Washington Post Cyberattack: State-Sponsored Espionage Targets Journalists and Press Freedom

Hoplon InfoSec
16 Jun, 2025
On June 13, 2025, a cyberattack targeting “The Washington Post” sent shockwaves through both media and cybersecurity communities. Microsoft email accounts used by reporters were compromised in what appears to be a state-sponsored espionage operation. The journalists affected were primarily those who cover sensitive national security and foreign affairs beats, including investigations into China’s global influence and intelligence operations.
This incident is not just another data breach. It represents a direct attack on democratic institutions and the vital role of the press in holding power accountable. It demonstrates how state actors now view the media as both a threat and a resource, something to be monitored, manipulated, or neutralized. As the details unfold, one thing is clear: cyberwarfare has entered the newsroom.
The Anatomy of the Breach
According to internal sources and early investigations, attackers infiltrated Microsoft-hosted email accounts via a targeted campaign rather than through brute force. This was no random phishing scam. It was deliberate and focused, exploiting trust in well-known cloud platforms and the high-pressure, time-sensitive nature of a journalist’s workflow.
The breach was detected after suspicious activity was flagged during routine security monitoring. Some journalists reported being locked out of their accounts or receiving notifications of login attempts from unfamiliar devices. In response, The Washington Post launched an internal security audit and brought in third-party cybersecurity consultants to trace the origin, scope, and mechanism of the breach.
Microsoft, which powers the organization’s email infrastructure, was alerted immediately. Their incident response team collaborated with The Post’s IT department to isolate affected accounts and initiate credential resets. Meanwhile, reporters were instructed to avoid digital communications on sensitive stories until the situation was contained.
Targeting the Press: A Growing Global Trend
The deliberate targeting of journalists and news organizations by state-sponsored hackers is not new but it is becoming more frequent and more brazen. In the past decade, cyberattacks on media outlets have grown in both sophistication and frequency, often timed around high-profile investigations or political unrest.
In 2013, The New York Times revealed it had been hacked by a China-based group following its exposé on the finances of former Premier Wen Jiabao’s family. In 2021, Bloomberg journalists investigating Chinese market activities were also targeted by cyber actors, though attribution remained inconclusive.
These are not isolated incidents. Newsrooms have become battlegrounds in the war over information. When traditional military and diplomatic channels are insufficient or undesirable nation-states turn to cyber tools to infiltrate, monitor, or disrupt journalistic efforts.
Who’s Behind It? A Closer Look at Suspected APT Groups

While official attribution is still pending, experts believe the breach is the work of a Chinese state-sponsored Advanced Persistent Threat (APT) group. Two groups in particular APT10 (Stone Panda) and APT31 (Zirconium) have previously targeted media institutions and government agencies involved in foreign policy.
APT10 is known for its involvement in Operation Cloud Hopper, a sweeping espionage campaign that infiltrated managed service providers (MSPs) globally, including in North America. APT31, meanwhile, has been linked to phishing campaigns using malicious browser extensions and fake news outlets to collect data from high-profile individuals.
These groups typically leverage zero-day vulnerabilities, stolen credentials, and token hijacking to maintain long-term access. Once inside a network, they move laterally with caution, often spending weeks or months surveilling users, collecting emails, and exfiltrating documents. The strategic focus of the Washington Post breach journalists investigating China strongly aligns with the tactics and targets of these groups.
How Did It Happen? Technical Breakdown of Likely Attack Vectors
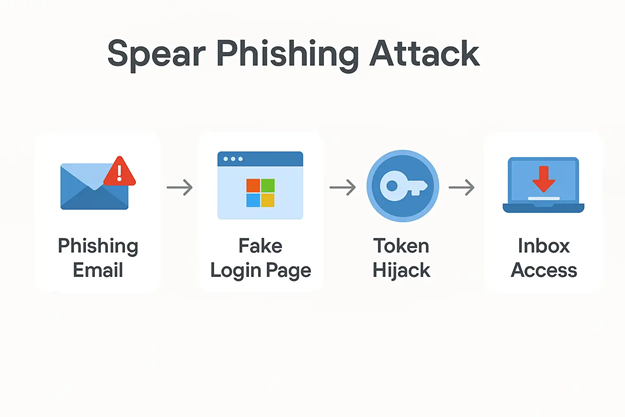
Although the technical details have not been fully disclosed, cybersecurity analysts have speculated that the attack involved a combination of social engineering and token-based exploitation.
One possibility is the use of token theft via OAuth manipulation, a method seen in previous Microsoft 365-related breaches. In this approach, attackers trick users into granting access to a malicious application posing as a legitimate Microsoft login prompt. Once granted, the token allows persistent access to email, calendar, and contacts without triggering standard login alerts or MFA prompts.
Another avenue could be session hijacking or MFA fatigue attacks, where users are bombarded with approval requests until they accidentally approve one, granting access to malicious actors.
Some experts are also considering the possibility of a cloud misconfiguration or the exploitation of previously unknown vulnerabilities in Microsoft’s authentication flow vulnerabilities which have historically been used in breaches such as Hafnium’s 2021 attack on Exchange servers.
These techniques highlight a dangerous reality: even when organizations adopt MFA and other best practices, motivated state actors can still find ways in through user deception or technical loopholes.
Why Journalists Are Easy and Valuable Targets

