TP-Link Gateway Omada: Fix 4 Serious Security Flaws
-20251022071907.webp&w=3840&q=75)
Hoplon InfoSec
22 Oct, 2025
When network teams opened their dashboards this week, they found a message they could not ignore. A widely deployed family of edge devices had received a serious security advisory, and for many administrators it felt like one of those wake-up calls: check your firmware now, and assume compromise is possible until proven otherwise.
The devices at the center of the alert are the Omada gateway family from TP-Link, and the fixes address a cluster of command injection and privilege problems that can lead to remote code execution. If you run a TP-Link Gateway Omada device in a business or home environment, this is one of those incidents worth immediate attention.
This story is not hypothetical. TP-Link posted an official bulletin showing that two of the problems allow arbitrary operating system commands to run on affected units. One of those two can be triggered by an unauthenticated remote attacker, and the vendor assigned it a critical score.
The public reporting, combined with coverage by security outlets, paints a clear picture: unpatched devices could be leveraged by attackers to move inside networks, steal credentials, or install persistent access. If you manage a TP-Link Omada gateway in your environment, patching should move ahead of lower-priority work.
The problem and its impact.
The Four Discovered Vulnerabilities:
TP-Link disclosed four vulnerabilities in Omada gateway firmware, tracked as CVE-2025-6541, CVE-2025-6542, CVE-2025-7850, and CVE-2025-7851. Two of them are classic OS command injection flaws.
One, CVE-2025-6542, can be chained without authentication, meaning an attacker on the network edge can shoot a carefully crafted request at the device and cause it to run shell commands. The other injection issues require either web portal login or administrator credentials, but any vulnerability that allows command execution is dangerous because it can give an attacker full control over the device.
To put that into context, imagine an attacker who can make the gateway execute commands. They could change routing rules, export VPN credentials, capture traffic, or drop a backdoor that survives reboots. Those outcomes are not abstract. Real-world incidents have shown how attackers use a foothold on networking hardware to pivot into sensitive servers and avoid detection.
For organizations that use a TP-Link Omada gateway at their perimeter, the difference between patched and unpatched can be the difference between an incident and a breach.
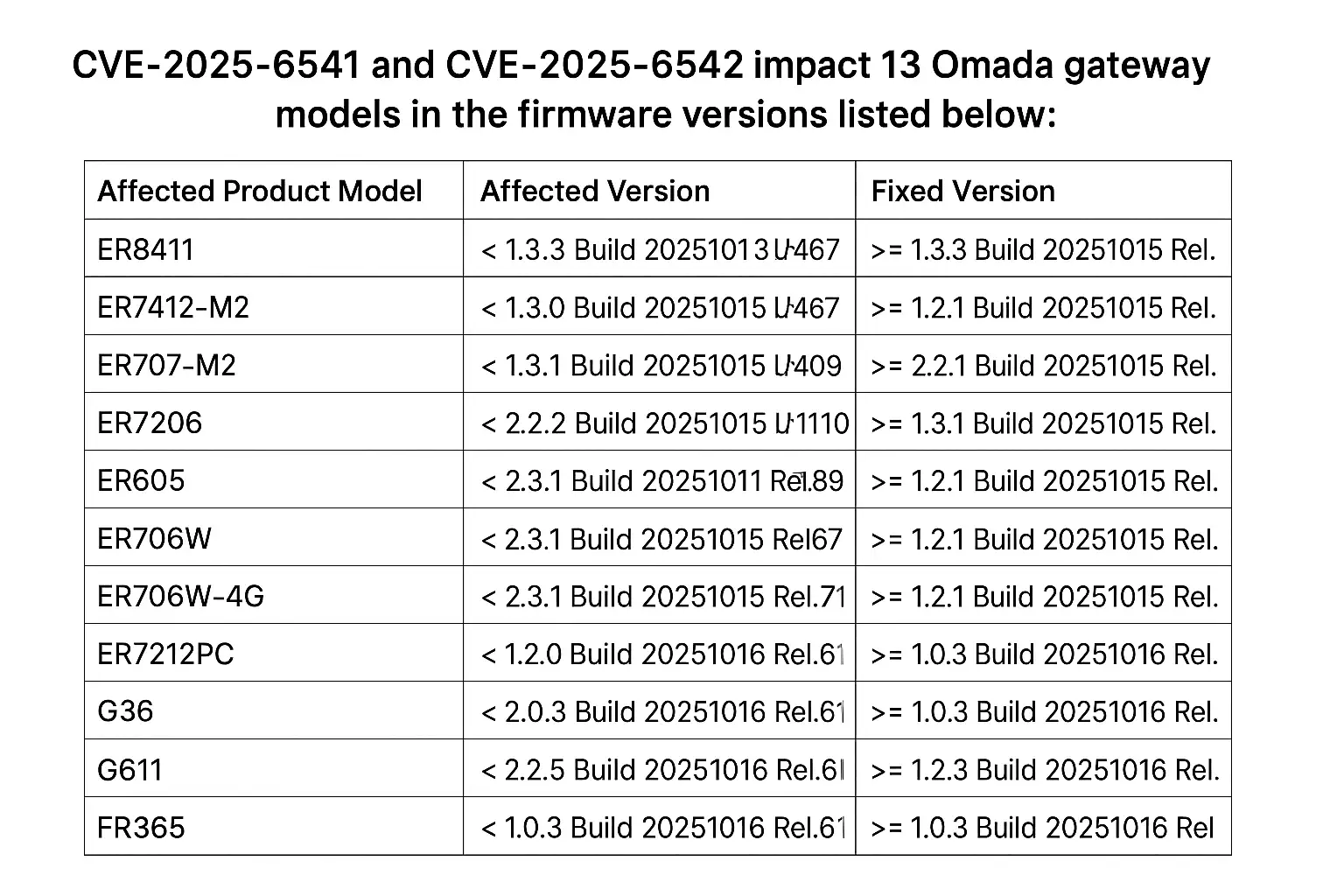
Which devices need updates?
