Prepare for the Top 5 Malware Threats of 2025

Hoplon InfoSec
08 Jan, 2025
2024 saw a surge in high-profile cyberattacks, with major companies like Dell and TicketMaster suffering from data breaches and infrastructure compromises. As we enter 2025, this trend shows no signs of slowing down. Organizations must proactively understand their cyber adversaries to avoid potential malware attacks. Here are the Top 5 Malware Threats of 2025 that you should start preparing to defend against today.
Lumma
Lumma is prevalent malware designed to steal sensitive information. It has been openly sold on the Dark Web since 2022. This versatile threat extracts data from targeted applications, including login credentials, financial records, and personal details.
Regular updates to Lumma have significantly enhanced its capabilities. It not only logs extensive information from compromised systems, such as browsing history and cryptocurrency wallet details but can also serve as a delivery mechanism for additional malicious software. In 2024, Lumma was propagated through diverse methods, including fake CAPTCHA pages, torrents, and targeted phishing emails.
Analysis of a Lumma Attack
Proactively analysing suspicious files and URLs within a sandbox environment can help you prevent Lumma infection.
Let’s see how you can do it using ANY.RUN’s cloud-based sandbox. It delivers definitive verdicts on malware and phishing along with actionable indicators and allows real-time interaction with the threat and the system.
Take a look at this analysis of a Lumma attack.
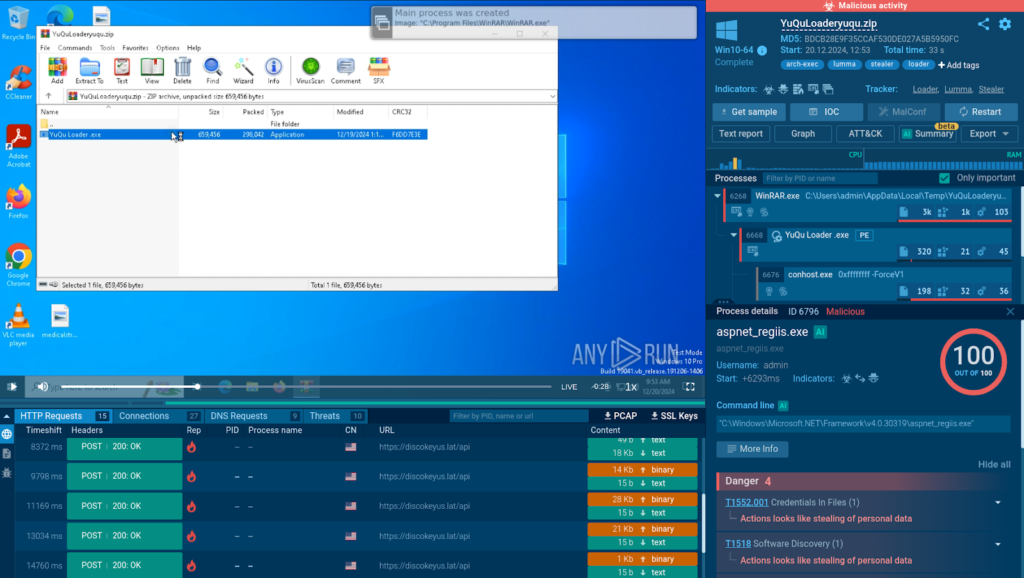
Lumma typically arrives in an archive containing an executable file. Once the .exe file is launched, a sandbox environment can automatically log all processes and network activities, providing a detailed view of Lumma’s behaviour and actions.
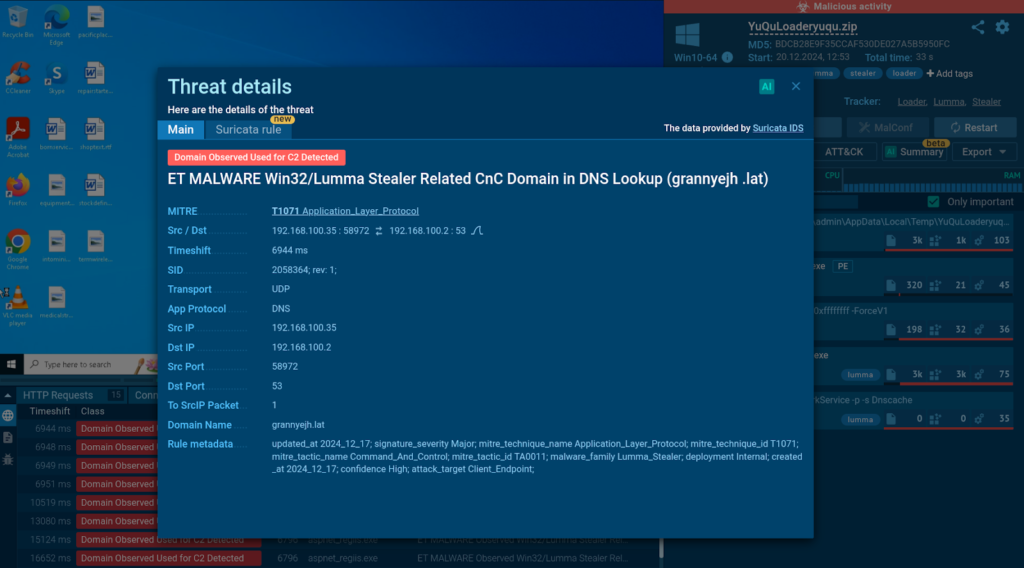
It connects to its command-and-control (C2) server.
