Volvo Data Breach Reveals Employee Risks After HR Supplier Attack

Hoplon InfoSec
25 Sep, 2025
Volvo Data Breach
A late summer cyber incident quietly became a messy autumn headache for many workers. The story reads like a modern parable about how a small vendor problem can become a big corporate embarrassment. At its heart the issue is simple and human. Payroll systems, sick leave records and HR notes are not glamorous, but when they leak they hit people where it matters most.
For employees and managers alike the reaction is the same: disbelief, irritation, and a slow, growing worry about identity theft and scams. This piece walks through what happened, why it matters, and what real people and organizations can do to recover and harden systems against the next shock.
What happened and how it was discovered
In late August a Swedish IT supplier that handles HR workflows detected unauthorized activity on its systems. The company provides software used by many public and private organizations to manage absence, rehabilitation and employee notes. That discovery triggered investigations, and within days the scale of the intrusion became clear.
Those intrusions were the typical cruel combination of data theft and ransomware pressure. Files were exfiltrated, and copies later showed up in locations outside the vendor’s control. For customers who trusted the supplier with employee records the unpleasant truth was that their workforce data was now in the hands of people who do not have their best interests at heart.
Who Miljödata is and why this mattered
Miljödata is not a household consumer brand, but it is deeply embedded in HR workflows across many Swedish municipalities and organizations. The company’s systems are used to track sick leave, workplace incidents, rehabilitation and related HR functions. That deep integration makes the vendor valuable but also risky when an attacker gains access.
When a vendor holds records across many clients it becomes a single point of failure. This is why an attack that looks like a vendor problem is often a broad societal problem. Multiple municipalities and regional bodies reported service outages and scrambled to find manual ways to handle critical tasks while systems were offline.
What Volvo Group’s exposure looks like
Volvo Group North America learned that some of its current and former employees’ records may have been part of the harvested files. According to notices sent to employees, the affected information was tied to HR support systems hosted by the supplier, not to a direct intrusion of Volvo’s own networks.
The company has been notifying impacted individuals, and the disclosure makes a key distinction: a third party was hit, and Volvo’s own IT systems were not breached. That nuance matters to corporate counsel and incident responders, but for a person whose name and identity number are in the leaked files the difference is small and deeply personal.
What types of employee data were affected
Reports indicate the stolen records included names, contact details and government issued identity numbers in some instances. Large sets of email addresses, names and other identifiers also appeared among the material published by the attackers. For employees, the real risk is identity fraud, tax scams and targeted social engineering that uses legitimately accurate personal details.
When unique identifiers like government identity numbers or social security equivalents are published, the threshold for real harm drops dramatically. Scammers can open accounts, file fraudulent tax returns or impersonate victims. The presence of such identifiers in the exfiltrated data is why this incident moved from a municipal IT problem into a consumer protection and legal issue.
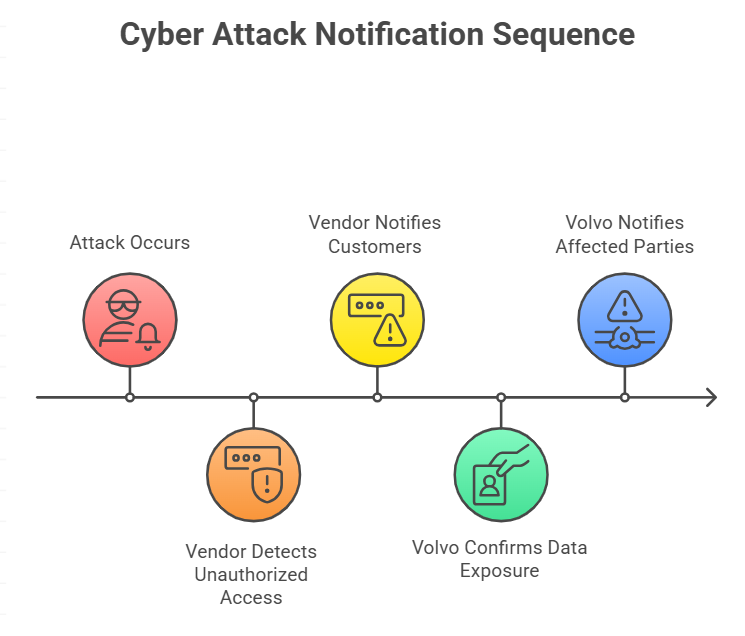
Timeline: attack, discovery, notification
Based on the vendor and customer notifications, the attack was believed to have occurred in August with detection and internal steps taken shortly after. The vendor told its customers when it identified the unauthorized access and staggered notifications were sent as investigations revealed which client data could be affected.
Volvo’s notices follow that pattern: once the vendor confirmed that its HR systems may have contained Volvo-related records the company moved to inform affected current and former workers and relevant authorities. The timing and sequence of those communications matter to regulators and to anyone tracking potential misuse of exposed data.
Why third party risk is the core lesson
This incident is a textbook example of supply chain vulnerability. Organizations often focus security budgets on their own perimeter, and rightly so, but third party software and service providers can be the weakest link. When HR platforms are deeply integrated and store long-lived personal data, they become attractive targets.
A mental image helps. Think of a group of houses sharing a single wooden bridge to the main road. You can fortify each house, add alarms and locks, but if the bridge is weak, everyone is at risk. The vendor is that bridge. Any organization that treats suppliers as purely operational partners rather than critical security assets increases its odds of being surprised.
Immediate response and containment steps
Good incident response has a few standard steps: containment, forensic analysis, notification and remediation. For affected organizations the first order of business is to isolate the flow of additional data and to determine the scope of what left the systems. For this attack that meant working with the vendor to map which client records were in affected systems and then beginning targeted employee outreach.
