Third-party Vendor Breachs Impacting Major Corporations
-20251016080336.webp&w=3840&q=75)
Hoplon InfoSec
19 Oct, 2025
I still remember the afternoon when a friend called to say that their credit card information had been used at a well-known store. They sounded confused. How could a big company forget something so simple? The voice on the phone is the real person behind news stories about vendor breaches and corporate compromises.
This article shows how those dominoes fall, where businesses keep failing, and what leaders can do to stop the next one from happening. As I go along, I will keep coming back to one stubborn fact: when a company trusts an outside supplier without checking the locks, things go wrong. A lot of the time, the cause of that trouble is a breach by a third-party vendor.
The attackers like the quiet route.
Most cyber attacks on big businesses don't come from a flashy zero day in a flagship product. They get in through someone smaller that the giant trusts. A well-known case is when hackers used login information from an HVAC company to break into a big store and steal millions of payment records. That event showed that attackers like to take the easiest route, going from a weak vendor to a big target instead of blasting through tough defenses.
Think of it as the back door to a big house. There are bolts and cameras on the main entrance, but the little service entrance is used by dozens of contractors and isn't checked very often. Attackers take advantage of that human trait.
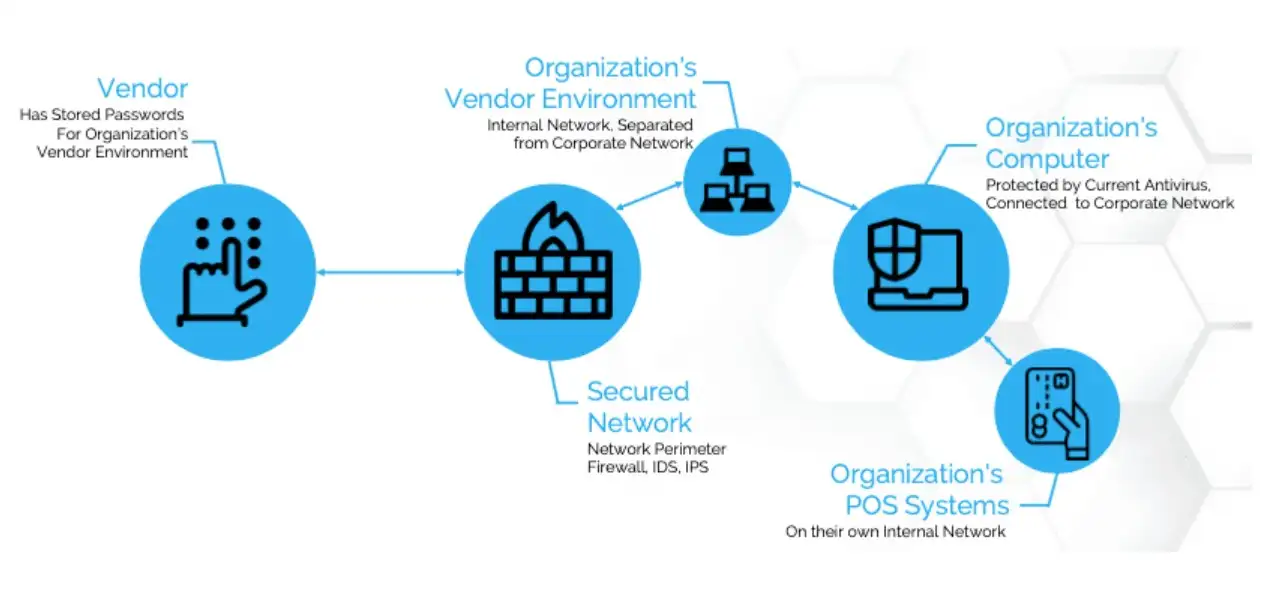
Vendors often need to be able to get into systems deeply and sometimes permanently. Every link could be a way for someone to get into the company that trusts them. That is third-party risk, vendor security, and supply chain vulnerability all talking about the same threat.
Real pain and real cost
Executives don't see breaches as a theoretical problem. In every way, they cost a lot. The costs of recovery, fines, lost customers, and long-term damage to your reputation all add up. Industry reports from the past few years have shown that the average cost of a breach has gone up a lot each year. Companies are realizing that the line item called "cyber risk" is not just a one-time cost but a recurring cost that affects hiring, product roadmaps, insurance, and stock prices.
The human cost is important, too, not just the money. Employees have a hard time wondering how safe their own workplace is. Customers feel like they've been wronged. Boards have to deal with tough questions about how to keep an eye on things. The combination of financial and emotional pain is what makes the scene of a corporate breach so chaotic for months after the first alert.
Third-party vendor breaches and what causes them
When we talk about third-party vendor breaches, we mean times when a supplier, partner, or outside service provider is hacked, and that hack affects the larger customer. There are patterns. One is phishing vendor employees to get their login information.
Another is a remote access setup that is weak and never had multifactor authentication. A third is bad segmentation that lets an intruder move from the vendor portal to the production systems.
The SolarWinds incident is a warning about the supply chain. Attackers poisoned a software update in the vendor environment, and that bad update spread to thousands of businesses, including some of the biggest names in government and business.
The damage wasn't just that a vendor was hacked; the vendor also became the way that attacks spread across many big networks. That is a big supply chain attack.
High-profile cases teach us important things.
Stories stay with you. Target is one of the first big lessons that many security teams learned in the last ten years. Attackers got in by using credentials and access from an HVAC company. Once they got in, they moved sideways and stole a lot of card information.
That one vendor relationship set off a chain reaction that hurt millions of customers and cost the store a lot of money in fines and lost trust. It's clear what happens: big brand, small vendor, huge effect.
