Apache Commons Text Vulnerability CVE‑2025‑46295: Remote Code Risk

Hoplon InfoSec
19 Dec, 2025
Is the Apache Commons Text vulnerability a big problem for Java apps today? Why are security teams sounding the alarm in December 2025?
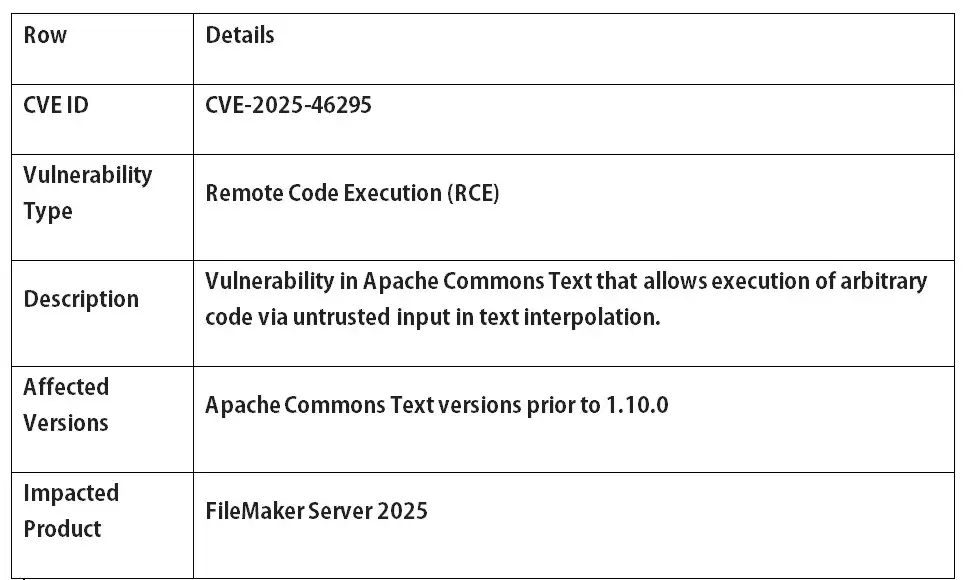
Yes. As of December 18, 2025, it has been confirmed that Apache Commons Text versions before 1.10.0 have a serious flaw called CVE-2025-46295 that lets attackers run code from a distance. When unsafe text interpolation processes untrusted input, attackers can run any code they want. Cyber Security News and the CVE databases have made this risk public, which means it is a real and urgent security issue.
This article explains the Apache Commons Text vulnerability in simple terms, breaks down how it works, and tells developers and organizations what they need to do right now.
Why the Apache Commons Text Vulnerability Is So Important
Apache Commons Text is not a little-known library that only a few projects use. It is quietly hidden in thousands of Java applications, frameworks, and business tools. It helps developers format text, replace placeholders, and change strings. The Apache Commons Text vulnerability is dangerous because it is so quiet.
When a security flaw affects a library that is used by a lot of people, it has effects that go beyond just one app. One insecure dependency can make customer portals, internal tools, and backend services open to attack without anyone knowing it. That is why this problem is a supply chain risk and not just a coding mistake.
Researchers who study security have confirmed that the vulnerability becomes very serious when apps use interpolation features with input that isn't trusted. In real life, that means that data that users control can become instructions that can be run.

What Really Goes Wrong Behind the Scenes
Text interpolation is meant to be useful. At runtime, it replaces placeholders with values. The issue arises when interpolation engines are permitted to assess intricate expressions or external lookups utilizing data sourced from users or external systems.
In some versions of Apache Commons Text, some interpolation features don't do a good job of limiting what those expressions can do. An attacker can make input that makes the system run commands that it wasn't meant to run. This is the main way that the Apache Commons Text vulnerability works.
It's like letting a stranger write instructions into your automation system without checking what they wrote. Even if the instructions are bad, the system always follows them.
A Clear Technical Breakdown of Which Versions Are Vulnerable and Why
All versions of Apache Commons Text that came out before 1.10.0 are affected. This includes a lot of environments that haven't updated their dependencies in years. Older versions let users use powerful interpolation options without making sure that safe defaults were used.
These features weren't meant to be harmful. They were made to be flexible. Researchers in security found that flexibility could be misused when it was used with data that wasn't trusted. That finding led to the official release of CVE-2025-46295.
You have to take a risk if your application uses Apache Commons Text directly or indirectly and relies on interpolation functions.
Why running code from a distance is so risky
In cybersecurity, remote code execution is thought to be one of the most dangerous types of vulnerabilities. It lets attackers run commands on a target system as if they were the app itself. This can result in stealing data, taking over a system, moving sideways, and leaving backdoors open.
If attackers can get to a vulnerable input path, they don't need to log in to exploit the Apache Commons Text vulnerability. That makes it easier to exploit and makes it more important to patch.