TP-Link’s advisory lists thirteen Omada gateway models and the exact firmware builds that contain fixes. The affected product list includes models such as ER8411, ER7412-M2, ER707-M2, ER7206, ER605, ER706W, and several FR and G series models.
If your device is running a build older than the fixed build referenced for your model, it is considered vulnerable. For many teams the first practical step is to inventory every TP-Link Omada gateway, confirm the installed build, and schedule upgrades in order of exposure.
In my experience working with small networks, the inventory step is often the blocker. Most shops do not have a single source of truth for device firmware versions. A quick command or login to each management console will usually reveal the version string.
If you find a TP-Link Gateway Omada device on a branch office connection or in a data closet that has not been touched in months, assume it needs this update. Treat the device like any other critical host: document, patch, and validate.
Attack Paths
Command injection allows attackers to supply input that the system concatenates into an OS command. If input is not safely sanitized, the kernel receives an unexpected instruction and executes it. With those primitives, attackers can do things that look benign on the surface, such as reading a configuration file, but which lead to credential theft and lateral movement.
For a TP-Link Omada gateway, that could mean reading the device’s VPN configuration to harvest keys, modifying DNS responses to redirect traffic, or installing a reverse shell for long-term access.
Security researchers who catalog vulnerabilities like these emphasize two practical risks: first, an unauthenticated RCE is ideal for automated scanning and mass exploitation; second, authenticated command injection is dangerous because stolen admin credentials are surprisingly common.
Attackers often reuse passwords across services, so once they have an admin password, they can weaponize the portal. That is why even the versions that require login are regarded as high risk in real deployments.
Quick Fixes
TP-Link has published firmware updates that address the four flaws and urged customers to apply them immediately. The vendor also recommended verifying configurations after upgrading, changing administrative passwords, limiting web management exposure to trusted networks, and monitoring logs for suspicious activity. These are sensible steps, but let us unpack them into a pragmatic checklist you can follow right now.
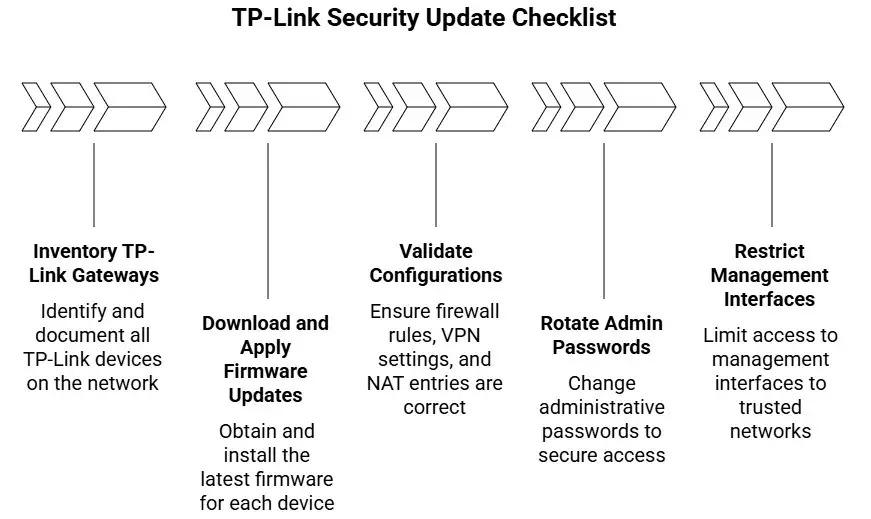
Short-term actions you can perform today:
· Inventory every TP-Link Omada gateway on your network and note firmware versions.
