IMPORTANT: How to repair the Tableau Server vulnerability quickly

Hoplon InfoSec
25 Aug, 2025
Tableau Server vulnerability
A little file goes to a staging site. No flash. Minutes later, the monitoring lights up, and service accounts start doing things they shouldn’t. The problem is related to a fault in how Salesforce security teams recently handled files for Tableau products. Anyone who utilizes Tableau for analytics or puts it in customer apps should care about the story.
This is the first time you’ll see the phrase “Tableau Server vulnerability” used to tell you what to repair today, what to look out for tomorrow, and how to explain risk to leaders.
What happened, and why now?
Salesforce found a number of problems via a proactive security check, sent out warnings, and included remedies in the maintenance release on July 22, 2025. CVE-2025-26496 is the worst problem. It’s a type of misunderstanding error in the file upload modules that can let local code into the system and completely compromise Windows and Linux.
Some more notable Tableau CVEs are unlimited file uploads that permit remote code execution and path traversal issues in upload flows. Together, they make the upload and document processing parts more vulnerable to attacks.
Why this Tableau Server security hole is important for all businesses
Attackers really like upload endpoints. They let enemies sneak in tailored payloads, move from the web tier to the host, and then move into data storage that powers dashboards. When the analytics layer is hacked, the breach generally gets to the same systems that company leaders monitor every day.
Security teams should see this as an important upgrade and a chance to fix problems that have been around for a long time with handling files and API permissions.
Versions that are affected and safe targets for upgrading
Authoritative records show that the critical upload flaws affected versions before 2025.1.3, 2024.2.12, and 2023.3.19. Independent coverage says you need to move to at least 2025.1.4 or later. At the time of writing, the current Tableau Server download site indicates 2025.1.5 as the branch head.
If you run clusters that last a long time, go to the most recent maintenance release in your branch that is still supported.
Threat model in simple terms
If a user, service, or integration may upload files to Tableau endpoints, a specially made file could be interpreted as the wrong type, included by the server, and used to run code or read sensitive paths. When you add weak service account scopes to that, you can move sideways into data sources and secrets.
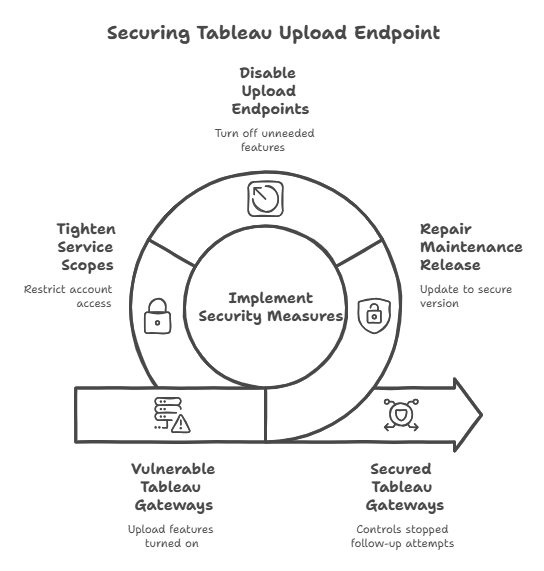
A global retailer discovered several Tableau gateways on the internet that were running a weak branch with upload features turned on for a B2B site. Their red team showed that a specially made file made it to the upload modules. Then, they utilized a path traversal vulnerability in a related API to get the credentials that let them see analytics data. The company repaired the maintenance release, turned off unneeded upload endpoints, and made service account scopes tighter. The controls stopped attempts to follow up during verification. The timeline matched published warnings and version advice from July 2025.
Things to look for in logs and telemetry
- Sudden jumps in POST requests to upload or tabdoc API endpoints
- File extensions that are out of the ordinary, multiple extensions, or names that are meant to trick you
- After an upload is done, files are read from directories they shouldn’t be in.
- New or changed temp files, then service restarts
- Service accounts getting to secrets or data sources they never used before
- These patterns are similar to how unrestricted or type-confused uploads act in the real world.
