New Stealit Malware Attacks in 2025: New Wave Hits Windows Users

Hoplon InfoSec
13 Oct, 2025
It started out quietly, like a rumor that spread through developer forums. A few strange executable files that were strange enough to make people raise their eyebrows started to spread through game mod sites and free VPN installers. Researchers then found out the truth: the new Stealth Malware attacking Windows systems uses Node.js extensions in a way that no one expected. What seemed like harmless software was really a polished info stealer that was hiding behind real technology.
When I first read the Fortinet research notes, I was struck by how subtle it all was. This wasn't a loud ransomware campaign or a simple phishing trap. It was quiet, graceful, and almost like surgery. The malware turned Node.js Single Executable Applications (SEA), which developers trust, into a cover for stealing data online. It shows us that cybersecurity isn't just about new ideas on one side.
The Evolution of Stealit: From a Simple Thief to a Skilled Operator
Stealit didn't show up yesterday. It has been around for a while in the darker parts of the internet, where it is known as a password-stealing tool that is sold on the black market. But by 2025, it had grown into something much bigger. An infostealer that used to be simple has now become part of a malware-as-a-service (MaaS) ecosystem. Anyone with a few hundred dollars and little skill could rent Stealit, change the payload, and start their own attacks.
The new Stealit malware that attacks Windows systems uses Node.js extensions in a way that makes it both stealthy and flexible. In older versions, hackers would hide bad scripts in Electron apps and trick people into downloading fake utilities or "free" software. Now that they've upgraded, they're using Node.js SEA to package their payloads. This is a real developer feature that lets coders put code into one standalone executable.
It's like putting something dangerous in a trusted delivery van in the real world. Antivirus programs often think these executables are safe because they look like regular developer builds. That's what gives this version its power.
How the Attack Works: From Interest to Compromise
A link to a download that looks good is usually the start of the infection chain. Picture a teen looking for a hacked version of a popular game or a "fast free VPN" that someone posted on Discord. They download the file from Mediafire, double-click it, and in a matter of seconds, their Windows computer is hacked. The installer looks normal, with buttons, icons, and a progress bar, but behind that facade is the New Stealit Malware Attacking Windows Systems Abuses Node.js Extensions.
There is a compressed JavaScript payload inside the Node.js executable. When it starts up, it quietly extracts itself from memory and starts running without opening a command window. There are no pop-ups, alerts, or anything else that could make someone suspicious. Once it's running, it does a quick scan of the system to get information about the machine, user accounts, browser cookies, and crypto wallets that are stored on the machine.
The code is made up of parts. Each piece has a job: one module steals session tokens, another collects saved passwords, and a third connects to a remote server using encrypted communication. The malware is both flexible and strong because of this layered design. If one part breaks, the others can still work.
Node.js Extensions: The Best Way to Hide
The abuse of Node.js extensions is at the heart of this campaign. These extensions help developers package code neatly so they can share it. It works on all platforms, is fast, and is light. But for a hacker, that efficiency is a way to hide.
The new Stealit malware that targets Windows systems takes advantage of Node.js extensions because they let scripts run without needing to install Node.js on the system. Traditional detection systems don't always look very closely at these compiled binaries. They see a normal executable and keep going.
In this case, the people who made Stealit put bad modules into what looks like real app code. The app works fine when you run it, but in the background, hidden processes start gathering private data. The payload runs entirely in memory, so it doesn't leave many traces on disk. It's hard to trace, even for seasoned analysts.
It's smart engineering, but for the wrong reasons. These developers are using new ideas as weapons instead of making better apps.
How It Avoids and Stays: Technical Debt
One of the worst things about this malware is that it can hide. Stealit embeds itself deep in the system after the first launch, making sure it comes back to life after every reboot. It could add tasks to the startup list, make entries in the Windows registry, or even drop hidden scripts in system folders.
It does a lot of checks before it runs its main functions to avoid being found. It shuts down right away if it sees a virtual machine or a sandbox environment, which are common setups for analyzing malware. It looks for tools like Wireshark or IDA and, if it finds them, pretends to be a broken app.
