Inside the Massive 184 Million Password Data Breach: How It Happened and What It Means for You

Hoplon InfoSec
30 May, 2025
In May 2025, cybersecurity researcher Jeremiah Fowler uncovered a significant breach: an unprotected Elasticsearch database containing over 184 million unique login credentials. This exposure, one of the largest of its kind in recent years, underscores the profound vulnerabilities that persist in today’s digital environment. The breach did not result from a targeted attack on a major company’s servers. Rather, it emerged from a confluence of user-level compromises, advanced infostealer malware, and poor data hygiene, a cautionary tale for individuals and organizations alike.
This article provides a comprehensive analysis of how this breach occurred, the mechanics behind infostealer malware, the real-world implications, and the best practices to mitigate similar threats in the future.
The Discovery: Anatomy of the Database
Fowler’s analysis revealed that the database contained:
- 184,162,718 unique username-password pairs, stored in plaintext and easily readable format.
- Credentials from a wide range of services, including:
- Major email providers: Google, Apple, Microsoft.
- Social media platforms: Facebook, Instagram, Snapchat, Discord, Roblox.
- Banking and healthcare portals.
- Over 220 government email addresses from at least 29 countries, including the United States, Canada, and the United Kingdom.
- The database itself lacked any form of access control; no password, no encryption.
Such a trove of data in an unsecured environment represents a severe lapse in operational security and highlights the ongoing challenges around third-party data aggregation and data hygiene.
Understanding the Source: Infostealer Malware and the Supply Chain of Data Theft
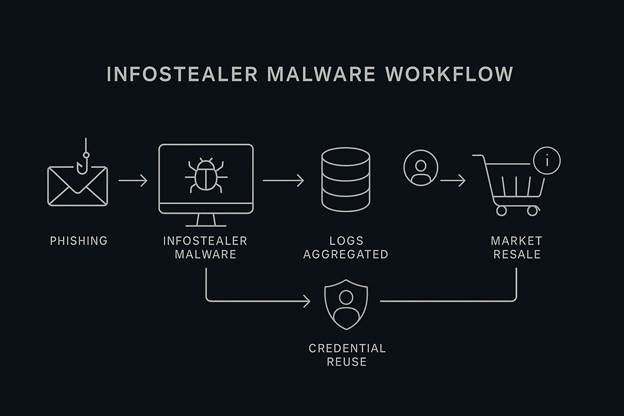
Unlike high-profile breaches involving direct attacks on corporate infrastructure (e.g., ransomware targeting corporate databases), this breach was likely the result of infostealer malware.
Infostealer malware is a category of malicious software designed to exfiltrate sensitive data from infected endpoints. Key characteristics:
- Deployment: Typically delivered through phishing campaigns, malicious advertisements, software cracks, or compromised websites.
- Scope of Harvesting: Beyond login credentials, infostealers capture autofill data, browser cookies, credit card data stored in browsers, and in some cases, messaging app data.
- Stealth: Infostealers often evade detection by traditional antivirus software due to their relatively small footprint and sophisticated obfuscation methods.
- Data Packaging: Stolen data is compiled into logs that are traded or sold in underground cybercrime marketplaces.
Common infostealers like RedLine Stealer, Raccoon Stealer, and Vidar have been implicated in similar attacks. They offer criminals a modular toolkit to exfiltrate and monetize user data at scale.
Database Aggregation
The breach suggests that the database was not tied to a single corporate breach but rather assembled from logs originating from multiple infostealer infections worldwide. Such aggregation is typically performed by cybercriminal groups who specialize in combining disparate data sources to build comprehensive credential lists for resale or targeted attacks.
Real-World Risks and Consequences
The exposure of over 184 million plaintext credentials carries significant and immediate risks:
Credential Stuffing and Account Takeover
Given the common practice of password reuse, these credentials can be systematically tested against a wide range of services; a process known as credential stuffing. Attackers employ automated scripts to attempt logins using these credentials across hundreds of online services, often with alarming success rates.
Financial and Healthcare Exploitation
Credentials tied to banking portals, financial services, and healthcare systems create direct pathways for fraud, identity theft, and insurance scams.
Government and Institutional Threats
The presence of .gov emails raises concerns around targeted phishing, social engineering, and potential infiltration of sensitive governmental networks.
Social Engineering at Scale
Attackers can weaponize this data to craft highly convincing spear phishing campaigns, impersonating trusted contacts or organizations to extract further sensitive information or deploy additional malware.