Quick checklist for busy teams to fix things
- Find all of your Tableau instances, including those for development and testing.
- Limit who can upload files and from where, especially on gateways that front the internet.
- Get the most recent maintenance release for your branch and install it.
- Change the secrets that Tableau services and connections utilize.
- Add WAF rules for filenames that look like they are trying to trick you and upload patterns that look suspect.
- Look for strange file paths that the tabdoc or upload APIs use.
- Allow service accounts to have the least amount of access they need, and get rid of old tokens.
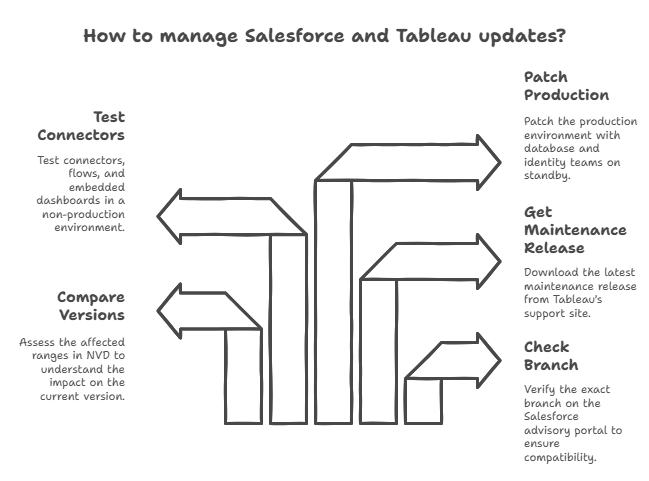
Path to improve step by step
- Look up your exact branch on the Salesforce advisory portal.
- Look at the affected ranges in NVD and see how your version of running compares.
- From Tableau’s support site, you can get the latest maintenance release.
- In a non-production environment, test connectors, flows, and embedded dashboards.
- During a window, patch production with database and identity teams on standby.
Things to ask your team this week
- Which settings still allow uploads from networks that aren’t trusted?
- Do any partners or apps automatically upload files through jobs?
- Are the Tabdoc and EPS modules keeping track of full request paths?
- Which service accounts can write to the filesystem behind the gateway?
- Is there an actual allowlist for file kinds that we follow?
- Each answer makes it clear what exposure is and what the steps are while patching.
- ZeroPath
- Copy and paste this executive summary into an email.
This Tableau Server flaw lets hazardous or mislabeled file uploads run programs or read files on hosts. Salesforce told everyone about the problems and fixed them in July 2025. Our risk depends on who may upload, how uploads are checked, and what our service accounts can access after a breach. The solution is to upgrade right away, limit upload surfaces, and make permissions stricter.
A technical deep dive for admins
Concentrate on three controls. First, the edition. Cases that happened before 2025.1.3, 2024.2.12, and 2023.3.19 are the most dangerous and need to be updated. Second, make sure that file types follow a positive model, don’t allow multiple extensions, and prevent filenames that look like scripts. Third, make secrets and OS-level permissions stronger so that uploaded stuff can’t touch important paths or keys.
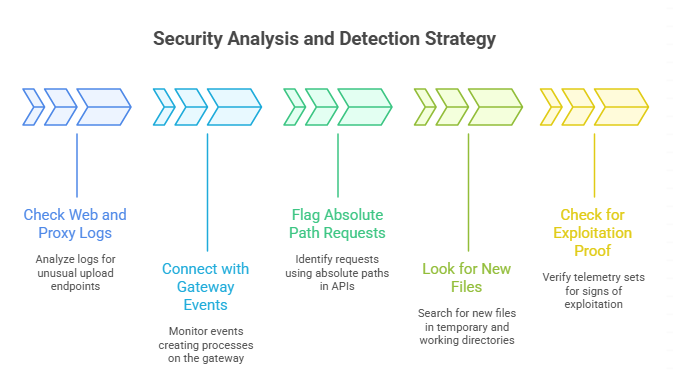
- Analysts’ strategy for detection and hunting
- Check web and reverse proxy logs for upload endpoints that have status codes that are different from what is normal.
