SolarWinds Attack on Exposed Servers: WHD Flaws Explained

Hoplon InfoSec
10 Feb, 2026
In February 2026: SolarWinds Web Help Desk Attack Overview
In February 2026, security researchers confirmed that attackers exploited flaws in SolarWinds Web Help Desk systems that were exposed to the internet. The attackers did not deploy obvious malware. Instead, they installed DFIR tools that are normally used by defenders, allowing them to quietly observe systems and remain undetected for longer periods. This SolarWinds attack on exposed servers shows how real tools can be used for bad things if you don't pay attention to security basics.
What is the SolarWinds attack on servers that are open to the public?
The SolarWinds attack on exposed servers was a series of attacks in which hackers went after SolarWinds Web Help Desk installations that were directly accessible from the internet. These systems are not meant to be used by the public; they are meant to help with internal IT work. They were easy to get into when they were left open.
Not only was the vulnerability different, but so was how attackers acted after getting in. They didn't steal data or use ransomware right away. Instead, they set up digital forensics and incident response tools. Security teams often trust these tools, which made it easy for attackers to blend in with normal administrative work.
This method shows that the attacker is thinking differently. The goal was to be persistent and visible, not fast. This makes the SolarWinds attack on exposed servers less obvious and harder to find than other types of attacks.
Why Hackers Went After SolarWinds Web Help Desk Systems
Many businesses and medium-sized companies use SolarWinds Web Help Desk. It often runs with higher permissions and can see assets, users, and internal systems. That makes it a good place for an attacker to start.
Exposure is another reason. In a number of confirmed cases, the servers that were affected could be reached from the open internet. There was no need for an advanced exploit chain. Attackers just looked for systems that were reachable and tried to exploit them.
There is also a trust issue. Tools like SolarWinds are an important part of IT work. Activity that comes from these platforms might not set off alarms right away. The attacker was able to stay longer because of this lack of trust.
How the Attack Really Worked
The attack began by exploiting flaws in SolarWinds Web Help Desk. There have been a few cases where attackers got into exposed instances without permission, but public reports don't confirm that this is happening on a large scale.
Once they got in, attackers used DFIR tools instead of custom malware. The purpose of DFIR tools is to collect logs, monitor processes, and analyze how the system works. When they fall into the wrong hands, they become very useful for spying.
Attackers could see how administrators acted, learn about the network's layout, and avoid things that might set off alarms with this method.
The tools themselves are real, which made it harder to figure out who did what and find them.
_compressed-20260210102226.webp)
An example from a real-life situation
Picture a medium-sized business using SolarWinds Web Help Desk on a server that vendors and employees who work from home can access. Over time, firewall rules get less strict to make things easier. The system stays unpatched for longer than planned.
An attacker finds the exposed service during routine scanning. They gain access and quietly install DFIR tooling. For weeks, nothing appears wrong. Tickets are processed. Systems run normally. Meanwhile, the attacker watches internal traffic and learns where sensitive systems live.
This is how the SolarWinds attack on exposed servers unfolded in real life. No loud alarms. No immediate damage. Just quiet observation.
Features That Made the Platform Attractive to Attackers
SolarWinds Web Help Desk offers centralized visibility into IT operations. That feature is valuable for administrators, but equally valuable for intruders.
The platform supports detailed logging and system interaction. Once compromised, those same features can tell you a lot about how users behave and how the infrastructure is built.
Access through a web browser was also a factor. It was easy to use, but it made things more dangerous when administrators didn't properly limit access. Features meant to make things easier became tools for spying.
Benefits of SolarWinds Web Help Desk When It Is Safe
Even though something went wrong, SolarWinds Web Help Desk is still useful when set up correctly. It helps teams manage alerts, assets, and incidents all in one place.
It also speeds up response times by bringing all IT tasks together. When access is limited to internal networks and patches are applied quickly, the risk level goes down a lot.
This matters because the SolarWinds attack on exposed servers was not caused by the concept of the tool, but by insecure deployment choices.
Pros Observed During Incident Response
One positive outcome was improved visibility into attacker techniques. The misuse of DFIR tools revealed how attackers are evolving toward stealth rather than speed.
Another benefit was awareness. Companies started looking at which of their internal tools were available to the public. Many people found out that services they had forgotten about were available on the internet.
The event also showed how important it is to keep an eye on behavior instead of just relying on malware signatures.
Cons and security flaws were found
The biggest problem was that management servers were open to attack.