The New Stealit Malware Attacking Windows Systems Abuses Node.js Extensions takes the game to the next level here. It gets real process names and behaviors from Node.js binaries that it runs through. Windows Defender might think it's just a regular Node.js app. That's a big problem for defenders who use automated detection instead of watching how people behave.
Its use of encryption adds another layer of deception. The malware talks to its command-and-control server in a way that makes it almost impossible to intercept without deep packet inspection. Every session key is different, and every transfer is hidden in regular HTTP traffic. It's like whispering in a crowded room for attackers—no one hears them.
Why Windows Users Are at Risk: Targets and Tactics
So why go after Windows in particular? In short, it's still the most popular operating system in the world. The new Stealit malware that targets Windows systems takes advantage of Node.js extensions because Windows systems are very easy to attack. Every day, millions of people use unverified downloads on their personal laptops and small-business PCs.
Attackers are counting on how people act. They don't need zero-day exploits or fancy hacking tools; all they need is curiosity and impatience. People who want free software often skip antivirus scans or ignore warnings from their browsers. And because a lot of these infected installers look like they were made by professionals, the trap seems safe.
Stealit variants have been found on social media, file-sharing sites, and even YouTube comments that link to "cracked" software. This combination of social engineering and technical evasion makes it a double threat. If you click the wrong button, private information can start going to an unknown server in just a few minutes.
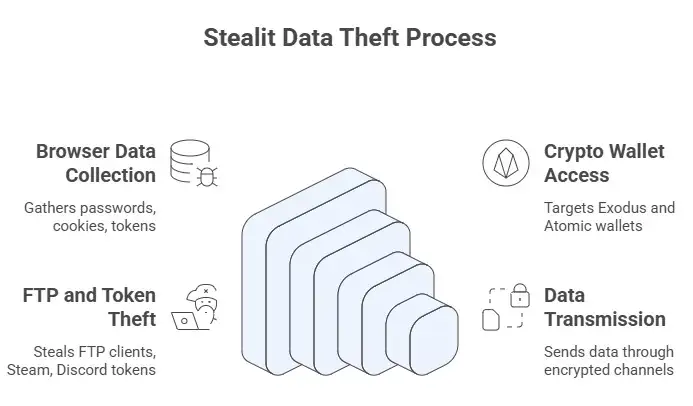
What Stealit Steals: Inside the Data Harvest
Stealit starts gathering information in the background after it is installed. First up is browser data, like saved passwords, cookies, and session tokens. That lets hackers get into everything from online banking to Gmail accounts. Next, it goes to crypto wallets and looks for popular clients like Exodus or Atomic. After that, there are FTP clients, Steam, and Discord tokens.
The new Stealit malware that attacks Windows systems uses Node.js extensions so well that many victims don't even know they've been hacked. There are no pop-ups, no crashes out of the blue, and nothing else that is too big. The malware keeps running, copying data to temporary files, and sending it off through encrypted channels.
In some cases that were seen, attackers used the stolen credentials to break into more systems, send spam, or even install ransomware. It's not just stealing data anymore. It's a way for bigger breaches to happen.
Think about waking up to find that all of your game accounts are locked, your crypto wallet is empty, or the credentials for your business have been sold on a dark web forum. That's what happened to a lot of people who unknowingly ran one of these bad installers.
Researchers at Fortinet found that some of this campaign came from file-sharing networks where fake gaming software was common. One file pretended to be a mod pack for Minecraft, and the other said it was a new VPN tool. Each had the same payload based on Node.js.
It's even scarier for businesses. A worker downloads a productivity tool that looks harmless, but within hours, sensitive company data starts to leave the network. The New Stealit Malware Attacking Windows Systems Abuses Node.js Extensions shows how even small mistakes in digital hygiene can lead to big problems.
Why It's So Hard to Find
Antivirus programs that have been around for a long time rely on known signatures. They look for matches in byte patterns or hashes. But this new malware keeps changing its shape. Every build is a little different, and every hash is one of a kind. Even advanced sandboxing doesn't always work because the malware stops running when it sees that it's being looked at.
Security teams are realizing that behavioral detection, which means watching what a process does instead of how it looks, is now very important. For instance, if a Node.js process starts reading browser files or sending data to strange domains, it should set off alarms. But most users won't notice unless they have advanced endpoint detection and response tools.
