TARmageddon Rust Flaw Allows Hackers to Run Code Remotely

Hoplon InfoSec
22 Oct, 2025
You pull a tar file that looks safe into a build pipeline, and all of a sudden, your container or CI runner starts running code that an attacker controls. TARmageddon is a real-life example of the horror that is happening right now.
TARmageddon is a bug that has to do with how some async TAR implementations for Rust read boundaries. The issue is that it allows you to "smuggle" extra files into specially generated archives by getting the PAX extended headers and ustar headers out of sync.
That difference can make an extractor think that attacker data is a new tar header. This permits files to be written to or overwritten outside of the extraction boundaries that were meant to be used. In the real world, this can let code execute on systems that unpack tar archives that aren't trusted when they are built, deployed, or installed.
To be explicit, I shall call this phenomenon by its name: the tarmageddon corrosion flaw. That term is used in warnings, research papers, and examples of how to exploit something.
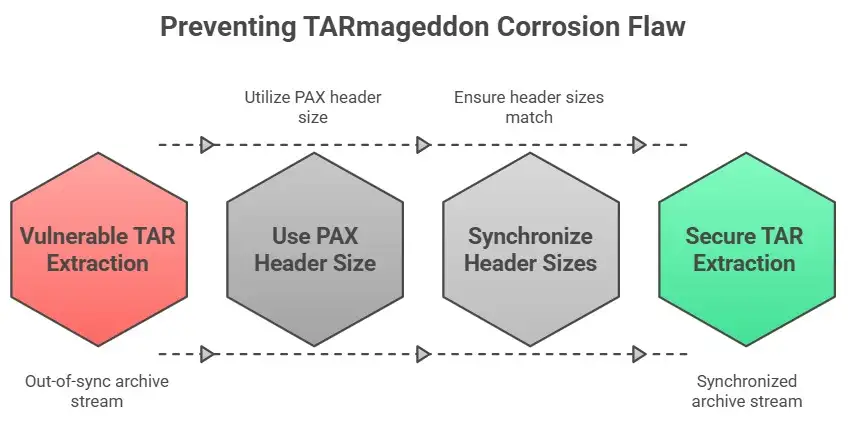
PAX enhanced headers in tar archives can update metadata like file size in more detail. The unsafe async-tar versions utilize the ustar header size instead of the PAX header size to figure out where the next header should go.
If the two numbers don't match, a well-made archive can cause the extractor to get out of sync with the archive stream. Then, the extractor mistakenly believes that the file's contents are headers and starts processing data that the attacker controls as new files. Researchers named the gap in logic TARmageddon.
The fault is hard to discover because it's not just a basic off-by-one or memory corruption; it has to do with parsing logic. It has an effect on any programming that utilizes these libraries to open archives. This means that the risk isn't only with one crate; forks, wrappers, and downstream projects that utilize or sell the code are also at risk. The Tarmageddon rust vulnerability is a good example of how a tiny change in protocols may cause a large problem.
What is affected?
The first results show async-tar and a few well-known forks and wrappers, including tokio-tar and astral-tokio-tar. Testcontainers, WasmCloud, and tools that language package managers or CI runs utilize are among well-known projects that employ these crates. To sum up, the ecosystem span is broad.
A tar parser that is weak and has a lot of dependencies is risky since it can be called from a lot of locations where you don't expect it to be. The issue has been given the identifier CVE-2025-62518, and some warnings claim it is quite dangerous, with a CVSS score of roughly 8.1.
That proves that you can access untrusted archives from a distance whilst they are being processed. There is a problem with the library code, so I'll mention the name again in simple terms so you can discover it: tarmageddon rust vulnerability.
Risk pathways
Think about a task for continuous integration that downloads build artifacts, a container build that pulls base layers from third parties, or a deployment pipeline that unpacks plugin packages. The attacker can set up files to alter scripts, binaries, or configuration files if the unpack step employs an unsafe async-tar implementation and the attacker controls the archive or has changed it.
From there, it's easy to run malicious code during the build or at runtime. This is exactly why it is so crucial to maintain the supply chain safe. Another example could be developer tools that unzip tarballs when language packages are added. A weakness that lets an attacker upload a false archive to a mirror or stop a download could be used on numerous developer PCs. The end effect is a lot of reach with very little exertion. The label still says "Tarmageddon rust vulnerability."
The vulnerability can have strong effects, but it still needs several things to work. The attacker needs a technique to send a carefully made tar archive to code that isn't very strong. It's considerably difficult to take advantage of systems that only work with archives that are signed and trusted.