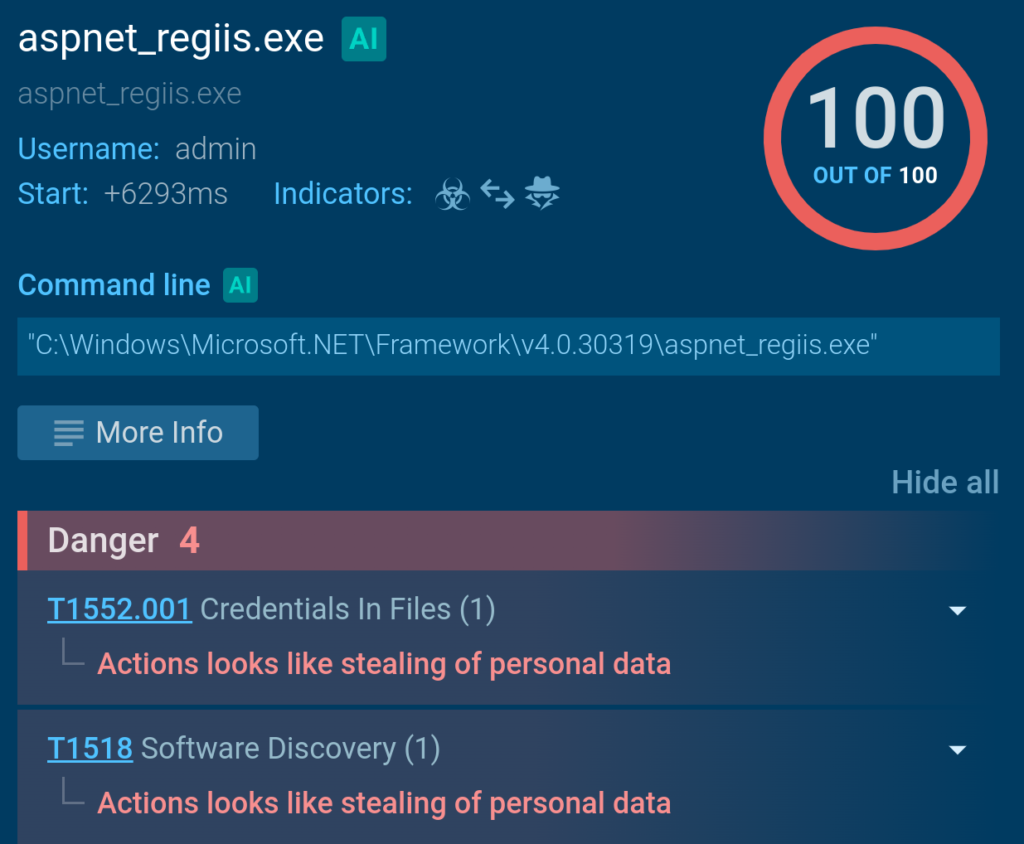
Next, it begins to collect and exfiltrate data from the machine.
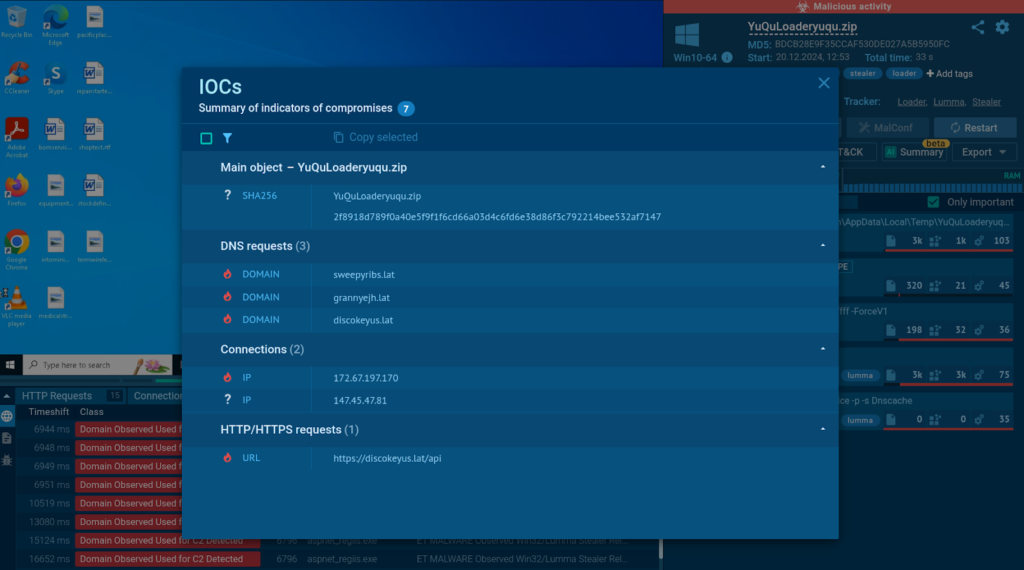
After finishing the analysis, we can export a report on this sample featuring all the important indicators of compromise (IOCs) and TTP that can be used to enrich defences against possible Lumma attacks in your organization.
