XZ Utils Backdoor Docker Images: Critical Security Threat 2025

Hoplon InfoSec
13 Aug, 2025
Late on a Friday, a developer noticed that SSH logins felt wrong, a small lag that did not match the server’s usual profile. That curiosity led to a message on a security list, and within hours the community learned that a popular compression library had been sabotaged at the source. The ripple effects did not stop at laptops or bare metal. They ran straight into container land, where automation is a superpower and a risk multiplier at the same time.
Teams had to ask a blunt question. Could XZ Utils backdoor Docker images be sitting in our registries unnoticed? The incident forced everyone to slow down, check assumptions, and treat base images with the same skepticism we reserve for third-party code.
What was backdoored and how it worked
The malicious code lived in release tarballs of xz, not in the everyday Git tree that most people scanned. During the build, an obfuscated macro unpacked a hidden object and slipped changes into liblzma. On targets that combined glibc, systemd, and a patched OpenSSH, the result could modify sshd behavior in ways that allowed remote access. Only versions 5.6.0 and 5.6.1 of xz carried the poison, which narrowed the window yet still allowed dangerous reach in rolling branches and prereleases. The nuance matters for containers because many images are built by bots from upstream packages without a second look.
Why containers were exposed so quickly
Containers are built from base images and dependency chains that update on their own schedule. If a base image tracked a fast-moving branch, and if its maintainers built during the unlucky window, the compromised package could ride along. A developer might never notice during Docker build, since compression utilities do not run loudly at build time. That is why some XZ Utils backdoor Docker images appeared so quickly across niche projects that automated builds from unstable repositories. The attack did not need to target containers directly. It only had to land in the supply line that images trust by default.
From the base image to your app
Layered images encourage reuse. That is great for speed, but it also preserves mistakes. If an image carried the compromised liblzma in a lower layer, later rebuilds might cache that layer even after upstream packages were fixed. Your Dockerfile could look clean and still inherit a bad library. That is the stealthy nature of XZ Utils backdoor Docker images and a reminder that refreshing layers is different from updating application code. To truly eliminate the risk, teams had to force rebuilds, re-resolve packages, and in some cases pin versions to known good releases rather than trust the latest.
What we learned in 2025
Research this year found that the story did not end when patches rolled out. Investigators uncovered dozens of Docker Hub images built during the exposure window that still circulate, often under generic tags that suggest stability. Some were pulled into private environments, which is how the trail was discovered. The lesson is painful and clear. If old tags remain reachable, old risks remain reachable too. When a registry keeps history by default, it takes extra effort to retire compromised artifacts, which explains why XZ Utils backdoor Docker images persist in the wild.
Which distros and images were most at risk?
The incident primarily touched rolling or prerelease channels. Fedora Rawhide and Fedora 40 beta received the bad packages, and Debian unstable carried them in certain builds. Alpine-based images largely avoided the issue because they rely on musl and different packaging, although derived images can always add vulnerable
components on top. This split explains why some official images stayed clean while community images that tracked fast branches did not. Knowing your base is not a formality. It is a control that decides whether XZ Utils backdoor Docker images can ever reach your workloads.
