Investigators Identify Hijacking Locker Malware Using Stolen Code-Signing Certificates.
Hoplon InfoSec
15 Oct, 2024
Cybersecurity experts found a malware campaign utilizing “Hijack Loader,” certified with valid code-signing certificates. HarfangLab uncovered the threat, distributing the Lumma information stealer via PowerShell scripts and DLL side-loading methods. The virus uses a variety of tactics to prevent detection, including signed binaries. This research demonstrates that code-signing certificates alone are insufficient signs of trustworthiness, as attackers might use flaws to spread malicious code.
Recently, cybersecurity experts uncovered a highly sophisticated malware campaign, dubbed ‘Hijack Loader,’ that leverages stolen code-signing certificates to evade detection. This virus, a carrier of threats like Lumma Stealer, infiltrates systems using advanced tactics such as PowerShell scripts and DLL side-loading.
This discovery underscores the evolving threat landscape, where even legitimate certificates can be weaponized, challenging the efficacy of standard security solutions. The need for constant adaptation and vigilance in managing such sophisticated attacks is paramount in the cybersecurity realm.
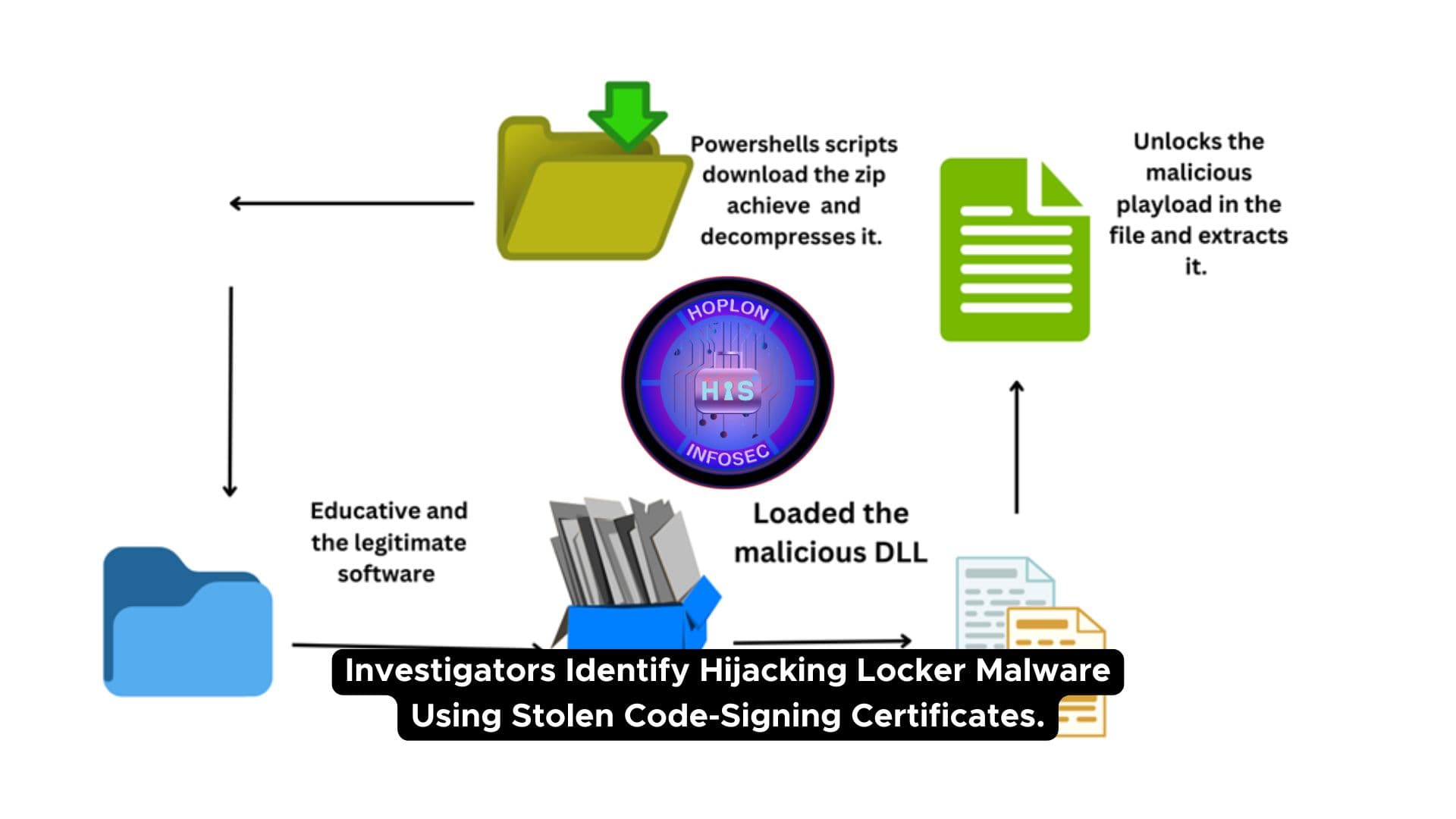
During the discovered malware campaign, attackers use a Hijack Loader to spread malicious payloads, namely the Lumma Stealer, by leveraging stolen code-signing certificates. This is crucial because code-signing certificates are commonly accepted as indicators of authentic software. The virus circumvents typical security mechanisms using these certificates, making identification difficult. The advertising employs sophisticated tactics such as DLL side-loading and PowerShell scripts, emphasizing the increasing sophistication of current cyber attacks and the necessity for stronger defenses in cybersecurity efforts.
