so important to find them quickly.
The most important things to remember are to patch regularly, train staff, look for signs of bad behavior, and act quickly. If companies take even a small loader alert seriously, they can stop much bigger problems from happening in the future.
In cybersecurity, the threats that aren’t loud are often the most important. That is what SmokeLoader shows.
Hoplon Infosec’s Endpoint Security protects against threats like SmokeLoader malware, stopping malicious plugins, data theft, and DoS attacks before they reach your systems.
Follow us on X (Twitter) and LinkedIn for more cybersecurity news and updates. Stay connected on YouTube, Facebook, and Instagram as well.
Share this :