On the other hand, using public package mirrors, container registries, or build artifacts from sources that haven't been vetted makes things more unsafe. The research community awarded it a high severity grade because it can lead to arbitrary file writes and possibly code execution when those conditions are satisfied. When you're looking for services that have been affected, the short form "tarmageddon rust vulnerability" makes it easy to scan logs and advisories fast.
Patches, fixes
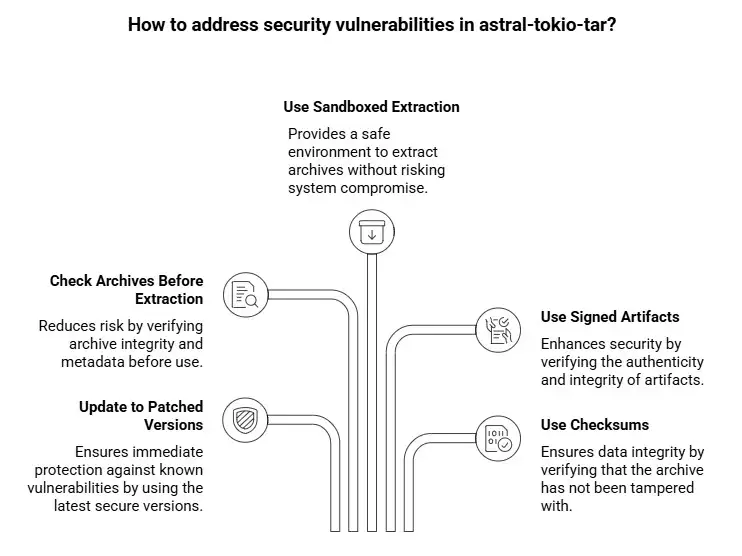
Several maintainers released advisories and fixed versions. For example, astral-tokio-tar released security warnings and corrected versions (0.5.6 and after). The responsible disclosure and patch notes say that you should either update to patched versions or carefully check archives you don't trust before extracting them. If you can't update right away, run extractors in sandboxed settings, examine the metadata of the archive before extraction, and use artifacts that are signed or contain checksums.
Use a cargo audit or a similar supply chain scanner on your dependency graph to do this. Give higher priority to crates that depend on async-tar versions. If you vendor dependencies, be sure to rebuild with the new versions. You can fix the Tarmageddon rust vulnerability with upgrades and hardening.
How to find dormant exposure in your environment
First, go through your codebase and lock files and look for any direct or indirect mentions of async-tar, tokio-tar, astral-tokio-tar, or any other forks. Use tools like cargo-audit, cargo tree, or dependency scanning in your CI pipeline.
Next, look for the places where your systems can get archives from outside sources and put up trust boundaries around them. Last but not least, extraction points: When you work with inputs you don't trust, just extract to containers or VMs that you don't care about. Also, check PAX headers when you can and log archive metadata. These actions will help protect your system even before all the updates are implemented. One more time for emphasis: add the Tarmageddon rust vulnerability to your list of vulnerabilities and keep an eye on it.
Lessons
This event teaches us two crucial things.
First, edge situations in protocols are critical. You need to verify parsing logic that combines header types very carefully from beginning to end.
Second, employing crates that are no longer used or cared for raises the risk. If maintainers aren't around, popular forks with millions of downloads can break down. The way people reacted to TARmageddon shows how weak transitive dependencies can be and how crucial it is to coordinate disclosure.
You might want to add fuzzing, tougher header validation, and safer defaults that don't let you extract untrusted archives until you say so if you have a crate that lets you extract archives. Once more, put "Tarmageddon rust vulnerability" in your changelog.
A timeframe that makes sense and what scientists say Researchers uncovered the core cause in late summer, according to public sources. They then published coordinated advisories and proof-of-concept information when remedies were ready.
The problem got worse quickly since it may hurt popular projects and instigate attacks on the supply chain. To keep track of the exact timelines for each vulnerable project, see the official warnings and CVE entries. The shortcut is still useful for sorting: Tarmageddon has a rust vulnerability.
Final thoughts
1. Check the dependencies of crates like async-tar, tokio-tar, astral-tokio-tar, and others.
2. If they are available, upgrade to the patched versions that the vendor suggests, such as astral-tokio-tar >= 0.5.6.
3. When you extract files from archives you don't trust, keep them in sandboxes and utilize signed artifacts instead.
4. Set up checks and logs at extraction points while the program is running, and then search for any file writes that you didn't expect.
5. Let the developers know about the danger, and add the phrase "tarmageddon rust vulnerability" to your internal incident tracker so that it is easy to find.
The TARmageddon Rust vulnerability shows how hidden flaws can lead to serious breaches. Hoplon Infosec can help protect your systems through Penetration Testing, identifying exploitable weaknesses like this before attackers do. Stay secure with expert testing and early risk detection.
Share this :