Web Application Penetration Testing Tools Explained for 2026 Security
-20260130214637.webp&w=3840&q=75)
Hoplon InfoSec
01 Feb, 2026
Are web application penetration testing tools still effective against modern attacks in 2026, or are businesses trusting outdated defenses?
They still matter, but only when used correctly, updated constantly, and combined with human judgment.
What is really happening with web application security right now?
In the first few weeks of 2026, security researchers quietly confirmed something many teams already suspected. Automated scanners were missing logic flaws, broken authentication flows, and chained attacks that real hackers exploit daily. This matters because modern businesses live inside web applications. Banking, healthcare portals, SaaS dashboards, and even internal HR systems rely on them.
That is why web application penetration testing tools remain one of the most searched security topics today. Organizations want clarity. They want to know which tools actually work, which ones waste time, and how attackers are evolving faster than dashboards and reports.
The core issue is not that tools are useless. The issue is blind trust.
Why web application penetration testing tools matter more than ever
Every serious breach starts small. A forgotten endpoint. A weak input validation rule. A misconfigured API. These are not dramatic movie scenes. They are boring, quiet mistakes.
Web application penetration testing tools exist to surface those mistakes before attackers do. They simulate real-world attacks by probing inputs, manipulating requests, and testing how applications respond under pressure.
In practice, these tools help security teams answer uncomfortable questions. Can an attacker bypass login controls? Can sensitive data be extracted through error messages? Can business logic be abused without triggering alarms?
Without testing tools, teams rely on hope. Hope is not a strategy.
-20260130214638.webp)
Web application penetration testing tools explained.
At their core, web application penetration testing tools are software solutions designed to identify security weaknesses in web-based systems. They act like controlled attackers, scanning applications for vulnerabilities such as SQL injection, cross-site scripting, authentication flaws, and insecure configurations.
What many people misunderstand is that these tools do not “secure” anything. They only reveal problems. Fixing those problems still requires human decisions, developer cooperation, and realistic prioritization.
Think of them like medical imaging. An MRI shows issues. It does not heal the patient.
Types of web application security testing tools used today
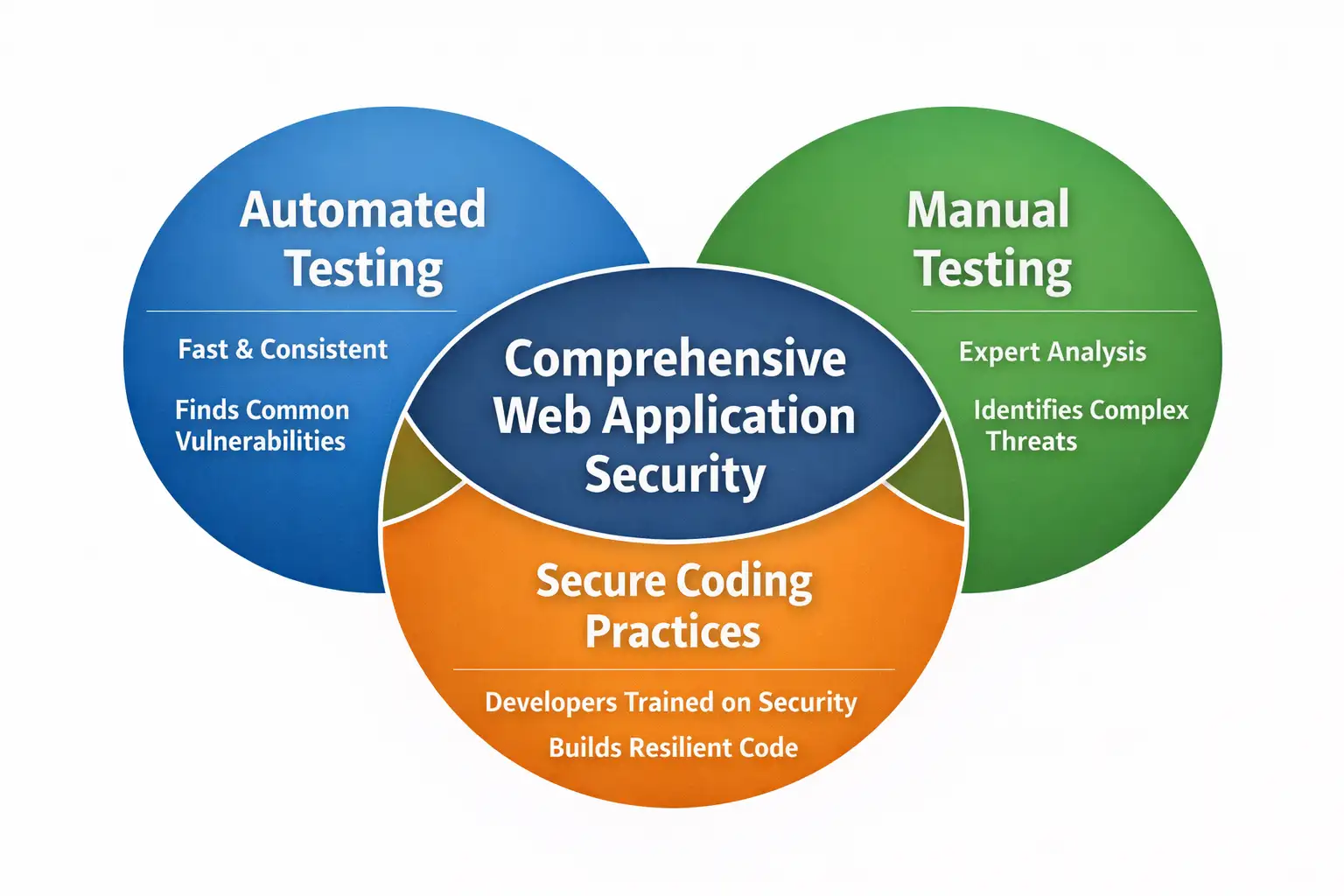
Modern security teams rarely rely on one tool. They combine multiple categories to cover different attack surfaces.
Dynamic testing tools interact with a running application and analyze responses in real time. Static testing tools examine source code without execution. Interactive tools sit between developers and applications during runtime.
Each type has strengths and blind spots. Overreliance on a single approach creates false confidence, which attackers love.
Web security testing tools and how attackers adapt
Attackers read the same documentation defenders do. When a vulnerability class becomes popular in tools, attackers pivot. They focus on logic flaws, chained exploits, and permission abuse that scanners struggle to detect.
