WatchGuard VPN Weakness Lets Hackers Access Systems

Hoplon InfoSec
20 Oct, 2025
WatchGuard Firebox Fireware OS has a critical vulnerability (CVE-2025-9242) that enables remote attackers to use IKEv2 VPN services to run arbitrary code. Even if previous VPN settings were deleted, it still affects different firmware versions. WatchGuard recommends an immediate firmware upgrade or the use of temporary VPN security workarounds, and patches are available.
In simple terms, what happened?
An important out-of-bounds write vulnerability was found in the part of the WatchGuard Fireware operating system that handles VPNs. To put it simply, a specially designed VPN handshake can make the product write data to a memory buffer that it shouldn't.
This lets an attacker from a distance run any code they want on affected devices without having to prove who they are. It's like someone getting past a handshake and then going into a server room with bad intentions. The vendor put out a warning and made patches available for the affected versions.
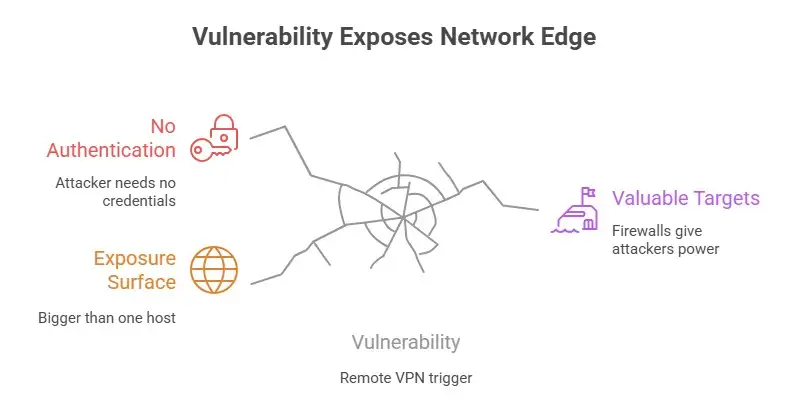
Why this weakness is very dangerous
There are three reasons why this is a big problem.
To start, the vulnerability can be triggered from a distance using VPN protocols that connect remote users and branch offices. That makes the exposure surface bigger than just one internal host.
Second, the problem is not authenticated, which means that an attacker does not need valid credentials to try to exploit it.
Third, network edge devices like firewalls are very valuable targets because breaking into them gives attackers a lot of power. All of these things together make the severity very high. A lot of security teams are making this their top priority.
Which devices and versions are affected?
The vendor's advisory lists a number of families and version ranges that are affected. Certain versions of Fireware OS, from different major branches, were said to be vulnerable until they were fixed in the updates that were given.
It needs to be fixed if your appliance runs any of the affected versions. The advisory also says that even if a vulnerable VPN configuration was removed before, some setups may still have traces of it that leave the device open to attack unless a patched version is installed. In this case, using the vendor's fixed firmware is the best and most reliable way to fix the problem.
A closer look at how attackers could use it
In terms of technology, the problem is with the way a certain VPN daemon handles certificate or identification payloads during an IKEv2 handshake. When that code doesn't check the length of a payload correctly, it copies data into a buffer that is a set size and can overwrite memory that is next to it.
In terms of attackers, that means that sending crafted traffic to the VPN service can set up situations where the attacker can overwrite return addresses or function pointers and then send execution to their payload. For defenders, the lesson is clear: Network-facing services that accept and parse input from outside the network always need strict boundary checks. If you want a technical playbook for testing, security advisories show you how to exploit a system step by step.
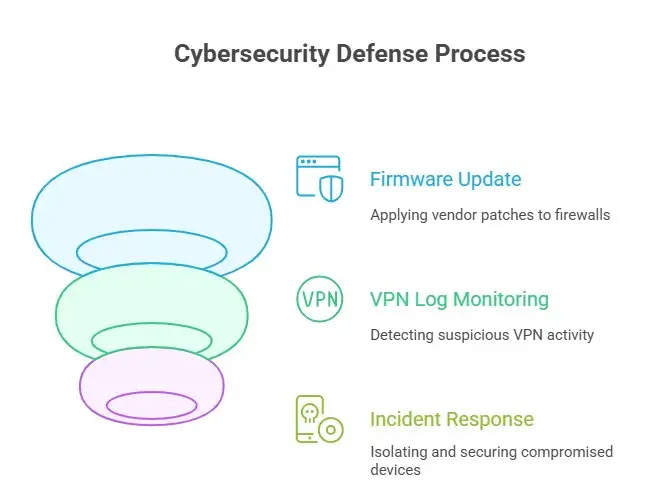
A quick list of things defenders need to do
1. Make a list of all your firewalls. Find all of your Firebox appliances and write down the versions of their Fireware OS.
2. Check the vendor's patched firmware and make sure to update the devices that need it first. If you can't patch right away, use the workarounds that the vendor suggests, like turning off dynamic peer BOVPNs and adding strict firewall rules.
3. Keep an eye on VPN logs for strange or repeated handshake attempts, traffic spikes, or failed authentications that could mean someone is scanning.
4. Assume that compromised devices could be used to move sideways and set conditional responses: isolate suspicious hosts, change credentials, and keep an eye on and log more activity.
If you need more specific steps, professional incident responders often do host integrity checks and configuration snapshots along with these actions to find changes that happen after exploitation.