How to check your images right now
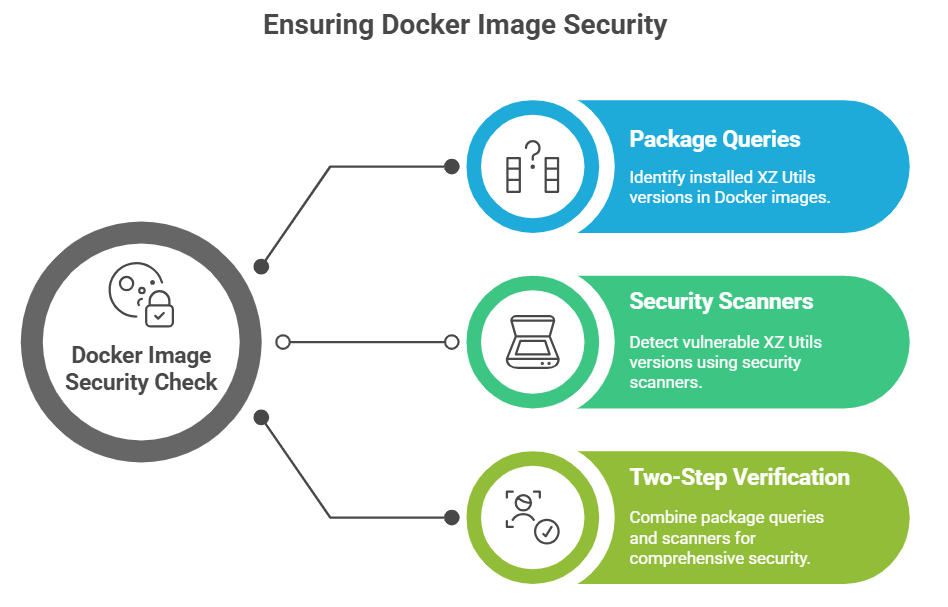
Start with the simplest test. For Debian- or Ubuntu-based images, run dpkg -l xz-utils or dpkg -l liblzma5 inside the container and check versions. For RPM-based images, use rpm -q xz or rpm -q xz-libs. Then scan with a container security tool that understands operating system packages. Docker Scout, Snyk, and others mapped CVE-2024-3094 early and continue to flag it. Combine both approaches. Package queries tell you what is present. Scanners tell you whether the version is safe. This two-step check catches XZ Utils backdoor Docker images with minimal effort.
Hunting in your registry and CI
Do not stop at one image. Search your registry by tag patterns from that time window and by digests that match known affected builds. Look through CI logs to find jobs that were built from rolling branches in late February and March of 2024. If you pushed to multiple registries, repeat the search everywhere. Teams often uncover a forgotten demo image or a proof of concept that still auto-deploys in a staging cluster. The quiet images are the ones that linger. Tracking them down is how you erase XZ Utils backdoor Docker images that nobody meant to keep.
Rebuild a strategy that actually removes risk
A safe rebuild means more than docker build with the same cache. Pin your distribution to a stable release, update package mirrors, and pass build args that disable layer caching for the steps that install system packages. Rebuild base images first, then application images that inherit from them. Delete or deprecate any tags that were built during the risky period. Announce the change in your changelog so downstream users know to pull fresh layers. This is the clean way to roll forward and evict XZ Utils backdoor Docker images from your fleet.
SBOMs, attestations, and provenance
Generate a software bill of materials for every image, store it with the artifact, and sign it. SBOMs help you answer a future audit in minutes instead of days. Use cosign or a similar tool to attach attestations that record when and how the image was built. If you ever need to prove that a fix shipped, you can point to the signature and the SBOM diff. This discipline would have made it easier to identify XZ Utils backdoor Docker images in many organizations, since you could query for liblzma and filter by version without opening a terminal on each host.
Pipeline guardrails that hold under pressure
Add stage gates that fail builds on critical vulnerabilities until an override is granted. Combine operating system package scans with application dependency scans. Track base image updates as chores with a real owner and a real schedule. Freeze tags in production so that the latest cannot drift under your feet. Each control is simple. Together they form a barrier that keeps XZ Utils backdoor Docker images from flowing into production when the next surprise lands. The goal is not perfect prevention. The goal is a fast, confident response that limits the blast radius.
Runtime signals and incident response
Even with all of the above, you still need to watch production. Unusual CPU spikes during SSH logins are a signal. A sudden change in SSHD logs is a signal. Unexpected outbound connections on odd ports are signals too. Treat them seriously. If you suspect exposure, isolate the host or pod, capture a forensic image, and rebuild from clean bases. Rotate credentials, verify network policies, and monitor egress for the next 48 hours. This is how you contain the impact of XZ Utils backdoor Docker images without turning a small scare into a prolonged outage.
A realistic team playbook
Picture a small startup with a staging cluster that uses a custom Fedora-derived image. The team discovers that a staging node was built in March 2024. They run rpm queries, confirm an affected liblzma version, and immediately cordon the node. Next, they rebuild the base image from a stable channel, force a fresh package install, and tag the result with a dated version. SBOMs are generated and signed. They then rebuild their app images, invalidate old deployments, and sweep their private registry for matching digests. Within a day they have removed XZ Utils backdoor Docker images from every environment and left a trail of evidence for later audits.
Communicating with stakeholders
Write a short, clear incident note. State that the exposure relates to a third-party package and give the CVE identifier. List the dates when affected images were built, the environments where they were deployed, and the steps taken to remediate. Link to upstream advisories and to your own changelog entries. This keeps customers, auditors, and executives confident while your team finishes the work. Being precise also helps others clean up any XZ Utils backdoor Docker images they may have pulled from your public tags.