XWorm
XWorm is a sophisticated malware program that grants cybercriminals remote control over infected systems. First detected in July 2022, it is capable of stealing a wide range of sensitive information, such as financial data, browsing history, saved passwords, and cryptocurrency wallet credentials.
With its advanced capabilities, XWorm enables attackers to monitor victims’ activities by logging keystrokes, capturing webcam images, recording audio input, scanning network connections, and viewing active windows. It also manipulates clipboard data, making it particularly effective at intercepting cryptocurrency wallet credentials.
In 2024, XWorm was linked to numerous large-scale cyberattacks, including those leveraging CloudFlare tunnels and legitimate digital certificates to bypass security defenses.
Analysis of a XWorm Attack
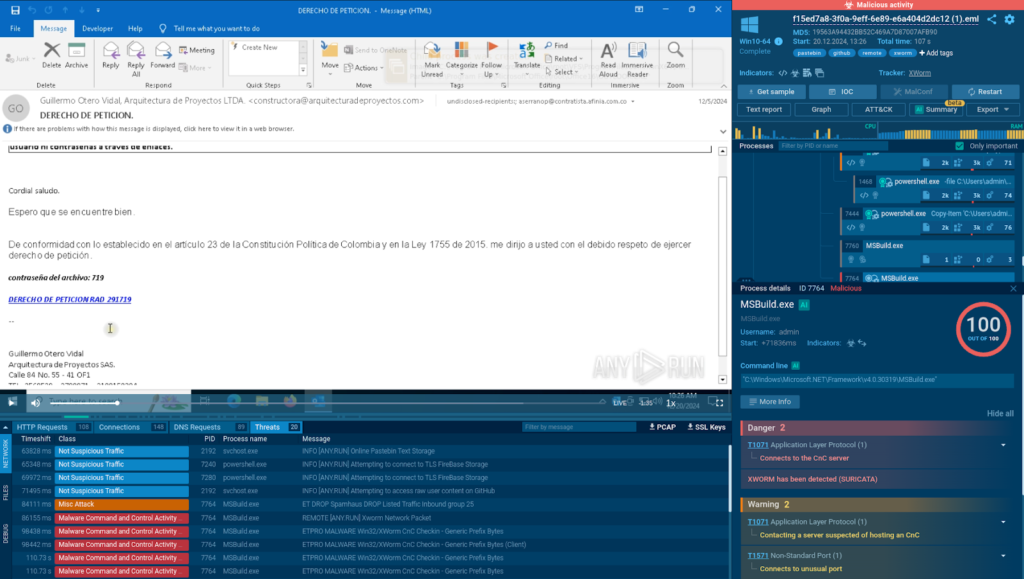
In this attack, we can see the original phishing email, which features a link to a Google drive.
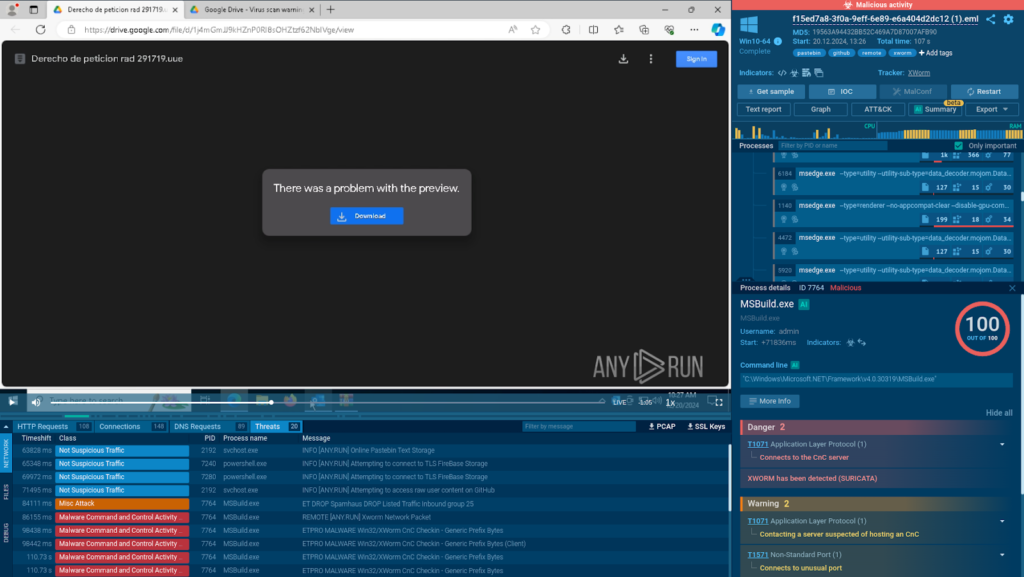
Once we follow the link, we are offered to download an archive which is protected with a password.