The New Stealit Malware Attacking Windows Systems Abuses Node.js Extensions shows how easily our ideas about "trusted technologies" can be broken. The same tools that developers use to make apps that work on many platforms are now being used to attack them. It's a scary reminder that things that are easy to use often come with hidden dangers.
How to Protect Yourself from Stealing
Habits are the first step in protection. Don't ever download software from places that aren't official. Always check the checksums and digital signatures. Keep security updates on and only run applications that have been signed.
Security experts say that firewalls, behavior-based antivirus, and strict application control policies are all good ways to protect yourself. Monitoring outbound traffic for strange behavior is very important for businesses. If a workstation suddenly starts talking to IP addresses that look fishy, you should look into it.
Small steps are important for each user. Don't ignore warnings from the system. It's likely that a game installer is too good to be true if it looks that way. Make backups of important files often, and only keep sensitive information in encrypted formats.
The New Stealit Malware Attacking Windows Systems takes advantage of careless Node.js extensions. Being aware and being disciplined are its natural enemies.

Stealit homepage(source: fortinet)
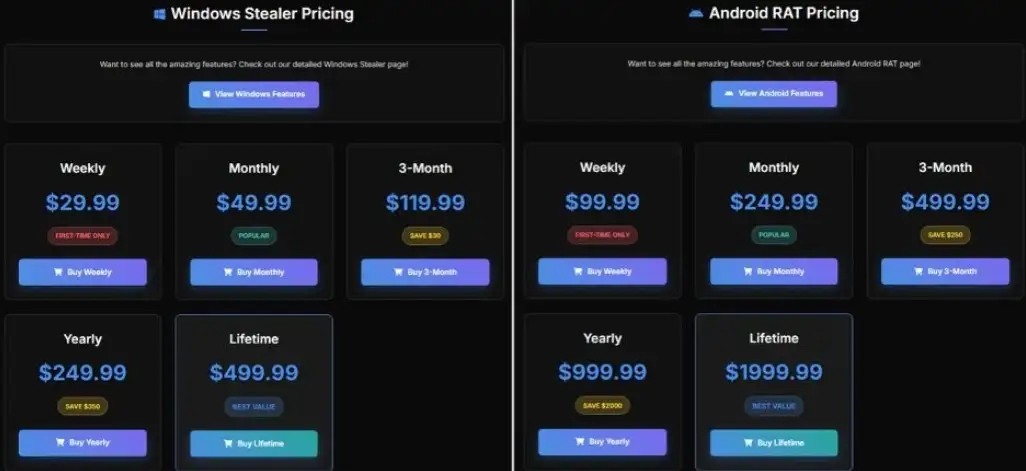
Stealit pricing(source: fortinet)

A promotional post on StealIt’s Telegram channel(source: fortinet)
Developers and the Node.js Community
This is also something developers can't ignore. The community needs to act when people misuse real tools. Strengthening code signing, adding checks for integrity, and promoting safe packaging practices are all important first steps.
When making single executable applications, the Node.js maintainers could add optional security prompts to warn users about including scripts that haven't been checked. Teachers and people who work on open-source projects can help people learn about how to use SEA responsibly and how it could be misused.
If the software industry doesn't build trust in its own tools, hackers will keep using new technology for bad things.
What We Can Learn from a Digital Chameleon
The technology of each generation of malware is different. The New Stealit Malware Attacking Windows Systems that uses Node.js Extensions isn't just another threat; it's a sign of where cybercrime is going. Attackers are figuring out how to hide behind the technologies that make modern software work.
The main point of this campaign is that security is never static. As frameworks change, so do the ways they can be used. We can't just rely on antivirus software or patches; we also need to be aware, curious, and skeptical.
Keep Stealit in mind the next time a download promises something fun. The installer that looks clean might not be safe at all. And the tool that was made for developers could be the perfect cover for a thief.
Hoplon Infosec’s Endpoint Security protects Windows systems from threats like Stealit malware, blocking malicious executables and safeguarding sensitive data before it can be stolen.
Share this :