OpenSSL Vulnerabilities: Remote Code Execution Risk Explained
-20260128105413.webp&w=3840&q=75)
Hoplon InfoSec
29 Jan, 2026
Is it possible for someone to run code on OpenSSL from a distance as of January 27, 2026?
Yes, but not in the way that social media headlines make it sound. OpenSSL released a big security update on January 27, 2026. It fixed 12 security issues, one of which was a high-severity flaw that could allow remote code execution in certain real-world situations.
The update is important because it shows a pattern that we all know but is still dangerous. Even small mistakes can lead to big security problems when software parses cryptographic data that isn't trusted.
This is exactly what happened here. While most of the fixed bugs could cause denial-of-service crashes, one vulnerability stands out because it can be triggered remotely and does not require authentication.
That is why conversations around OpenSSL remote code execution vulnerabilities are suddenly everywhere. And this time, the concern is grounded in verified technical details.
What changes were made to OpenSSL security in January 2026?
OpenSSL said that the update fixes security holes in versions 3.6 to 1.0.2, including CMS, PKCS#12, PKCS#7, BIO buffers, and TLS-related parts. OpenSSL also confirmed that FIPS modules are not affected, which is important because the vulnerable code paths are outside of validated boundaries.
At the center of the update is CVE-2025-15467, a flaw in how OpenSSL processes CMS AuthEnvelopedData when AEAD ciphers such as AES-GCM are used. By embedding oversized initialization vectors inside ASN.1 parameters, an attacker can trigger a stack overflow before authentication checks occur.
This is not theoretical. This is a known failure mode in security engineering, and it has caused real incidents before.
-20260128105413.webp)
Why CVE-2025-15467 is different from typical OpenSSL bugs
Most OpenSSL vulnerabilities over the years have fallen into two categories: subtle cryptographic weaknesses or stability issues that require unusual conditions. CVE-2025-15467 does not fit neatly into either group.
The vulnerability occurs early in the parsing process. Before OpenSSL verifies that the data is legitimate, memory is already written to the stack. If that write exceeds expected boundaries, the application can crash. In less protected environments, it could be shaped into a code execution path.
This is why security researchers describe it as an OpenSSL RCE vulnerability rather than just a crash bug.
Applications that process untrusted CMS or PKCS#7 data are at the highest risk. This includes S/MIME-enabled email systems, document verification services, and any backend service that automatically processes encrypted or signed content from external sources.
No encryption key required
One detail that security teams should not overlook is that attackers do not need encryption keys to trigger this vulnerability. The crafted input alone is enough.
That dramatically changes the OpenSSL exploit risk calculation. While platform defenses like ASLR or stack canaries may limit reliable exploitation, relying on those defenses alone is never a strong strategy. OpenSSL itself rated the issue as high severity, which reflects the realistic worst-case impact.
From a defender’s point of view, this is exactly the kind of OpenSSL security flaw that deserves immediate attention, not delayed patch cycles.
The quieter but still important PKCS#12 vulnerability
Another issue fixed in the update is CVE-2025-11187, which affects how OpenSSL validates PBMAC1 parameters in PKCS#12 files. When key length values exceed expected limits, the library may experience stack overflows or null pointer dereferences.
This vulnerability is less likely to be exploited remotely, but it still matters. PKCS#12 files are commonly used to store certificates and private keys. They are frequently exchanged, uploaded, and imported across systems.
Several additional low-severity flaws were also fixed, mostly tied to PKCS#12 parsing, PKCS#7 handling, BIO buffering, and TLS features. Individually, these may look minor. Together, they highlight how fragile cryptographic parsing logic can be.
This pattern is typical of a cryptographic library exploit class of issues. Small mistakes compound quickly when dealing with complex formats.
-20260128105412.webp)
Which OpenSSL versions are affected, and which are safe?
OpenSSL confirmed that the affected vulnerabilities span versions 3.6 through 1.0.2. Older branches that do not support features like CMS AuthEnvelopedData or PBMAC1 are not affected.
The recommended patched versions include
· OpenSSL 3.6.1
· OpenSSL 3.5.5
· OpenSSL 3.4.4
· OpenSSL 3.3.6
· OpenSSL 3.0.19
· Premium-support fixes for 1.1.1 and 1.0.2
Again, FIPS modules remain unaffected, which is important for regulated industries relying on validated cryptographic implementations.
Why do OpenSSL vulnerabilities always confuse online users?
Every time OpenSSL vulnerabilities appear in the news, misinformation spreads faster than patches. That is not new.
Some posts describe the issue as a global compromise. Others claim it is a “zero-day worm.” Neither is accurate. This is how zero-day misinformation starts. It feeds on partial truths and technical jargon taken out of context.
Security teams also face cybersecurity false alerts when scanners flag OpenSSL versions without understanding vendor backports or actual usage. A version string alone does not tell the full story.
-20260128105411.webp)
If you encounter a claim with no CVE, no OpenSSL advisory, and no reproducible details, it is reasonable to say:
“This appears to be unverified or misleading information, and no official sources confirm its authenticity.”
In this case, official sources do confirm the vulnerabilities. The challenge is understanding their real impact.
How to verify OpenSSL vulnerability exposure properly
Many teams ask how to verify OpenSSL vulnerability status without wasting days. The answer is methodical, not dramatic.
Start by identifying where OpenSSL is actually used. System packages, containers, embedded libraries, and statically linked binaries all count.
Next, confirm whether your applications parse untrusted CMS, PKCS#7, or PKCS#12 data. This is where risk sharply increases.
Then perform OpenSSL vulnerability verification using official OpenSSL release notes and vendor advisories, not just automated scanners.
