Brazilian Military Targeted Through Zimbra Zero-Day Hidden in Malicious Calendar Files

Hoplon InfoSec
06 Oct, 2025
You open your email on a Monday morning. A calendar invite shows up along with the usual meeting requests. Everything seems fine. When you click "Accept," everything seems fine for a short time. But something is going on behind the scenes. In early 2025, attackers used a zero-day flaw in Zimbra to turn regular .ICS (iCalendar) files into weapons that could silently compromise targets.
It's subtle, almost beautiful. Our calendars, which we trust, turned into a Trojan horse.
Why Zimbra and ICS Were the Best Targets
Zimbra is not just an email service. Businesses, governments, and the military all use it to share mail, contacts, and calendars. Because so many people use it, it is a good target. And what about iCalendar files? People talk to them all the time. They are everywhere: meeting invites, reminders, and exported events. Most people wouldn't think twice about opening them.
But the attackers saw a hole. Zimbra's Classic Web Client didn't clean up HTML content in ICS files completely. This meant that harmful scripts could hide inside and wait for someone to look at the calendar. When the embedded JavaScript was opened, it ran quietly, allowing access to emails, contacts, and the ability to change mailbox filters. With a CVSS score of 5.4, the CVE-2025-27915 vulnerability opened a hidden door for hackers.
How the Attack Happened
The method looked easy, but it was very accurate. Attackers sent ICS files that had obfuscated JavaScript in them. In one case that was reported, the Libyan Navy Office of Protocol was faked to send invitations to Brazilian military members. The JavaScript was waiting for a calendar entry to be rendered. The script would start up in less than a minute.
What could it do? It could read emails, contacts, and folders that were shared. It could make rules for forwarding that aren't obvious, like one called "Correo" that sends mail to [email protected]. It even had logic to hide parts of the interface and only let certain time windows run, all to avoid being found. And when the script needed to get data out, it did so quietly by talking to a server at ffrk.net/apache2_config_default_51_2_1.
It's like a magic trick that happens at just the right time. While the audience claps, everything seems normal. But the magician is already in charge behind the curtain.
Signs of Detection and Warning
It's hard to see this kind of attack. Most people think the ICS files look normal. Researchers at StrikeReady found the exploit by keeping an eye on ICS attachments that were larger than 10 KB and had strange script patterns. Some signs of a breach were sudden changes to mailbox rules, hidden UI elements in Zimbra, and connections to outside servers that weren't expected.
Technical analysts have also noticed that the attack uses TTPs that are similar to those used by UNC1151 and some behaviors that are similar to those used by APT28 campaigns, but it is still unclear who is responsible.
Awareness is very important for businesses. It's not only about firewalls and antivirus. It's about looking at behavior, like changes in filters, strange calendar behavior, and network traffic that doesn't make sense.
The Fix and the Fixing
Zimbra fixed this problem in versions 9.0.0 Patch 44, 10.0.13, and 10.1.5, which came out on January 27, 2025. You have to update to these versions. In addition to patching, companies should check their mailbox rules, look closely at large ICS attachments, and teach users how to spot suspicious calendar invites. Even invites that look trustworthy but come from people you don't know should be looked at again.
It reminds us that security isn't just about keeping people out. We should look closely at every tool we use every day, even something as simple as a calendar invite.
In an email, the attacker pretended to be the Libyan Navy's Office of Protocol and sent a zero-day exploit to a Brazilian military group.
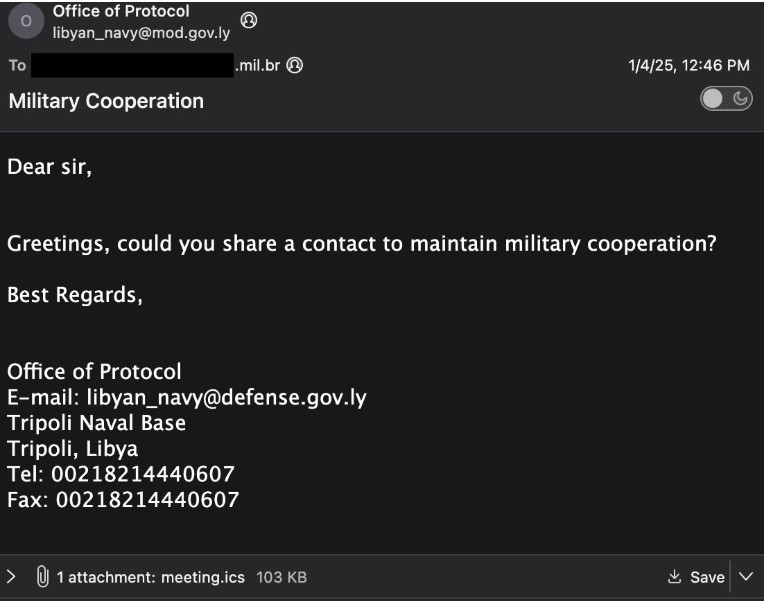
Source: StrikeReady
The attackers sent a 0 KB .ICS that hid a JavaScript file encoded with Base64.