Once compromised, these systems provide deep access.
Another issue was detection delay. Because attackers used trusted tools, traditional alerts were less effective.
Patch management gaps also played a role. Some affected systems were not running the latest versions, increasing risk unnecessarily.

What Organizations Should Do Next
First, look over all systems that are connected to the internet. Management tools should not be open to the public unless they really need to be.
Second, quickly install updates and follow the vendor's hardening guides. Basic security measures should never be put off for the sake of convenience.
Third, monitor how tools are used, not just what tools are present. Unusual behavior from trusted software deserves attention.
Impact of the SolarWinds Attack on Exposed Servers Across Industries
The SolarWinds attack on exposed servers did not target one specific sector. What made it concerning was how broadly applicable the technique was. Any organization running SolarWinds Web Help Desk with public exposure became a potential target, regardless of industry size or geography.
The effect was immediate for IT service providers. These environments often use centralized tools to manage multiple customer systems. If a help desk platform is hacked, it can quietly turn into a map of client networks, support workflows, and internal dependencies.Even without data theft, that visibility alone creates long-term risk.
Healthcare and education environments faced a different challenge. Many rely on lean IT teams and legacy configurations. When DFIR tools were deployed by attackers, detection became difficult because system monitoring already involved similar utilities. Distinguishing legitimate administrative activity from malicious observation required time and careful review.
Why Using DFIR Tools Changed the Nature of the Attack
Traditionally, attacks leave traces that security teams are trained to find. Malware files, command and control traffic, or unusual outbound connections usually stand out. In this case, attackers chose a quieter path.
DFIR tools are designed to help defenders understand systems during investigations. When attackers used them, activity blended into normal workflows. Logs showed tools that were already trusted. Processes looked familiar. This delayed response and increased uncertainty.
This approach reflects a broader trend in modern intrusions. Attackers are finding out that being patient is often better than being quick.
The SolarWinds attack on exposed servers demonstrated how living off trusted tools can be more effective than deploying obvious malicious code.
Visual Data Overview
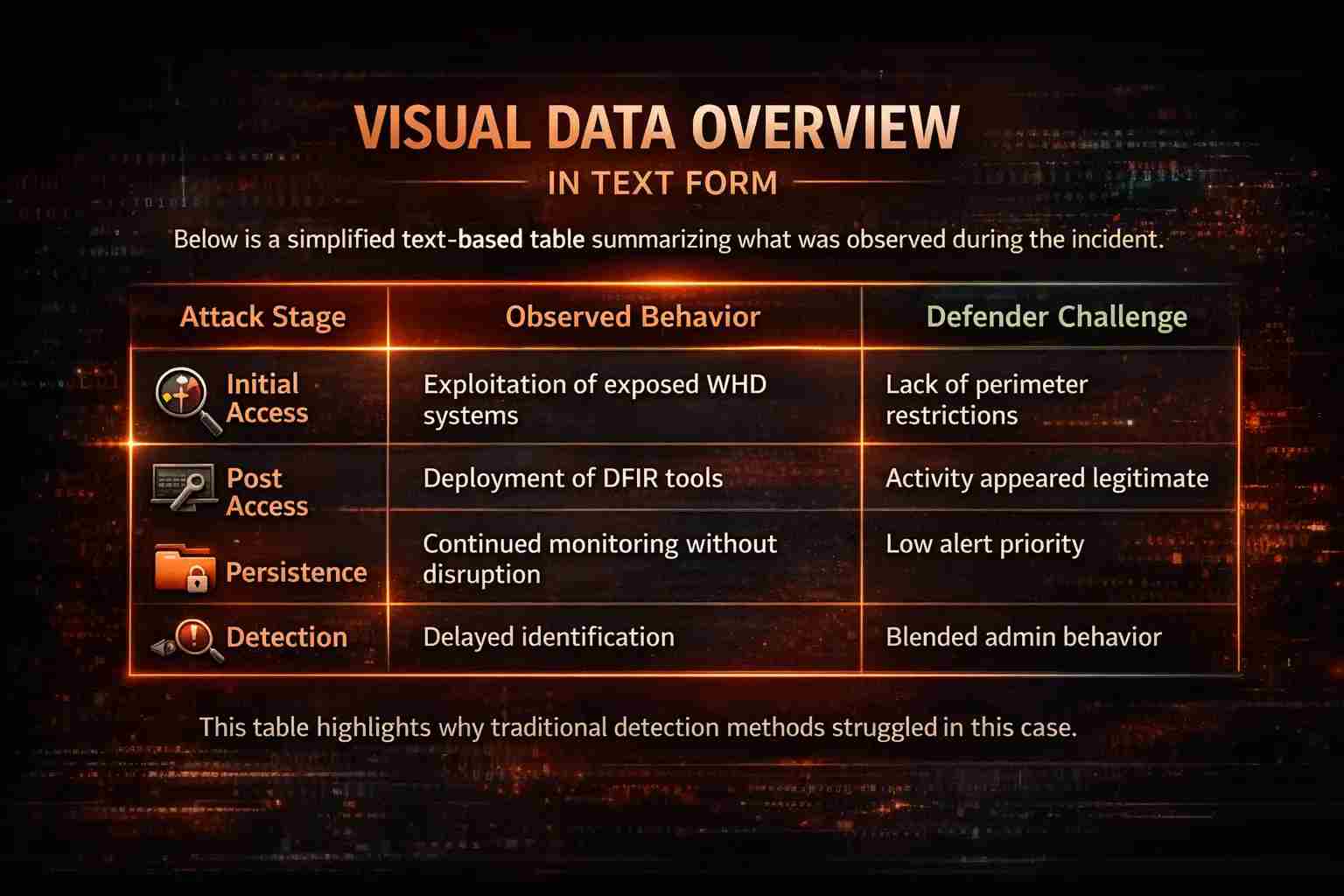
This table highlights why traditional detection methods struggled in this case.
What This Incident Reveals About Modern Attack Patterns
The SolarWinds attack on exposed servers reinforces a key lesson. Security failures often come from configuration choices, not just software flaws.
Public exposure of internal tools remains one of the most common and preventable issues. Over time, exceptions get added. Temporary access becomes permanent. Documentation fades. Attackers rely on this drift.
