VoidLink Malware Targets Linux Cloud Systems With Self-Deletion

Hoplon InfoSec
13 Jan, 2026
It's important to be clear in the first hundred words. VoidLink malware shows that attackers are changing the way they think about Linux targets. This malware doesn't see Linux servers as static machines; instead, it sees them as living cloud platforms. It acts more like a flexible framework than a single bad file.
People are calling this new advanced Linux VoidLink malware "cloud-native Linux malware" because it knows how to work with containers, orchestration layers, and dynamic infrastructure. That alone puts it ahead of a lot of older Linux threats that used simple persistence or loud attacks.
The fact that VoidLink can delete itself is what makes it stand out. It can erase a lot of its footprint once it reaches its goals or when it sees that it is being analyzed. That makes it harder to respond to incidents and leaves defenders with more questions than answers.
How We Found VoidLink Malware and What We Know So Far
Researchers first saw VoidLink malware while looking into strange behavior in cloud workloads. These were not regular desktops that had been hacked. Most of the systems that were affected were Linux servers that ran containerized apps.
Reports say that the malware did not make itself known by crashing systems or causing obvious damage. It didn't stand out. The logs looked normal. As expected, the containers restarted. Credentials quietly went away. That pattern set off alarms for incident response teams.
Being honest about not knowing is important. As of this writing, no one has publicly given VoidLink malware a specific CVE identifier. It is not just one exploit; it is a framework for malware. That means it usually depends on weak passwords, services that are open to the public, or holes in the supply chain, instead of just one security hole.
Understanding VoidLink as a Linux Malware Framework
A lot of people still think of malware as just one file that does something bad. VoidLink malware messes with that way of thinking. Researchers say it is a Linux malware framework that is based on modular plugins.
This design lets operators load only the parts they need. In one setting, the main concern may be malware that steals credentials. In another, the main goal might be lateral movement or staying in the same place.
That flexibility is important in the cloud because each workload is different. A static payload would break down quickly. Attackers can change their plans on the fly with a modular approach, which is why VoidLink is often called adaptive stealth malware.

Why Cloud-Native Linux Malware Is Becoming More Common
There is cloud-native Linux malware because cloud infrastructure changed the game. Containers don't last long. IP addresses change. Logs are spread out across services. That level of complexity makes things hard to see.
VoidLink malware uses those blind spots to its advantage. It knows about Docker metadata. It knows how to use Kubernetes service accounts. It can hide in what looks like normal container behavior.
This doesn't mean that cloud platforms are always unsafe. It means that hackers are figuring out how defenders work and making malware that fits in with the environment.
How VoidLink Gets a Foothold in Technical Behavior
Paths for Initial Access
According to public reports, VoidLink malware doesn't just use zero-day exploits. Instead, it often gets in through Docker APIs that are open, weak SSH credentials, or Kubernetes dashboards that aren't set up correctly.
This is how a lot of cloud breaches happen in real life. A developer keeps a test service open. A public repository gets an API token. Attackers are always scanning and waiting.
Once it gets in, VoidLink is quiet. It doesn't use all of its modules right away. That restraint is planned.
Collecting Credentials in Cloud Environments
One of the most worrying things about it is that it can steal credentials. When you use VoidLink, it looks for environment variables, mounted secrets, and configuration files that are often used in cloud workloads.
Secrets are often added to Docker containers while they are running. If permissions are too broad, service account tokens may be available in Kubernetes. VoidLink malware knows where to find things.
You can use those credentials later to move around in the cloud, get to storage buckets, message queues, or even CI pipelines.
Post-Exploitation Control and Modular Plugins
VoidLink uses a modular plugin malware architecture to add features only when they are needed. This makes it smaller and less likely to be found.
Some reported modules are all about running commands. Others take care of ways to keep things going. Linux malware usually uses things like cron jobs or modified startup scripts.
There are also signs of post-exploitation Linux malware modules that are meant to map out internal networks and cloud services. At this point, the threat becomes more planned than random.