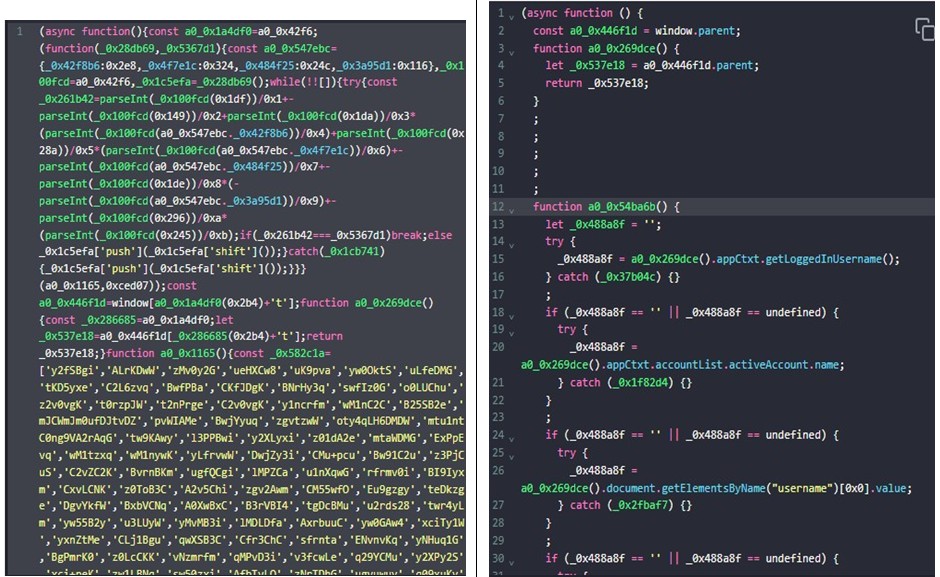
Decoding the JS payload
Source: StrikeReady
The payload goes after Zimbra Webmail to steal credentials, emails, contacts, and shared folders. It runs in multiple IIFEs at the same time.
What we learned
This exploit proves a simple point: threats often hide in places we don't expect them to. People often don't think much of XSS vulnerabilities, but they can be very useful for breaking into systems when used by the right people. Attackers are going after things that don't get a lot of attention, like collaboration suites, calendar parsers, and other "boring" features.
It's clear what organizations should do. Always patch quickly, keep an eye on strange behavior, and don't assume that everyday software is safe. Users should be a little skeptical of calendar invites that come out of nowhere.
Source
BleepingComputer has a full technical overview of this exploit that you can read for more information. Hackers used iCalendar files to take advantage of a Zimbra flaw that was a zero-day.
Bill Toulas of BleepingComputer says, "Researchers who were looking for unusually large ICS attachments found that a flaw in Zimbra was being used in the wild."
Summary: A Zimbra zero-day in ICS calendar files used CVE-2025-27915 to attack the Brazilian military. Users should install the patch and keep an eye out for strange behavior.
Box of Hoplon Insight
Suggestions:
• Right away, update all Zimbra instances to the most recent patched versions.
• Mark and check large ICS attachments before opening them, especially if they come from someone you don't know.
• Check mailbox filters and forwarding rules for changes that shouldn't have happened.
• Keep track of and look into strange calendar behavior or UI problems.
• Give employees training on how to recognize suspicious invites.
Hoplon Infosec’s Web Application Security Testing helps find hidden vulnerabilities in web apps like Zimbra before attackers do, keeping your systems safe from zero-day exploits.
Follow us on X (Twitter) and LinkedIn for more cybersecurity news and updates. Stay connected on YouTube, Facebook, and Instagram as well. At Hoplon Infosec, we’re committed to securing your digital world.
Share this :