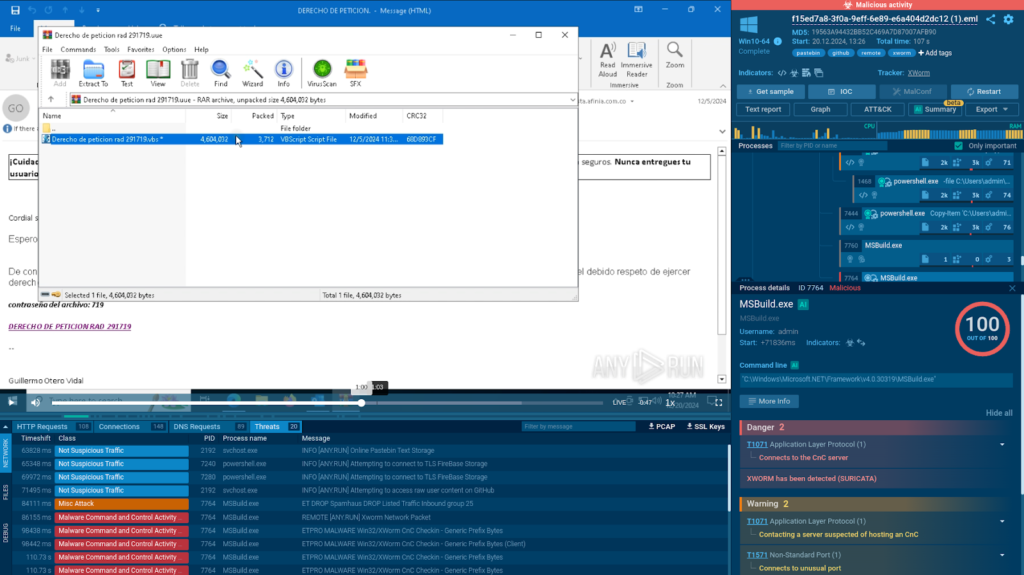
The password can be found in the email. After entering it, we can access a .vbs script inside the .zip file.
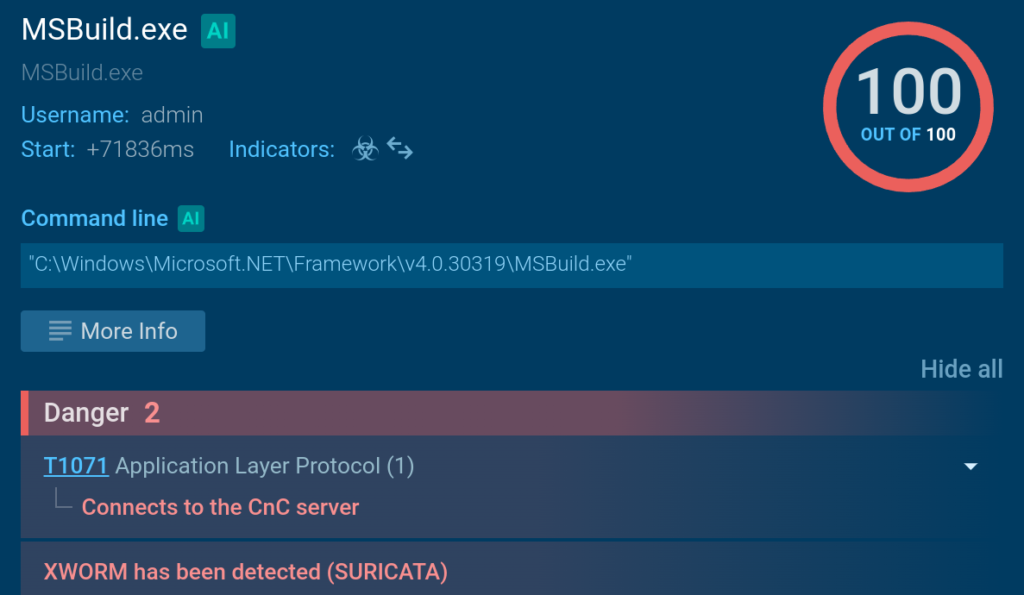
As soon as we launch the script, the sandbox instantly detects malicious activities, which eventually lead to the deployment of XWorm on the machine.