Containment is not only technical. It is also operational. HR teams had to pivot to manual processes for payroll or absence management in affected municipalities. Legal and communications teams had to craft plain language messages to employees that explained risk without causing panic. That choreography matters because poor messaging can make an incident far worse than the leak itself.
Regulatory and legal implications
When sensitive personal identifiers appear in stolen data, regulators often get involved. Data protection authorities in multiple jurisdictions can require breach notifications, incident reports and sometimes penalties if negligence is found. For multinational employers this is a complex dance between local law, employee rights and disclosure obligations.
From a legal perspective the fact that a vendor was the initial target does not absolve customers of scrutiny. Contracts, audits and evidence of due diligence become central in any regulatory review. For affected people the important question is whether reasonable safeguards were in place and if organizations acted quickly once they knew about the incident.
What affected people should do right now
If your information might be in the leaked set, take the basics seriously. Monitor bank and credit statements, set fraud alerts where available, and be extra cautious about emails, phone calls or texts that ask for more personal information. Scams often arrive quickly after a breach, using accurate details to trick victims.
Also, consider freezing credit if your jurisdiction supports that measure. Keep documentation of any suspicious transactions and report fraud to the appropriate authorities. Human patience is finite, but a few hours of vigilance now can prevent months of cleanup later.
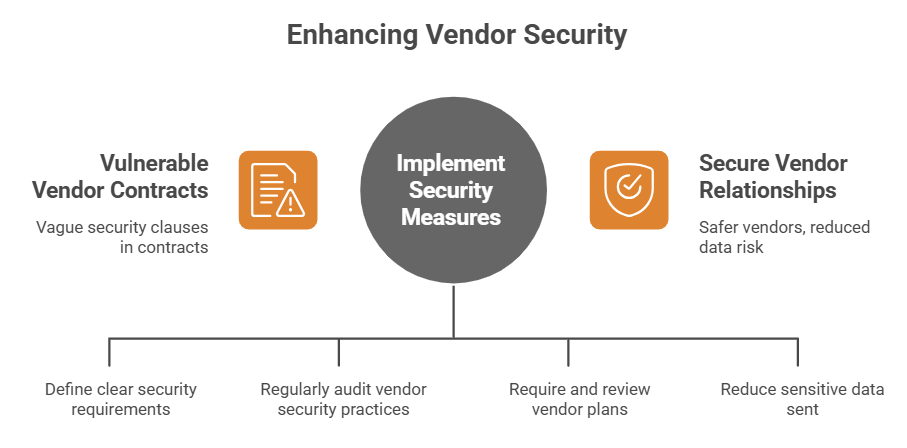
How companies can reduce vendor risk going forward
A change in procurement practice is overdue at many organizations. Security clauses in contracts should be specific, not vague. Routine audits, right to inspect and security performance metrics can shift the balance toward safer vendors. Additionally, technical measures such as encryption of stored personal identifiers and compartmentalization reduce the damage if a supplier is breached.
Security is also about empathy and process. Require vendors to show you incident response plans, run tabletop exercises together and avoid single point of failure architectures. Where possible reduce the amount of sensitive data you send to suppliers. Minimalism helps. Less stored data equals less data to worry about when something goes wrong.
The human side: stories and consequences for employees
Data breaches are often presented in corporate dashboards and legalese, but they translate into real stories. An employee whose identity number is leaked may receive suspicious messages, be denied a loan, or spend weeks correcting a fraudulent water bill. Those are not hypothetical outcomes. They are time consuming and emotionally draining.
Managers and HR teams must treat victims as people, not data points. That means offering support, being transparent about what is known, and helping with resources like credit monitoring or fraud reporting guidance. The humane response can make a huge difference in how trust is rebuilt after the dust settles.
What security teams should change in playbooks
Security teams should add more supplier-focused scenarios to their tabletop exercises. Simulate vendor compromises that affect payroll or HR systems and practice communication between security, HR, legal and communications teams. Those rehearsals make real events less chaotic.
On the technical side, include vendor logs in your threat detection feeds where feasible. If a supplier shares access paths or API keys with you, treat those credentials like your own crown jewels. Vigilant rotation of credentials and a principle of least privilege help limit blast radius when a vendor is hit.
Wider industry implications for supply chain resilience
This incident is another arrow pointing to a systemic problem. Large swaths of public administration rely on a handful of vendors. Consolidation and convenience create efficiency but also concentration risk. The industry must weigh the economic benefits of shared platforms against the risk of widespread simultaneous outages.
Policymakers and buyers should encourage diversity of providers and interoperable systems that allow a faster failover when one supplier is compromised. Resilience is not a buzzword. It is a strategic position that reduces dependency on single suppliers and helps communities maintain continuity when things go sideways.
Practical takeaways and next steps
For employees: assume you might be affected, take protective steps and keep records of suspicious activity. For organizations: audit your vendor relationships, require stronger contractual security commitments and run regular joint incident rehearsals. For leaders: remember that security is as much about relationships and governance as it is about firewalls.
Keep this in mind. A breach at a vendor is not a remote problem. It is a practical test of whether you had the right processes and the right empathy in place when people came asking for help.
Closing reflection
This episode is a reminder that modern infrastructure is deeply social. We build systems to help people, but when those systems fail the cost is borne by employees who trusted their employers to keep their information safe. Technical fixes are necessary, but so is an honest, human response that centers the people whose lives are affected.
Take this as an opportunity to rebuild stronger procedures and clearer lines of responsibility. If nothing else, a painful event like this can catalyze real change in how we manage vendors, protect identities and restore trust.
Follow us on X (Twitter) and LinkedIn for more cybersecurity news and updates. Stay connected on YouTube, Facebook, and Instagram as well.
Share this :