More recent examples show that this isn't set in stone. A clothing store said that hackers got to customer data through an outside marketing company. Small businesses that handle data or run digital campaigns are appealing because they deal with a lot of data but don't always have the same level of security as larger companies. That's the kind of hole that hackers look for.
Why audits and contracts alone aren't enough
A lot of businesses think that a vendor security questionnaire and clauses in a contract will fix the problem. No, they don't. A one-time audit is like a picture. Contracts can spell out what a vendor has to do, but they don't change how they keep their security up-to-date every day.
The truth is that risk is always changing because of things like software updates, staff turnover, changing privileges, and changing business relationships.
A better way to do things is to think of vendor security as a living program. That means always keeping an eye on things, making sure that vendors can only see certain parts of the system, and having quick detection controls that assume a breach is possible. It also means having clear plans for what to do when a third-party vendor breaches so that the response is quick and organized.
The human factor and incentives that don't line up
Vendors are busy meeting deadlines, delivering services, and lowering costs. For smaller companies, security is often just a box to check. At the same time, the company that buys services may not want to make the procurement process harder or push back the time it takes to get to market.That misalignment makes it possible for convenience to win over caution and for the weakest link to become the entry point.
To fix it, you need to make sure that the incentives are in line. Take security into account when making purchasing decisions. Give important suppliers training or tools. Share threat information when it's useful. Don't think of vendor security as an outsourced task; think of it as a shared responsibility.
Real defenses that work
If you run a business program, there are a few things you can do to lower risk in ways that matter. First, take stock. Know who each vendor is, what level of access they have, and what data they can see. Second, break things up and limit access.
Don't give a marketing vendor access to your production database if all they need is an anonymized data feed. Third, make sure that vendor accounts use multifactor authentication and modern endpoint hygiene. Fourth, ask for periodic attestation and keep an eye on high-risk providers all the time.
Rehearsals are another step that is often missed. Do tabletop exercises that test what would happen if a vendor went down or a breach happened. A team that has practiced is faster, less stressed, and more effective when the time comes.
How to talk to customers after a breach
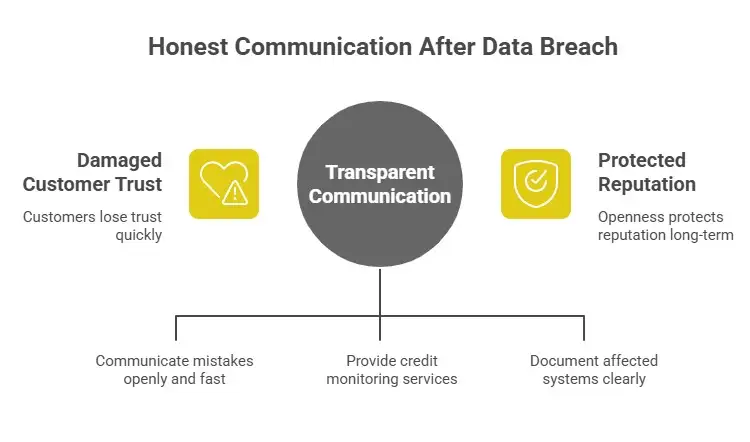
It's more important to be honest and quick than to spin. Customers would rather hear about mistakes than nothing at all. If a breach affects customer data, be very clear about what happened, what you know, and what you're doing to keep them safe. If it's appropriate, offer concrete help like credit monitoring and promise to follow up clearly. Don't use legalese or staged statements that only make people more suspicious.
Regulators and boards will also want to know more. Make a correct timeline, a list of systems that were affected, and a plan to make sure it doesn't happen again. That level of openness actually helps to protect your reputation in the long run.
The rules that are changing
Regulators are not sitting around. More and more, fines and other actions are being taken against vendors who don't do their jobs. People are watching companies that can't show they can control third-party risk. Laws about data protection say that security must be reasonable.
If a vendor causes exposure and the customer didn't pay enough attention, the customer is often responsible.
That reality in the rules is making businesses create better vendor management programs with clear audit trails and controls that can be measured.
I used to work for a mid-sized service that used a small payments partner to process credit cards. Their partner shut down their service one morning because they saw strange login activity. The mid-sized business worked quickly to switch to a backup processor and keep things running.
They had practiced a switchover and had a supplier risk map, so the downtime was short. That readiness turned what could have been a public relations nightmare into a small footnote.
The lesson is clear. You cannot prevent every third-party vendor breach, but you can plan for them. What makes recoveries different from disasters is being ready, not panicking.
Creating a culture that doesn't allow breaches
Culture is important. If procurement, legal, and engineering all make vendor security a top priority, defenses get stronger. Leaders should give teams rewards for taking steps to lower risks. Celebrate small victories, like a vendor segmentation project that went well. Don't think of security as an afterthought; make it a part of the product development story.
This change in culture is slow, but it adds up. Over time, it makes it harder for hackers to find that easy way in.
Final thoughts and what to do tomorrow
Third-party vendor breaches are now a big part of the corporate risk landscape. They will keep happening because businesses work with a lot of different people and because attackers are better at taking advantage of people and processes that aren't working than they are at finding new bugs. In principle, the best way to move forward is simple: make a list of your partners, limit access, keep an eye on things all the time, practice your response, and make sure that vendor security is not optional.
Make a list of your top 10 vendors by data access and ask what would happen if each one were to go down or be hacked. That one exercise often reveals surprising risks. After that, choose one high-risk vendor and cut their access in half. Small steps lead to real strength.
Explore our main services:
· Deep and Dark Web Monitoring
· ISO Certification and AI Management System
· Web Application Security Testing
For more services, go to our homepage.
Share this :