Texas DOT Data Breach: What Happened, Who Was Affected, and Why It Matters

Hoplon InfoSec
12 Jun, 2025
In one of the most serious cybersecurity incidents of 2025, the Texas Department of Transportation (TxDOT) confirmed a breach that compromised the private data of over 423,000 individuals through unauthorized access to nearly 300,000 crash reports. Occurring within TxDOT’s Crash Records Information System (CRIS), this event has sent shockwaves through public institutions, cybersecurity circles, and legal departments across the United States.
The breach exposed not only personal data but detailed, incident-specific information, putting citizens at risk for identity theft, insurance fraud, and emotionally manipulative phishing campaigns. In response, Texas established the Texas Cyber Command, a move that many view as the beginning of a long-overdue overhaul of the state’s public sector cybersecurity infrastructure.
This article explores the breach in detail, outlines what was compromised, how the state responded, and what lessons can be drawn from this unfolding situation.
The Timeline of the Breach
Discovery of Anomalies
The incident came to light on May 12, 2025, when TxDOT’s internal monitoring tools flagged irregular access activity within CRIS. The system, which stores all crash reports filed across Texas, had become a target due to its deep reservoir of sensitive information.
Identification of Compromised Credentials
The security team determined that a valid user account had been compromised, likely through phishing or a credential reuse attack. The account had been used to download large volumes of crash records discreetly over an extended period.
This form of “low-and-slow” data extraction is a common tactic among sophisticated attackers. Rather than drawing immediate attention by exfiltrating large data sets all at once, the adversary likely accessed smaller batches over days or weeks.
Public Acknowledgment
By early June, TxDOT released an official statement confirming the breach and initiating public notification. The agency also activated a breach response team to manage communications, technical containment, and victim support. Transparency and speed, often lacking in such scenarios, were evident in this case, earning public and professional recognition.
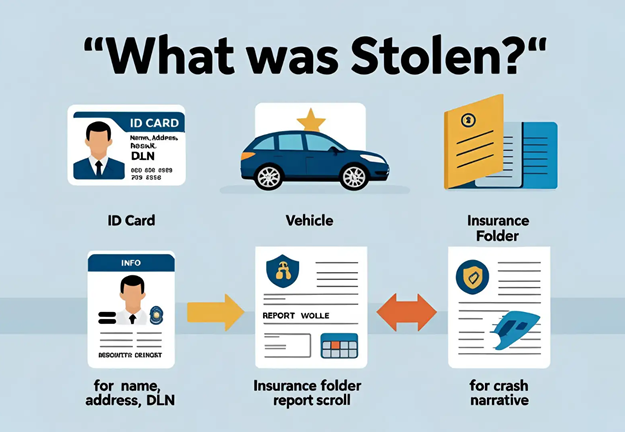
What Kind of Data Was Exposed?

Personal Identifiable Information (PII)
Crash reports in Texas include full names, dates of birth, mailing addresses, email addresses, and driver’s license numbers. These identifiers alone are sufficient to conduct identity theft, file fraudulent taxes, or apply for credit in someone else’s name.
Insurance and Vehicle Information
Beyond basic PII, the breach revealed detailed records of vehicle registrations, insurance carriers, and license plates. This makes it easier for attackers to fabricate claims or target individuals for auto-related scams.
Crash Details and Police Narratives
The most alarming data compromised may be the crash narratives themselves. These detailed incident descriptions often written by police officers include injury information, fault assessments, GPS coordinates, and even emotionally charged statements from those involved. These details can be manipulated to enhance phishing campaigns by referencing real-world trauma.
Why This Breach Is Particularly Dangerous
Sophisticated Phishing Risks
Armed with accurate crash data, scammers can convincingly impersonate law enforcement, insurance agents, or medical facilities. For example, a scammer may call or email a victim saying, “We’re following up on your March 12 accident on I-35 involving a gray Ford Escape.”
The level of personalization available here is unlike generic spam and could fool even tech-savvy individuals.
Legal and Financial Fraud
This data can be used to file false injury claims, impersonate accident victims in lawsuits, or generate fake witness statements. Insurance companies could be misled into paying fraudulent settlements.
Emotional Exploitation
Victims involved in fatal crashes or traumatic incidents may now fear their most vulnerable experiences are being exploited. This type of breach, therefore, doesn’t just expose data it exposes pain, grief, and trust in institutions.
Public Notification and Support Systems
Proactive Outreach
Unlike many public entities that delay or minimize breach notifications, TxDOT promptly mailed letters to every individual identified as being affected. These letters clearly outlined what data was compromised and included next steps for personal protection.
Dedicated Hotline and Identity Monitoring
TxDOT established a 24/7 support hotline and offered credit monitoring resources. This hotline gave people an immediate lifeline for reporting suspicious activity and understanding how to secure their digital identities moving forward.
Legal Disclosures
Although current Texas law did not require TxDOT to report this breach publicly, the agency chose to do so. This move may become a blueprint for how public agencies ethically handle digital crises, emphasizing transparency over minimal compliance.
Government Response: The Texas Cyber Command