AsyncRAT
AsyncRAT is a remote access trojan (RAT) that first emerged in 2019. Initially distributed via spam emails exploiting the COVID-19 pandemic as a lure, it has since gained widespread use in a variety of cyberattacks.
Over time, AsyncRAT has evolved to include a broad spectrum of malicious capabilities. It can record screen activity, log keystrokes, install additional malware, steal files, disable security software, maintain persistence on compromised systems, and even launch Distributed Denial of Service (DDoS) attacks against targeted websites.
In 2024, AsyncRAT remained a notable cyber threat, frequently masquerading as pirated software. It was also among the first malware families to be used in advanced attacks involving AI-generated scripts, showcasing its adaptability to modern cybercrime techniques.
Analysis of an AsyncRAT Attack
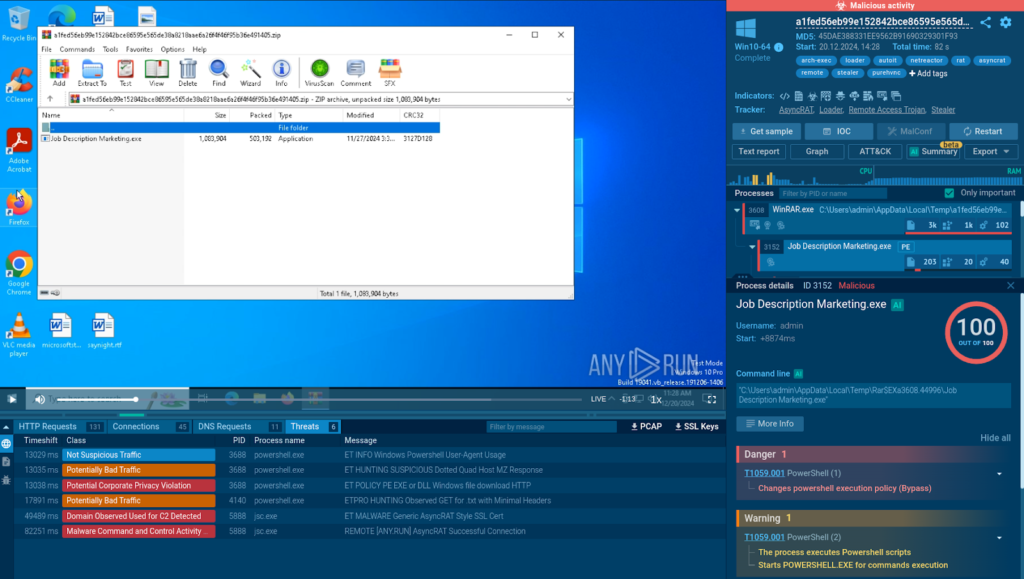
In this analysis session, we can see another archive with a malicious executable inside.
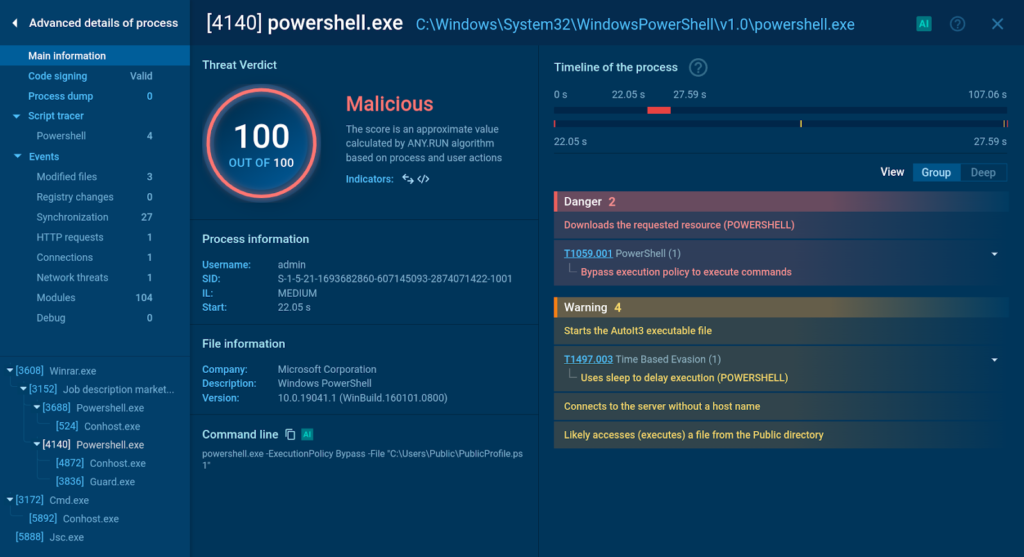
Detonating the file kicks off the execution chain of XWorm, which involves the use of PowerShell scripts to fetch additional files needed to facilitate the infection.
