Vietnam Credit Information Center Cyberattack: Inside the Breach and What Comes Next

Hoplon InfoSec
12 Sep, 2025
Vietnam Credit Information Center Cyberattack
It was like a cold wave of news. In early September, national cybersecurity teams noticed strange activity on the central credit database, which led to the Vietnam Credit Information Center cyberattack being reported. That first alert set off a series of checks at banks and government agencies, and researchers quickly started looking for signs of data on underground forums.
This article tells the story in simple words. I will talk about what investigators have said so far, what independent trackers are saying, why this is important for regular people, and what both institutions and people can do next that makes sense. Don’t just give headlines; give clear examples, realistic scenarios, and useful advice.
Summary for executives
It’s easy to remember the short version. Officials said there was a cybersecurity problem at the national credit database and warned that personal information may have been stolen. Agencies are trying to figure out how bad the damage is and how to stop it from getting worse. Independent trackers and dark web monitors have said that there are large datasets for sale, but those numbers are still being checked.
It’s also clear why this is important. Millions of people have their financial fingerprints stored in a national credit database. If those fingerprints get out, hackers can steal people’s identities, open fake credit accounts, and run convincing social engineering attacks on both people and businesses.
Timeline of finding out and warning the public
Vietnam’s cybersecurity emergency team first noticed problems on September 10, and public warnings came out in the days that followed. The credit center quickly went into incident response mode, and government and banking partners were told right away. That quick notice is a good thing.
Some journalists and independent monitors then started to flag listings on underground marketplaces that said they had credit records from all over the country. Investigators looked more closely at those listings because marketplace posts sometimes have real samples that can be checked. Still, it takes time to confirm things, so intelligence teams are careful to treat early marketplace claims as leads rather than facts.
What happened: a simple explanation
The Vietnam Credit Information Center is primarily It looks like the cyberattack involved getting into a central database without permission that collects credit information for people and businesses. That database helps with lending decisions, risk scoring, and other financial services all over the country. When someone gets into that system, they can see more than just usernames and emails. They might also be able to see detailed, structured financial profiles.
Imagine that the system is like a national record of financial trust. If that ledger is open to the public, hackers can steal the information and use it for targeted fraud, forgeries, and long-term identity theft. That makes problems at credit bureaus very sensitive, both politically and financially.
Who might be responsible for the event?
Notices that are available to the public suggest that investigators are looking into a group that steals data in an organized way and has a history of big breaches. Several news sources have suggested that a known black-hat group could be behind the leak, based on the way it happened and the listings seen on criminal forums. Attributing blame is hard at first, and investigators usually wait for forensic evidence before doing so.
From the point of view of the defense, the name of the group doesn’t matter as much as the actor’s ability and reason for doing what they did. Some of these groups collect financial information to sell right away. Some people want to keep the data so they can use it for targeted extortion or for a long time. Knowing why someone did something helps you figure out how to respond.
Scope and scale: how big could this get?
There are both good and bad possibilities. Optimistic investigators warn that the system is still working and that these kinds of breaches don’t always involve a full dump; sometimes they only involve partial exfiltration. Pessimistic trackers point to marketplace posts that say there are a lot of records for sale. If this is true, it would have a big effect on both consumers and institutions. Right now, the exact number has not been confirmed in public.
Authorities need to find a balance between being open and keeping people calm. To get an exact number, you need to compare the stolen samples to system records, which takes time and care.
What kinds of records seem to be out in the open?
Public and investigative reports talk about the usual sensitive fields that are in credit files, such as personal identifiers, credit histories, risk analyses, and sometimes even government ID numbers and income records. Some monitors say that encrypted payment information may be there, but it won’t be useful right away without more work. Fraudsters can use all of these kinds of records as weapons.
Not all leaks are equally harmful, so it’s important to keep that in mind. A list of hashed emails is not as dangerous right away as a file that has raw identity numbers and credit lines next to each other. The devil is in the details, and that’s what the investigators are trying to check.
How attackers probably got in: common methods and signs
When big centralized databases are hacked, investigators often find one or more of the following: stolen login information, open admin interfaces, cloud storage that wasn’t set up correctly, or social engineering that tricked employees. The way the indicators are arranged in public reports suggests that this is a targeted data exfiltration and not a noisy ransomware attack. That pattern suggests that the extraction was done in a stealthy way, not by shutting down the service.
Defenders should assume that more than one attack vector was tried based on what they know. The main ways to protect against these kinds of attacks are network segmentation, strict management of admin keys, and strong logging.
Authorities took immediate steps to contain the problem.
The national cybersecurity agency worked with the central bank and the credit center to limit access, check logs, and end any active sessions that seemed suspicious. Those are the first steps that are usually taken in an incident response plan. At the same time, banks were told to keep a closer eye on strange account activity.
Good containment practices give you more time. They don’t erase stolen data, but they can slow down attackers and make it harder for them to use the data again.
Effect on banks, lenders, and the credit market
Lenders have problems right away when a credit database is hacked. Risk models may need to be changed, fraud detection thresholds may catch more false positives, and banks may have to pay more to fix problems. If customers don’t trust how you handle their data, the market can change. Experts have said that these kinds of events can make cybersecurity more expensive for the whole industry.