Another insight is that attackers increasingly value intelligence over disruption. Watching quietly gives you more power than doing damage right away.This changes how defenders must think about risk.
How Organizations Can Reduce Similar Risks
The most effective step is reducing attack surface. Internal management tools should never be internet-facing unless there is a strong operational reason and additional protections are in place.
Network segmentation matters. Even if a tool is compromised, lateral movement should be limited. This reduces what attackers can observe or influence.
Behavioral monitoring also deserves attention. When trusted tools act in unusual ways, that should trigger review. Context matters more than tool names.
What will happen to SolarWinds and enterprise IT security in the future?
SolarWinds has been trying to earn back people's trust for a long time after problems in the past. This doesn't mean that someone is trying to hurt people or stop using a product, but it does show that attackers keep testing popular platforms.
Future attacks are likely to follow similar patterns. Trusted tools. Quiet access. Long observation periods. Defenders will need to focus more on usage patterns than signatures.
The SolarWinds attack on exposed servers is unlikely to be the last example of this approach. It is better viewed as a warning sign of where enterprise threats are heading.
Frequently Asked Questions
What is SolarWinds Web Help Desk used for?
SolarWinds Web Help Desk is an IT support platform used to manage service tickets, assets, and alerts. It is commonly deployed in enterprise and mid-sized environments.
Were all SolarWinds users affected?
No. Only systems that were exposed to the internet and vulnerable were at risk. Organizations with restricted access and proper configuration were far less likely to be impacted.
Did attackers steal data?
Public reporting does not confirm widespread data theft. The focus appeared to be observation and monitoring rather than immediate exfiltration.
Why is using DFIR tools dangerous in attacks?
DFIR tools are trusted and commonly used by defenders. When attackers deploy them, malicious activity can blend in with normal administrative behavior.
Is this related to earlier SolarWinds incidents?
This incident is separate from earlier supply chain attacks. However, it continues the theme of attackers targeting trusted enterprise software.
Hoplon Insight Box
Key Recommendations Based on Observed Activity
• Review all internet-facing services and close unnecessary exposure
• Restrict access to IT management platforms using network controls
• Monitor how tools are used, not just which tools are installed
• Treat prolonged quiet access as a high-risk indicator
• Document and regularly audit configuration exceptions
Final Takeaway
The SolarWinds attack on exposed servers was not about dramatic destruction. It had to do with being patient, being seen, and abusing trust. Attackers showed how easy it is to turn normal activity against organizations by taking advantage of unprotected Web Help Desk systems and using real forensic tools.
The lesson is clear. It's not just the tools that are important for security, but also how and where they are used.
not just about tools, but about how and where those tools are used.
Share this :