Finally, patch and restart services. A patched library does nothing if the process is still running the old code.
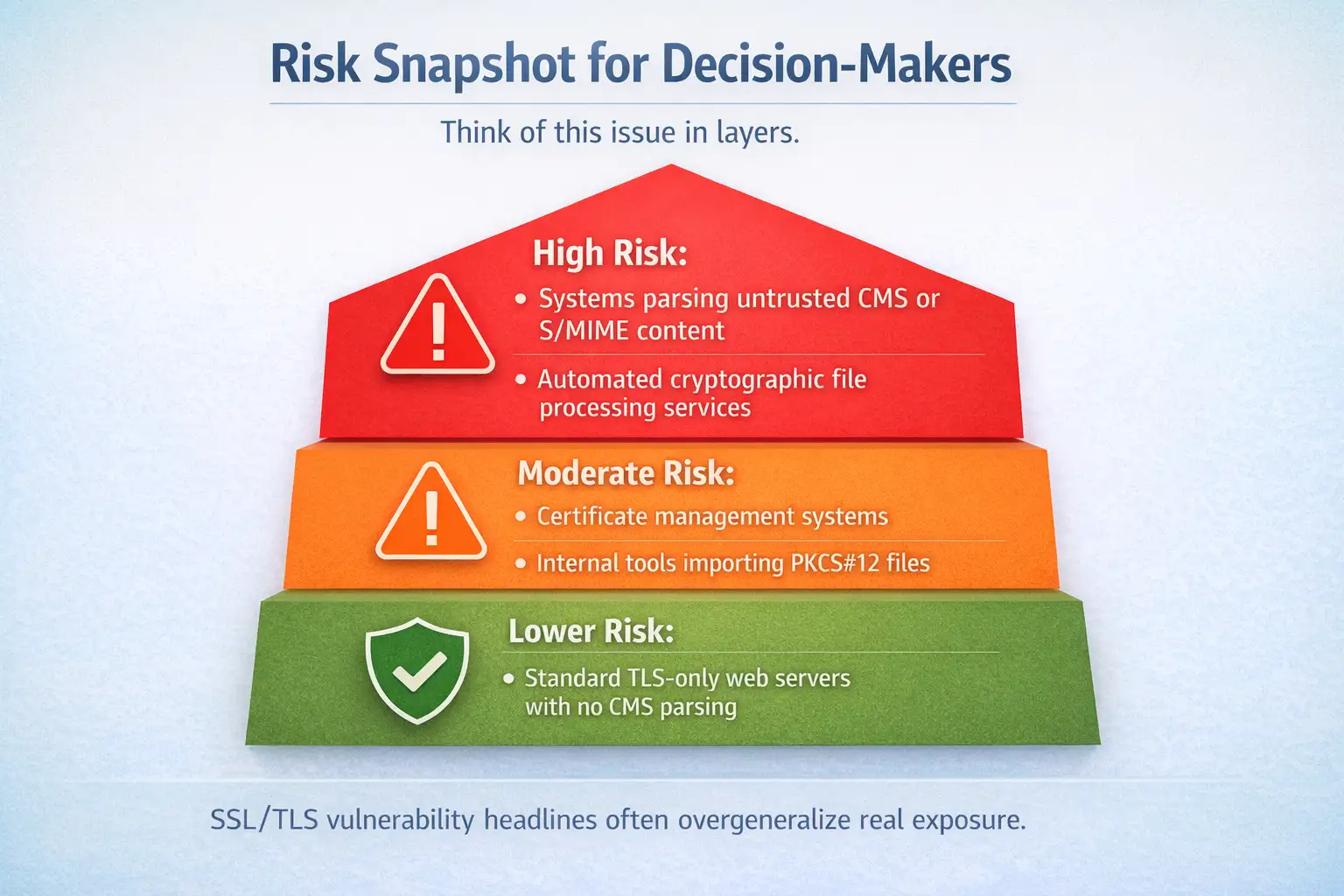
A simple risk snapshot for decision-makers
Think of this issue in layers.
High risk:
· Systems parsing untrusted CMS or S/MIME content
· Automated cryptographic file processing services
Moderate risk:
· Certificate management systems
· Internal tools importing PKCS#12 files
Lower risk:
· Standard TLS-only web servers with no CMS parsing
This layered view helps explain why SSL/TLS vulnerability headlines often overgeneralize real exposure.
What should users and businesses do next?
As soon as you can, update OpenSSL to the most recent patched versions. Put systems that handle untrusted cryptographic data at the top of your list.
Until all the patches are in place, don't process PKCS#12, PKCS#7, or CMS files that aren't trusted if you can help it. Even short-term restrictions lower exposure.
Finally, document your OpenSSL emergency security response. Clear records help during audits and future incidents.
People Also Ask
Is OpenSSL currently vulnerable?
Only if you are running affected versions and using the vulnerable features. Patching resolves the issue.
Can OpenSSL be exploited remotely?
In specific setups, yes. CVE-2025-15467 can be triggered remotely without authentication in applications parsing untrusted CMS data.
How do I check my OpenSSL version?
Run the command "openssl version -a," but also look at the bundled libraries and vendor advisories.
What happens if OpenSSL is compromised?
Outcomes range from service crashes to potential code execution, depending on the vulnerability and environment.
Are OpenSSL vulnerabilities common?
They are not frequent, but when they occur, their impact is wide due to OpenSSL’s reach.
Final takeaway
This update is not about panic. It is about discipline.
The vulnerabilities are real, the impact is understood, and the fixes are available. Organizations that act quickly and verify exposure carefully will likely experience little disruption. Those who delay may learn, once again, that cryptographic parsing bugs do not announce themselves politely.
Share this :