· Download and apply the fixed firmware for each model. Back up device configs before you upgrade.
· After the upgrade, validate that firewall rules, VPN settings, and NAT entries remain correct.
· Rotate admin passwords and remove any default or shared credentials.
· Restrict management interfaces to internal networks or a management VPN only.
· Turn on logging and set up alerts for suspicious logins or configuration changes.
If you do these steps, you dramatically reduce the attack surface. One pragmatic note: schedule upgrades during maintenance windows, and if you have remote sites, test the firmware on a single unit before mass rollout to avoid unexpected compatibility issues.
Keeping Devices Safe
This advisory is a reminder that network appliances need the same lifecycle attention as servers. Firmware rarely updates itself without administrative action, and many teams underinvest in patch automation for networking gear.
Over time, that creates a patch backlog and a collection of forgotten devices that attackers can exploit. For anyone operating a TP-Link Omada gateway, consider adding these longer-term controls: centralized inventory and patch management, periodic configuration audits, multi-factor authentication for management interfaces, and network segmentation so that a compromised gateway cannot trivially reach critical assets.
In several engagements I have seen teams implement an internal firmware policy that mandates monthly checks and a defined response time for critical CVEs. Pairing that policy with a small internal dashboard that tracks model numbers and firmware builds turns a reactive team into a proactive one. That approach works well for both small MSPs and in-house IT teams supporting distributed offices.
Mitigation Steps
Not every site can be patched in an hour. If you cannot apply firmware immediately, there are compensating controls you can use to reduce exposure. Block access to the device web interface from the internet, place the device management IP behind a jump host or bastion, and apply strict firewall rules to allow management traffic only from known admin addresses.
Review VPN access and consider temporarily removing any external admin accounts until you can patch. These measures will not fix the underlying bug, but they raise the effort required for exploitation and buy time.
Another temporary measure is increased monitoring. Send logs to a central SIEM, enable alerts for failed login attempts, and look for odd process starts on the gateway if the firmware supports it. In environments without centralized monitoring, ask remote site contacts to report any sudden reboots, strange DNS behavior, or unknown administrative accounts. Those symptoms can be early signs of exploitation.
Case Studies
Think of the gateway like the front door to your house. If the lock has a flaw that allows a stranger to slip a tool through the mail slot and unlock the door without a key, the entire house becomes vulnerable. That is what a remote unauthenticated command injection resembles in networking terms. In other cases the attacker needs to know a PIN code or find a key under the doormat, which mirrors the vulnerabilities requiring admin access. Either way, the appliance is an entry point.
I remember a small firm where an outdated router was used to jump into a file server. The company had not patched the networking device because it was “out of sight.” Once the attacker had the gateway, lateral movement was swift. The lesson is that security is holistic: protecting endpoints and servers while neglecting network infrastructure invites compromise. If you operate a TP-Link Omada gateway, treat it like a server that can run code and therefore requires equivalent care.
Takeaway
This TP-Link advisory should not be read as a reason to panic but as a call to act. The vendor has released patches, and the steps to reduce risk are straightforward: inventory, patch, validate, and monitor. For teams that have tight change windows, prioritize public-facing gateways and sites that provide VPN services to remote employees.
For everyone else, schedule the updates as soon as possible and confirm the post-upgrade state. If you own or manage a TP-Link gateway Omada device, now is the right time to treat this like an incident and follow through until you are certain your estate is no longer vulnerable.
Hoplon Infosec offers penetration testing to find vulnerabilities in network devices like TP-Link Omada gateways. They simulate attacks to help you patch weaknesses and secure your network before real attackers exploit them.
Follow us on X (Twitter) and LinkedIn for more cybersecurity news and updates. Stay connected on YouTube, Facebook, and Instagram as well. At Hoplon Infosec, we’re committed to securing your digital world.
Share this :