Examples from the real world to help you understand the danger
Think of the firewall as a locked back door with a hole in it. When you say a password, the peephole camera looks at your face and lets you in. Now picture that the peephole's casing is broken and someone can put a fake ID into the mechanism that tricks the latch right away. That's what out-of-bounds write errors can let an attacker do: they can get around checks that are supposed to be there and make the system do something it shouldn't.
You could also think of it as a postal sorter with a mechanical arm. If the arm doesn't know how big the package is and pushes mail that is too big, it could break gears and cause the whole line to go the wrong way. Arbitrary code execution in software works by misrouting execution.
Why you should not put off patching firewalls
Companies sometimes put off patches to networking gear because they need planned maintenance and short service outages. But putting off fixes for a remote code execution problem on a perimeter device is very dangerous. Once an exploit is made public or proof-of-concept code is released, attackers quickly look for vulnerable instances.
In the past, a lot of breaches happened after organizations made public disclosures but hadn't yet applied vendor updates. Schedule the update during a maintenance window for mission-critical environments, and make sure you have rollback and test plans ready.
Things that teams often have trouble with and how to get past them
Teams often have trouble patching because of old firmware that doesn't work with new ones, custom settings, or the fear of breaking services that depend on them. To lower those risks, test patches first in a lab or on a device that isn't in use. Before upgrading, make a record of your current settings and make backups. If you depend on certain VPN setups, make sure they work on test hardware after you patch them.
If you can't quickly apply a patch, use layered defenses: block management access from networks you don't trust, make VPN users authenticate through an extra layer like a jump host, and use microsegmentation to keep the compromised appliance from easily accessing important internal systems.
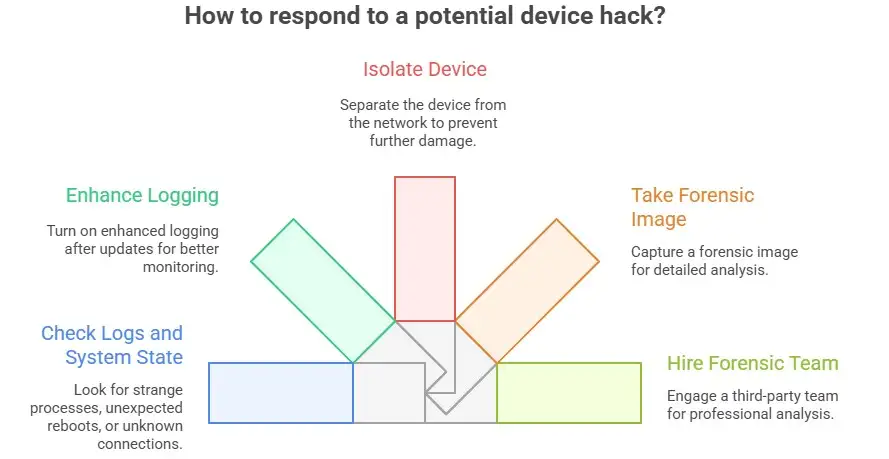
How to check if your device was hacked or used for something else
You can look for a number of signs in logs and the state of the system. Look for strange processes, unexpected reboots, sudden changes in settings, or connections to unknown hosts going out. Many vendors include improvements to logging in their patches. After you update, turn on enhanced logging if it's available. If you think a device has been hacked, separate it from the rest of the network and take a forensic image of it for analysis.
People who respond to incidents will look for changed binaries, strange scheduled tasks, or persistence mechanisms that the attacker put in place. If you don't have your own forensic team, you might want to hire a reliable third party.
Wider lessons from this event
A single flaw in a widely used product shows how important it is to have multiple layers of defense. It is dangerous to only use a perimeter appliance. Use endpoint detection, network segmentation, and identity protections together to limit the damage if a firewall fails. Part of good operational hygiene should be regular vulnerability scans, threat intelligence feeds, and a plan for emergency patching. Also, keep clear configuration baselines so you can quickly spot and fix any changes.
What customers and vendors need to do better in the future
Vendors should write parsing code that checks the length of strings very carefully and spend money on fuzz testing for parts that connect to the network. Customers should keep a list of their assets, keep track of the firmware lifecycle for their devices, and, if possible, automate patch management.
Clear communication is good for both sides: vendors should post clear advisory information and steps for fixing problems, and customers should sign up for vendor security mailing lists or advisories so they know about problems right away.
Useful takeaways
Security is a story told in layers. There is no one fix that will work for everything, but timely updates, monitoring, and good operational practices lower risk by a lot. If you take care of Firebox appliances, make sure to apply the vendor's patches first. Also, assume that attackers will look for exposed devices soon after a public advisory. In the short term, make a list of what you have, test the patches, use them, and keep a close eye on things.
If you are giving advice to others, send them a short list of what to do: find devices, patch them when you can, use workarounds when you have to, and keep an eye on them like your network depends on it. It does, though.
To prevent risks like the WatchGuard VPN exploit, Hoplon Infosec’s Penetration Testing service identifies vulnerable entry points before attackers do. Their expertise helps secure perimeter devices and harden your infrastructure against remote code execution threats.
Follow us on X (Twitter) and LinkedIn for more cybersecurity news and updates. Stay connected on YouTube, Facebook, and Instagram as well. At Hoplon Infosec, we’re committed to securing your digital world.
Share this :