That doesn’t mean the banking system is going to fail. Banks need to act quickly to keep customers safe, spend money on monitoring, and make sure customers understand what is going on so they don’t panic.
Consumers are at risk of credit fraud and identity theft.
For each customer, the threats in the real world are clear and scary. People who have credit records can make fake loan applications, open accounts, or pretend to be victims in social engineering calls. If you don’t stop this kind of fraud, it will cost a lot of money and take a long time to fix. After these notices, people should expect to take on more risk. There are useful steps that can be taken right away.
Dark web listings, claims of verification and sale
Several trackers and dark web monitors reported listings that said they were selling credit records for the whole country. These posts are often how hackers make money, but not all of them are real. Investigators check samples against official records to make sure they are correct. If the samples match, that makes us a lot more sure. In this case, a number of independent monitors reported sample posts, which led to the wider alerts.
If you see a post online that looks suspicious and has your email or ID in it, don’t panic; instead, take action.
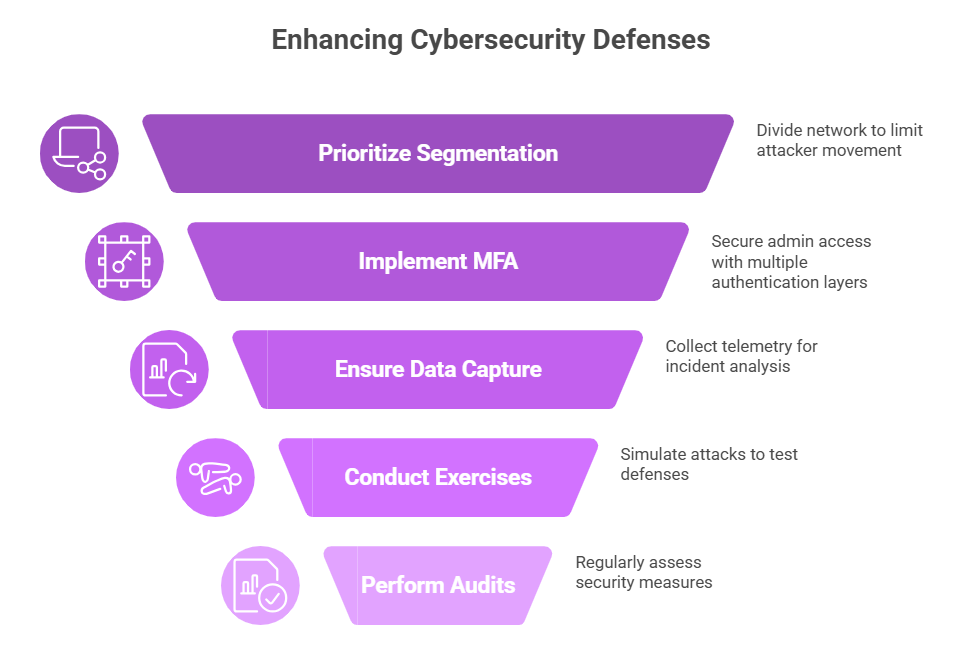
Technical lessons for security teams and CISOs
The checklist is something defenders know well, but it’s also very important. Make segmentation a priority, use multifactor authentication for admin access, make sure full packet capture or endpoint telemetry is available during the incident window, and run focused exercises that mimic data exfiltration. These steps make it harder for the attacker to move around and speed up the work of forensic experts. It’s no longer up to you whether or not to do regular privacy audits and external penetration tests.
Effects on policy, regulations, and national security
When a national credit repository is hacked, it raises questions about how to keep an eye on it, how to limit the amount of data it collects, and where to host it. Lawmakers will want to know if the way data is collected is fair, and regulators will probably want data custodians to follow stricter security rules. That debate is good, and over time it usually leads to stronger protections.
Things that people and small businesses can do
If you are a customer in the affected market, start with the simple, effective things. Sign up for any free credit monitoring your bank offers, turn on two-factor authentication for all of your accounts, check your statements every day, and be wary of calls or emails that you didn’t ask for. If your identity number or bank account number is in a verified sample, call your bank right away and think about putting a temporary freeze on your credit.
For small businesses, make sure vendors and the supply chain can get to your data, change API keys if necessary, and keep a close eye on any strange transactions. Quick detection at the merchant level stops a lot of other frauds from happening.
Takeaway that you can use
The Vietnam Credit Information Center cyberattack shows that centralized trust systems are very valuable targets. The next part of the story will include forensic evidence, action taken by the credit center and banks, and a longer discussion about how to keep large financial datasets safe. For now, the best things to do right away are to be more careful and to have stronger controls in place at institutions.
The Vietnam Credit Information Center Cyberattack highlights the risk of stolen financial data appearing on underground forums. Hoplon Infosec’s Deep and Dark Web Monitoring tracks these threats in real time, alerts organizations to exposed data, and provides actionable insights to prevent fraud and identity theft.
Follow us on X (Twitter) and LinkedIn for more cybersecurity news and updates. Stay connected on YouTube, Facebook, and Instagram as well. At Hoplon Infosec, we’re committed to securing your digital world.
Share this :