Journalists represent a unique cybersecurity challenge. They handle sensitive information, communicate with vulnerable sources, and often work from multiple devices or insecure networks. Despite this, their profession demands rapid information exchange, collaboration across borders, and minimal delays conditions that can conflict with strict cybersecurity protocols.
From a threat actor’s perspective, compromising a journalist’s email account is a goldmine. It may reveal:
- Communication with government officials
- Whistleblower identities
- Drafts of explosive reports
- Unpublished insights on national security
Once that data is harvested, it can be used for political manipulation, blackmail, disinformation campaigns, or to protect hostile regimes from public scrutiny.
Comparison with Past Media Breaches

| Incident | Year | Target | Perpetrator | Method | Motive |
| NYT China Exposé | 2013 | New York Times | China (APT) | Phishing + RATs | Political surveillance |
| Bloomberg Hack | 2021 | Financial journalists | Unknown (suspected China) | Credential theft | Market intelligence |
| Washington Post Attack | 2025 | National security reporters | China (suspected APT) | Token/session hijack | Espionage & press disruption |
This pattern reflects an escalation from passive monitoring to active infiltration, with threat actors aiming to shape international narratives by undermining the journalists crafting them.
The Implications for Press Freedom
The impact of this cyberattack goes far beyond technical inconvenience. It threatens the very core of investigative journalism. Confidential sources may refuse to communicate, fearing exposure. Journalists may become more cautious in their reporting or avoid sensitive topics altogether. The chilling effect on free expression is real and corrosive.
Moreover, this event could erode public confidence in the media’s ability to protect information and operate independently. If media organizations appear vulnerable to foreign manipulation, the credibility of their reporting may be questioned, ironically playing into the hands of authoritarian regimes that seek to discredit free press globally.
Microsoft’s Role and Repeated Scrutiny

Microsoft’s platforms, while feature-rich and widely adopted, have now been implicated in multiple high-profile breaches. SolarWinds, Hafnium, and now the Washington Post. Each case involves attackers exploiting either gaps in Microsoft’s identity and access management systems or weaknesses in third-party integrations.
While Microsoft has invested heavily in Zero Trust architecture and Defender for Office 365, critics argue that the company still faces challenges in proactively identifying and mitigating platform-level risks before they’re weaponized by APTs.
This latest breach may reignite calls for stricter security-by-default settings, better token management, and more transparent auditing mechanisms within the Microsoft ecosystem especially for sensitive industries like journalism, law, and government.
The Washington Post’s Immediate Response
In the hours following the breach discovery, The Washington Post initiated several containment and recovery actions:
- All affected credentials were immediately reset
- MFA was re-enforced across the board
- Cybersecurity consultants were hired to conduct a digital autopsy
- Communication was limited on certain sensitive investigations until systems were cleared
The organization also issued a public statement confirming the breach while withholding details that could compromise the investigation. This transparent yet cautious approach reflects a maturing attitude toward cyber incident disclosure, acknowledging the attack without enabling the attackers.
Additionally, The Post began reviewing its long-term cybersecurity roadmap, with new initiatives for journalist security training, endpoint detection systems, and encrypted collaboration platforms.
How the Media Industry Can Respond Proactively
This incident must be seen as a broader call to action for the global journalism community. Media houses must treat cybersecurity as mission-critical infrastructure, not just an IT issue. Key steps include:
- Mandating phishing-resistant MFA (e.g., FIDO2 keys)
- Restricting app-level access to mailboxes
- Encrypting sensitive communications and files
- Investing in endpoint detection and response (EDR)
- Creating journalist-focused OpSec training programs
Beyond individual newsroom upgrades, there is an urgent need for inter-organization threat intelligence sharing. Just as government agencies collaborate under ISACs (Information Sharing and Analysis Centers), media organizations could benefit from similar alliances to warn one another of APT tactics, phishing templates, or compromised infrastructure.
A Turning Point for Cybersecurity and Democracy
The Washington Post cyberattack is more than a technological breach, it’s a political and philosophical turning point. It underscores the fragility of institutions that democracy depends on, especially when those institutions rely on digital tools provided by private companies.
This incident demonstrates that information, not infrastructure, is now the battleground of power. Journalists are on the front lines of this war, not with pens and paper, but with keyboards, inboxes, and encrypted chats. If we fail to protect them, we not only compromise national security, but we also silence voices that keep democracies transparent and accountable.
Conclusion
As nation-state cyberattacks grow in scale and precision, no sector is off-limits, not even journalism. The Washington Post breach is a grim reminder that even the most vigilant organizations are not immune to determined adversaries. But it also serves as a call to arms. It demands a recalibration of how we view cybersecurity in the information age.
Defending the press is no longer just about legal protections or editorial independence, it’s about encryption, authentication, digital literacy, and cyber resilience. If the media industry, tech providers, and governments fail to rise to this challenge, the price will be much more than a headline; it will be the erosion of truth itself.
Did you find this article helpful? Follow us on Twitter and LinkedIn for more Cyber Security news and updates. Stay connected on Facebook and Instagram as well. At Hoplon Infosec, we’re committed to securing your digital world.
Share this :