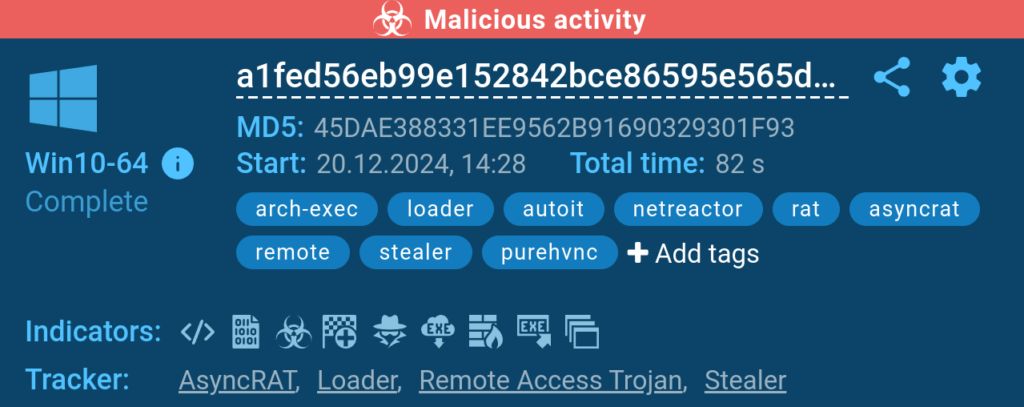
Once the analysis is finished, the sandbox displays the final verdict on the sample.
Remcos
Remcos is a malware program initially marketed by its creators as a legitimate remote access tool. Since its release in 2019, it has been employed in various cyberattacks, enabling malicious activities such as stealing sensitive information, remote system control, keylogging, and screen recording.
By 2024, Remcos continued to be a significant threat, distributed through sophisticated campaigns. These often relied on script-based techniques, starting with a VBScript that executed a PowerShell script to deploy the malware. Additionally, attackers leveraged vulnerabilities such as CVE-2017-11882, using malicious XML files to exploit targets and compromise systems.
Analysis of a Remcos Attack
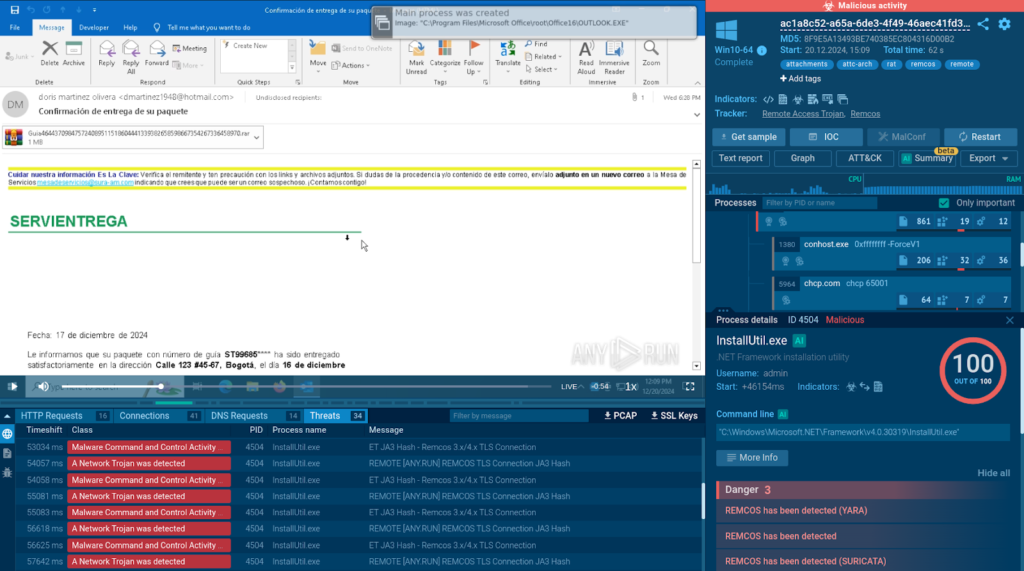
In this example, we are met with another phishing email that features a .zip attachment and a password for it.