- Connect with events that create processes on the gateway. Keep an eye out for script interpreters or strange child processes.
- Flag requests that use absolute paths in tabdoc-related APIs.
- After uploads, look for new files in the temp and working directories.
- Check to make sure that no public proof of exploitation has shown up in your telemetry sets, and then keep an eye on the feeds.
How this is different from other Tableau problems
There were a lot of CVEs in upload and input validation in the last several months. One set lets you upload files without any restrictions in EPS modules. Another one lets you go over paths using Tabdoc APIs. The pattern highlights why companies need to patch quickly and see file handling as a crucial tier rather than a nice-to-have feature.
Cloud and embedded use cases need extra attention.
If you put dashboards in client portals or automate uploads from cloud operations, make sure those parts are separate from each other with strong network and identity boundaries. Limit which tenants can upload. Stop TLS at a gateway you control, add inspection, and log request bodies where regulations allow. These procedures make a Tableau Server vulnerability less dangerous while a patch is being fully applied.
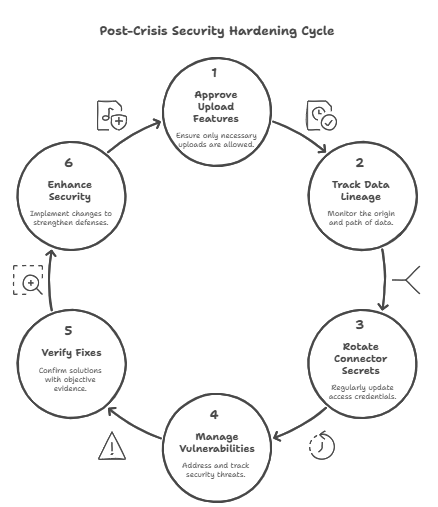
Updates to policies and governance that stick
- Make it clear that upload features are exceptions that need approval.
- Keep track of the data lineage for every file that goes into Tableau flows.
- Require connectors to change their secrets every so often.
- Add the applicable CVEs to your vulnerability exception tracker and set a deadline for when they will expire.
- Check that the fix works with an objective artifact, not just a change ticket.
- These policy changes keep hardening alive after the crisis.
- Conversations between buyers and sellers will speed up.
When you talk to managed service providers and embedded analytics vendors, ask them what branch they run, when they will upgrade, and how they limit uploads. Ask them for the logs for your tenant. Make sure that their compensating controls are in line with the vendor recommendation and the NVD guidance. If they can’t provide you details, plan to block access until they fix the problem.
Questions and Answer
No, this isn’t just about one CVE. There were a number of problems in the disclosure window, but CVE-2025-26496 is the worst and has to do with the upload modules. Related upload vulnerabilities and path traversal problems make the risk picture bigger.
Do we have proof that people are being exploited in the wild?
There is no public proof of exploitation or public proof of concept as of the end of August 2025. That could change, so keep an eye on threat feeds.
Feedly
Which version should we choose?
Advisories list the versions that will be affected before 2025. 1.3, 2024.2.12, and 2023.3.19. A number of sources say 2025. 1.4 or later. 2025 is the current date on the product page. 1.5. The newest maintenance release for your branch is the safest option.
Does Tableau Desktop need to be fixed too?
Yes. The important problem with type confusion impacts both the server and the desktop. Update both when necessary.
In the End
The latest Tableau Server vulnerability reveals that even trusted business tools may become valuable targets if file upload features aren’t examined. This is not just a job for security leaders to fix; it should also remind them to make validation stronger, privileges tighter, and detection faster. The message is clear: don’t wait for something bad to happen to show the risk. Now is the time to act, evaluate your policies, and make sure your analytics platform is strong.
Hoplon Infosec is ready to help you with patching, monitoring, and long-term defense so that your team can stay one step ahead of hackers.
Follow us on X (Twitter) and LinkedIn for more cybersecurity news and updates. Stay connected on YouTube, Facebook, and Instagram as well. At Hoplon Infosec, we’re committed to securing your digital world.
Share this :