Windows Remote Desktop Services Vulnerability 2025 Guide
-20251112185139.webp&w=3840&q=75)
Hoplon InfoSec
12 Nov, 2025
You're an IT manager drinking your morning coffee when you get an alert. A user has used Remote Desktop Services (RDS) to get into a system, and now the machine has SYSTEM-level privileges. You scratch your head.
What happened?
The truth is that a flaw in Windows Remote Desktop Services lets an attacker go from being a regular user to having full control. This article will explain what this vulnerability is, how hackers use it, why it matters, and most importantly, how you can protect your systems.
What is the Windows Remote Desktop Services security hole?
The Windows Remote Desktop Services vulnerability is mainly about how RDS handles user sessions, redirection, memory objects, or access controls. For example, CVE-2020-0655 lets a remote authenticated user use clipboard redirection in Remote Desktop Services to run code in another user's session.
• In CVE-2025-59202, a "use after free" vulnerability in Remote Desktop Services let a local attacker with fewer privileges gain more.
• Even earlier, Microsoft’s MS16-017 (CVE-2016-0036) described an elevation of privilege vulnerability in RD, P, where specially crafted data over an authenticated RDP logon could allow elevated code execution.
To put it simply, an attacker who takes advantage of the flaw can move up to administrative or SYSTEM privileges when you think you are connected as a normal user through RDS. This gives them full control of the machine or network.
Why This Weakness Is So Risky
1.Trusted Access Channel
People often use RDS for remote management, support, or telecommuting. Many organizations have it open (even if only internally) because they trust it, which makes it a target for hackers. That trust turns into a problem once the Windows Remote Desktop Services vulnerability is used.
2. Getting more power
We usually think of RDS risks as brute-force access or stealing credentials, but in this case, the attacker might already have limited access and then use the vulnerability to get a lot more. Moving from a low-privilege user to SYSTEM or Administrator means being able to move across the network, launch lateral attacks, steal data, or fully compromise the system. ( See general ways to raise your privileges:
3. Huge Attack Surface
The potential impact of a Windows Remote Desktop Services vulnerability is high because RDS (and its underlying protocol, Remote Desktop Protocol) is used in many Windows environments, including servers, desktops, terminal services, and remote support machines. Kaspersky, for instance, lists the vulnerability as one of several risks that could allow someone to gain access to Windows remote components.
4. It's easy to find ways to exploit in the real world.
Attackers can use simple methods, like tricking a user into connecting to a malicious RDS server or changing an exposed RDS environment, to take advantage of the vulnerability and gain more access. For example, the blog post about CVE-2025-48817 talks about how a bad RDP server can trick a privileged user's client into running any code.
How Attackers Take Advantage of This Weakness
Let's go over a common way that a Windows Remote Desktop Services vulnerability could be used:
-20251112184815.webp)
1Getting in: The attacker gets in, maybe as a regular user account with remote access or through an account that has been hacked and has RDS access.
2. RDS connection: The attacker connects to a target machine using RDS. The connection looks real because remote desktop services are often turned on or allowed.
3. Triggering the vulnerability: Leveraging the vulnerability in RDS (memory corruption, clipboard redirection misuse, insufficient access controls), the attacker executes code or manipulates services to escalate privileges. (e.g., CVE-2020-0655).
4. Privilege escalation: The attacker moves from being a low-privilege user to having SYSTEM or Administrator rights on the host.
5. After the attack: The attacker can install a backdoor, move laterally across the network, steal credentials, or take data out of the network. RDS is the place where more damage can happen.
Example from real life: A standard user whose machine is accessible through RDS has had their remote session compromised. They use a flaw in RDS to issue commands as SYSTEM, turn off security controls, and install malware that stays on the system even after it is rebooted.
What Makes These Weaknesses Possible? Main Causes
There are a few problems that often make a Windows Remote Desktop Services vulnerability possible:
• RDS settings that are wrong or too open: for example, making RDS available on the internet, not using Network Level Authentication, allowing drive/clipboard redirection, etc.
• Problems with how RDS components handle memory: Use-after-free, buffer overflow, or not handling objects correctly in RDS code (for example, CVE-2025-59202).
• Not enough separation of privileges: RDS processes run with higher privileges, which could expose weak areas.
• Patching that takes too long and old systems: Older versions of Windows or servers that haven't been patched yet are still at risk (for example, MS16-017).
• Use of high-value target accounts: Once the attacker takes advantage of the vulnerability, it will be easier for them to do their job if the person logging in through RDS has administrative rights.