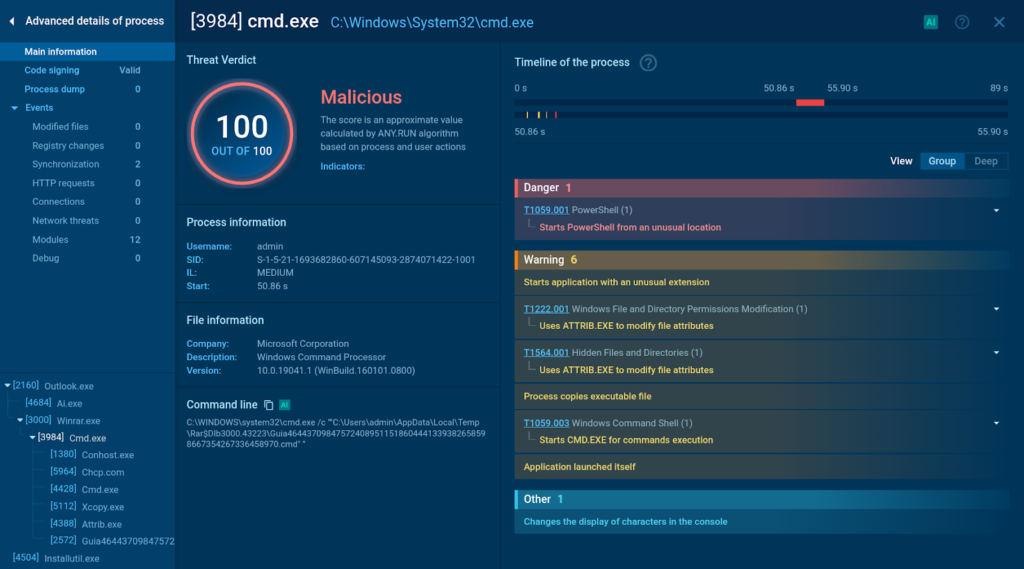
The final payload leverages Command Prompt and Windows system processes to load and execute Remcos.
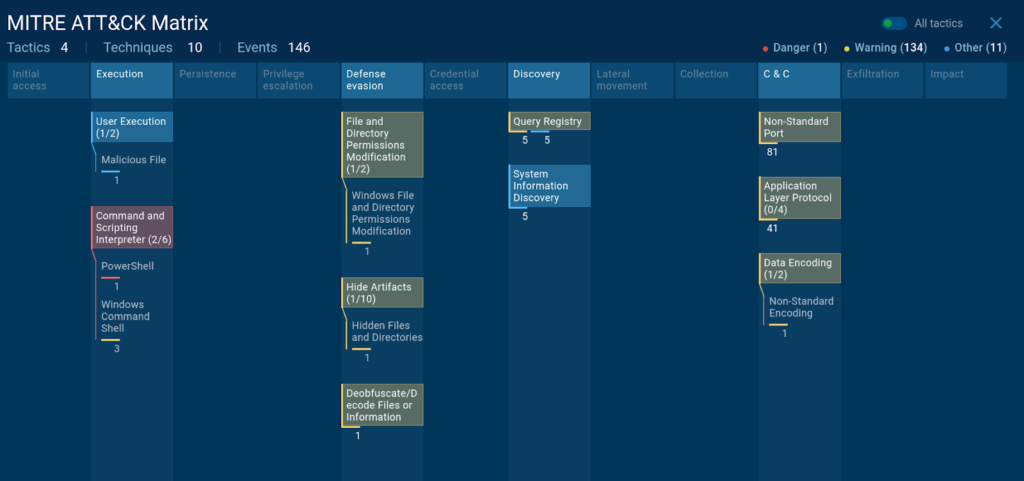
The ANY.RUN sandbox maps the entire chain of attack to the MITRE ATT&CK matrix for convenience.
LockBit
LockBit is a highly advanced ransomware primarily targeting Windows systems and is regarded as one of the most significant ransomware threats. It dominates the Ransomware-as-a-Service (RaaS) landscape, enabling a decentralized network of affiliates to execute attacks. In 2024, LockBit was linked to high-profile breaches, including the UK’s Royal Mail and India’s National Aerospace Laboratories.
Despite efforts by law enforcement, including the arrest of several developers and affiliates, the LockBit group remains active. The group has announced plans to release LockBit 4.0 in 2025, signaling its continued evolution and persistence in the global ransomware threat landscape.
Analysis of a LockBit Attack
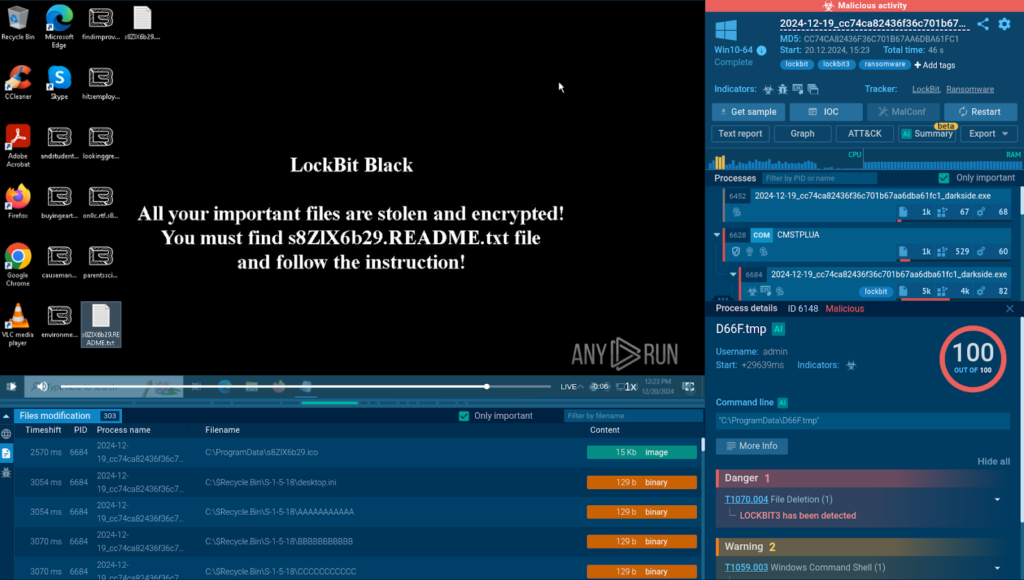
Check out this sandbox session, showing how fast LockBit infects and encrypts files on a system.