This is why experienced testers often say tools find the obvious problems first. The dangerous ones hide deeper.
Best web application penetration testing tools for enterprise environments
Large organizations face a different challenge than startups. They manage dozens or hundreds of applications, each with unique logic and legacy components.
Enterprise-grade web application penetration testing tools must support authentication handling, API testing, role-based access checks, and integration with development pipelines. Simpler tools may work for small sites but collapse under enterprise complexity.
Common Vulnerabilities Found in Web Apps

A real-world example
A financial services company once ran automated scans weekly and proudly reported zero critical issues. Months later, a breach occurred through a flawed password reset workflow. No scanner flagged it because technically, nothing was “broken.”
An attacker simply understood the business logic better than the software did.
That incident did not discredit testing tools. It exposed how they were being used.
People Also Ask
Do web application penetration testing tools replace manual testing?
No. Tools accelerate discovery but cannot reason like humans. Manual testing remains essential for logic flaws and creative abuse paths.
Are free web penetration testing tools safe to use?
Some are excellent when used responsibly. Others create noise or false positives. Tool choice matters less than tester skill.
How often should web apps be penetration tested?
Anytime major changes occur,r and at least annually for stable systems. Continuous testing is ideal for high-risk environments.
Can penetration testing tools break production systems?
Poorly configured tools can cause performance issues. Testing should be controlled and approved.
Why over-automation creates invisible risk
Automation is comforting. Dashboards look clean. Reports look final. But attackers do not follow checklists.
Security leaders who rely solely on web application penetration testing tools often discover problems only after damage occurs. Balanced programs treat tools as assistants, not decision-makers.
The most mature teams blend automation, manual review, and developer education into a single workflow.
What should users and companies do next?
Start by asking honest questions. Are tools updated? Are results reviewed critically? Are developers involved in remediation discussions?
Testing without fixing is theater. Fixing without understanding is guesswork.
Security improves when feedback loops stay tight and realistic.
According to the OWASP Web Security Testing Guide, “No single tool can identify all security vulnerabilities. Human insight remains essential.”
Gartner security analysts consistently echo this view, emphasizing layered testing strategies over tool dependency.
Practical Recommendations
Use web application penetration testing tools early in development, not just before launch.
Combine automated scans with targeted manual testing
Focus reports on exploitability, not raw vulnerability counts
Retest after fixes to confirm real improvement
Treat findings as learning opportunities, not blame assignments
Final takeaway
Web application penetration testing tools are not broken. Expectations are. When used thoughtfully, they expose real risk and prevent real harm. When treated as magic shields, they create silence where warnings should be.
Security is not about tools alone. It is about curiosity, discipline, and the willingness to question clean reports.
Share this :