Hijack Loader Malware Delivery of Lumma Stealer
The Hijack Loader virus installs the Lumma Stealer, an information-stealing application that collects sensitive data from infected computers. The attackers utilize stolen code-signing certificates to masquerade the malware as genuine software, allowing it to circumvent typical security measures.
The distribution method uses DLL side-loading and PowerShell scripts, allowing Hijack Loader to run malicious programs undetected. Once within the system, Lumma Stealer can collect data such as login passwords and financial information, posing significant security concerns to enterprises.
The virus is a delivery channel for Lumma Stealer, a program that steals sensitive information from affected devices. Attackers use stolen code-signing certificates to make malware look legal, allowing it to avoid antivirus and security software. Malware spreads through sophisticated tactics such as DLL side-loading and PowerShell scripts, enabling malicious code to operate undetected on the target system. Lumma Stealer, once launched, takes vital information such as passwords, financial details, and personal data, posing a severe cybersecurity concern.
Hijack Loader malware acts as the initial stage of an attack, delivering the highly dangerous Lumma Stealer by exploiting stolen code-signing certificates. These certificates give the malware a legitimate appearance, enabling it to evade detection by most security solutions. The use of the DLL side-loading technique, where a malicious DLL file is loaded through a legitimate application, is a key part of this delivery.
When combined with PowerShell scripts, these methods allow the attacker to install Lumma Stealer, which then collects sensitive data like login credentials, session cookies, and financial information from the infected system.
HarfangLab has identified three distinct versions of the PowerShell script, with the first instance detected in mid-September 2024. Each version represents an evolution of the malware, demonstrating the adaptability and persistence of the attackers.
A PowerShell script that uses mshta.exe to execute code from a remote server
A remotely-hosted PowerShell script that is immediately run using the Invoke-Expression cmdlet.
A PowerShell script uses msiexec.exe to download and execute a payload from a remote URL.
Stolen Code-Signing Certificates
The exploitation of Stolen Code-Signing Certificates by the Hijack Loader malware is a wake-up call for the cybersecurity community. These certificates, designed to verify software authenticity, have been hijacked by attackers to give their malware a cloak of legitimacy, bypassing many security measures. This not only makes the malware harder to detect but also undermines trust in the code-signing system. It’s a clear signal that even trusted certificates can be compromised, necessitating immediate and enhanced scrutiny of certificate-based trust in cybersecurity protocols.
Misusing these certificates raises serious concerns about the reliability of certificate-based trust models, as even verified software can become a vehicle for cyberattacks. Organizations must adopt stricter measures to validate code signatures and detect compromised certificates. Stolen Code-Signing Certificates are pivotal in sophisticated malware attacks like Hijack Loader.
These certificates, originally intended to verify software legitimacy, are hijacked by attackers to sign malicious code. This allows malware to evade detection by masquerading as trusted software, making it highly effective at bypassing traditional security measures.
Exploiting these certificates demonstrates how traditional trust mechanisms in software distribution can be manipulated, necessitating stricter verification and monitoring processes.
Expanding on this further:
Misuse of Trust: The theft and subsequent misuse of these certificates fundamentally undermine the trust model that certificates are based on. Security systems typically regard signed code as safe, making it easier for malware to blend in and evade detection.
Broader Attack Surface: Once these stolen certificates are acquired, attackers can use them across different malware campaigns, infecting a wide range of victims with seemingly legitimate software.
Mitigating the Threat: Organizations must employ multi-layered security measures beyond trusting code-signing certificates, such as real-time behavior analysis, stricter access controls, and certificate reputation management, to detect and prevent such misuse.
The larger cybersecurity implications of stolen code-signing certificates are significant, as they undermine faith in digital signatures and security mechanisms. When attackers use these certificates, they expose flaws in established trust models, proving that even trustworthy software may be corrupted. This makes it more difficult to identify and mitigate malware, as many security solutions rely on the integrity of signed code.
To combat this, organizations must adopt a more proactive stance in identifying and mitigating emerging threats, including advanced techniques like real-time monitoring, threat intelligence sharing, and more stringent verification processes. This shift not only enhances resilience against such attacks but also pushes the cybersecurity industry towards a more proactive stance in identifying and mitigating emerging threats, ultimately fostering a more secure digital environment.
For more details, visit:
https://thehackernews.com/2024/10/researchers-uncover-hijack-loader.html
https://securityaffairs.com/65233/deep-web/digital-code-signing-certificates-malware.html
Share this :