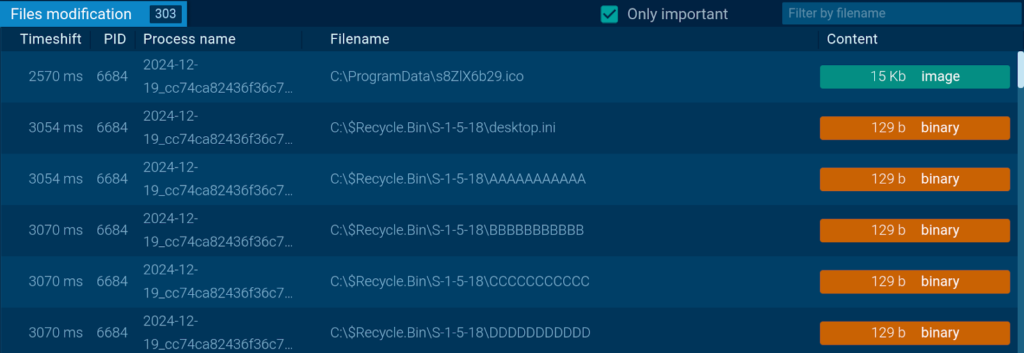
By tracking file system changes, we can see it modified 300 files in less than a minute.
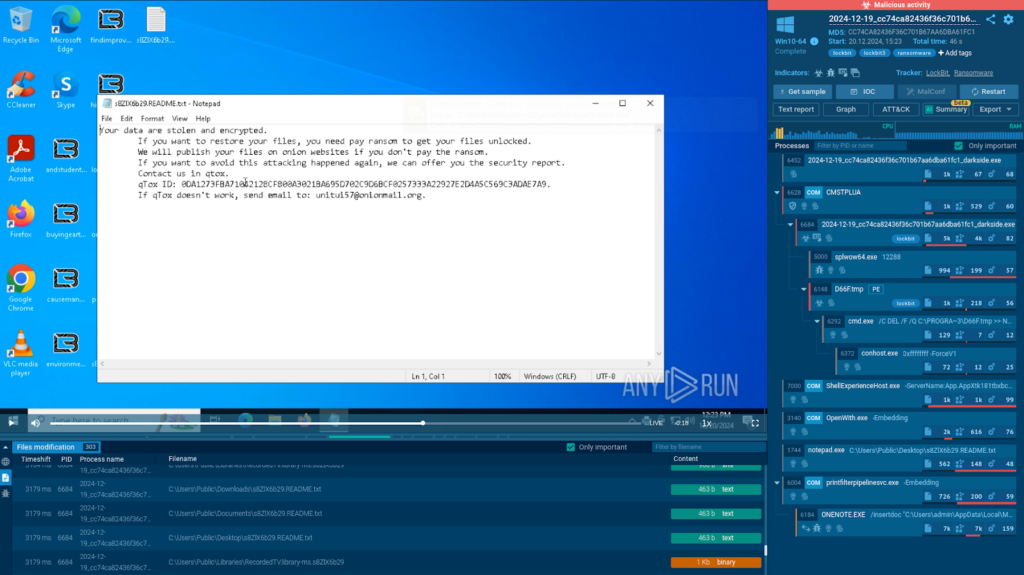
The malware also drops a ransom note, detailing the instructions for getting the data back.
Improve Your Proactive Security with ANY.RUN’s Interactive Sandbox
Proactively analyzing cyber threats is the smartest way to protect your organization. With ANY.RUN’s Interactive Sandbox, you can safely examine suspicious files and URLs in a virtual environment to easily identify malicious content.
Here’s how ANY.RUN can help your company:
- Quickly Detect Threats: Identify harmful files and links during routine checks.
- Understand Malware Behavior: Dive deeper into how malware works to uncover its tactics.
- Enhance Incident Response: Gather critical threat insights to respond to security incidents more effectively.
Stay ahead of cyber threats with smarter, faster analysis using ANY.RUN.
Share this :