Supply Chain Attacks: The Door No One Sees

Hoplon InfoSec
23 Aug, 2025
Supply Chain Attacks
A Shocking Wake-Up Call
My acquaintance works in the financial field. She called me in a panic on Monday morning. Her firm had done a standard software upgrade over the weekend. Nothing strange. By Monday, it was a mess. Emails didn’t get through, data was lost, and accounts locked themselves. Later, they found out that hundreds of other businesses had the same problem.
That wasn’t poor luck. It was an attack on the supply chain. Hackers didn’t break down the front door. They strolled right in pretending to be a trustworthy seller.
What do supply chain attacks really look like?
Just think about it. Hackers don’t always go straight for the target. First, they go for the suppliers, partners, or software builders. Then the damage moves down the line.
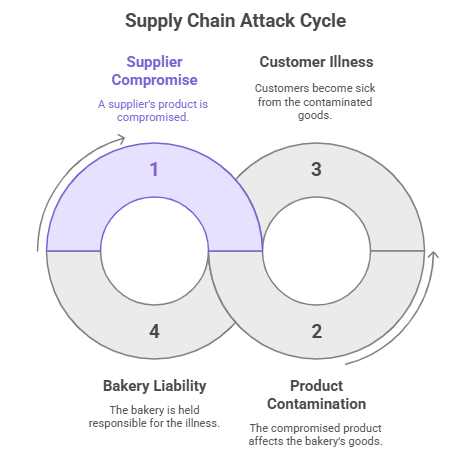
It is like putting poison in flour at the mill. Customers are already in danger by the time the bakery creates bread and sells it. The bakery had no chance.

Why Hackers Go This Way
It’s hard to break into a corporation head-on. Firewalls, security mechanisms, and trained workers. But if you can get into a small vendor with weaker protection, you can get in with half the work.
From the point of view of a criminal, supply chain attacks work well. One bad update might hurt thousands of people.
Looking Back: The Attacks That Made Everything Different
This method has been around for many years. Hackers in the past utilized floppy disks that had been tainted to disseminate malware. The notion has just changed.
NotPetya spread all over the world in 2017 after taking over an upgrade for Ukrainian accounting software. It put shipping firms, banks, and even hospitals out of business. In 2020, SolarWinds showed how bad supply chain hacks may be. Hackers put bad code into software that governments and Fortune 500 corporations trust.
How They Get In
There are a lot of tricks. Some attackers get into the process of building software. Others change the hardware before it gets to you. Even small flaws, like weak passwords or systems that aren’t up to date at a vendor, might let anybody in.
Once inside, assailants take their time. They wait, fit in, and then attack when it matters most.
The Domino Effect That No One Thinks About
Picture yourself as the owner of a tiny bakery. You get your flour from a provider. If that flour is dirty, every loaf, cake, and cookie will make people sick. And those customers hold you responsible, not the mill.
That’s how attacks on the supply chain work. If one link in the chain breaks, the damage spreads far beyond where it started.
Different Kinds of Trouble
There are different types of these attacks. Some get into software updates. Some of them have hardware that is not working right. Attackers can also go after open-source projects by putting bad code into shared libraries.
Every style is risky. Updates seem safe and real. It can take years for hardware problems to show themselves. And vulnerabilities in the cloud can affect many businesses in only a few hours.
Third-Party Vendors: The Weak Spot
Businesses currently rely a lot on outside vendors. Cloud providers, IT contractors, and payroll services. Each one makes things easier, but they also make things riskier.
Companies think that if they trust a partner, they are safe too often. That is exactly what attackers take advantage of.
The Risk That Comes with Updates
Updates are meant to keep us safe. They tell us to patch up swiftly to keep safe. But if the update itself is hacked, you are putting the attacker’s code on your own computer.
This is very harmful, as SolarWinds revealed. Updating was the appropriate thing to do for thousands of groups. That one thing led to their collapse.

NotPetya caused billions of dollars in harm. One of the biggest shipping firms in the world, Maersk, had to build hundreds of servers from the ground up. FedEx also lost hundreds of millions of dollars. The system that monitored Chernobyl even went down for a short time.
SolarWinds let people spy on U.S. government institutions for months. People who were hurt trusted a tool they had used for years. That breach of confidence is what made the attack so memorable.
Why They Are So Hard to Find
Traditional security systems seek for things that seem wrong. But real updates come with supply chain assaults already in them. Signed and checked.
It’s like putting a false grain of rice in a big bag. You don’t know something is incorrect until after you’ve cooked and served it. At that point, it’s too late.
The Damage That Goes Beyond Money
The loss isn’t just money. Companies can get sued, fined, and lose business. But trust is the deeper wound.
Customers lose trust when they find out that a supplier leaked their information. And once trust is gone, it’s hard to get it back.
What Businesses Can Really Do
There is no perfect way to defend yourself. But groups can make it difficult for people to attack. Check vendors more carefully. Make audits necessary. Use frameworks that don’t immediately trust anyone.
It also helps to have layered defenses. It’s like putting a lot of locks on a door. It might not stop every intruder, but it does slow them down and limit the damage.
What Normal People Can Do
This isn’t only a problem for the boardroom. People and employees are important. Be wary of upgrades that seem strange. Tell someone about strange behavior on the system. Stay away from unapproved or pirated software.
At home, make sure to use strong passwords, turn on multi-factor authentication, and only install software from trusted sources. These little things can make the difference between being safe and being exposed.
Are They Here to Stay?
Yes, unfortunately. There will always be supply chain attacks. As organizations rely more on global networks, attackers will keep going after the weakest points.
The only genuine chance is working together. Governments need to communicate information more quickly. Companies need to make sure that their providers do what they say they will. And workers need to stay on their toes. If not, these attacks will stay concealed in doors that no one is monitoring.
Explore our main services:
Share this :