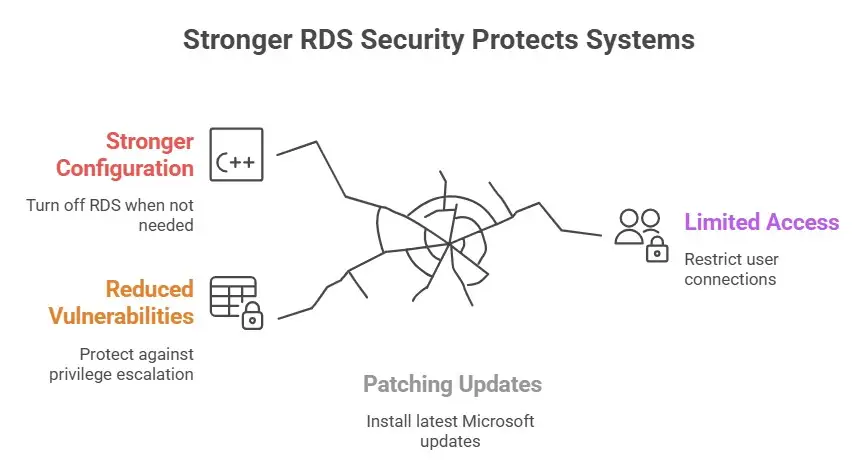
How to Stay Safe from the Windows Remote Desktop Services Security Hole
Patch quickly and all the time.
The best way to protect yourself is to install the latest Microsoft updates. For instance, Microsoft's bulletin MS16-017 talked about a way to get more privileges through RDP in 2016. The CVE-2025-59202 patch came out on October 14, 2025, which is more recent. Always keep the parts of RDS up to date.
Make RDS configuration stronger.
• Turn off RDS when you don't need it.
• Make sure that Network Level Authentication (NLA) is used for all RDS sessions.
• Only allow redirection features (like the clipboard and drives) when necessary. In the past, people have used these features to their advantage.
• Limit which users can connect through RDS, and don't give them too many administrative rights.
Access Control and Least Privilege
Make sure that users who have access to RDS don't have too many privileges. If an attacker uses a Windows Remote Desktop Services vulnerability to log in as a regular user, they will have a harder time than if they have admin rights. Limit standing privileges and use just-in-time access.
Network Segmentation and Watching
Give RDS hosts more value and keep them separate from other hosts. Keep an eye on remote sessions, record what happens, and set up alerts for strange privilege escalations or session patterns. Lateral movement and credential harvesting are common after an RDS compromise, as shown in pentesting literature.
Add Multi-Factor Authentication (MFA) and Credential Hygiene.
Many RDS vulnerabilities don't need stolen credentials, but combining MFA with good credential hygiene makes it harder for attackers to get in. Make sure that passwords are not the only way to get to things from a distance.
Getting ready for an incident response
Think about what could happen if there is a breach: If a vulnerability lets an attacker use RDS to gain more access, have playbooks ready. Add steps for isolating the host, taking away access, and doing a forensic investigation. Knowing how to act quickly cuts down on damage.
Anecdote from the real world
I once talked to a company where a junior help-desk account had RDS access to help with support. Because of a mistake, the account had local admin rights on the machine.
A vulnerability in the RDS service (unpatched) was exploited via a malicious session, and within hours, the attacker had SYSTEM access, pivoted to the domain controller, and deployed ransomware. What caused it? A mix of RDS misconfiguration, late patching, and too many user rights. The protections above could have stopped that from happening.
-20251112184313.webp)
Final Thoughts and Key Takeaway
The vulnerability in Windows Remote Desktop Services is still a big problem. When attackers use it, they don't just get a remote session; they also get control. Because many companies trust RDS, even users with low-level privileges can be the starting point for full system or network breaches.
The good news is you can stop this from happening. Patch regularly, make RDS configurations more secure, use least privilege, keep an eye on sessions, and get ready for incidents. Don't think of RDS as just another way to get remote access. Instead, think of it as a high-value access vector. This lowers the chances that a weakness will become a full-blown breach.
"The weakest link in remote access opens the door to everything else." So be careful when you use RDS access.
Questions and Answers
Q1: How quickly should I apply patches for a flaw in remote desktop services?
A1. As soon as you can. A lot of these weaknesses, like CVE-2025-59202, are made public and are very serious. The longer you wait, the more likely it is that someone will take advantage of you.
Q2. Can an attacker take advantage of a flaw in Windows Remote Desktop Services without having the right credentials?
A2. It depends on the exact vulnerability. Some need authentication (like clipboard redirection misuse in RDS), while others may be worse and let you run code from a distance with fewer permissions. Assuming that any weakness in the RDS infrastructure could be dangerous is the safest thing to do.
Q3. Does turning off RDS completely get rid of the risk?
A3. If you don't need RDS, turning it off is a good way to protect yourself. You should still harden it as described, even if you need remote access. Taking away services that aren't needed makes the attack surface smaller.
Q4. What does monitoring do after a breach of remote desktop services?
A4. Monitoring is very important. If a hacker takes advantage of a flaw in Windows Remote Desktop Services, they are likely to gain more access and move laterally to get to the data. Being able to see strange session patterns, new administrative accounts, or changes in privileges that weren't expected can stop the breach from getting worse.
Author: Hoplon Infosec
Bio: Security enthusiast with over 10 years in mobile cybersecurity. Connect with me on LinkedIn.
Address: 1415 W 22nd St Tower Floor, Oak Brook, IL 60523, United States
Phone: +1 773-904-313 , Contact: [email protected]
About/Privacy: At Hoplon Infosec, we provide expert insights into cybersecurity. Our editorial policy: all articles are written by in-house specialists or thoroughly reviewed by them to ensure accuracy, credibility, and up-to-date information.
Share this :