Technical Oversights and Broader Lessons

The existence of an unsecured database of this magnitude points to a broader issue: the lack of secure data handling practices in certain corners of the data ecosystem.
Lack of Encryption
Sensitive data, particularly credentials, should never be stored in plaintext. Best practices mandate hashing with modern algorithms like bcrypt or Argon2 to render passwords unusable even if accessed.
Absence of Access Controls
The database was accessible to the public, without authentication or firewall protection. This is a fundamental violation of data security principles, exposing both the data and the individuals whose privacy depends on it.
Third-Party Data Aggregators
The database did not originate from a single entity, underscoring the challenges in the digital supply chain of data. Data brokers, malware operators, and underground marketplaces create a complex web that even diligent individuals and secure companies struggle to fully control.
Actionable Recommendations for Individuals
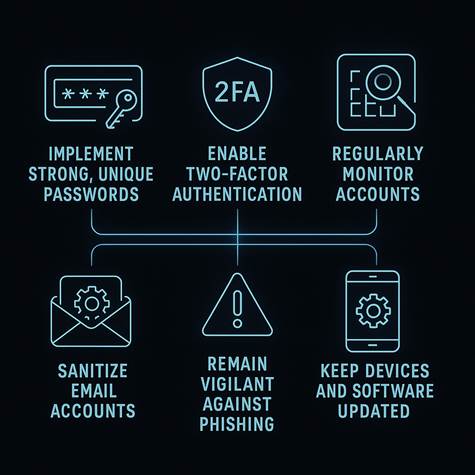
In light of this breach, individuals must take proactive measures:
- Implement Strong, Unique Passwords: Avoid reusing passwords across different services. Leverage password managers to generate and store strong, unique credentials for every account.
- Enable Two-Factor Authentication (2FA): 2FA significantly reduces the impact of credential compromises by adding a second layer of verification.
- Regularly Monitor Accounts: Watch for unauthorized logins or financial activity. Enable account activity notifications where available.
- Sanitize Email Accounts: Email accounts often serve as de facto personal archives. Remove sensitive documents, tax forms, medical records, contracts, regularly. Use secure, encrypted storage for essential files.
- Remain Vigilant Against Phishing: Expect an increase in phishing attempts leveraging exposed data. Independently verify the legitimacy of requests before sharing personal information or clicking links.
- Keep Devices and Software Updated: Regular patching is critical to close known vulnerabilities exploited by infostealers and other malware.
Strategic Considerations for Organizations
Organizations should view this breach as a call to strengthen their cybersecurity posture:
- Conduct Regular Security Audits: Identify and remediate vulnerabilities in both internal systems and third-party partnerships.
- Enhance Endpoint Security: Implement robust endpoint detection and response (EDR) solutions to detect infostealers and other stealthy malware strains.
- Adopt a Zero-Trust Approach: Treat every access request as potentially compromised, verifying identity and enforcing least-privilege principles.
- Educate Users: Provide continuous training on phishing awareness and cybersecurity hygiene.
- Develop an Incident Response Plan: Ensure that incident response plans account for third-party and supply chain breaches, not just direct attacks.
A Broader Reflection on Data Stewardship
This breach is a stark reminder that cybersecurity is not just a technical challenge; it is a matter of trust, resilience, and stewardship. When 184 million individuals’ credentials can be compiled and exposed in plaintext, it becomes clear that every user, developer, and organization has a role to play in safeguarding data integrity.
The convenience of digital services must be balanced with a sober awareness of the evolving threat landscape. As infostealer malware becomes increasingly commoditized and data brokers continue to thrive in the shadows, the collective digital hygiene of individuals and organizations becomes the first and sometimes only, line of defense.
Conclusion
The exposure of 184 million plaintext credentials illustrates how the digital ecosystem’s weakest links, individual endpoints infected by infostealers, can be aggregated into a profound global security risk. While the breach’s immediate impact will unfold over months and years, the underlying lesson is timeless: cybersecurity is a shared responsibility, and vigilance at every layer of the digital experience is no longer optional—it is essential.
For those who see cybersecurity as merely a technical discipline, this incident is a reminder that it is, at its core, about safeguarding human lives and livelihoods in an increasingly interconnected world.
Did you find this article helpful? Follow us on Twitter and LinkedIn for more Cyber Security news and updates. Stay connected on Facebook and Instagram as well. At Hoplon Infosec, we’re committed to securing your digital world
Share this :