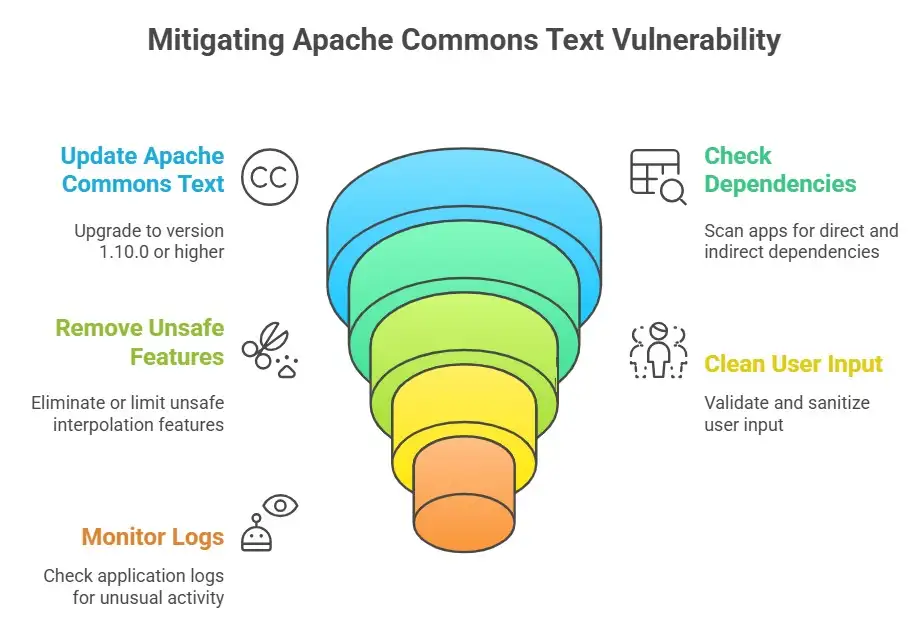
How to Fix Things and Lower Risk Right Away
Companies don't need to freak out, but they do need to do something.
Some useful steps to take to reduce the damage are
Update Apache Commons Text to version 1.10.0 or higher.
Check all apps for direct and indirect dependencies.
Remove or limit unsafe interpolation features.
Check and clean all input from users.
Check application logs for strange behavior.
The best way to fix the problem is to upgrade. Apache has said that newer versions fix the problem by removing or securing the unsafe behavior that caused it.
Dependency scanning tools can help find hidden use in third-party products and frameworks. A lot of teams only find out they're affected after scanning their whole dependency tree.
Many organizations have been able to avoid silent exposure thanks to this step alone.
Comparing Text4Shell and Lessons Learned
Security experts quickly compared CVE-2025-46295 to the Text4Shell vulnerability from 2022. That comparison makes sense.
Both problems have to do with Apache Commons Text and unsafe interpolation. Both show how small libraries can do a lot of damage. The only thing that makes a difference is awareness.
After Text4Shell, a lot of groups said they would make dependency management better. The Apache Commons Text vulnerability shows that the lesson still needs to be learned again.
Faster disclosure and patch adoption are one big improvement that has happened since then. Vendors and maintainers are getting back to people faster than they used to. That helps keep people from taking advantage of others in the real world.
Example of an effect in the real world
An enterprise software program that used Apache Commons Text internally was a clear example. Some products came with versions that were vulnerable but didn't show it until the CVE came out.
Once the problem was found, vendors released updates that replaced the library version that was causing the problem. Customers who used those updates right away closed the risk. Those who waited were still in danger.
This pattern shows why being aware of dependencies is just as important as writing code.
Questions that are often asked
What is the Apache Commons Text flaw in simple terms?
When untrusted input is used, attackers can use unsafe text processing features to run malicious code.
Which versions should not be used?
Any version of Apache Commons Text that is older than 1.10.0 should be seen as unsafe.
How can I find out if my app is affected?
Look for Apache Commons Text in your list of dependencies. Look over how text interpolation features are used.
Is upgrading enough to solve the problem?
The main fix is to upgrade. Extra protection comes from input validation and safer coding practices.
What You Should Do Next and Final Thoughts
There is more than one bug in the Apache Commons Text vulnerability. It's about how easy it is for trusted libraries to become attack paths when convenience is more important than security.
If you work with Java apps, now is a good time to stop and think about how dependencies are managed. Updating libraries is not busy work. It is managing risk.
Use this weakness as a reminder that security doesn't always work. It often fails quietly, in code we stopped thinking about years ago.
Check your systems. Make sure your dependencies are up to date. And going forward, make sure that secure defaults are always part of how you build software.
You can also read these important cybersecurity news articles on our website.
· Windows Fix,
For more, please visit our homepage and follow us on X (Twitter) and LinkedIn for more cybersecurity news and updates. Stay connected on YouTube, Facebook, and Instagram as well. At Hoplon Infosec, we’re committed to securing your digital world.
Share this :