Establishment of a Dedicated Cybersecurity Agency
In June 2025, Texas Governor Greg Abbott announced the creation of the Texas Cyber Command, backed by $135.5 million in initial funding. This dedicated entity will manage the state’s cybersecurity policies, oversee public sector network security, and coordinate incident response across departments.
Long-Term Responsibilities
The Cyber Command will be tasked with:
- Implementing state-wide Zero Trust architecture
- Monitoring public infrastructure for cyber threats
- Training government employees in cybersecurity awareness
- Setting policy and compliance benchmarks
- Performing regular penetration tests and red-team exercises
A Culture Shift in Government IT
This agency signals a profound culture shift. For too long, cybersecurity in public institutions has been seen as an IT department concern. Texas’s new initiative elevates it to a strategic function essential to governance, on par with physical infrastructure maintenance and emergency services.
The Mechanics of the Attack
Likely Exploit Path
Although specifics are being withheld due to the ongoing investigation, cybersecurity analysts agree that this was likely a privilege escalation exploit. After compromising an account probably through phishing or credential stuffing, the attacker was able to navigate CRIS without triggering alarms.
The system likely lacked sufficient segmentation, allowing broad access once inside. Without proper access logs, multi-factor authentication, or real-time detection, the attacker was free to extract sensitive data undetected.
Lessons for Infrastructure Security
This breach underscores the urgent need for modern authentication controls, such as behavioral analytics, least privilege policies, and AI-driven anomaly detection.
Industry Response and Expert Opinions
The Wake-Up Call for State Systems
Security experts see this as a textbook example of what happens when critical infrastructure is built on outdated technology with insufficient oversight. Many state systems are still reliant on legacy software written in older languages and supported by skeletal IT teams.
Expert Commentary
Lisa Hernandez, a Director at Sentinel Secure, stated:
“When you leave an entire crash report system open to a compromised account, it’s not a question of if you’ll be breached—it’s when. TxDOT’s data was a sitting duck for any organized cyber actor.”
Her comments reflect a growing urgency in the cybersecurity community: governments must be proactive, not reactive.
Comparative Analysis with Other Breaches
Let’s compare the TxDOT breach with other notable incidents to better understand its place in the broader landscape:
| Breach | Year | Records Exposed | Type of Data | Consequence |
| TxDOT (Texas) | 2025 | 423,000+ | PII + crash reports | Cyber Command formed |
| Texas Tech Health Sciences | 2024 | 1.4 million | Medical, SSNs | HIPAA violations, investigations |
| Washington State Auditor | 2021 | 1.6 million | Financial aid data | Public lawsuits |
| California DMV | 2021 | 38 million | Vehicle data | Vendor and policy reform |
The depth and specificity of TxDOT’s stolen data, particularly the narrative crash reports, make it more invasive and psychologically distressing, even if the total number of affected individuals is smaller than in other breaches.
Legislative Fallout and Reform Movements
Pushing for Better Breach Laws
The breach has reignited discussions in the Texas legislature about adopting more comprehensive data protection laws. Proposals are circulating to require:
- 72-hour public disclosure deadlines
- Independent cybersecurity audits
- Mandatory data classification and encryption
- Civil liability for preventable government negligence
National Implications
Other states are watching closely. Texas, being among the first to create a full-scale Cyber Command in response to a breach, may set the tone for national standards. Federal agencies, including CISA, have begun offering additional resources to state agencies looking to upgrade systems.
What to Do If You’re Affected
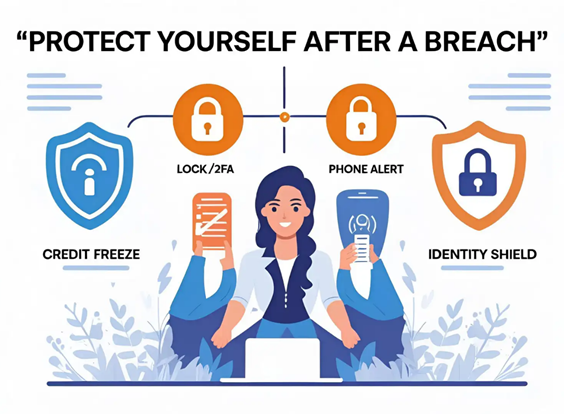
Immediate Steps
Anyone notified by TxDOT should:
- File a credit freeze with Equifax, TransUnion, and Experian
- Review bank and insurance accounts for unusual activity
- File taxes early to prevent fraudulent returns
- Enable multi-factor authentication wherever possible
- Use the dedicated TxDOT hotline for identity monitoring enrollment
Long-Term Digital Hygiene
Even if you weren’t impacted, this is a wake-up call to review your digital footprint. Use password managers, avoid credential reuse, and regularly audit what information you share online.
Final Takeaways and Conclusion
The TxDOT data breach marks a critical inflection point for public sector cybersecurity. It exposed deep flaws in legacy systems, underscored the devastating human cost of data exposure, and prompted legislative and structural reforms that will likely ripple across the country.
While the breach itself was alarming, the response sets a new precedent for how government agencies should act during digital crises, with transparency, urgency, and empathy.
As governments hold increasingly large amounts of personal data, citizens are right to demand better protection. Trust in public institutions is earned not just by building roads and managing policies but by ensuring the digital security of every person they serve.
Did you find this article helpful? Follow us on Twitter and LinkedIn for more Cyber Security news and updates. Stay connected on Facebook and Instagram as well. At Hoplon Infosec, we’re committed to securing your digital world.
Share this :