VoidLink Overview: source
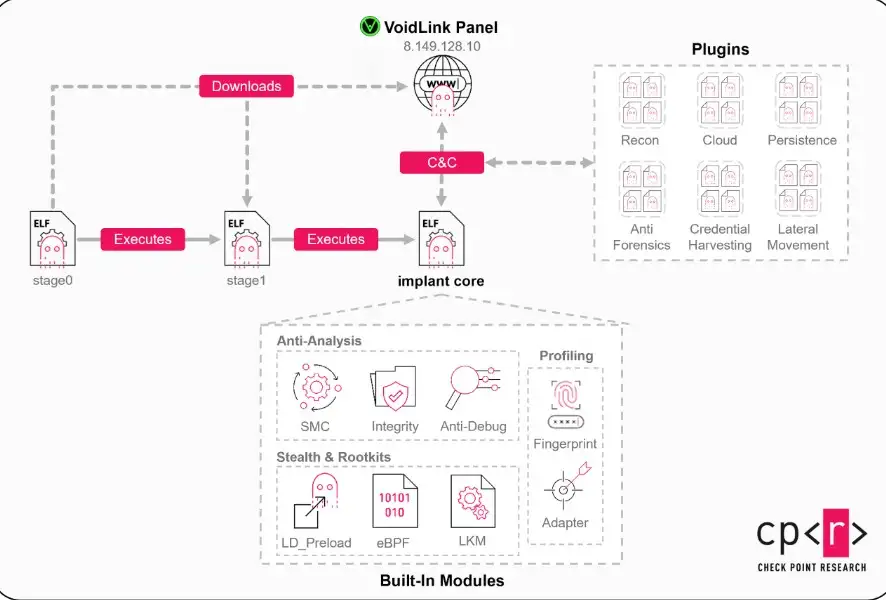
Advanced Techniques: LD_PRELOAD, eBPF, and Kernel Interaction LD_PRELOAD Malware
Injection LD_PRELOAD malware injection isn't new, but VoidLink uses it carefully. It can intercept system calls without changing binaries directly by taking over shared libraries.
This lets VoidLink malware hide processes, hide network connections, or change the output of commands. To an administrator, everything seems fine.
eBPF malware Linux features
Some studies talk about trying out eBPF malware Linux techniques. eBPF is a powerful and legal tool that is often used for monitoring. That also makes it good for stealth.
There is still some doubt here. Researchers don't all agree on how much VoidLink uses eBPF. What is certain is that hackers are looking into it, and VoidLink seems to be in line with that trend.
Risks of Loadable Kernel Module Malware
VoidLink has not yet released a confirmed kernel rootkit to the public, but the way the framework is set up suggests that it could support loadable kernel module malware. If used, this would give you deep control over the system.
Defenders should see this as a warning sign and not a confirmed feature.
Linux Self-Deletion Malware and Anti-Forensic Design
One of the most talked-about things about it is that it is called self-deletion malwarefor Linux. VoidLink looks for signs of debugging, analysis, or sandboxing.
When it is triggered, it deletes temporary files, clears memory artifacts, and turns off its own parts. This makes it hard to put the pieces back together in a forensic way.
In incident response, missing evidence is often more dangerous than clear evidence. Teams might not realize how big the compromise is.
Targeted Platforms: Docker, Kubernetes, and Cloud Providers
VoidLink malware that targets Docker and Kubernetes environments has caused worry in many fields. A lot of modern businesses depend on these platforms, even though they don't have a lot of security knowledge.
Container escape malware attempts are one of the Linux scenarios that pose a threat to cloud containers. There is no known universal escape method, but misconfigurations often make isolation weaker than expected.
Public reports talk about the attack surface of cloud infrastructure on AWS, Azure, GCP, and regional providers. The malware doesn't go after just one vendor. It goes after mistakes.
Control and Command Design and Silent Communication
VoidLink uses Linux malware patterns for C2 command-and-control that mix in with regular traffic. HTTPS is a common thing. Domains can change. Payloads are protected.
Some traffic even pretends to be API calls to real services. This makes it harder to find things just by watching the network.
VoidLink can slow down activity based on system load or time of day because its adaptive stealth malware behavior lets it do so. That patience is scary but works.