Workflow for detecting and removing backdoored images
When a high-severity supply chain attack like this occurs, you need a repeatable plan:
1. Incident Trigger and Awareness. An alert or bulletin prompts an internal ticket and security huddle.
2. Initial Scoping. Match the vulnerable version release window to your build and registry history.
3. Targeted Image Scanning. Run OS package queries and vulnerability scanners side by side.
4. Containment. Isolate affected containers or nodes immediately.
5. Clean Rebuild. Start from trusted bases, pin versions, disable caching, and pull from safe mirrors.
6. Registry Cleanup. Remove or deprecate risky tags to prevent future pulls.
7. Verification and SBOM Update. Confirm no vulnerable packages remain, then sign and store artifacts.
8. Deployment and Monitoring. Roll out clean images and monitor for anomalies for at least 48 hours.
9. Communication and Lessons Learned. Notify stakeholders and update incident response playbooks.
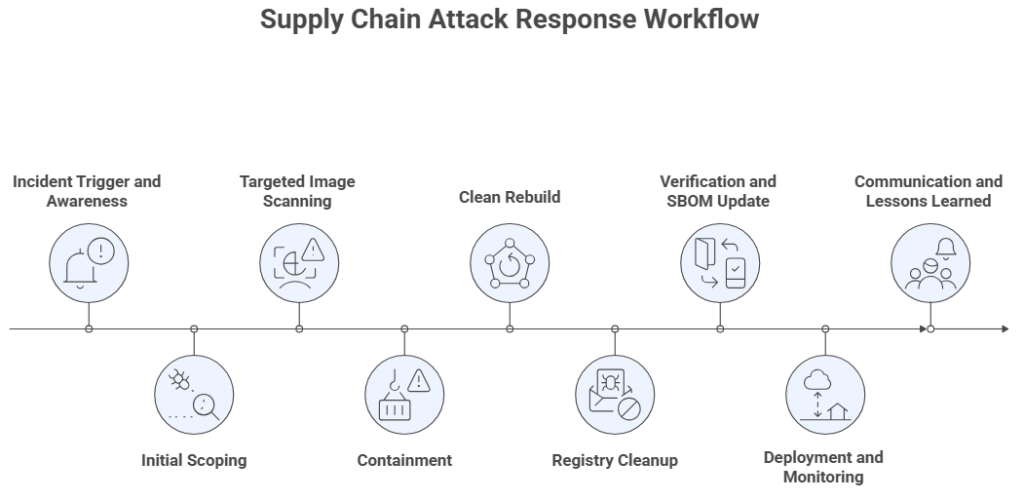
This workflow ensures that XZ Utils backdoor Docker images are detected, removed, and prevented from returning.
A compact checklist you can reuse
• Identify images built in late February and March 2024 and scan them
• Query packages inside containers and confirm xz and liblzma versions
• Rebuild base images from stable channels and pin versions
• Invalidate caches, force fresh installation steps, and retag clean builds
• Generate and sign SBOMs and attach them to artifacts
• Add pipeline gates for critical CVEs and freeze production tags
• Monitor runtime for unusual SSHD behavior or network egress
• Publish a short incident note with dates, scope, and fixes
• Retire old tags in your registry so nobody pulls a risky image by accident.
• Educate the team on how a subtle upstream change can travel far in containers
ActionNoteScan Feb–Mar 2024 imagesFocus on high-risk buildsCheck xz & liblzma versionsEnsure versions are secureRebuild base imagesUse stable channels, pin versionsClear caches & retag buildsForce fresh installationGenerate & attach SBOMsFor traceability and complianceAdd CVE gates, freeze tagsPrevent vulnerable builds in productionMonitor SSHD & networkWatch for unusual activityPublish incident noteInclude dates, scope, fixesRetire old registry tagsPrevent accidental pullsEducate teamShow impact of upstream changes
Final thoughts
The XZ Utils backdoor Docker images case shows how fragile software supply chains can be. Even a small change in an upstream dependency can create serious risks. Regular scanning, verifying image sources, and monitoring runtime activity are essential to prevent such threats. Security begins with awareness and quick action when something feels unusual.
Share this :