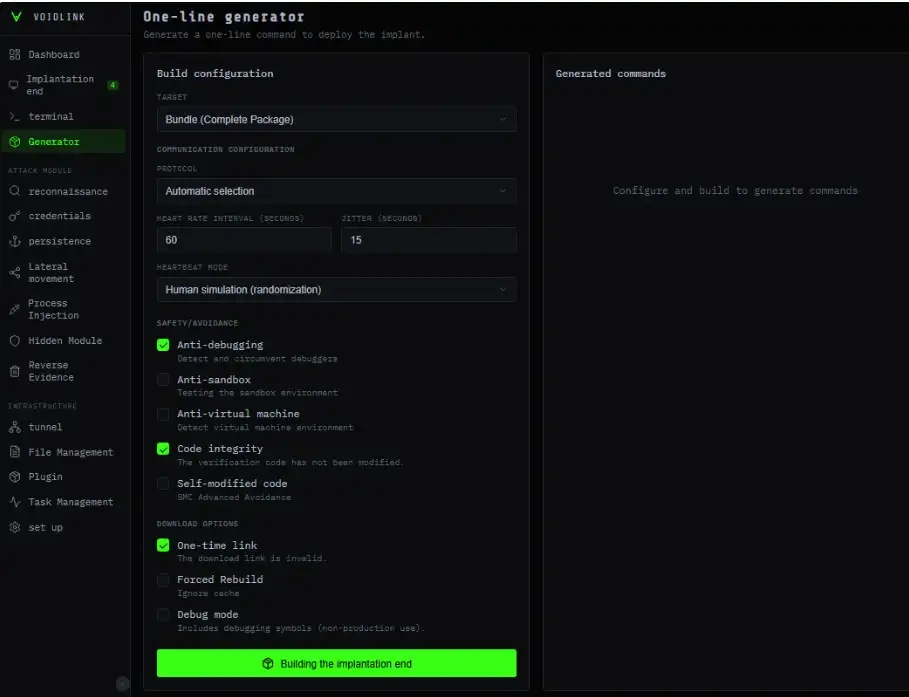
VoidLink uses a builder panel to create custom versions: source.
What it means in the real world and why businesses should care
For most victims, the first thing that happens is not ransomware or visible damage. It is quiet access to data.
Stealing credentials can leave the cloud open to attack for a long time. Attackers could come back weeks later with real access. That wait breaks the connection in your mind between cause and effect.
SaaS providers, fintech platforms, DevOps teams, and managed service providers are some of the industries that are at risk. Linux and containers are the most common things in any environment that could be a target.
Challenges in detection and useful signs
How to Find VoidLink Malware in Linux Containers
To find VoidLink malware in Linux containers, you need to watch how they act. Just checking the integrity of the file isn't enough.
If you notice strange access to service account tokens, unexpected use of LD_PRELOAD, or API calls that don't make sense, you should be suspicious.
Runtime security tools that know what a container is are better than regular antivirus software.
Gaps in Logs and Telemetry
Many breaches keep happening because logs aren't complete. When you restart a container, it deletes local logs. Centralized logging is helpful, but it needs to be set up correctly.
VoidLink malware does well in this area. It hides in the places that defenders don't think of.
How to defend yourself and how to reduce risk
Making Cloud Environments Stronger
Start with the basics. Limit access to the Docker API. Change your credentials. In Kubernetes RBAC, use the least privilege.
These steps may sound boring, but they stop a lot of real attacks.
Watching and responding
Use tools that protect your workload by watching behavior instead of signatures. Alert on strange interactions between the library and the kernel.
If you think your credentials have been compromised, treat themas ife they are burned. Change everything around.

Questions that are asked a lot
What is the VoidLink virus?
VoidLink malware is a new type of cloud-native Linux malware framework that targets containerized environments, focuses on stealing credentials, and uses stealth techniques like self-deletion.
Can VoidLink malware get into Linux containers?
Yes. VoidLink malware is targeting Docker and Kubernetes environments by taking advantage of misconfigurations and credentials that are out in the open, according to public analysis.
How does VoidLink stay hidden?
It uses modular plugins, adaptive behavior, LD_PRELOAD injection, and sometimes experimental techniques at the kernel level. It also gets rid of itself when it sees that it is being analyzed.
What can businesses do to keep Linux servers safe from cloud malware?
The best defenses are still strong access controls, least privilege policies, runtime monitoring, and regular credential rotation.
What You Should Remember
VoidLink malware is scary, not because it looks cool, but because it feels real. It acts like a patient intruder who knows how to use modern technology.
The most important lesson isn't about one type of malware. It's all in your head. Linux cloud security threat models need to change as the environment does.
VoidLink is handled under Cloud Security + Incident Response, with a strong focus on Linux, Docker, and Kubernetes protection.
This is what you should remember. Think that attackers know as much about your cloud as you do. Then make defenses that don't let them find a quiet place to hide.
Share this :